Configuring Roles
Role management in DataArts Security provides more intuitive and powerful permission management capabilities based on permission sets. The difference between a role and a permission set is that a permission set directly associates users with permissions, while a role is created or managed on the data source to carry the association between users and permissions.
If you associate roles with permission sets on the role management page, permissions are synchronized only to roles instead of users. You are advised to use role management to manage permissions and permission relationships more intuitively. Role management also allows you to use managed roles to manage existing data source permissions.
- Common roles: Create roles on the data source to associate users and permissions.
- Manage roles: Manage existing roles on the MRS data source and inherit their permissions of the MRS data source. (To view existing roles on the MRS data source, log in to MRS FusionInsight Manager and choose System > Permission > Role).
This section describes Configuring a Common Role, Configuring Managed Roles, and Related Operations.
Prerequisites
- You have configured a workspace permission set. For details, see Configuring Workspace Permission Sets.
- During the synchronization of MRS and GaussDB(DWS) roles, the system uses the users in the data connections in Management Center to perform addition, deletion, modification, and query operations. Users in the data connections must have the following permissions:
- Users in MRS Ranger connections must have the admin permission of the Ranger component.
- In non-rights separation mode (RSM), database users in GaussDB(DWS) connections must have at least the dbadmin permission of the database. In RSM, users must have the system administrator permissions.
For details about the configuration method, see Checking the Cluster Version and Permissions.
- Metadata of tables has been collected in DataArts Catalog through a metadata collection task if you want to view the metadata of databases, tables, and fields in data connections during permission configuration in fast mode.
Constraints
- Currently, roles can only be created for MRS and GaussDB(DWS) clusters.
- Role management is available only when the version of the CDM cluster selected for the agent in the data connection is 2.10.0.300 or later.
- During the synchronization of MRS and GaussDB(DWS) roles, the system uses the users in the data connections in Management Center to perform addition, deletion, modification, and query operations. Users in the data connections must have the following permissions:
- Users in MRS Ranger connections must have the admin permission of the Ranger component.
- In non-rights separation mode (RSM), database users in GaussDB(DWS) connections must have at least the dbadmin permission of the database. In RSM, users must have the system administrator permissions.
For details about the configuration method, see Checking the Cluster Version and Permissions.
- Workspace permission sets are mainly used to define the permissions of workspaces rather than manage permissions. Roles cannot be created for workspace permission sets. If you create roles for permission sets, permissions are synchronized only to roles instead of users.
- Only the directory permissions of the cluster are displayed for roles in the workspace.
- During authorization, the name of the object to be authorized (database, table, or column name) can contain only digits, letters, underscores (_), hyphens (-), and wildcards (*).
- DWS permission sets can be used to grant permissions of a specified database or schema. The asterisk (*) cannot be used as a wildcard character. Wildcard characters are supported for tables or columns. For example, if you want to grant permissions to all tables in a schema, enter * for the data tables.
- If a DWS permission set is used to grant a user the permissions of all tables in a schema of the DWS data source (that is, the data tables are set to *), the user has permissions on all tables in the schema. Due to the restrictions of DWS permissions, these permissions are applicable only to the current table. This user has no permissions on the tables (future tables) created after permission synchronization. In this case, the administrator must manually synchronize permissions of the role or permission set so that the user has permissions on future tables.
To avoid manually synchronizing the permissions on future tables, you can configure the users for creating future tables in a specified schema. When these users create future tables in the specified schema, all the users that have full table permissions on the schema in the current instance automatically obtain the permissions on the created future tables.
- During permission synchronization, you need to configure required permissions for the dlg_agency. For details, see Authorizing dlg_agency.
- The current data permission control uses the allowlist mechanism, which adds operation conditions to the users to be authorized without affecting the permissions the users already have. If you only want to make the permissions granted by the data permission control take effect, you need to revoke the original permissions of the users to be authorized. For details, see Data Permission Management.
- During script execution and job testing in DataArts Factory, the MRS or DWS data source uses the account of the data connection for authentication by default. Therefore, permission management still does not take effect during data development. You need to enable fine-grained authentication so that the current user is used for authentication during script execution and job testing in DataArts Factory. In this way, different users have different data permissions, and permission management for roles and permission sets takes effect.
Configuring a Common Role
- On the DataArts Studio console, locate a workspace and click DataArts Security.
- In the navigation pane on the left, choose .
- Use either of the following methods to configure a common role:
- Configuring an existing role: On the Role Management page, permission sets that have been created in Creating a Permission Set are displayed in the navigation tree as common roles by default. You can click a role name to go to the role details page.
Figure 1 Role details page

- Creating a role: On the page, click
 in the navigation tree and select Create Common Role. Set the parameters listed in Table 1 and click OK. The details page of the created role is displayed by default.
in the navigation tree and select Create Common Role. Set the parameters listed in Table 1 and click OK. The details page of the created role is displayed by default.
Table 1 Parameters Parameter
Description
*Name
Permission set name, which is unique in the instance.
You should include the meaning of the permission set and avoid meaningless descriptions in the name so that the permission set can be quickly identified.
*Parent Permission Set
Select a parent permission set, which can be a workspace permission set or another permission set. After you select a parent permission set, the permissions of the current permission set are a subset of the parent permission set's permissions.
*Administrator
The administrators are the owners of the permission set and can configure the permissions in the permission set. The administrators can perform the following operations:- Permission configuration: Assign data source permissions to the workspace permission set.
- User configuration: Assign permissions in the workspace permission set to users, user groups, or workspace roles.
- Permission set creation: Create permission sets and roles based on the workspace permission set. The created permission sets do not contain more permissions than the workspace permission set.
Description
Information to make the permission set easier to be identified
Figure 2 Creating a common role
- Configuring an existing role: On the Role Management page, permission sets that have been created in Creating a Permission Set are displayed in the navigation tree as common roles by default. You can click a role name to go to the role details page.
- On the role details page, you can expand the Basic Information area to view the name, ID, and administrator of the role. For details, see Figure 3.
- Data Source Role Configuration: On this page, you can click Create to create roles for associating users and permissions.
Figure 4 Data Source Role Configuration page

Click Create. In the displayed dialog box, select data sources, set Role Name, and click OK.
Figure 5 Creating a data source role
If you no longer need a data source role, click Delete in the Operation column to delete the role. After the role is deleted, permissions are no longer synchronized to the role and only synchronized to user information.
- Permissions: On the role details page, click the Permissions tab. By default, By data is selected. You can also select By permissions. The configured permissions are the same for By data and By permissions, and the only difference lies in how the permissions are displayed. You are advised to select By permissions for batch authorization.
- By data: The system allows you to configure permissions for data. Currently, only MRS data sources are supported. The configured permissions will be automatically synchronized.
Figure 6 Configuring permissions on the By data page

When configuring permissions, you can select Entire DB, Entire table, or Entire column, and select the corresponding levels in the data source information to perform a batch authorization. You can also click Authorization in the Operation column of a data record in the expanded navigation pane to authorize access to the data.
Fast mode and Show data this role has no permission to are supported. If Fast mode is enabled, metadata of databases, tables, and columns is obtained from DataArts Catalog. Otherwise, metadata is obtained from the data source. If metadata has been collected, you are advised to enable Fast mode.
- Note that the permissions of databases, tables, and columns are managed by layer. For example, a user who has been granted database permissions does not have the permissions of tables and columns. Table and column permissions must be granted separately.
For example, if you enter a table name or an asterisk (*) as a wildcard during database authorization, you are authorizing the table. If you enter a column name or an asterisk (*) as a wildcard character, you are authorizing the column.
- During authorization, the name of the object to be authorized (database, table, or column name) can contain only digits, letters, underscores (_), hyphens (-), and wildcards (*).
Figure 7 Authorization on the By data page
- Note that the permissions of databases, tables, and columns are managed by layer. For example, a user who has been granted database permissions does not have the permissions of tables and columns. Table and column permissions must be granted separately.
- By permissions: The system allows you to configure permissions.
After configuring permissions, you can edit, synchronize, or delete them.
Figure 8 Configuring permissions on the By permissions page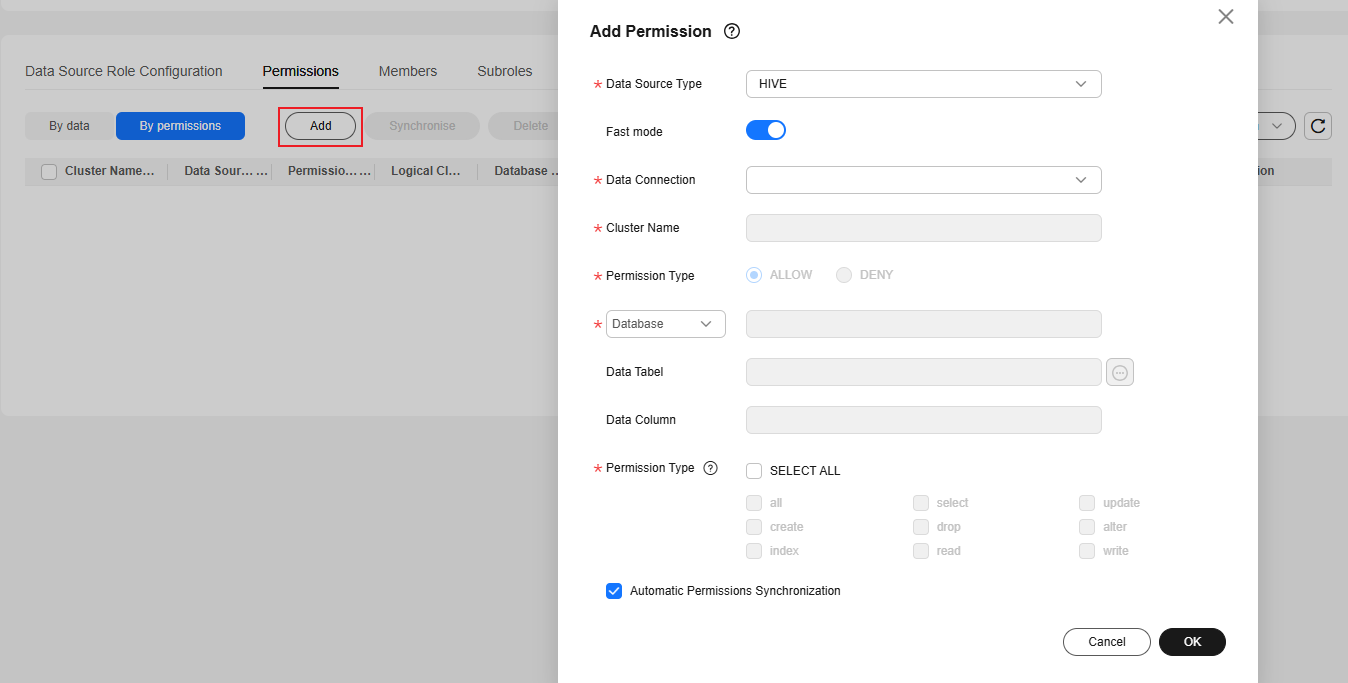
- By data: The system allows you to configure permissions for data. Currently, only MRS data sources are supported. The configured permissions will be automatically synchronized.
- Members: On the role details page, click the Members tab.
Members associate the roles on the Data Source Role Configuration page with users. Click Add to add users, user groups, or workspace roles to roles. You can select users or user groups that have been added to the workspace.
When you add a member, Automatic User Synchronization is selected. The added member will be automatically synchronized. You do not need to synchronize role information manually.
Figure 9 Members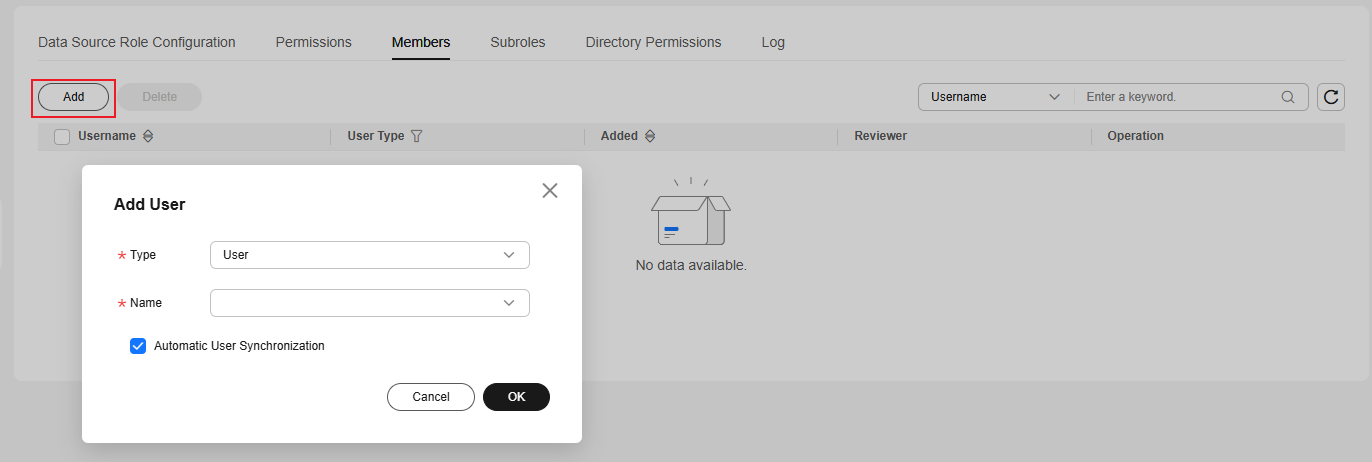
- Subroles: On the role details page, click the Subroles tab.
On this page, you can view the subroles of the current role.Figure 10 Viewing subroles

- Directory Permissions: On the role details page, click the Directory Permissions tab.
Directory permissions obtain the HDFS policies of this role from the Ranger component to display the HDFS paths to which this role has permissions. In addition, you can view the operation permissions of the paths. You can search for the permissions of a path. Only exact match is supported.
Figure 11 Viewing directory permissions
- Log: On the role details page, click the Log tab.
On this page, you can view the log details if permission synchronization fails. The system deletes logs generated 30 days ago at 00:00 every day.Figure 12 Viewing logs

- After the role is configured, it does not take effect immediately. You need to synchronize the permissions and role to the data source for permission management to take effect. For details, see Related Operations.
Configuring Managed Roles
- On the DataArts Studio console, locate a workspace and click DataArts Security.
- In the navigation pane on the left, choose .
- On the page, click
 in the navigation tree and select Create Managed Role. In the displayed dialog box, select a Ranger connection, set Parent Permission Set/Role, and click Manage in the Operation column of the MRS roles to be managed. You can also select multiple MRS roles to be managed and click Manage above the list.
in the navigation tree and select Create Managed Role. In the displayed dialog box, select a Ranger connection, set Parent Permission Set/Role, and click Manage in the Operation column of the MRS roles to be managed. You can also select multiple MRS roles to be managed and click Manage above the list.
If you no longer want to manage roles, you can delete the managed roles from the role management navigation tree. After the managed roles are deleted, permissions are no longer synchronized to the roles and only synchronized to user information.
Figure 13 Creating a managed role
- Close the Manage Role dialog box and return to the page. In the role management navigation tree, locate the MRS role added in the previous step and click the role name to go to the role details page.
- On the role details page, you can expand the Basic Information area to view the name, ID, and administrator of the role. For details, see Figure 14.
- Members: On this page, you can view the users or user groups associated with the MRS role. Currently, users cannot be added to managed roles in DataArts Security.
Figure 15 Members

- Permissions: On the role details page, click the Permissions tab. By default, By data is selected. You can also select By permissions. The configured permissions are the same for By data and By permissions, and the only difference lies in how the permissions are displayed. You are advised to select By permissions for batch authorization.
- By data: The system allows you to configure permissions. If a metadata collection task has been executed successfully, you can view the data source information and click
 to expand the navigation pane.
Figure 16 Configuring permissions on the By data page
to expand the navigation pane.
Figure 16 Configuring permissions on the By data page
When configuring permissions, you can select Entire DB, Entire table, or Entire column, and select the corresponding levels in the data source information to perform a batch authorization. You can also click Authorization in the Operation column of a data record in the expanded navigation pane to authorize access to the data.
Fast mode and Show data this role has no permission to are supported. If Fast mode is enabled, metadata of databases, tables, and columns is obtained from DataArts Catalog. Otherwise, metadata is obtained from the data source. If metadata has been collected, you are advised to enable Fast mode.
- Note that the permissions of databases, tables, and columns are managed by layer. For example, a user who has been granted database permissions does not have the permissions of tables and columns. Table and column permissions must be granted separately.
For example, if you enter a table name or an asterisk (*) as a wildcard during database authorization, you are authorizing the table. If you enter a column name or an asterisk (*) as a wildcard character, you are authorizing the column.
- During authorization, the name of the object to be authorized (database, table, or column name) can contain only digits, letters, underscores (_), hyphens (-), and wildcards (*).
Figure 17 Authorization on the By data page
- Note that the permissions of databases, tables, and columns are managed by layer. For example, a user who has been granted database permissions does not have the permissions of tables and columns. Table and column permissions must be granted separately.
- By permissions: The system allows you to configure permissions.
After configuring permissions, you can edit, synchronize, or delete them.Figure 18 Configuring permissions on the By permissions page
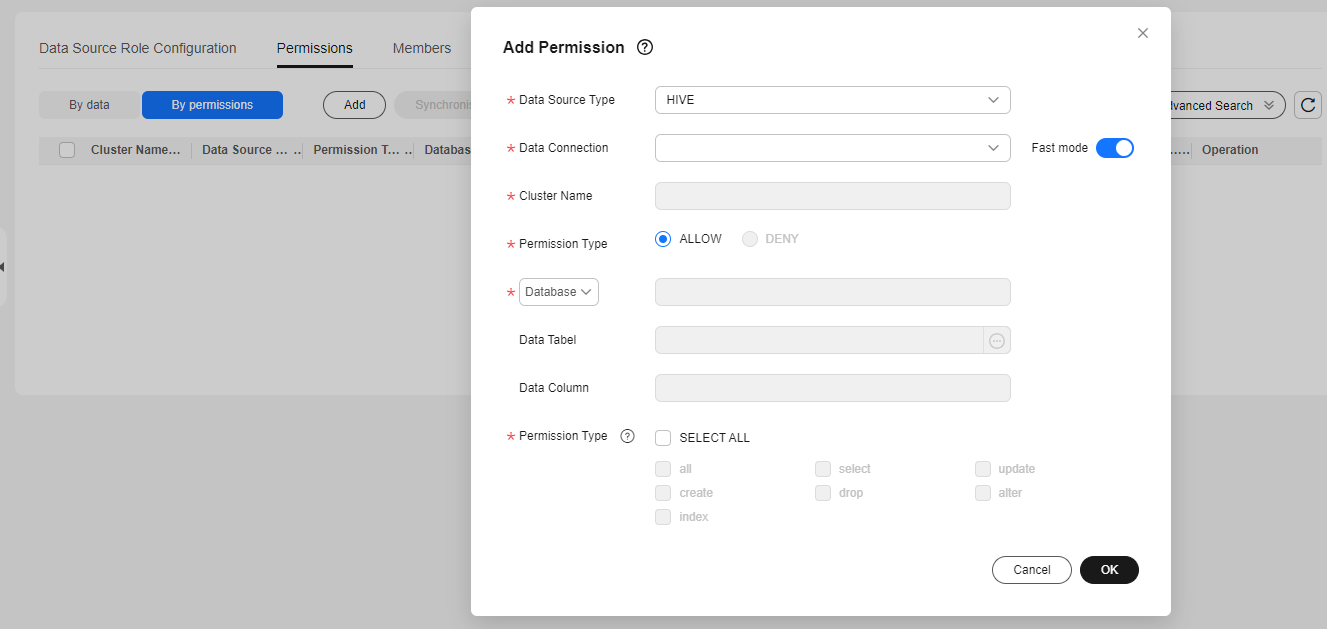
- By data: The system allows you to configure permissions. If a metadata collection task has been executed successfully, you can view the data source information and click
- Directory Permissions: On the role details page, click the Directory Permissions tab.
Directory permissions obtain the HDFS policies of this role from the Ranger component to display the HDFS paths to which this role has permissions. In addition, you can view the operation permissions of the paths. You can search for the permissions of a path. Only exact match is supported.
Figure 19 Viewing directory permissions
- The permissions configured for the managed role do not take effect immediately. You need to manually synchronize the permissions to the Ranger component for permission management to take effect. For details, see Synchronizing Permissions.
Related Operations
- Synchronizing permissions: After configuring data permissions on the Role Management page, you need to synchronize the permissions to the data source for permission management to take effect.
To synchronize permissions, click Synchronize Permissions in the upper right corner of the Basic Information area on the role details page. To synchronize the permissions of multiple roles, select the roles in the role management navigation tree and click
 above the navigation tree.
above the navigation tree. - Synchronizing roles: In common role management (managed roles do not need to be synchronized), after a role is created for a permission set, the role takes effect only after being synchronized to the data source.
To synchronize a role, click Synchronize Role Information in the upper right corner of the Basic Information area or click Synchronize in the Operation column on the Data Source Role Configuration tab page. To synchronize multiple roles, select the roles in the role management navigation tree and click
 above the navigation tree.
above the navigation tree.
- After role synchronization is successful, MRS data source roles are named in Role name_Timestamp format, and the GaussDB(DWS) data source roles are named in dataarts_studio_role_Role name format.
- In scenarios where roles are synchronized to an MRS cluster, after the system prompts a successful role synchronization, permission management takes effect after about five minutes during which the Ranger component automatically synchronizes roles from the MRS cluster. You can check whether the synchronization is complete based on Data Source Role Name on the Data Source Role Configuration tab page.
- Roles that are not synchronized are named in Role name_10-digit timestamp format.
- Roles that have been synchronized are named in Role name_13-digit timestamp format.
- Deleting roles: In the Role Management navigation pane, select roles and click
 above the navigation pane. In the displayed dialog box, confirm the roles to be deleted and click Yes.
Common roles for which roles, permissions, users, or child permission sets have been configured cannot be deleted. To delete such roles, delete the related configurations first. If permissions have been configured for a managed role, the role cannot be deleted. To delete the role, clear related configurations first.
above the navigation pane. In the displayed dialog box, confirm the roles to be deleted and click Yes.
Common roles for which roles, permissions, users, or child permission sets have been configured cannot be deleted. To delete such roles, delete the related configurations first. If permissions have been configured for a managed role, the role cannot be deleted. To delete the role, clear related configurations first.
Deleted common roles are moved to the recycle bin. You can restore them within 30 days. After 30 days, they will be deleted permanently. For details, see Managing the Recycle Bin.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






