Copied.
Purchasing an ECS in Custom Config Mode
Scenarios
Elastic Cloud Server (ECS) is a cloud server that provides scalable, on-demand resources, including vCPUs, memory, OS, and Elastic Volume Service (EVS) disks. After purchasing an ECS, you can use it like using your local computer or physical server.
You can create an ECS by specifying its vCPUs, memory, OS, specifications, and login mode.
This section describes how to create an ECS on the management console.
Procedure
|
Step |
Description |
|---|---|
|
|
|
Log in to the ECS console and open the page for purchasing ECSs. |
|
|
Specify parameters based on your service requirements. |
|
|
Confirm the configuration details and complete the purchase. |
Preparations
- Sign up for a HUAWEI ID and complete real-name authentication.
Before purchasing an ECS, sign up for a HUAWEI ID, enable Huawei Cloud services, and complete real-name authentication first.
If you have enabled Huawei Cloud services and completed real-name authentication, skip this step.
- Top up your account.
Ensure that your account has sufficient balance. If not, top up your account.
- Plan network resources, such as VPCs and subnets.
When you purchase an ECS, the system creates a default VPC (vpc-default) and subnet (subnet-default).
If you do not want to use the default VPC and subnet, you can create a VPC and subnet in the corresponding region in advance. For more details, see VPC and Subnet Planning.
- Create a security group and add rules to it.
When you purchase an ECS, the system creates default security groups (default, Sys-WebServer, and Sys-FullAccess). For more information about security groups and rules, see Default Security Groups and Rules.
If the default security groups and rules cannot meet your service requirements, you can modify them. For details, see Configuring Security Group Rules.
- Create a key pair.
To log in to the ECS using a key pair, create one in advance. For details, see (Recommended) Creating a Key Pair on the Management Console.
- Create dedicated physical resources.
To make your ECSs run on isolated physical hardware, apply for a Dedicated Computing Cluster (DCC) before creating the ECSs.
For details, see Applying for a DCC.
- Register an edge site.
To create ECSs for CloudPond sites, register an edge site in advance.
For details, see Registering an Edge Site.
Step 1: Access the Page for Purchasing ECSs
Click Buy ECS on the ECS console.

Step 2: Specify Parameters
Specify parameters required for purchasing an ECS. These parameters include but are not limited to the billing mode, region, AZ, specifications, storage, and network.
Basic Configuration
- Select a billing mode.
You can select an appropriate billing mode based on the required duration and resource inventory to help you save costs.
Table 1 Billing modes Option
Description
Scenarios and Constraints
Reference
Yearly/Monthly
Yearly/Monthly is a prepaid billing mode in which you pay for ECSs before using them.
Yearly/monthly ECSs are billed by the required duration specified in the order.
This cost-effective mode is ideal when the duration of ECS usage is predictable. This billing mode is recommended for long-term users.
A yearly/monthly ECS cannot be deleted. If such an ECS is not required anymore, unsubscribe from it.
Pay-per-use
Pay-per-use is a postpaid billing mode. You pay as you go and just pay for what you use.
Pay-per-use ECSs are billed by the second and settled by the hour.
This mode is ideal when you want more flexibility and control on ECS usage.
Spot pricing
Spot pricing is a postpaid billing mode. You pay as you go and just pay for what you use. In Spot pricing billing mode, your purchased ECS is billed at a lower price than that of a pay-per-use ECS with the same specifications.
In Spot pricing billing mode, you can select Spot or Spot block for Spot Type. Spot ECSs and Spot block ECSs are billed by the second and settled by the hour.
Spot pricing is a good option if you want to enjoy the same performance at a lower price.
In spot pricing billing mode, your purchased ECSs are not suitable for long-term workloads or workloads that require high stability.
- (Optional) Set Reserved Instance.
This parameter is displayed only when Billing Mode is set to Pay-per-use and you have applied for the open beta test (OBT) of reserved instances. If you want to associate reserved instances (RIs) with your pay-per-use ECSs, select Associate RI and select an RI.
Figure 2 Reserved instance
- (Optional) Set Spot Type.
This parameter is displayed only when Billing Mode is set to Spot pricing. You can select Spot or Spot block for Spot Type.
Figure 3 Spot type
- Spot: The price of spot ECSs fluctuates with the market. For details, see Purchasing a Spot ECS.
- Spot block: The price of spot block ECSs depends on the predefined duration. For details, see Purchasing a Spot Block ECS.
- Set Region.
A region refers to a physical data center area where ECSs reside. For lower network latency and faster resource access, select the region nearest to your services.

- ECSs in different regions cannot communicate with each other over an intranet.
- Once ECSs are purchased, the region cannot be changed.
- When you purchase ECSs for a CloudPond edge site, the default region is the region where the edge site is located and cannot be changed.
- Set AZ.
An AZ is a physical location that uses independent power supply and networks. AZs in the same region can communicate with each other over an intranet.
Table 2 Selecting an AZ Option
Description
Scenarios and Constraints
Reference
Random
The available ECS types and flavors vary depending on AZs.
The system uses hash algorithms to allocate an AZ based on your universally unique identifier (UUID) and the ECS flavor you have selected.
To view all ECS types and flavors supported by the cloud platform, select Random for AZ.
AZN
AZs supported in the selected region. N indicates the sequence number of an AZ.
If you want to create an ECS in a specified AZ, select that AZ.
- For high availability (HA), create ECSs in different AZs.
- For low network latency, create ECSs in the same AZ.
Edge AZ
Edge AZs are deployed in on-premises data centers and are dedicated to CloudPond users.
If you are purchasing ECSs for a CloudPond edge site, an edge AZ is selected by default and it cannot be changed.
What Are the Relationships Between Edge Sites, Regions, and AZs?
Instance
- Select an instance selection mode.
Table 3 Instance parameters Option
Description
Scenarios and Constraints
Reference
By Type
You can select ECS specifications based on different properties.
- CPU architecture: x86 or Kunpeng
- Search filters: Filter by vCPU, memory, or keyword.
- Specifications: Select specifications by ECS type and flavor.
This mode is suitable for users who are familiar with the CPU architecture, vCPUs, memory, and instance family and generation of ECSs and want to select specific specifications.
By Scenario
ECS specifications are recommended based on categories and sub-categories.
This mode is suitable for users who have specific service requirements.
- (Optional) Set CPU Architecture.
This parameter is displayed only when you select By Type.
Table 4 CPU architectures Option
Description
Scenarios and Constraints
Reference
x86
The x86 CPU architecture uses Complex Instruction Set Computer (CISC) and supports almost all general software.
The execution of such an instruction is complex and time-consuming.
It is suitable for platform-dependent scenarios using Windows software and x86-compatible commercial software.
Kunpeng
The Kunpeng CPU architecture uses Reduced Instruction Set Computer (RISC) and Huawei-developed processors, so it is more cost effective.
RISC executes fewer types of computer instructions at a higher speed than CISC. RISC simplifies the computer architecture and improves the execution speed.
It is suitable for the following scenarios:
- Platform-independent scenarios such as e-commerce, big data, and scientific computing
- Arm native scenarios such as mobile phone simulation
- (Optional) Set Category and Sub-category.
These parameters are displayed only when you select By Scenario.

The specifications vary by region and AZ. For details, see the specifications displayed on the console.
Table 5 Categories and sub-categories Category
Sub-category
Description
Recommended Specification (Example)
Web applications
Traditional office
High security and reliability, suitable for traditional office scenarios like OA, ERP, and CRM with less than 200 concurrent access requests
C7 and C6
Enterprise websites
A balance of compute, memory, and network resources with a baseline level of vCPU performance and high cost-effectiveness
- C7 and C6
- S7 and S6
Personal application setup
A balance of compute, memory, and network resources with a baseline level of vCPU performance and high cost-effectiveness
- S7 and S6
- T6
Development and testing
A balance of compute, memory, and network resources with a baseline level of vCPU performance and the ability to provide burst CPU power at any time for as long as required
S7 and S6
Front-end servers
A balance of compute, memory, and network resources with a baseline level of vCPU performance. These ECSs can be used as front-end servers like Apache, Nginx, and IIS.
S7 and S6
Back-end servers
High ratio of CPUs to memory, high performance, and low latency. These ECSs are cost-effective options for back-end servers like Tomcat and JBoss.
C7, C6, and C6s
Website applications/E-commerce
100,000 pageviews/1,000 active users
Cost-effective, flexible, elastic resources available anytime
- S7 and S6
- T6
200,000 pageviews/2,000 active users
Suitable for e-commerce websites, which require high-performance cloud servers with fast elasticity and high stability to handle traffic bursts typical of special promotions, flash sales, and live commerce
- C7, C6, and C6s
- S7 and S6
500,000 pageviews/5,000 active users
Suitable for e-commerce websites, which require high-performance cloud servers with fast elasticity and high stability to handle traffic bursts typical of special promotions, flash sales, and live commerce
C7, C6, and C6s
Gaming
Gaming
Suitable for gaming services, which require high performance, high stability, high cost-effectiveness, and low latency
C7, C6, and C6s
Databases
Compute
Stable, high-performance compute
C7, C6, and C6s
Storage
Servers that use local disks with high storage bandwidth and IOPS to provide cost-effective mass data storage
- M7 and M6
- D7 and D6
Network
High PPS performance, high TPS throughput, and low network latency for rapid data exchange and processing
- E7 and E6
- M7 and M6
- C7, C6, and C6s
Data analytics
Management nodes
A large volume of compute resources scheduled to accelerate data processing
C7, C6, and C6s
Compute nodes
Balanced compute with high performance and stability
- M7 and M6
- C7, C6, and C6s
- I7, Ir7, I3, and Ir3
- S7 and S6
Storage nodes
Cost-effective, high-bandwidth storage for processing large amounts of reads and writes
D7, D6, and D3
High performance computing
High performance computing
High-performance compute clusters with large compute and high cost-effectiveness
H3
Graphics rendering
Animation rendering
CPU-accelerated rendering with high precision and stability
aC7, C6, and C3
Video rendering
GPU-accelerated rendering with high processing speed
G6
AI/Machine learning
AI training
Compatible with NVIDIA smart NICs for deep learning training, scientific computing, computational fluid dynamics, computational finance, seismic analysis, molecular modeling, and genomics.
P2vs, P2v, and P2s
AI inference
Compatible with NVIDIA smart NICs for image classification and recognition, speech recognition, natural language processing, video encoding and decoding, machine learning, and lightweight training.
Pi2
- Set Search Filters.
- Select specifications.
- Select vCPUs and memory, or enter a keyword to search for ECS specifications.
- Select ECS specifications by instance family and generation from the list.
For details about each type, see ECS Types.

- Sold-out vCPU and memory resources cannot be selected. You can select Hide sold-out specifications when purchasing ECSs.
- Set the scope of specifications to be displayed.
- Hide sold-out specifications: After this option is selected, sold-out specifications are not displayed.
- Only show latest generation: After this option is selected, only newly released ECS types and specifications are displayed. If this option is not selected, all ECS types and specifications available on the cloud service platform are displayed.
- Select specifications.
- (Optional) Set Maximum Price.
This parameter is available only when Billing Mode is set to Spot pricing and Spot Type is set to Spot.
- Automatic (Recommended): uses the pay-per-use price as the highest price you are willing to pay for a spot ECS.
- Manual: requires you to set the upper price limit for a spot ECS. The maximum price must be greater than or equal to the market price and less than or equal to the pay-per-use price.
For details, see Purchasing a Spot ECS.
- (Optional) Set Predefined Duration.
This parameter is available only when Billing Mode is set to Spot pricing and Spot Type is set to Spot block.
- Predefined Duration: a duration that you specify for your spot block ECS. Prices vary depending on predefined durations.
During the predefined duration, if your spot block ECS is automatically terminated by the system, you will not be billed for the resource usage within the predefined duration. If you delete your spot block ECS within the predefined duration, you will be billed based on the usage duration.
- Price for Each Spot Block ECS: you do not need to configure this parameter.
- (Optional) Number of Durations: This parameter is displayed only when Predefined Duration is set to 6 hours.
For details, see Purchasing a Spot Block ECS.
- Predefined Duration: a duration that you specify for your spot block ECS. Prices vary depending on predefined durations.
OS
- Set Image.
An image is an ECS template that contains an OS and necessary configurations. You can use an image to create ECSs.
Table 6 Images Option
Description
Reference
Public image
A public image is a standard OS image which is highly stable, authorized, and visible to all users. It contains an OS and preinstalled public applications.
If you need other applications or software, configure them on the new ECSs.
Private image
A private image is an image available only to the user who created or imported it. It contains an OS, preinstalled public applications, and the user's personal applications, saving the time for configuring an ECS repeatedly.
Shared image
A shared image is a private image shared by another account. You can use the same image to create ECSs across accounts.
KooGallery image
This parameter is available only when Billing Mode is set to Yearly/Monthly or Pay-per-use.
A KooGallery image is a third-party image that has an OS, application environment, and software preinstalled. You can use such an image for website setup, application development, and visualized management with just a few clicks. No additional configurations are required.
- (Optional) Set Host protection (HSS).
When you select certain public images, Host Security Service (HSS) is enabled by default. HSS Basic Edition provides one-month free trial and automatically installs the HSS agent. HSS Basic Edition provides functions such as weak password and vulnerability detection.
HSS is designed to improve the overall security for ECSs. It helps you eliminate risks, defend against intrusions and web page tampering, provide advanced defense, and manage security operations.
After the one-month free trial period expires, the HSS basic edition quotas will be automatically released, and HSS will not protect your servers.
If you want to continue using HSS or upgrade HSS security capabilities, you need to purchase HSS. For details, see What Should I Do When the Free Trial of HSS Basic Edition Expires?
After ECSs are purchased, you can switch between different HSS editions on the HSS console. For details about differences among different editions, see Specifications of Different Editions.
- (Optional) Set License Type.
This parameter is displayed only when the image you select is billed. It specifies a license type for using an OS or software.
Currently, you can select Bring your own license (BYOL), which allows you to use your existing OS license without the need to apply for a license again.
For more information about license types, see License Types.
Storage & Backup
- (Optional) Set Storage Type.
This parameter is displayed only when you have applied for a storage pool on the Dedicated Distributed Storage page.
Disks are classified as EVS disks and DSS disks based on whether they use dedicated storage resources. DSS disks provide dedicated storage resources.- DSS: disks are created using resources from the dedicated storage pool.
- EVS: disks are created using public storage resources.

- When you create disks in a DSS storage pool, the disk type must be the same as that of the requested storage pool. For example, both are of the high I/O type.
- For more information about DSS, see Dedicated Distributed Storage Service.
- Set System Disk.
A system disk stores the OS of an ECS, and is automatically created and initialized once the ECS is created.

If you detach the system disk that is purchased along with a yearly/monthly ECS and want to continue using it as a system disk, you can only attach it to the original ECS. If you want to use it as a data disk, you can attach it to any ECS.
Table 7 System disk parameters Parameter
Description
Scenarios and Constraints
Reference
Disk Type
Disk types are classified based on the I/O performance of disks.
Disks can be classified into the following types by I/O performance: Extreme SSD V2, Extreme SSD, General Purpose SSD V2, Ultra-high I/O, General Purpose SSD, High I/O, and Common I/O.
EVS disks differ in performance and price. You can choose whichever disk type is the best fit for your applications.
System Disk
System disk capacity, in GiB.
EVS disks are billed by disk capacity. Select appropriate capacity based on service requirements.
NOTE:For a P1 or P2 ECS, the system disk must be greater than or equal to 15 GiB. It is recommended that the system disk be greater than 40 GiB.
IOPS
Number of read/write operations performed by an EVS disk per second
This parameter is displayed only when General-Purpose SSD V2 is selected for Disk Type.
You are advised to set IOPS based on the value range and service requirements.
Throughput
Amount of data read from and written into an EVS disk per second
This parameter is displayed only when General-Purpose SSD V2 is selected for Disk Type.
Configure a desired throughput based on the value range and your service requirements.
- (Optional) Set Advanced Options for the system disk.
If you want to set SCSI and Encryption for the system disk, click Advanced Options.
Table 8 Advanced options Option
Description
Scenarios and Constraints
Reference
SCSI
Specifies the SCSI device type for the system disk.
This parameter is selected by default.
Device types:
- VBD: indicates the Virtual Block Device (VBD) mode.
- SCSI: indicates the Small Computer System Interface (SCSI) mode.
The default device type is VBD. If SCSI is selected, the disk will support transparent SCSI command transmission.
NOTE:The disk device type is configured during the purchase process. Once disks are purchased, the device type cannot be changed.
Encryption
Encrypts the system disk.
- If the ECS is created from an encrypted image, the system disk of the ECS is automatically encrypted.
- If the image you selected is not encrypted, you can select Encryption to encrypt the system disk.
Disk encryption provides strong security protection for your data. Snapshots generated from encrypted disks and disks created using these snapshots automatically inherit the encryption attribute.
For details, see step 4.
- (Optional) Set encryption parameters.
This parameter is displayed only when Encryption is selected in Advanced Options.

To use the encryption feature, click Create Agency first to grant EVS the permissions needed to obtain KMS keys for EVS disk encryption and decryption.
If you do not have sufficient permissions to grant EVS, apply for required permissions from the user who has the Security Administrator permissions.
For details, see Can All Users Use the Encryption Feature?
The encryption parameters are as follows:
- Agency Name: specifies the name of the agency that is used to grant EVS the permissions needed to obtain KMS keys for disk encryption and decryption. When Agency Name is displayed as EVSAccessKMS, KMS permissions have been granted to EVS.

To use the encryption feature, click Create Agency first to grant EVS the permissions needed to obtain KMS keys for EVS disk encryption and decryption.
If you do not have sufficient permissions to grant EVS, apply for required permissions from the user who has the Security Administrator permissions.
For details, see Can All Users Use the Encryption Feature?
- KMS Encryption: specifies how to obtain a KMS key.
- Select an existing key: Select a KMS key from the KMS Key Name drop-down list.
- Enter a key ID: Select a KMS key using the key ID.
- (Optional) KMS Key Name: specifies the name of the key used to encrypt EVS disks. This parameter is displayed only when KMS Encryption is set to Select an existing key.
You can select an existing key pair, or click Create KMS Key and create a KMS key on the KMS console. The default value is evs/default.
- KMS Key ID: specifies the ID of the key used to encrypt data disks.
- Agency Name: specifies the name of the agency that is used to grant EVS the permissions needed to obtain KMS keys for disk encryption and decryption. When Agency Name is displayed as EVSAccessKMS, KMS permissions have been granted to EVS.
- Set Data Disk.
Data disks store user data. If you add data disks (click Add Data Disk) when purchasing ECSs, the system will automatically attach the data disks to the ECSs. If you purchase data disks after ECSs are purchased, you need to manually attach the data disks.

- After data disks are attached to an ECS, you need to initialize the disks before using them.
- If you detach the non-shared data disk purchased when you purchase a yearly/monthly ECS and want to attach it again, you can only attach it to the original ECS as a data disk.
- The data disks purchased with a yearly/monthly ECS do not support separate renewal, unsubscription, auto-renewal, changing to pay-per-use, and deletion.
Table 9 Data disk parameters Parameter
Description
Scenarios and Constraints
Reference
Disk Type
Disk types are classified based on the I/O performance of disks.
Disks can be classified into the following types by I/O performance: Extreme SSD V2, Extreme SSD, General Purpose SSD V2, Ultra-high I/O, General Purpose SSD, High I/O, and Common I/O.
EVS disks differ in performance and price. You can choose whichever disk type is the best fit for your applications.
Data Disk
Data disk capacity, in GiB.
EVS disks are billed by disk capacity. Select appropriate capacity based on service requirements.
IOPS
Number of read/write operations performed by an EVS disk per second
This parameter is displayed only when General-Purpose SSD V2 is selected for Disk Type.
You are advised to set IOPS based on the value range and service requirements.
Throughput
Amount of data read from and written into an EVS disk per second
This parameter is displayed only when General-Purpose SSD V2 is selected for Disk Type.
Configure a desired throughput based on the value range and your service requirements.
Quantity
Number of data disks.
Specify the quantity of data disks to be added as required.
When purchasing an ECS, you can add a maximum of 23 data disks to the ECS.
- (Optional) Set Advanced Options for data disks.
To set SCSI, Sharing, and Encryption for data disks, click Advanced Options.
Table 10 Advanced options Option
Description
Scenarios and Constraints
Reference
SCSI
Specifies the SCSI device type for data disks.
This parameter is selected by default.
Device types:
- VBD: indicates the Virtual Block Device (VBD) mode.
- SCSI: indicates the Small Computer System Interface (SCSI) mode.
The default device type is VBD. If SCSI is selected, the disk will support transparent SCSI command transmission.
NOTE:The device type is configured during disk purchase. It cannot be changed after the disk has been purchased.
Sharing
Sharing is used to set a data disk as a shared disk.
After a data disk is configured as a shared disk, the shared disk can be attached to multiple ECSs.
Encryption
Encryption is used to encrypt data disks.
Disk encryption provides strong security protection for your data.
For details, see step 4.
Create Disk from Data Disk Image
This option is used to create a data disk from a data disk image.
If you use a Windows or Linux image to create an ECS, you can use a data disk image to create a data disk.
Select Create Disk from Data Disk Image. In the displayed list, select your data disk image.
NOTE:One data disk image can be used for one data disk only.
This function is unavailable if you have selected a full-ECS image to create ECSs or selected SCSI, Sharing, or Encryption for data disks.
- (Optional) Select Enable backup.
Configure this parameter only when you need to back up ECSs or EVS disks.
CBR backups can help you restore data in case of any ECS failures. To ensure data security, you are advised to enable backup.

- For CBR pricing details, see How Is CBR Billed?
- Cloud Backup and Recovery is not supported for CloudPond.
- (Optional) Set Cloud Backup and Recovery.
This parameter is displayed only when Enable backup is selected.
The following options are provided:- Create new: Set CBR parameters.
- Set the vault name, which consists of a maximum of 64 characters. Only letters, digits, underscores (_), and hyphens (-) are allowed. For example, vault-f61e. The default naming rule is vault_xxxx.
- Set the vault capacity, which is required for backing up the ECS. The vault capacity cannot be smaller than that of the ECS to be backed up. The value range is from the ECS's total capacity to 10,485,760, in GiB.
- Select a backup policy from the drop-down list, or log in to the CBR console and configure a desired one.
- Use existing: Select an existing CBR vault and configure a backup policy.
- Select an existing cloud backup vault from the drop-down list.
- Select a backup policy from the drop-down list, or log in to the CBR console and configure a desired one.
- Create new: Set CBR parameters.
Network
- Set VPC and Primary NIC.
Virtual Private Cloud (VPC) allows you to create logically isolated, configurable, and manageable virtual networks for ECSs. You can configure security groups, Virtual Private Network (VPNs), CIDR blocks, and bandwidths in your VPC. By default, ECSs in different VPCs cannot communicate with each other.
Figure 4 Network
You can select an existing VPC from the drop-down list box. By default, the system attaches a primary network interface (NIC) and specifies how a private IP address will be assigned.
For details, see VPC and Subnet Planning.

- You need to ensure that DHCP is enabled in the VPC which the ECS belongs to.
- If you want to use the shared VPC and subnet from another account, accept the resource sharing invitation first. For details, see Responding to a Resource Sharing Invitation.
For more information about VPC subnet sharing, see VPC Sharing in the Virtual Private Cloud User Guide.
- Set Primary NIC.
The primary NIC provides the default route and cannot be deleted. It is automatically created along with an ECS. After a VPC is specified, the system attaches a primary NIC to the ECS by default and specifies how a private IP address will be assigned.
- Set Primary NIC: If there are multiple subnets in the VPC, you can select another subnet from the drop-down list as the primary NIC.
- Set how an IPv4 address will be assigned. Automatically assign IP address is selected by default.
- Automatically assign IP address: The system automatically assigns a private IPv4 address to the primary NIC.
- Manually specify IP address: You need to manually assign a private IPv4 address to the primary NIC. Before specifying an IP address, click View In-Use IP Address to avoid address conflict.

If you specify a private IPv4 address when creating multiple ECSs in a batch, note the following:
- This IP address serves as the start IP address.
- The required IP addresses must be consecutive and available within the subnet.
- The subnet that contains the specified IP address cannot overlap with other subnets.
- Use existing network interface: This parameter is displayed only when the selected VPC has available network interfaces. You can select an existing network interface from the drop-down list as the primary network interface.
- (Optional) Set how an IPv6 address will be assigned. IPv6 not required is selected by default.
This parameter is displayed only when the IPv6 column of the selected ECS flavor is Yes and IPv6 is enabled for the subnet.
- IPv6 not required: No IPv6 address is allocated to the network interface.
- Automatically-assigned IPv6 address: The system automatically assigns a private IPv6 address to the network interface.
If Automatically-assigned IPv6 address is selected, the system assigns IPv6 addresses. In a VPC, ECSs use IPv6 addresses to access the dual-stack intranet.
To enable an ECS to access the Internet, you need to assign an EIP shared bandwidth, and add the ECS's IPv6 address to the shared bandwidth.
For details, see Adding EIPs to or Removing EIPs from a Shared Bandwidth.

- For details about how to enable IPv6 for a subnet, see IPv6 Network.
- After creating an ECS, check whether the ECS has obtained an IPv6 address. If not, enable IPv6 so that the ECS dynamically obtains an IPv6 address. For details, see Dynamically Assigning IPv6 Addresses.
- (Optional) Click Add Extension NIC.
Extension NICs can be separately added. If you need to attach multiple NICs to an ECS, you can add multiple extension NICs and specify their IP addresses.
Extension NICs cannot communicate with external networks before you configure policy-based routes for them. For operation details, see Configuring Policy-based Routes for an ECS with Multiple Network Interfaces.

The number of extended network interfaces that can be attached to an ECS is determined by the ECS specifications. For details, see A Summary List of x86 ECS Specifications and A Summary List of Kunpeng ECS Specifications.
- Set Extension NIC1: If there are multiple subnets in the VPC, you can select another subnet from the drop-down list as the extension NIC.
- Set how an IPv4 address will be assigned. Automatically assign IP address is selected by default.
- Automatically assign IP address: The system automatically assigns a private IPv4 address to the extension NIC.
- Manually specify IP address: You need to manually assign a private IPv4 address to the extension NIC. Before specifying an IP address, click View In-Use IP Address to avoid address conflict.
- Use existing network interface: Specify a NIC as the extension NIC. You can select a NIC from the drop-down list.
- (Optional) Set how an IPv6 address will be assigned. IPv6 not required is selected by default.
This parameter is displayed only when the IPv6 column of the selected ECS flavor is Yes and IPv6 is enabled for the subnet.
- IPv6 not required: No IPv6 address is allocated to the network interface.
- Automatically-assigned IPv6 address: The system automatically assigns a private IPv6 address to the network interface.
If Automatically-assigned IPv6 address is selected, the system assigns IPv6 addresses. In a VPC, ECSs use IPv6 addresses to access the dual-stack intranet.
To enable an ECS to access the Internet, you need to assign an EIP shared bandwidth, and add the ECS's IPv6 address to the shared bandwidth.
For details, see Adding EIPs to or Removing EIPs from a Shared Bandwidth.

- For details about how to enable IPv6 for a subnet, see IPv6 Network.
- After creating an ECS, check whether the ECS has obtained an IPv6 address. If not, enable IPv6 so that the ECS dynamically obtains an IPv6 address. For details, see Dynamically Assigning IPv6 Addresses.
- Set Source/Destination Check.
When this function is enabled, source IP addresses in the outbound packets will be checked. If the IP addresses are incorrect, the packets will not be sent out. This function helps prevent spoofing packet attacks and improve security. By default, Source/Destination Check is enabled.

The source/destination check settings apply only to the NICs created along with the ECSs.
Security Group
- Configure a security group.
Select an available security group from the drop-down list. You can select multiple security groups for an ECS (no more than five security groups are recommended). The access rules of all the selected security groups apply to the ECS.
When you create an ECS for the first time, the system automatically creates the following default security groups: default, Sys-WebServer, and Sys-FullAccess. For details, see Default Security Groups and Rules.
You can expand Security Group Rules to view details of inbound and outbound rules. Security group rules determine ECS access and usage. For details about how to configure security group rules, see Adding a Security Group Rule. Enable the following common ports and protocols as needed:
- Port 80: default port for web page access through HTTP.
- Port 443: port for web page access through HTTPS.
- ICMP: used to ping ECSs to check their communication statuses.
- Port 22: reserved for logging in to Linux ECS using SSH.
- Port 3389: reserved for remote desktop login to Windows ECSs.
- (Optional) Create a security group using templates.
If security groups displayed in the drop-down list do not meet your service requirements, click Create Security Group to create one using templates.
The templates have preset inbound and outbound rules. You can select one as needed.
- Configure security group details.
Figure 5 Configuring security groups
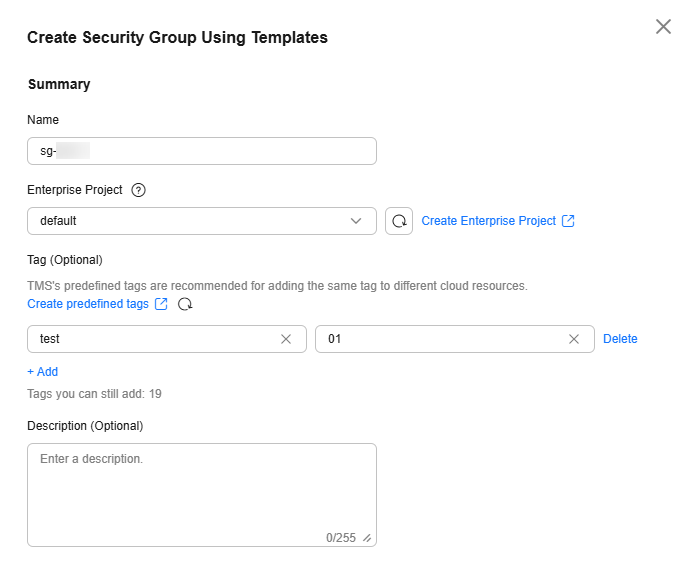
Table 11 Security group parameters Parameter
Description
Example value
Name
This parameter is mandatory.
A security group name, which can contain:- 1 to 64 characters
- Only letters, digits, underscores (_), hyphens (-), and periods (.)
NOTE:You can change the security group name after a security group is created. It is recommended that you give each security group a different name.
sg-AB
Enterprise Project
This parameter is mandatory.
When creating a security group, you can add the security group to an enabled enterprise project.
An enterprise project facilitates project-level management and grouping of cloud resources and users. The default project is default.
For details about how to create and manage enterprise projects, see Enterprise Management User Guide.
default
Tag
This parameter is optional.
You can add tags to the security group. Tags help you to identify, classify, and search for your security groups.
For details, see Overview.
Tag key: test
Tag value: 01
Description
This parameter is optional.
It describes a security group.
The description can contain a maximum of 255 characters and cannot contain angle brackets (<>).
-
- Configure templates for a security group.
Table 12 Template parameters Parameter
Description
Example value
Template
This parameter is mandatory.
There are three templates preset with different inbound and outbound rules for you to select.
- General-purpose web server: By default, ports SSH (22), RDP (3389), HTTP (80), HTTPS (443), and ICMP (All) are allowed.
- All ports open: Inbound traffic on any port is allowed. This poses security risks, so exercise caution when selecting this template.
- Common ports open: You can select common protocols and ports that the inbound rule will apply to.
Common ports open
Inbound Rules
This parameter is optional. This parameter is available only when Template is set to Common ports open.
The protocols and ports listed below can be quickly added. Select them as needed.- Remote Login and Ping: SSH (22), RDP (3389), FTP (20-21), Telnet (23), and ICMP (All)
- Web Service: HTTP (80), HTTPS (443), and HTTP_ALT (8080)
- Database: MySQL (3306), MS SQL (1433), PostgreSQL (5432), Oracle (1521), and Redis (6379)
-
- Click OK.
- Configure security group details.
- (Optional) Configure security group rules.
Click Configure Security Group Rules to modify rules of the current security group.
For details, see Configuring Security Group Rules.
- (Optional) Show or hide security group rules.
You can click Security Group Rules to show or hide the security group rules.
- Selected security groups: If there are multiple security groups, you can move a security group up or down to adjust the priority.
- Security group rules: You can view inbound rules and outbound rules.
Public Network Access
- Set EIP.
An EIP is a static public IP address bound to an ECS in a VPC. Using the EIP, the ECS can provide services externally.
The following options are provided:
- Auto assign: The system automatically assigns an EIP with exclusive bandwidth for each ECS. You can set the bandwidth.
- Use existing: An existing EIP will be assigned to an ECS. When using an existing EIP, you are not allowed to create ECSs in a batch.
- Not required: An ECS without an EIP cannot access the Internet. It can only be used to deploy services or clusters in a private network.

For a yearly/monthly ECS, Auto assign is unavailable for EIP. If an EIP is required, bind an existing EIP to the ECS. Alternatively, purchase an EIP that is billed in pay-per-use payment and then bind the EIP to the ECS.
- Set EIP Type.
- Dynamic BGP: If there are changes on a network using dynamic BGP, network configurations can be promptly adjusted using the specified routing protocol, ensuring network stability and optimal user experience.
- Static BGP: If there are changes on a network using static BGP, network configurations cannot be promptly adjusted and user experience may be affected.
- (Optional) Set Billed By.
This parameter is displayed only when EIP is set to Auto assign. Each bandwidth can be used by only one EIP.
- Bandwidth: Dedicated bandwidth will be billed by size.
- Traffic: Dedicated bandwidth will be billed by traffic you have actually used.
- Shared bandwidth: The bandwidth can be used by multiple EIPs and you will be billed based on the shared bandwidth.

- A bandwidth can be shared among a limited number of EIPs. If the number of EIPs cannot meet service requirements, switch to a higher shared bandwidth or apply for expanding the EIP quota of the existing bandwidth.
- Yearly/monthly EIPs do not support shared bandwidths.
- When a shared bandwidth that is billed on a yearly/monthly basis expires, the system automatically deletes the bandwidth configuration and creates a dedicated bandwidth billed by traffic for the EIPs sharing the deleted bandwidth configuration.
- (Optional) Set Bandwidth Size.
This parameter is displayed only when EIP is set to Auto assign. Select the bandwidth based on service requirements. The unit is Mbit/s.
- (Optional) Select an EIP.
This parameter is displayed only when EIP is set to Use existing. You can select an available EIP from the drop-down list.
Instance Management
- Set ECS Name.
The ECS Name set here will be used as the initial hostname in the ECS OS.
The name can contain only letters, digits, underscores (_), hyphens (-), and periods (.).

The name of a Windows ECS can contain a maximum of 15 characters and must be unique, or some Windows applications may be unavailable.
The naming rules of hostnames comply with RFC 952 and RFC 1123.
When you set the ECS name and hostname, you are advised to use letters (a-z), digits (0-9), and hyphens (-) to prevent unknown issues. In the ECS:
- Underscores (_) will be converted to hyphens (-).
- A combination of a hyphen and underscore (-_) will be converted to a hyphen (-).
- Periods (.), hyphens (-), underscores (_), and non-Latin characters at the beginning of the name will be ignored.
- For periods (.) and non-Latin characters that are not at the beginning of the name, they and any content following them will be ignored.
- When you purchase multiple ECSs in a batch, both automatic and custom naming are supported.
- Automatic naming: The system automatically appends four-digit numbers to the end of each instance name, moving up in increments of 1. For example, if you enter ecs, the first instance will be named as ecs-0001, the second as ecs-0002, and so on. If an ECS named ecs-0010 already exists, the subsequently created ECSs will be automatically named from ecs-0011.
- Custom naming: You can create a custom naming rule using the format, "name_prefix[begin_number,bits]name_suffix", where "begin_number" is a value from 0 to 9999, and "bits" from 1 to 4. For example, if you created a custom naming rule ecs[66,3]abc and created two ECSs, the system automatically names the instances ecs066abc and ecs067abc.
- Allow duplicate name: allows ECS names to be duplicated. If you select Allow duplicate name and create multiple ECSs in a batch, the created ECSs will have the same name.
- Set Login Mode.
Login Mode specifies the method for logging in to an ECS.
Table 13 Login mode parameters Option
Description
Scenarios and Constraints
Reference
Password
A username and its initial password are used for ECS login authentication.
The initial password of user root is used for authenticating Linux ECSs. The initial password of user Administrator is used for authenticating Windows ECSs.
It is recommended that you set passwords with high complexity to prevent malicious attacks. The passwords must meet the requirements described in Table 14.
NOTE:The system does not periodically change the ECS password. It is recommended that you change your password regularly for security.
Key pair
A key pair is used for ECS login authentication.
You can select an existing key pair, or click Create Key Pair and create a desired one.
Key pair authentication is more secure than password authentication.
NOTE:If you use an existing key pair, make sure that you have saved the key file locally. Otherwise, logging in to the ECS will fail.
Password from image
This parameter is displayed only when you select Private Image for Image and use a Linux private image with a password configured.
You can use the password of the selected private image for logging in to the ECS.
Make sure that a password has been set for the selected private image.
Image Management Service User Guide
Set password later
The password for logging in to the ECS is not configured during the ECS creation.
After the ECS is created, choose More > Reset Password in the Operation column, set a password for the ECS as prompted, and log in to the ECS.
Resetting the Password for Logging In to an ECS on the ECS Console
Table 14 Password complexity requirements Parameter
Requirement
Password
- Consists of 8 to 26 characters.
- Contains at least three of the following character types:
- Uppercase letters
- Lowercase letters
- Digits
- Special characters for Windows: !@$%^-_=+[{()}]:,./?~#*
- Special characters for Linux: !@$%^-_=+[{}]:,./?~#*
- Cannot contain the username or the username spelled backwards.
- Cannot contain more than two consecutive characters in the same sequence as they appear in the username. (This requirement applies only to Windows ECSs.)
- (Optional) Set a password.
This parameter is displayed only when Login Mode is set to Password.
Set Password and Confirm Password by referring to Table 14. The two values entered must be the same.
- (Optional) Set a key pair.
This parameter is displayed only when Login Mode is set to Key pair. You can select an available key pair from the drop-down list or create a key pair by referring to (Recommended) Creating a Key Pair on the Management Console.

If you use an existing key pair, make sure that you have saved the key file locally. Otherwise, logging in to the ECS will fail.
- (Optional) Set Tag.
You can add tags to ECSs.
Tags help you easily identify and manage your ECSs. You can add up to 10 tags to an ECS.
For details, see Overview.

Tags added during ECS creation will also be added to the created EIP and EVS disks (including the system disk and data disks) of the ECS. If the instance uses an existing EIP, the tags will not be added to that EIP.
If your organization has created a tag policy for ECS, you need to add tags for ECS based on the tag policy. If a tag does not comply with the tag rules, the creation may fail. Contact the organization administrator to learn details about the tag policy.
After creating the ECS, you can view the tags on the pages providing details about the ECS, EIP, and EVS disks.
Advanced Settings
- Select Detailed monitoring.
If you select certain public images, it is a good practice to use the host monitoring function. Host monitoring collects ECS OS metrics, such as CPU usage, memory usage, and network status, so that you can use these metrics to monitor resource utilization or locate a fault.
After you enable detailed monitoring, an agent will be installed on the ECS to provide 1-minute fine-grained monitoring of ECS metrics, such as vCPUs, memory, network, disks, and processes.
For details about the monitoring metrics after the agent is installed, see OS Monitoring Metrics Supported by ECSs with the Agent Installed.
- (Optional) Set ECS group.
An ECS group applies the anti-affinity policy to the ECSs in it so that the ECSs are automatically allocated to different hosts. For instructions about how to create an ECS group, see Managing ECS Groups.

An existing ECS attached with a local disk cannot be added to an ECS group. To use ECS group functions, select an ECS group when creating an ECS.
- Add an ECS description.
- Set User Data.
You can inject user data, for example, inject the OS initialization script, to ECSs during ECS creation. During the first startup of the ECSs, the data will be automatically injected.
- As text: allows you to enter the user data in the text box.
- As file: enables the text to automatically inject a script file or other files into a specified directory on an ECS when you create the ECS.
For details, see Injecting User Data.
- Set Agency.
When your ECS resources need to be shared with other accounts, or your ECS is delegated to professional personnel or team for management, the tenant administrator creates an agency in IAM and grants the ECS management permissions to the personnel or team. The delegated account can log in to the cloud system and switch to your account to manage resources. You do not need to share security credentials (such as passwords) with other accounts, ensuring the security of your account.
If you have created an agency in IAM, select the agency from the drop-down list. For more information about agencies, see Account Delegation.
- Set CPU Options.
- To configure hyper-threading for an ECS, select Specify CPU options.
For details about hyper-threading, see Enabling or Disabling Hyper-Threading.
- Set Threads per Core.
This parameter is displayed when Specify CPU options is selected. You can select a parameter value from the drop-down list.
- 1: one thread per core, which means hyper-threading is disabled.
- 2 (default value): two threads per core, which means hyper-threading is enabled.
- To configure hyper-threading for an ECS, select Specify CPU options.
Quantity
- (Optional) Select the required duration for ECSs.
This parameter is displayed only when Billing Mode is set to Yearly/Monthly. The duration can be from 1 month to 1 year.
- (Optional) Set Auto-renew.
This parameter is displayed only when Billing Mode is set to Yearly/Monthly.
You can select Auto-renew to automatically renew yearly/monthly resources when they expire.- Monthly: Your subscription will be automatically renewed each month.
- Yearly: Your subscription will be automatically renewed each year.
For details about auto-renewal, see Auto-Renewal Rules.
- (Optional) Determine whether to select Set scheduled deletion time for Required Duration.
This parameter is displayed only when Billing Mode is set to Pay-per-use or Spot pricing. If you select Set scheduled deletion time and set a time, the ECS will be automatically deleted when the time is reached.

After you set a scheduled deletion time, the system automatically deletes the ECS at the specified time. Back up data in advance.
The scheduled deletion time must be at least 1 hour from the current time but not more than 3 years from now. You can change the scheduled deletion time before the instance is deleted.
The system executes the scheduled deletion task every 5 minutes and stops the billing after the ECS is deleted.
- Set Quantity.
You can set how many ECSs to be created in a batch. ECSs created in the same batch have the same configurations.
The system displays the remaining number of ECSs you are allowed to create. If the number of ECSs you want to create exceeds the quota, increase the quota.

You can set the following at the bottom of the purchase page:
- When Billing Mode is set to Yearly/Monthly, you can set quantity and required duration.
- When Billing Mode is set to Pay-per-use or Spot pricing, you can set quantity.
After the setting is complete, you can hover over the price to view billing items. If you have any questions about the price, click Pricing details to learn more.
Step 3: Confirm the Configuration and Submit the Order
- In the Configuration Summary panel on the right side, confirm the ECS details.
Mandatory fields that are not configured are displayed in red. You need to set them in the parameter configuration area.
- (Optional) Click Save as Launch Template.
Perform this step only when you need to create an ECS using a launch template. For details, see Purchasing ECSs Using Auto Launch Groups.
The configuration cannot be saved as a launch template if the billing mode is yearly/monthly or spot block, host security is enabled, or the login mode is password.
- Read and agree to the agreement, and click Submit.
After the ECS is created, it will be started by default.
- Click back to ECS list. You can view the created ECS on the ECS list page.
Follow-up Procedure
- Resetting the password
If you set Login Mode to Set password later during the ECS creation, you can reset the password after creating the ECS.
For details, see Resetting the Password for Logging In to an ECS on the ECS Console.
- Connecting to an ECS
You can connect to an ECS in multiple ways. For details, see Login Overview (Windows) and Login Overview (Linux).
- Initializing an EVS data disk
If you created a data disk when creating an ECS, initialize the data disk first before using it. For details, see Initializing Data Disks.
- Using an ECS
After purchasing an ECS, you can build environments, websites, or applications on it. For details, see Best Practices Summary.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





