Why Does WAF Block Normal Requests as Invalid Requests?
Symptom
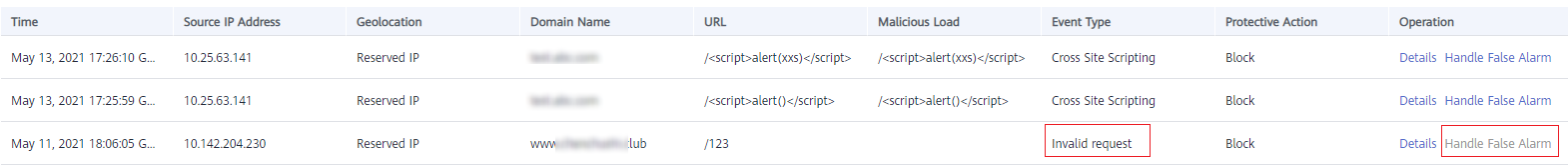
After a website is connected to WAF, a normal access request is blocked by WAF. On the Events page, the corresponding Event Type reads Invalid request, and the Handle False Alarm button is grayed out, as shown in Figure 1.
Possible Cause
- When form-data is used for POST or PUT requests, the number of parameters in a form exceeds 8,192.
- The URL contains more than 2,048 parameters.
- The number of headers exceeds 512.
Solution
If you confirm that a blocked request is a normal request, allow it by referring to Configuring Custom Precise Protection Rules.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot