Scenarios
A virtual IP address is a private IP address assigned from a VPC subnet. You can use a virtual IP address and Keepalived to set up a high-availability active/standby web cluster. In such a cluster, if the active ECS goes down, the virtual IP address is bound to the standby ECS to provide services. This section describes how to use a virtual IP address and Keepalived to set up a high-availability web cluster.
Architecture
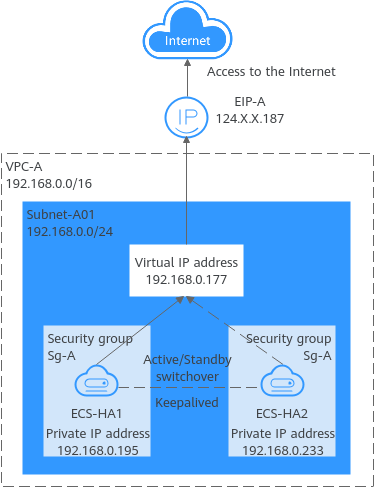
Figure 1 shows a high-availability web cluster using Keepalived. In this architecture, virtual IP address
192.168.0.177 is bound to
ECS-HA1 and
ECS-HA2. To allow
ECS-HA1 and
ECS-HA2 to access and be accessed from the Internet, an EIP (
EIP-A) is bound to the virtual IP address. They work as follows:
- ECS-HA1 works as the active ECS and provides services accessible from the Internet using EIP-A. ECS-HA2 works as the standby ECS, with no services deployed on it.
- If ECS-HA1 goes down, ECS-HA2 takes over services, ensuring service continuity.
Figure 1 A high-availability web cluster using a virtual IP address and Keepalived
Advantages
A high-availability cluster can have one active ECS and one standby ECS or one active ECS and multiple standby ECSs. You can bind a virtual IP address to these ECSs. If the active ECS goes down, the standby ECS becomes the active ECS and continues to provide services.
Notes and Constraints
All servers of the HA cluster must be in the same subnet.
Resource Planning
In this example, the VPC, subnet, virtual IP address, EIP, and ECSs must be in the same region but can be in different AZs.
The following resource details are only for your reference. You can modify them if needed.
Table 1 Resource planning
|
Resource Type |
Quantity |
Description |
|
VPC and subnet |
1 |
- VPC name: Set it as needed. In this example, VPC-A is used.
- VPC IPv4 CIDR block: Set it as needed. In this example, 192.168.0.0/16 is used.
- Subnet name: Set it as needed. In this example, Subnet-A01 is used.
- Subnet IPv4 CIDR block: Set it as needed. In this example, 192.168.0.0/24 is used.
|
|
ECS |
2 |
In this example, two ECSs are required for active/standby switchover. Configure the two ECSs as follows:
- Name: Set this parameter as needed. In this example, the two ECSs are named ECS-HA1 and ECS-HA2.
- Image: Select an image as needed. In this example, a public image (CentOS 7.8 64bit) is used.
- System Disk: General Purpose SSD | 40 GiB
- Data Disk: In this example, no data disk is required. You can attach data disks based on service requirements and ensure data consistency between the two ECSs.
- Network parameters
- VPC: Select a VPC. In this example, VPC-A is used.
- Subnet: Select a subnet. In this example, Subnet-A01 is used.
- Security Group: Select a security group as needed. In this example, ECS-HA1 and ECS-HA2 are associated with the same security group (Sg-A).
- Private IP address: Specify 192.168.0.195 for ECS-HA1 and 192.168.0.233 for ECS-HA2.
|
|
Virtual IP address |
1 |
Assign a virtual IP address from Subnet-A01.
- Assignment Mode: Set it as needed. In this example, Automatic is selected.
- Virtual IP address: 192.168.0.177 is used in this example.
- Instances: Bind 192.168.0.177 to ECS-HA1 and ECS-HA2.
- EIP: Bind 192.168.0.177 to EIP-A.
|
|
EIP |
1 |
- Billing Mode: Select a billing mode as needed. In this example, Pay-per-use is used.
- EIP Name: Set it as needed. In this example, EIP-A is used.
- EIP: The IP address is randomly assigned. In this example, 124.X.X.187 is used.
|
Procedure
You can follow the process in Figure 2 to set up a high-availability web cluster using a virtual IP address and Keepalived
Figure 2 Process for setting up a high-availability web cluster
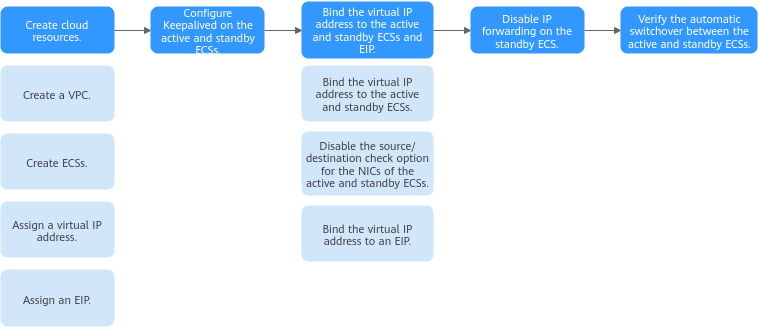
Step 1: Create Cloud Resources
- Create a VPC and subnet.
For details, see Creating a VPC and Subnet.
- Create two ECSs, one as the active ECS and the other as the standby ECS.
For details, see Purchasing an ECS in Custom Config Mode.
Configure the ECSs as follows:
- Network: Select VPC-A and Subnet-A01 you have created.
- Security Group: Create security group Sg-A and add inbound and outbound rules to it. Each security group comes with preset rules. You need to check and modify the rules as required.
Add rules in Table 2 to Sg-A and associate Sg-A with ECS-HA1 and ECS-HA2.
Table 2 Sg-A rules
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|
Inbound |
Allow |
IPv4 |
TCP: 22 |
Source: 0.0.0.0/0 |
Allows remote logins to Linux ECSs over SSH port 22. |
|
Inbound |
Allow |
IPv4 |
TCP: 3389 |
Source: 0.0.0.0/0 |
Allows remote logins to Windows ECSs over RDP port 3389. |
|
Inbound |
Allow |
IPv4 |
TCP: 80 |
Source: 0.0.0.0/0 |
Allows external access to the website deployed on the ECSs over HTTP port 80. |
|
Inbound |
Allow |
IPv4 |
All |
Source: current security group (Sg-A) |
Allows the ECSs in Sg-A to communicate with each other using IPv4 addresses. |
|
Inbound |
Allow |
IPv6 |
All |
Source: current security group (Sg-A) |
Allows the ECSs in sg-A to communicate with each other using IPv6 addresses. |
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows ECSs in Sg-A to access the external networks using IPv4 addresses. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows ECSs in Sg-A to access the external networks using IPv6 addresses. |

In this example, Source is set to 0.0.0.0/0, which allows any external IP address to remotely log in to ECSs in Sg-A. To ensure security, you are advised to set Source to a specific IP address, for example, the IP address of your local PC.
If your ECSs are associated with different security groups, you need to add rules in Table 3 to allow the ECSs in the two security groups to communicate with each other.
Table 3 Rules of security groups Sg-A and Sg-B
|
Security Group |
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|
Sg-A |
Inbound |
Allow |
IPv4 |
All |
Source: Sg-B |
Allows ECSs in Sg-B to access those in Sg-A over any IPv4 protocol and port. |
|
Sg-B |
Inbound |
Allow |
IPv4 |
All |
Source: Sg-A |
Allows ECSs in Sg-A to access those in Sg-B over any IPv4 protocol and port. |
- EIP: Select Not required.
- Assign a virtual IP address from Subnet-A01.
For details, see Assigning a Virtual IP Address.
- Assign an EIP.
For details, see Assigning an EIP.
Step 2: Configure Keepalived on ECS-HA1 and ECS-HA2
- Configure Keepalived on ECS-HA1.
- Bind EIP-A (124.X.X.187) to ECS-HA1.
For details, see Binding an EIP.
- Remotely log in to ECS-HA1.
For details, see How Do I Log In to My ECS?
- Run the following command to install the Nginx and Keepalived packages and related dependency packages:
yum install nginx keepalived -y
If information similar to the following is displayed, the installation is complete:
[root@ecs-ha1 ~]# yum install nginx keepalived -y
Loaded plugins: fastestmirror
Determining fastest mirrors
base | 3.6 kB 00:00:00
epel | 4.3 kB 00:00:00
extras | 2.9 kB 00:00:00
updates | 2.9 kB 00:00:00
(1/7): epel/x86_64/group | 399 kB 00:00:00
(2/7): epel/x86_64/updateinfo | 1.0 MB 00:00:00
(3/7): base/7/x86_64/primary_db | 6.1 MB 00:00:00
(4/7): base/7/x86_64/group_gz | 153 kB 00:00:00
(5/7): epel/x86_64/primary_db | 8.7 MB 00:00:00
(6/7): extras/7/x86_64/primary_db | 253 kB 00:00:00
(7/7): updates/7/x86_64/primary_db
.....
Dependency Installed:
centos-indexhtml.noarch 0:7-9.el7.centos gperftools-libs.x86_64 0:2.6.1-1.el7 lm_sensors-libs.x86_64 0:3.4.0-8.20160601gitf9185e5.el7_9.1
net-snmp-agent-libs.x86_64 1:5.7.2-49.el7_9.4 net-snmp-libs.x86_64 1:5.7.2-49.el7_9.4 nginx-filesystem.noarch 1:1.20.1-10.el7
openssl11-libs.x86_64 1:1.1.1k-7.el7
Complete!
- Modify the Nginx configuration file.
- Run the following command to open the /etc/nginx/nginx.conf file:
vim /etc/nginx/nginx.conf
- Press i to enter the editing mode.
- Replace the original content with the following:
user root;
worker_processes 1;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
#gzip on;
server {
listen 80;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
root html;
index index.html index.htm;
}
#error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
}
- Press ESC to exit and enter :wq! to save the configuration.
- Modify the index.html file to verify whether the website is successfully accessed.
- Run the following command to open the /usr/share/nginx/html/index.html file:
vim /usr/share/nginx/html/index.html
- Press i to enter the editing mode.
- Replace the original content with the following:
Welcome to ECS-HA1
- Press ESC to exit and enter :wq! to save the configuration.
- Run the following commands to set the automatic startup of Nginx upon ECS startup:
systemctl enable nginx
systemctl start nginx.service
Information similar to the following is displayed:
[root@ecs-ha1 ~]# systemctl enable nginx
Created symlink from /etc/systemd/system/multi-user.target.wants/nginx.service to /usr/lib/systemd/system/nginx.service.
[root@ecs-ha1 ~]# systemctl start nginx.service
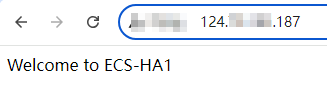
- Open a browser, enter the EIP address (124.X.X.187), and press Enter to verify the access to a single Nginx node.
If the web page shown in the following figure is displayed, Nginx is successfully configured for
ECS-HA1.
Figure 3 ECS-HA1 accessed
- Modify the Keepalived configuration file.
- Run the following command to open the /etc/keepalived/keepalived.conf file:
vim /etc/keepalived/keepalived.conf
- Press i to enter the editing mode.
- Replace the IP parameters in the configuration file as follows:
- mcast_src_ip and unicast_src_ip: Change their values to the private IP address of an ECS. In this example, private IP address 192.168.0.195 of ECS-HA1 is used.
- virtual_ipaddress: Change the value to a virtual IP address. In this example, 192.168.0.177 is used.
! Configuration File for keepalived
global_defs {
router_id master-node
}
vrrp_script chk_http_port {
script "/etc/keepalived/chk_nginx.sh"
interval 2
weight -5
fall 2
rise 1
}
vrrp_instance VI_1 {
state MASTER
interface eth0
mcast_src_ip 192.168.0.195
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
unicast_src_ip 192.168.0.195
virtual_ipaddress {
192.168.0.177
}
track_script {
chk_http_port
}
}
- Press ESC to exit and enter :wq! to save the configuration.
- Configure the Nginx monitoring script.
- Run the following command to open the /etc/keepalived/chk_nginx.sh file:
vim /etc/keepalived/chk_nginx.sh
- Press i to enter the editing mode.
- Replace the original content with the following:
#!/bin/bash
counter=$(ps -C nginx --no-heading|wc -l)
if [ "${counter}" = "0" ]; then
systemctl start nginx.service
sleep 2
counter=$(ps -C nginx --no-heading|wc -l)
if [ "${counter}" = "0" ]; then
systemctl stop keepalived.service
fi
fi
- Press ESC to exit and enter :wq! to save the configuration.
- Run the following command to assign execute permissions to the chk_nginx.sh file:
chmod +x /etc/keepalived/chk_nginx.sh
- Run the following commands to set the automatic startup of Keepalived upon ECS startup:
systemctl enable keepalived
systemctl start keepalived.service
- Unbind EIP-A from ECS-HA1.
For details, see Unbinding an EIP.
- Configure Keepalived on ECS-HA2.
- Bind EIP-A (124.X.X.187) to ECS-HA2.
For details, see Binding an EIP.
- Remotely log in to ECS-HA2.
For details, see How Do I Log In to My ECS?
- Run the following command to install the Nginx and Keepalived packages and related dependency packages:
yum install nginx keepalived -y
If information similar to the following is displayed, the installation is complete:
[root@ecs-ha2 ~]# yum install nginx keepalived -y
Loaded plugins: fastestmirror
Determining fastest mirrors
base | 3.6 kB 00:00:00
epel | 4.3 kB 00:00:00
extras | 2.9 kB 00:00:00
updates | 2.9 kB 00:00:00
(1/7): epel/x86_64/group | 399 kB 00:00:00
(2/7): epel/x86_64/updateinfo | 1.0 MB 00:00:00
(3/7): base/7/x86_64/primary_db | 6.1 MB 00:00:00
(4/7): base/7/x86_64/group_gz | 153 kB 00:00:00
(5/7): epel/x86_64/primary_db | 8.7 MB 00:00:00
(6/7): extras/7/x86_64/primary_db | 253 kB 00:00:00
(7/7): updates/7/x86_64/primary_db
.....
Dependency Installed:
centos-indexhtml.noarch 0:7-9.el7.centos gperftools-libs.x86_64 0:2.6.1-1.el7 lm_sensors-libs.x86_64 0:3.4.0-8.20160601gitf9185e5.el7_9.1
net-snmp-agent-libs.x86_64 1:5.7.2-49.el7_9.4 net-snmp-libs.x86_64 1:5.7.2-49.el7_9.4 nginx-filesystem.noarch 1:1.20.1-10.el7
openssl11-libs.x86_64 1:1.1.1k-7.el7
Complete!
- Modify the Nginx configuration file.
- Run the following command to open the /etc/nginx/nginx.conf file:
vim /etc/nginx/nginx.conf
- Press i to enter the editing mode.
- Replace the original content with the following:
user root;
worker_processes 1;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
#gzip on;
server {
listen 80;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
root html;
index index.html index.htm;
}
#error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
}
- Press ESC to exit and enter :wq! to save the configuration.
- Modify the index.html file to verify whether the website is successfully accessed.
- Run the following command to open the /usr/share/nginx/html/index.html file:
vim /usr/share/nginx/html/index.html
- Press i to enter the editing mode.
- Replace the original content with the following:
Welcome to ECS-HA2
- Press ESC to exit and enter :wq! to save the configuration.
- Run the following commands to set the automatic startup of Nginx upon ECS startup:
systemctl enable nginx
systemctl start nginx.service
Information similar to the following is displayed:
[root@ecs-ha2 ~]# systemctl enable nginx
Created symlink from /etc/systemd/system/multi-user.target.wants/nginx.service to /usr/lib/systemd/system/nginx.service.
[root@ecs-ha2 ~]# systemctl start nginx.service
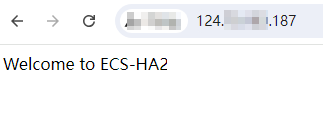
- Open a browser, enter the EIP address (124.X.X.187), and press Enter to verify the access to a single Nginx node.
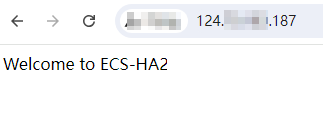
If the web page shown in the following figure is displayed, Nginx is successfully configured for
ECS-HA2.
Figure 4 ECS-HA2 accessed
- Modify the Keepalived configuration file.
- Run the following command to open the /etc/keepalived/keepalived.conf file:
vim /etc/keepalived/keepalived.conf
- Press i to enter the editing mode.
- Replace the IP parameters in the configuration file as follows:
- mcast_src_ip and unicast_src_ip: Change their values to the private IP address of an ECS. In this example, private IP address of ECS-HA2 (192.168.0.233) is used.
- virtual_ipaddress: Change the value to a virtual IP address. In this example, 192.168.0.177 is used.
! Configuration File for keepalived
global_defs {
router_id master-node
}
vrrp_script chk_http_port {
script "/etc/keepalived/chk_nginx.sh"
interval 2
weight -5
fall 2
rise 1
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
mcast_src_ip 192.168.0.233
virtual_router_id 51
priority 90
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
unicast_src_ip 192.168.0.233
virtual_ipaddress {
192.168.0.177
}
track_script {
chk_http_port
}
}
- Press ESC to exit and enter :wq! to save the configuration.
- Configure the Nginx monitoring script.
- Run the following command to open the /etc/keepalived/chk_nginx.sh file:
vim /etc/keepalived/chk_nginx.sh
- Press i to enter the editing mode.
- Replace the original content with the following:
#!/bin/bash
counter=$(ps -C nginx --no-heading|wc -l)
if [ "${counter}" = "0" ]; then
systemctl start nginx.service
sleep 2
counter=$(ps -C nginx --no-heading|wc -l)
if [ "${counter}" = "0" ]; then
systemctl stop keepalived.service
fi
fi
- Press ESC to exit and enter :wq! to save the configuration.
- Run the following command to assign execute permissions to the chk_nginx.sh file:
chmod +x /etc/keepalived/chk_nginx.sh
- Run the following commands to set the automatic startup of Keepalived upon ECS startup:
systemctl enable keepalived
systemctl start keepalived.service
- Unbind EIP-A from ECS-HA2.
For details, see Unbinding an EIP.
Step 3: Bind the Virtual IP Address to the Active and Standby ECSs and EIP
- Bind virtual IP address 192.168.0.177 to ECS-HA1 and ECS-HA2.
For details, see Binding a Virtual IP Address to an Instance or EIP.
- Disable Source/Destination Check for the network interfaces of the active and standby ECSs.
When you bind a virtual IP address to an ECS,
Source/Destination Check is disabled by default. You can perform the following operations to check whether the function is disabled. If the function is not disabled, disable it.
- In the ECS list, click the name of the target ECS.
The ECS details page is displayed.
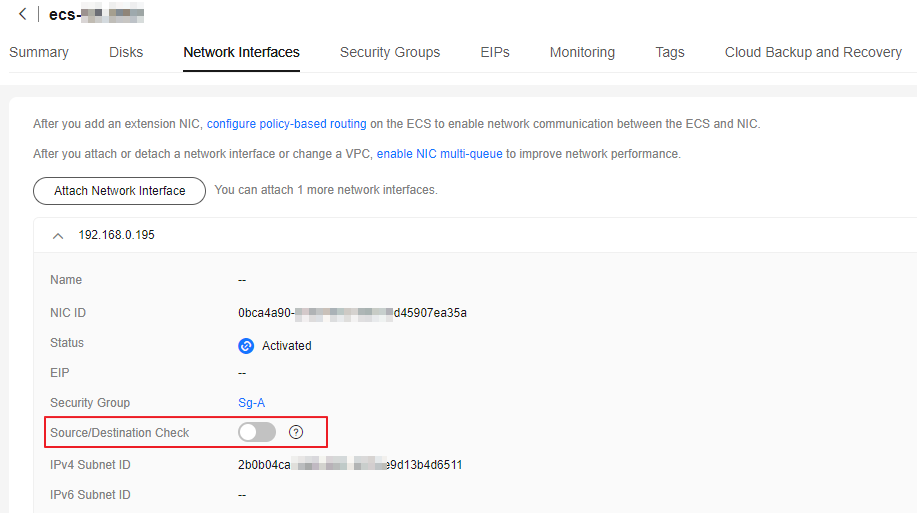
- On the Network Interfaces tab, click
 to expand the details area and check whether Source/Destination Check is disabled.
to expand the details area and check whether Source/Destination Check is disabled.
If the information shown in Figure 5 is displayed, Source/Destination Check is disabled.
Figure 5 Disabling Source/Destination Check
- Bind virtual IP address 192.168.0.177 to EIP-A.
For details, see Binding a Virtual IP Address to an Instance or EIP.
Step 4: Disable IP Forwarding on the Standby ECS
If a virtual IP address is bound to active/standby ECSs, you need to disable IP forwarding on the standby ECS. If an active/standby ECS switchover happens, ensure that IP forwarding of the new standby ECS is also disabled.
To make sure you do not miss any settings, it is better to disable IP forwarding on both of active and standby ECSs.
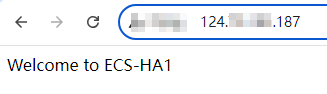
- Open a browser, enter the EIP address (124.X.X.187), and press Enter to access the active ECS.
If the following page is displayed, the
ECS-HA1 is used as the active ECS.
Figure 6 The active ECS accessed
- Remotely log in to the standby ECS (ECS-HA2 in this example).
For details, see How Do I Log In to My ECS?
- Disable IP forwarding by following the operations in Table 4. In this example, the ECS runs the Linux OS.
Table 4 Disabling IP forwarding
|
OS |
Operations |
|
Linux |
- Run the following command to switch to user root:
su root
- Run the following command to check whether IP forwarding is enabled:
cat /proc/sys/net/ipv4/ip_forward
In the command output, 1 indicates that IP forwarding is enabled, and 0 indicates that IP forwarding is disabled. The default value is 0.
- If 0 is displayed, no further action is required.
- If 1 is displayed, go to the next step.
- Use either of the following methods to modify the configuration file:
Method 1
- Run the following command to open the /etc/sysctl.conf file:
vim /etc/sysctl.conf
- Press i to enter the editing mode.
- Set net.ipv4.ip_forward to 0.
- Press ESC to exit and enter :wq! to save the configuration.
Method 2
Run the sed command. An example command is as follows:
sed -i '/net.ipv4.ip_forward/s/1/0/g' /etc/sysctl.conf
- Run the following command to apply the modification:
sysctl -p /etc/sysctl.conf
|
|
Windows |
- In the search box, enter cmd to open the command prompt window, and run the following command:
ipconfig/all
- In the command output, if the value of IP Routing Enabled is No, IP forwarding is disabled.
- If IP Routing Enabled is Yes, IP forwarding is not disabled. Go to the next step.
- Enter regedit in the search box to open the registry editor.
- Set the value of IPEnableRouter under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters to 0.
- If the value is set to 0, IP forwarding will be disabled.
- If the value is set to 1, IP forwarding will be enabled.
|
Step 5: Verify the Automatic Switchover Between the Active and Standby ECSs
- Restart the active and standby ECSs.
- Remotely log in to ECS-HA1.
For details, see How Do I Log In to My ECS?
- Run the following command to restart ECS-HA1:
reboot
- Repeat 1.a to 1.b to restart ECS-HA2.
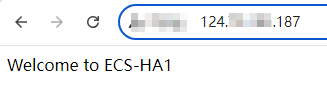
- Check whether the website on the active ECS can be accessed.
- Open a browser, enter the EIP address (124.X.X.187), and press Enter.
If the following page is displayed,
ECS-HA1 is used as the active ECS and the website can be accessed.
Figure 7 ECS-HA1 accessed
- Remotely log in to ECS-HA1 and run the following command to check whether the virtual IP address is bound to the network interface (eth0) of ECS-HA1:
ip addr show
If information similar to the following is displayed, the virtual IP address (
192.168.0.177) has been bound to the network interface (eth0) of
ECS-HA1, and this ECS is the active one.
[root@ecs-ha1 ~]# ip addr show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether fa:16:3e:fe:56:19 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.195/24 brd 192.168.0.255 scope global noprefixroute dynamic eth0
valid_lft 107898685sec preferred_lft 107898685sec
inet 192.168.0.177/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::f816:3eff:fefe:5619/64 scope link
valid_lft forever preferred_lft forever
- Run the following command to disable Keepalived on ECS-HA1:
systemctl stop keepalived.service
- Check whether ECS-HA2 becomes the active ECS.
- Remotely log in to ECS-HA2 and run the following command to check whether the virtual IP address is bound to the network interface (eth0) of ECS-HA2:
ip addr show
If information similar to the following is displayed, the virtual IP address (
192.168.0.177) has been bound to the network interface (eth0) of
ECS-HA2, and this ECS becomes the active one.
[root@ecs-ha2 ~]# ip addr show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether fa:16:3e:fe:56:3f brd ff:ff:ff:ff:ff:ff
inet 192.168.0.233/24 brd 192.168.0.255 scope global noprefixroute dynamic eth0
valid_lft 107898091sec preferred_lft 107898091sec
inet 192.168.0.177/32 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::f816:3eff:fefe:563f/64 scope link
valid_lft forever preferred_lft forever
- Open a browser, enter the EIP address (124.X.X.187), and press Enter to check whether the website on the active ECS (ECS-HA2) can be accessed.
If the following page is displayed,
ECS-HA2 is used as the active ECS and the website can be accessed.
Figure 8 ECS-HA2 accessed