Before You Start
Overview
Web Application Firewall (WAF) is a tool used to protect web applications. WAF is deployed in front of web applications. It checks HTTP and HTTPS traffic between the Internet and web applications and identifies and blocks web attacks based on predefined protection rules. WAF can defend against many types of attacks, such as SQL injection, cross-site scripting (XSS), web shells, command/code injection, file inclusion, sensitive file access, third-party application vulnerability exploits, CC attacks, malicious crawler scanning, and cross-site request forgery (CSRF). You can use WAF to protect web servers, web applications, and sensitive data.
This document describes how to use application programming interfaces (APIs) to perform operations on WAF, such as querying and updating.
Before you start, ensure that you are familiar with WAF. For details, see Web Application Firewall (WAF).
API Calling
WAF provides Representational State Transfer (REST) APIs, allowing you to use HTTPS requests to call them. For details, see API Calling.
Endpoints
An endpoint is the request address for calling an API. Endpoints vary depending on services and regions. For the endpoints of all services, see Regions and Endpoints.
Concepts
- Account
An account is created upon successful registration with the cloud platform. The account has full access permissions for all of its cloud services and resources. It can be used to reset user passwords and grant user permissions. The account is a payment entity, which should not be used directly to perform routine management. For security purposes, create Identity and Access Management (IAM) users and grant them permissions for routine management.
- User
An IAM user is created using an account to use cloud services. Each IAM user has its own identity credentials (password and access keys).
- Region
Regions are divided based on geographical location and network latency. Public services, such as Elastic Cloud Server (ECS), Elastic Volume Service (EVS), Object Storage Service (OBS), Virtual Private Cloud (VPC), Elastic IP (EIP), and Image Management Service (IMS), are shared within the same region. Regions are classified as universal regions and dedicated regions. A universal region provides universal cloud services for common tenants. A dedicated region provides services of the same type only or for specific tenants.
- Availability zone (AZ)
An availability zone (AZ) contains one or more physical data centers. Each AZ has independent cooling, fire extinguishing, moisture-proof, and electricity facilities. Within an AZ, compute, network, storage, and other resources are logically divided into multiple clusters. AZs within a region are interconnected using high-speed optical fibers to support cross-AZ high-availability systems.
- Project
A project corresponds to a region. Projects group and isolate resources (including compute, storage, and network resources) across physical regions. Users can be granted permissions in a default project to access all resources in the region associated with the project. If you need more fine-grained access control, you can create subprojects under a default project and create resources in subprojects. Then you can assign required permissions for users to access only the resources in specific subprojects.
Figure 1 Project isolation model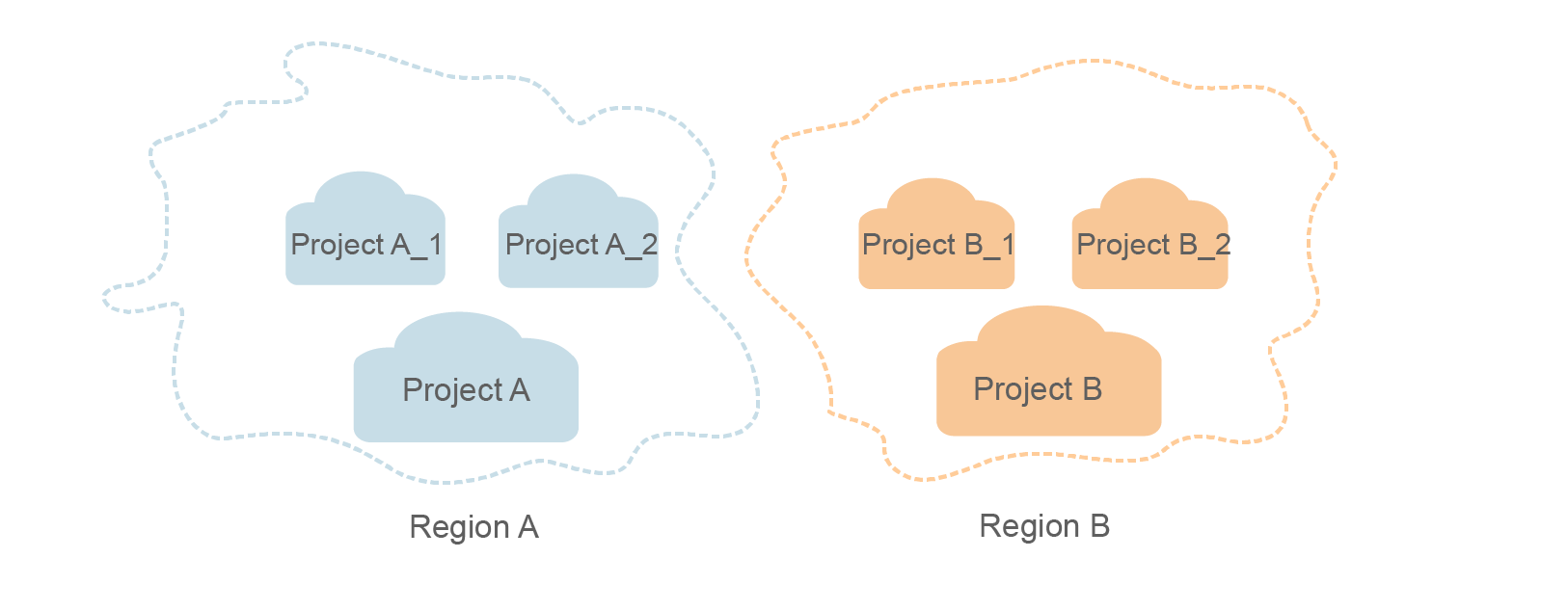
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





