Converting an Ordinary Cluster to an Encrypted Cluster
GaussDB(DWS) allows you to convert an unencrypted cluster to an encrypted cluster when the cluster status is Available on the console. To ensure data security, converting a cluster to an encrypted cluster is an irreversible high-risk operation and will restart the cluster. As a result, services may be unavailable for a short period of time. Exercise caution when performing this operation.
If the current console does not support this feature, contact technical support.
Creating a KMS Agency
Scenario
Before converting a cluster to an encrypted cluster, you need to create an agency that grants the KMS Administrator permissions to GaussDB(DWS).
Procedure
- Click your account in the upper right corner of the page and choose Identity and Access Management.
- In the navigation pane on the left, choose Agency. In the upper right corner, click Create Agency.
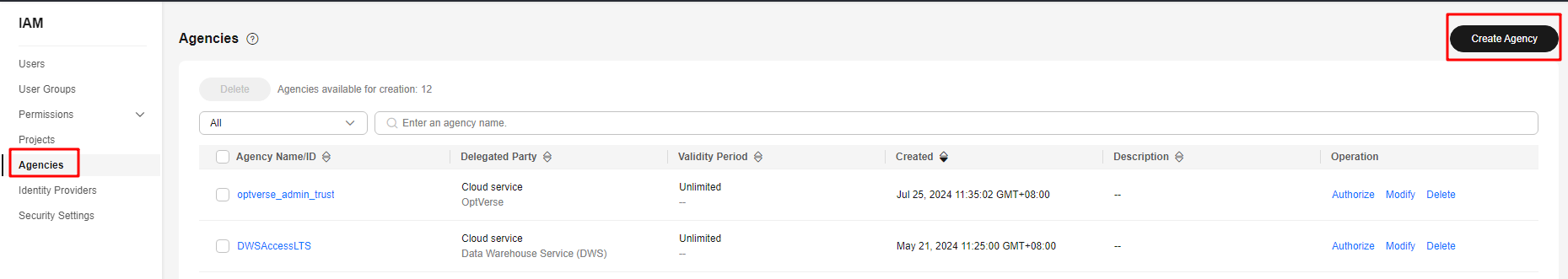
- Select Cloud Service and set Cloud Service to DWS.
- Click Finish. In the displayed dialog box, click OK to grant the KMS Administrator permission to the agency.
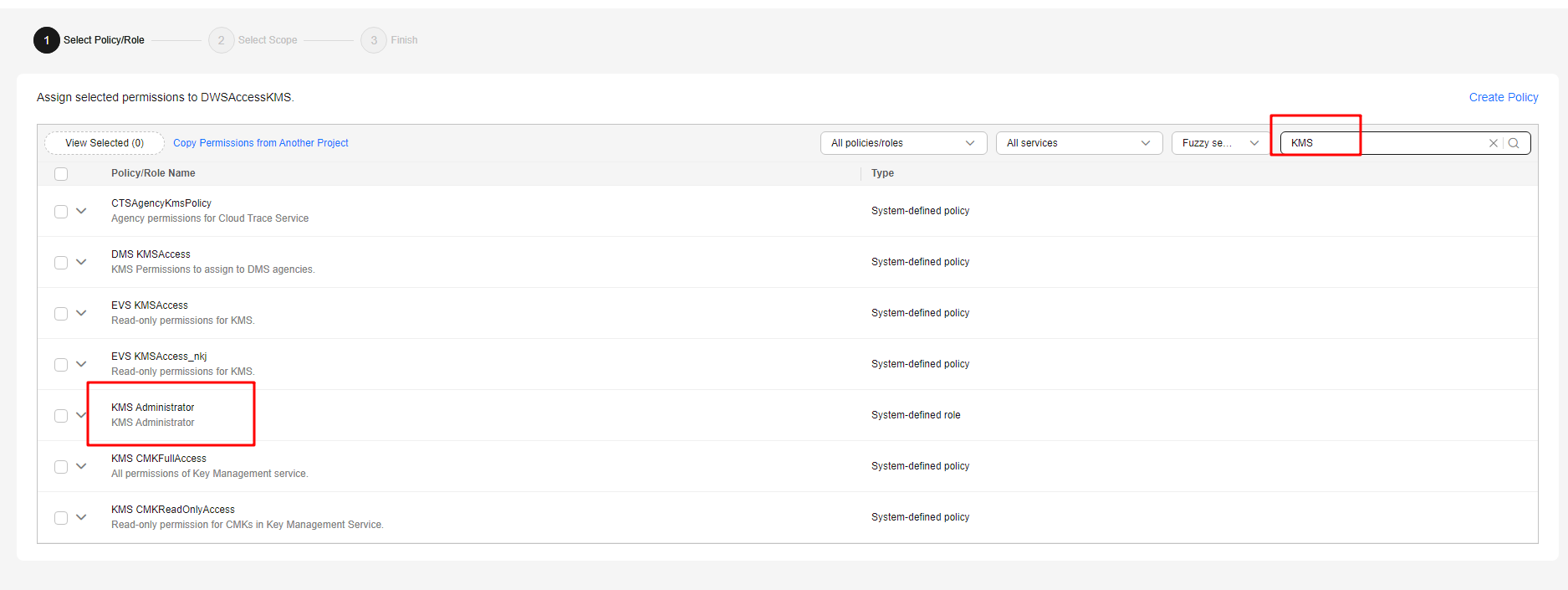
- Click Next. Select All resources or specific resources, confirm the information, and click Submit.
Procedure
- Log in to the GaussDB(DWS) console. In the navigation pane on the left, choose Clusters > Dedicated Clusters.
- In the cluster list, locate the row that contains the target cluster and choose More > Convert to Encrypted Cluster in the Operation column.
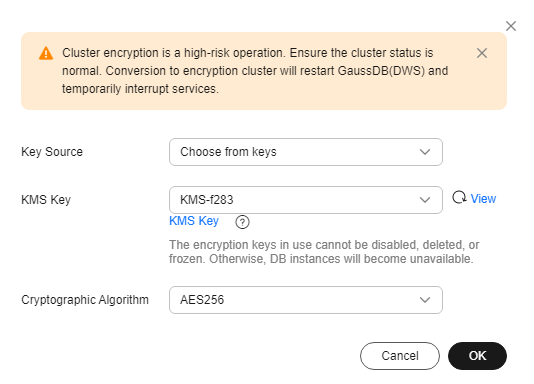
- In the dialog box that is displayed, select the key source, key name, and encryption algorithm to convert the cluster to an encrypted cluster.
- Method 1: Select a key name. You can create a resource share to share KMS resources with other members. After accepting the sharing invitation, members can select the shared KMS resource from the key source.
Figure 1 Select from existing keys
- Method 2: Enter the key ID. Enter the key ID used for authorizing the current tenant. For details, see Viewing a CMK.
When you grant permissions on the Creating a Grant page, the authorized object must be an account instead of a user. The authorized operations must at least contain Querying key details, Encrypting data, and Decrypting data.
Figure 2 Key ID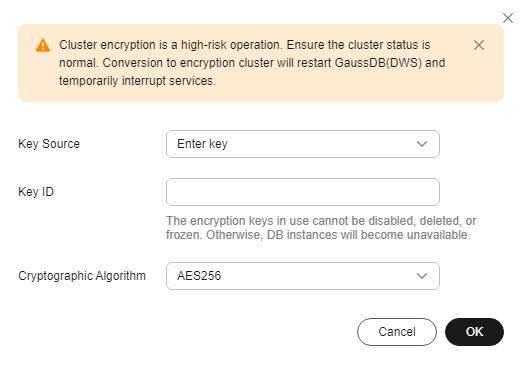
Table 1 Description Parameter
Description
Key Source
You can select a key name from the key list or directly enter a key name.
Cryptographic Algorithm
Encryption algorithms include:
- AES256 (general encryption algorithm, SM algorithms not supported)
- SM4 (compatible with international algorithms)
- The database encryption function cannot be disabled once it is enabled.
- After Encrypt DataStore is enabled, the key cannot be disabled, deleted, or frozen when being used. Otherwise, the cluster becomes abnormal and the database becomes unavailable.
- Snapshots created after the database encryption function is enabled cannot be restored using open APIs.
- By default, only Huawei Cloud accounts or users with Security Administrator permissions can query and create agencies. IAM users under an account do not have the permission to query or create agencies by default. Contact a user with that permission and complete the authorization on the current page.
- Method 1: Select a key name. You can create a resource share to share KMS resources with other members. After accepting the sharing invitation, members can select the shared KMS resource from the key source.
- After the conversion, you can click the cluster name to go to the Cluster Details page to view the cluster details. For details, see Viewing Database Encryption Information.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





