Function Overview
-
Workspace
-
Workspace is a desktop service based on cloud computing. Unlike conventional PCs and VDIs, Workspace enables enterprises to quickly build office environments without investing a large amount of money and spending days in deployment.
Workspace supports multiple login modes, allowing you to flexibly access files and use applications for mobile office. With Direct Connect, you can freely use applications on your enterprise network.
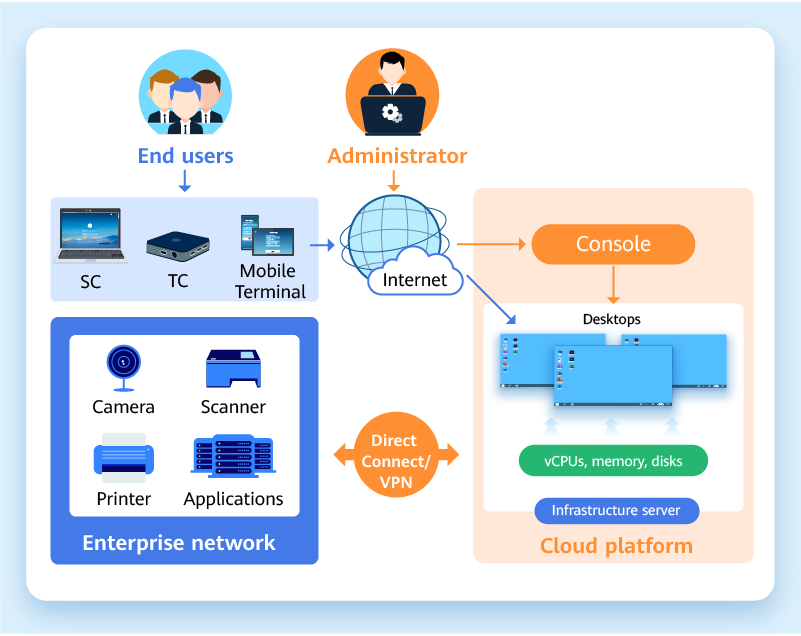
-
-
Purchase Desktops
-
If you plan to purchase a batch of cloud desktops for individuals or enterprise employees, you can log in to the console using an account that has passed real-name authentication and purchase desktops as required.
Workspace supports the creation of common Windows desktops. A Windows desktop is a desktop created by Workspace using an image generated by Windows OS software.

-
-
Desktop Overview
-
An administrator can view the desktop usage in their region to handle faults or adjust resources in a timely manner for lower costs.
- Viewing the login status: An administrator can view the data of running, stopped, and faulty desktops in their region.

- Viewing the login status: An administrator can view the data of desktops that are in use, offline, ready, disconnected, or cannot be connected in their region.
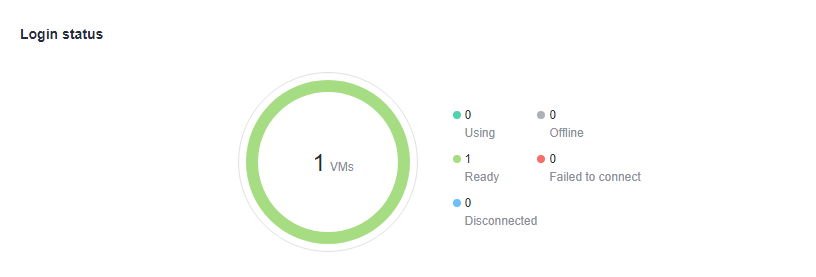
- Viewing the number of online users: An administrator can view the number of online users in a specified period.

-
-
Desktop Management
-
An administrator can perform operations on desktops in their region such as stopping, starting, restarting, deleting, and renaming desktops, changing users, and viewing desktop specifications and usage.
When cloud desktop disks cannot meet service requirements, administrators can add disks or expand disk capacity.
When user desktop specifications and billing modes cannot meet service requirements, administrators can modify them as required.
-
Starting, stopping, restarting, deleting, and renaming desktops
-
Administrators can start, stop, restart, and delete desktops, and can also change desktop names to match desktops with their users or hide key information.
- Administrators can shut down idle desktops during off-peak hours and start the desktops again when they are needed.
- When frame freezing occurs on a desktop, the administrator can restart the desktop for maintenance.
- When a desktop is no longer used, the administrator can delete the desktop to save resources.
- When a desktop is used in a specific scenario and key information needs to be hidden, or a desktop needs to be accurately matched with the user, the administrator can rename the desktop after creating it.
- Administrators can shut down idle desktops during off-peak hours and start the desktops again when they are needed.
-
-
Viewing Desktops That Fail to Be Created
-
If a desktop creation failure message is displayed during desktop purchase, the administrator can view the failure cause. It is easy to understand the cause and provide feedback.
-
-
Disk
-
When desktop disks cannot meet service requirements, administrators can add disks or expand disk capacity.
- Administrators can add data disks with the required capacity. A maximum of 10 data disks can be created on Workspace.
- Administrators can expand the capacity of specific disks (including system disks and data disks) based on the existing disk capacity of the desktop and service requirements.
You can restore a desktop to the initial template by recomposing the system disk, which does not affect the data on the data disk.
-
-
Modifying configurations
-
If the desktop specifications (vCPUs and memory) cannot meet service requirements, administrators can modify the specifications.
- Desktops in Yearly/Monthly Mode:
- You can increase the cloud desktop specifications as required. For example, if the current desktop specification is 8 vCPUs and 16 GB memory, you can change the specification to 8 vCPUs and 32 GB memory.
- Desktops in Pay-per-use Mode:
- You can increase or decrease the cloud desktop specifications as required. For example, if the current desktop specification is 8 vCPUs and 16 GB memory, you can change the specification to 8 vCPUs and 32 GB memory or a specification lower than 8 vCPUs and 16 GB memory, such as 4 vCPUs and 8 GB memory.
If the validity period of a pay-per-use desktop needs to be changed to a periodic one, you can change the desktop billing mode to yearly/monthly.
- Desktops in Yearly/Monthly Mode:
-
-
Changing a User
-
If a user stops using a desktop, you can assign the desktop to a new user to save resources.
-
-
-
User Management
-
An administrator can perform operations on desktop users in their region, such as modifying user information, resetting user passwords, resending notification emails, unlocking and deleting users.
-
Modifying user information
-
- If a user wants to use the new email address to receive desktop login information, the user can contact the administrator to change the email address. After the administrator resends the notification email, the user can receive the desktop login information in the new email address.
- For common accounts that have low security requirements, the administrator can change the settings so that users cannot change their passwords and that their passwords never expire.
- For employees of temporary OA, the administrator can set the expiration time for their accounts or disable their accounts in a timely manner to prevent unnecessary information leakage.
-
-
Resetting a User Password
-
You can reset the password on your own or by contacting the administrator. This operation varies depending on whether the AD is connected.
- When the AD is connected:
If a user loses or forgets the login password, the user needs to contact the administrator. The administrator resets the password for the user on the AD server and notifies the user of the new password.
- When the AD is not connected:
- If a user loses or forgets the login password, the user needs to contact the administrator. After the administrator handles the issue on the Workspace console, the user receives a password resetting email. The user can click the link in the email to change the password.
- If a user loses or forgets the login password, the user can reset the password on the client login page. If the password has expired, reset the password as prompted during login. If the password has not expired, click Forgot Password on the login page, request for changing the password as prompted, and change the password in the link in the received password resetting email.
-
-
Unlocking a user
-
If an account is locked due to consecutive incorrect password inputs, you can contact the administrator to unlock the account on the console. If an existing AD domain of an enterprise is used, unlock the account on the AD server.
-
-
Deleting a user
-
If a user desktop has been deleted, the administrator can delete the user on the User Management page.
-
-
-
Policy Management
-
Desktop policies include the protocol policy and access policy.
- A protocol policy is a set of security rules used to control peripheral access permissions and data transmission between user terminals and cloud desktops.
A protocol policy is a set of security rules used to control peripheral access permissions and data transmission between user terminals and cloud desktops.
- An access policy is a security rule used to determine whether a user can access the Internet.
The administrator can use access policies to determine the access mode (access from the Internet or through Direct Connect) for users to access cloud desktops.
-
Protocol Policy
-
- Workspace has created data transmission and peripheral access policies for purchased desktops in common office scenarios. If different users have different requirements on data transmission and peripheral access, the administrator can create policies that meet specific office requirements.
- When the requirements for data transmission and peripheral access permissions change, administrators can modify existing policies, or delete existing policies and create new ones. Only user-defined policies can be deleted. Default policies cannot be deleted. The priority, name, target object, parameter settings, and description of a user-defined policy can be modified. For default policies, only the parameter settings can be modified.
- The administrator creates workspaces in multiple areas. The policy configuration of each workspace must be the same. The administrator can export the policies in the area where the policies have been configured and import the policies to the target area to quickly configure desktop policies in different areas.
-
-
Access Policy
-
The administrator can create access policies to determine the access mode (access from the Internet or through Direct Connect) for users to access cloud desktops.
-
-
-
User Login Records
-
User login records include information such as the desktop login time, desktop name, username, terminal OS, and terminal IP address. The information helps administrators learn about the desktop operating status and user login status, facilitating fault locating and system maintenance.
Administrators can filter required information based on the login time and login user and export the information to the local PC.
-
-
Tenant Configuration
-
The administrator can maintain the enterprise ID and network access.
-
Modifying an access network
-
Workspace can be accessed through Internet access or Direct Connect. Administrators can select a network access mode as required.
By default, the Internet access mode is used to access desktops. You can enable Direct Connect or switch to Direct Connect.
If ports 443 and 8443 are disabled and desktops cannot be accessed through the Internet, administrators can switch to other ports that are not disabled according to the network plan.
-
-
Modifying a service subnet
-
If the selected service subnet cannot meet service requirements, the administrator can create a service subnet in the VPC service and switch to the new service subnet in the tenant configuration of Workspace.
-
-
Changing the Service Status
-
After the administrator subscribes to the service, if no desktop exists in the current project (without sub-projects) or sub-project for more than 14 days, the system automatically locks the service status. You can create desktops and users only after the administrator reactivates the service status of the project or sub-project.
-
-
-
User AD Domain Authentication
-
Workspace supports user authentication using the account authentication system of the cloud platform or the AD domain of the user.
Before purchasing desktops, you can configure information about connecting to the AD domain on the Tenant Configuration page.
You can choose whether to connect to the AD domain when creating a desktop. After a desktop is created, the choice cannot be modified.
-
-
Multi-Factor Authentication
-
In addition to the username and password for the first identity authentication, multi-factor authentication can be enabled. When a user logs in to the desktop, the user is required to provide a verification code for the second identity authentication, which enhances desktop security. Workspace supports the cloud platform's authentication system (verification codes are generated by virtual MFA devices on the cloud platform) or enterprise's authentication system (verification codes are generated by enterprise's own devices). If the cloud platform's authentication system is used, you need to bind a virtual MFA device upon the first login. If the enterprise's authentication system is used, no device needs to be bound.
-
-
Desktop Login Modes
-
Workspace allows end users to log in to desktops using software clients (SCs), thin clients (TCs) and mobile clients.
- An SC is a Workspace client installed on a local PC so that users can access desktops from the PC. Clients can be installed on Windows 10 PCs to access desktops. If you have a PC that meets the OS requirements, you can use this method for login.
- Thin client (TC) is a small-sized commercial PC designed based on the PC industry standard. The Workspace client is installed on the PC to access the desktop. You can use this method to log in from a TC that meets the requirements.
- A mobile terminal is a Workspace client installed on a mobile device so that users can access the desktop through the mobile device. The mobile device is called a mobile terminal. Currently, only Android smart devices are supported.
-
-
Multi-screen Display
-
Workspace supports multi-monitor display of PC desktops. If you need to use multiple screens to display office content, you can log in to the cloud desktop from a PC connected to multiple monitors that support adaptive display.
Currently, a Windows device supports display on a maximum of four monitors, and a non-Windows device supports display on a maximum of two monitors.
-
-
Private Image Management
-
You can create desktops using Windows private images created through either of the following two methods.
- You can use one-click image conversion to convert a desktop created using a Windows image to a private image.
- You can also obtain an official ISO image file from an official channel and register it as a private image in IMS, create and configure an ECS, and convert the ECS into a private desktop image.
-
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






