Cyber Security
Configuring Database Account Security
Account description
When setting up a DWS cluster, the system will create the following accounts to provide comprehensive background operations and maintenance services for databases:
- dbadmin: system administrator account used for the initial login to the DWS database. It is responsible for creating service databases, managing common users, and assigning permissions.
- If separation of duties is enabled, additional accounts such as security administrator and audit administrator will be generated. The names of these accounts can be customized by the user. For details, see .
- Ruby: default O&M account, which cannot be used by O&M personnel of non-cloud service providers.
- om_user_First eight digits of the cluster ID: Other O&M accounts with preset permissions such as gs_role_analyze_any, gs_role_vacuum_any, gs_role_read_all_stats, and gs_role_signal_backend. These accounts are used for fault locating and cannot be used by O&M personnel of non-cloud service providers. For details, see Authorizing a DWS Cluster O&M Account.
Password complexity requirements
- The password of DWS system administrator dbadmin is set when the cluster is created. The DWS console verifies the password complexity. If the verification fails, the password cannot be set.
You can learn more password complexity requirements in Creating a DWS Storage-Compute Coupled Cluster.
- Other common database users are also required to maintain a certain level of complexity in their passwords.
- The password should contain 8 to 32 characters.
- The password should contain at least three types of the following characters: uppercase letters, lowercase letters, digits, and special characters.
- The password cannot be the same as the user name or the user name in reverse order, case insensitive.
- The password cannot be the current password or the current password in reverse order.

To prevent your database password from being cracked, set a strong password and periodically change it.
User-defined password policy
You can modify default password policies. For details, see Creating a Custom Password Policy for DWS.
Configuring policies for account locking and password expiration
- Database user password validity: password_effect_time determines how long a database user password remains valid. When the password expires, the system prompts the user to change it. To modify this parameter, contact technical support.
- Maximum number of incorrect password attempts: The number of incorrect password attempts is controlled by the failed_login_attempts parameter. If the number of incorrect password attempts exceeds the specified value, the account is automatically locked. In this case, the system administrator needs to unlock the account. This parameter can be set on the DWS console. For details, see Modifying GUC Parameters of the DWS Cluster.
- Automatic account unlocking time: password_lock_time specifies the duration after which an account is automatically unlocked if it has been locked. To modify this parameter, contact technical support.
Resetting a password
- If the password of system administrator dbadmin is locked or forgotten, you can reset it using the DWS console.
- The password of a common user can be reset by system administrator dbadmin by running SQL commands in the background. The following command is an example. For details, see Creating a Custom Password Policy for DWS.
1ALTER USER joe IDENTIFIED BY 'password';
Configuring Security Groups
A security group is a collection of access control rules for instances, such as cloud servers, containers, and databases, that have the same security requirements and that are mutually trusted within a VPC. You can define different access control rules for a security group, and these rules are then applied to all the instances added to this security group.
Each security group can have inbound and outbound rules to control the traffic to and from instances. For inbound rules, you need to specify the source, port, and protocol. For outbound rules, you need to specify the destination, port, and protocol.
Enabling the EIP function for your database may expose your EIP DNS and database port to potential hacking risks. To protect information such as your EIP, DNS, database port, database account, and password, you are advised to set the range of source IP addresses in the DWS security group to ensure that only trusted source IP addresses can access your DB instances.
When setting up a DWS cluster, you can choose to configure a security group or use the default one. The default security group allows only port 8000 by default. After creating the cluster, you can modify the security group rules or switch to a different one.
Unbinding an EIP from an External Link
EIP offers public IP addresses and bandwidth for Internet access, making external access easier but also increasing the risk of network-wide attacks. EIPs are susceptible to external DoS/DDoS attacks.
If you do not require public network access, it is best to consider the database as an internal component and use an internal IP address for accessing it. In this case, it is advised to detach the EIP from the database.
Unbinding procedure
- Log in to the DWS console and choose Dedicated Clusters > Clusters.
- In the cluster list, click the name of the target cluster. The cluster details page is displayed.
- Click Edit in the Connection area. On the displayed page, click Unbind.
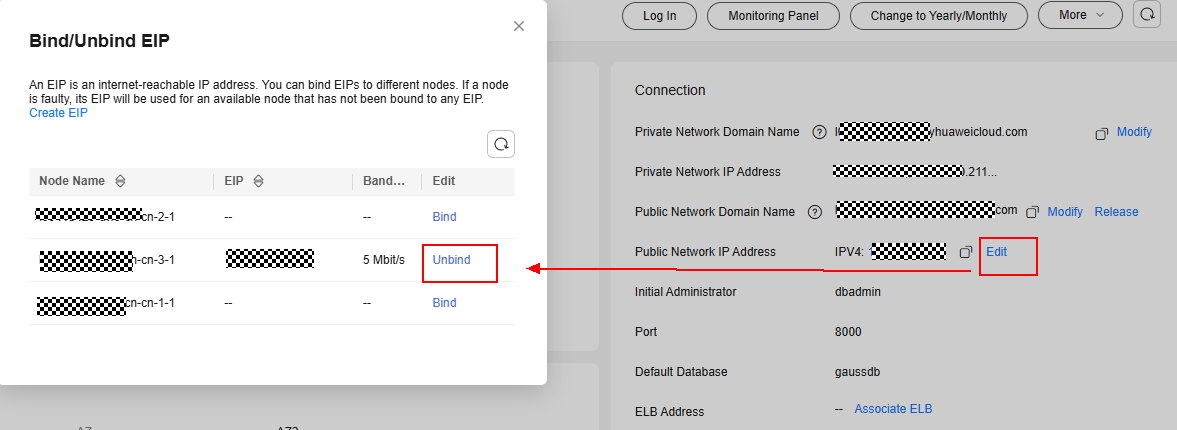

To meet high availability requirements, if a cluster is bound to an ELB, you only need to unbind the EIP from the ELB. For details, see the ELB user guide.
SSL-encrypted Data Transmission
DWS supports the standard SSL. As a highly secure protocol, SSL authenticates bidirectional identification between the server and client using digital signatures and digital certificates to ensure secure data transmission. To support SSL connection, DWS has obtained the formal certificates and keys for the server and client from the CA certification center. It is assumed that the key and certificate for the server are server.key and server.crt respectively; the key and certificate for the client are client.key and client.crt respectively, and the name of the CA root certificate is cacert.pem.
The SSL mode delivers higher security than the common mode. By default, the SSL function is enabled in a cluster to allow SSL or non-SSL connections from the client. For security purposes, you are advised to enable SSL connection. The server certificate, private key, and root certificate have been configured in DWS by default.
For details, see Establishing Secure TCP/IP Connections in SSL Mode.
Using DBSS (Recommended)
Database Security Service (DBSS) is an intelligent database security service. Based on the machine learning mechanism and big data analytics technologies, it can audit your databases, detect SQL injection attacks, and identify high-risk operations.
It is advised to use DBSS for enhanced data security capabilities. For details, see Database Security Service.
Advantages
- DBSS can help you meet security compliance requirements.
- DBSS can help you comply with DJCP (graded protection) standards for database audit.
- DBSS can help you comply with security laws and regulations, and provide compliance reports that meet data security standards (such as Sarbanes-Oxley).
- DBSS can back up and restore database audit logs and meet the audit data retention requirements.
- DBSS can monitor risks, sessions, session distribution, and SQL distribution in real time.
- DBSS can report alarms for risky behavior and attacks and respond to database attacks in real time.
- DBSS can locate internal violations and improper operations and keep data assets secure.
Deployed in bypass pattern, database audit can perform flexible audits on the database without affecting user services.
- Database audit monitors database logins, operation types (data definition, operation, and control), and operation objects based on risky operations to effectively audit the database.
- Database audit analyzes risks and sessions, and detects SQL injection attempts so you can stay apprised of your database status.
- Database audit provides a report template library to generate daily, weekly, or monthly audit reports according to your configurations. It sends real-time alarm notifications to help you obtain audit reports in a timely manner.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





