Java Spring Framework Remote Code Execution Vulnerability
Spring Framework is a lightweight open-source application framework for developing enterprise Java applications. A remote code execution (RCE) vulnerability was disclosed in the Spring framework and classified as critical. This vulnerability can be exploited to attack Java applications running on JDK 9 or later versions.
Vulnerability Name
Zero-Day RCE Vulnerability in the Spring Framework
Affected Versions
- JDK 9 or later
- Applications developed using the Spring Framework or derived framework
Mitigation
- Buy a WAF instance .
- Add the website domain name to WAF and connect it to WAF. For details, see Adding a Domain Name to WAF.
- In the Basic Web Protection configuration area, set the protective action to Block and complete the configuration. For details, see Configuring Basic Web Protection Rules.
Figure 1 Basic Web Protection
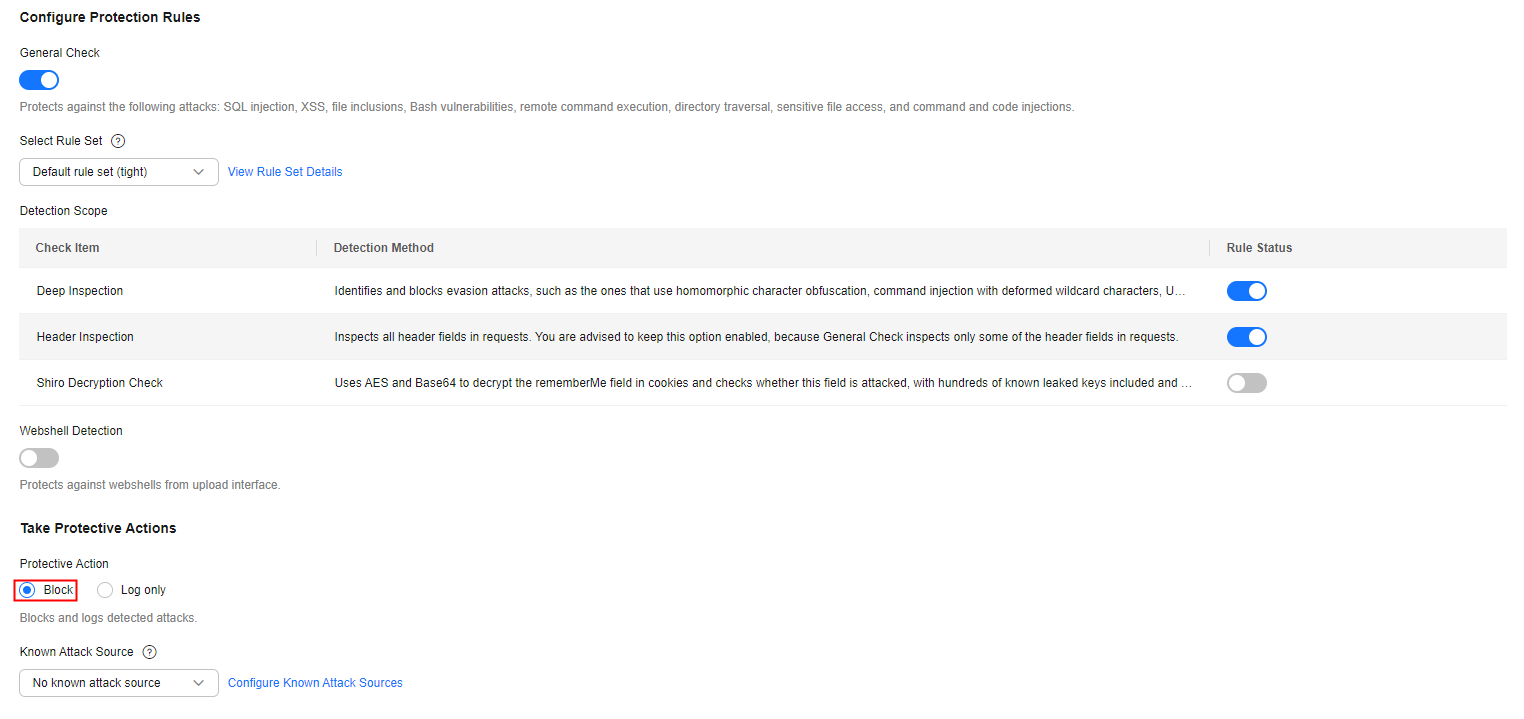

There are two types of malicious payload in this vulnerability. Whether to enable Header Inspection depends on the type of payloads in your services.
- Type 1: Malicious payloads are included in submitted parameters. In this situation, Header Inspection can be disabled.
- Type 2: Malicious payloads are included in a custom header field. In this situation, Header Inspection must be enabled to block attacks.
Type 2 malicious payloads depend on Type 1 malicious payloads so whether to enable Header Inspection is determined by your service requirements.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





