Creating an Advanced Policy
Scenarios
General policies can meet daily office requirements. You can customize advanced policies for special scenarios.
Prerequisites
You have purchased a desktop.
Procedure
- Log in to the console.
- Choose Policies > Protocol Policies. The Protocol Policies page is displayed.
- Click Create Policy.
- Enter the policy name and description.

- The policy name can contain up to 55 characters in digits, letters, and underscores (_).
- The description can contain up to 255 characters.
- Select a creation mode as required.
- Create without template: Create a policy using the default blank template.
- Create with template: Create a policy using an existing policy template, whose configuration items will be used by default.

You can select an existing policy template or add a custom template.
The system provides four policy templates to help you quickly configure desktop policies in four different scenarios.
- In security scenarios, Huawei Delivery Protocol (HDP) prevents data in a desktop from being transferred to or even stored on personal storage devices and ensures that data is stored only in an on-premises data center.
- In gaming scenarios, cursor follow-up and image display are optimized to ensure smoothness even in poor bandwidth conditions.
- In graphics processing scenarios, the display frame rate can be adjusted to improve the display quality and the cursor follow-up mode can be adjusted to narrow the gap between the cursor and the image and reduce the visual difference.
- In video editing scenarios, video acceleration is used to optimize video playback quality. The cursor closely follows user operations, improving user experience.
- Use existing policy: If a policy group has been created, you can import a policy from the existing policy group. The configuration items of the selected policy will be used by default.
- Click Next: Configure Policy. The General Policy Configuration page is displayed.
- On the General Policy Configuration page, click Advanced Policies to go to the Advanced Policies page.
- Configure an advanced policy, as shown in Figure 1.
For details about how to configure an advanced policy, see Table 1.
Table 1 Advanced policy list Policy Name
Description
You can configure policies for the redirection of USB ports, devices, printers, and cameras.
You can configure policies for the redirection of audio, audio playback, and audio recording.
You can configure policies for automatic reconnection interval, waiting time before automatic monitor shutdown after screen locking, screenshot prevention, and IP address access control.
You can configure policies for the display level, display frame rate, and video frame rate.
You can configure policies for file redirection and clipboard redirection.
You can configure policies for automatic screen locking, self-service maintenance, and disconnection after screen locking.
You can configure policies for watermark content, display settings, and display mode.
You can configure policies for general audio/video bypass.
You can configure policies for virtual channel control.
You can configure policies related to computer mouse devices, such as feedback and simulation mode.
You can configure policies related to screen recording, such as screen recording type, frame rate, and resolution.
- Configure required policies and click Next: Select Target Object.
- Select an object type as required and then select an object.
- Click Next: Finish. The policy has been created and will take effect upon the next login to the desktop.

 indicates that the policy is enabled.
indicates that the policy is enabled. indicates that the policy is disabled.
indicates that the policy is disabled.
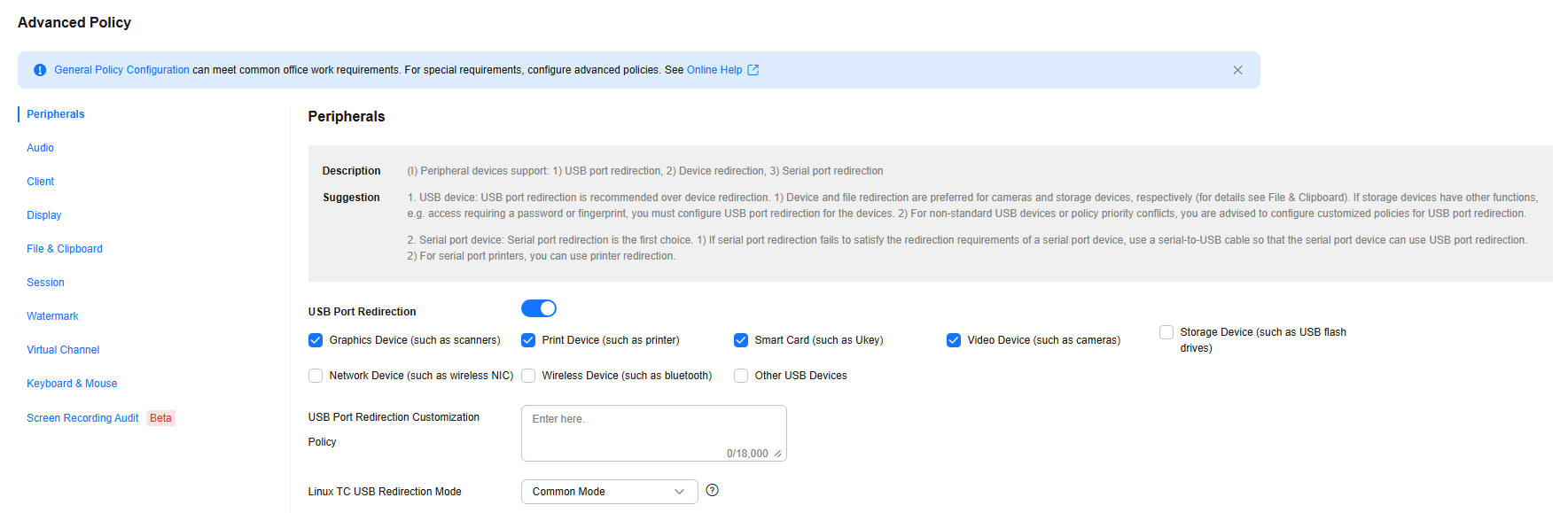
Peripherals

- A peripheral may support:
- USB port redirection
- Device redirection
- Serial port redirection
- USB devices: USB port redirection is recommended over device redirection.
- Device redirection is recommended for cameras, and file redirection for storage devices (see Files and Clipboards). If a storage device has other functions, such as password- or fingerprint-based access, you must configure USB port redirection for the device.
- For non-standard USB devices or policy priority conflicts, you are advised to customize policies for USB port redirection.
- Serial port devices: Serial port redirection is preferred.
- If serial port redirection fails to satisfy the redirection requirements of a serial port device, use a serial-to-USB cable so that the serial port device can use USB port redirection.
- For serial port printers, you can use printer redirection.
Audio
|
Type |
Parameter |
Description |
Example Value |
|---|---|---|---|
|
Audio Redirection |
Audio redirection switch |
Applications on user desktops can use audio devices on terminals to record and play audio. |
|
|
Playback Redirection |
Playback redirection switch |
This parameter takes effect only after audio redirection is enabled. The playback switch is controlled separately.
|
|
|
Playback Scenario |
|
Music playback |
|
|
Recording Redirection |
Recording redirection switch |
This policy takes effect only after audio redirection is enabled. The recording switch is controlled separately.
|
|
|
Recording Scenario |
|
Voice call |
Clients
|
Parameter |
Description |
Example Value |
|---|---|---|
|
Auto Reconnection Interval (s) |
Specifies the interval at which the client attempts to connect to the server after the client is disconnected abnormally. The value ranges from 0 to 50. |
5 |
|
Session Persistence Time (s) |
Specifies the longest duration allowed for automatic reconnection attempts after the client is disconnected abnormally. The value ranges from 0 to 180. |
180 |
|
Auto Monitor Shutdown After Screen Locking |
|
|
|
Auto Monitor Shutdown In (s) |
This parameter is valid only when Auto Monitor Shutdown After Screen Locking is enabled. This parameter specifies the waiting time before the local monitor is automatically shut down after the VM screen is locked. The value range is 10–600,000 seconds. |
300 |
|
Screenshot Prevention Policy |
After the policy is enabled, users are prevented from saving and sharing screenshots captured on cloud desktops.
NOTE:
|
|
|
IP Address Access Control |
By default, this parameter is left blank, indicating that all clients can access the desktop. After the IP address of a client is specified, only the specified client can access the desktop. You need to enter a valid IP address and subnet mask for IP address-based access control. The IP address and subnet mask are separated by a vertical bar (|). If there are multiple IP addresses and subnet masks, separate them with semicolons (;), for example, IP address|Mask;IP address|Mask;IP address|Mask. |
192.168.0.1|255.255.255.255 |
|
Verification of Terminals Added to a Domain |
You can configure a policy to control terminal access to desktops. After the policy is enabled, only terminals that are added to the company's domain can access desktops.
|
|
|
Terminal Login Control |
You can configure a policy to control terminal access to desktops.
|
|
Display
|
Type |
Parameter |
Description |
Example Value |
|---|---|---|---|
|
Display |
Display Policy Level |
|
Level 4 (recommended) |
|
Display Frame Rate (FPS) |
Indicates the image refresh rate in non-video scenarios. Increasing this value improves image and operation smoothness but consumes more network bandwidth and VM CPU resources. The value ranges from 1 to 60. The recommended value ranges from 15 to 25. |
25 |
|
|
Video Frame Rate (FPS) |
Indicates the image refresh rate of video. Increasing this value improves video playback smoothness but consumes more network bandwidth and VM CPU resources.
NOTE:
This parameter is unavailable after Rendering acceleration is enabled. |
- |
|
|
Bandwidth (kbit/s) |
Limits the peak bandwidth of a user. The value ranges from 256 to 25,000. |
20000 |
|
|
Image Compression Parameters |
Min. Capacity for Image Cache (MB) |
The minimum capacity for image cache, expressed in MB. Increasing this value reduces bandwidth usage but consumes more client memory resources. If the parameter is set to a value smaller than 50, the cache function is disabled. The value ranges from 0 to 300. |
200 |
|
Lossy Compression Recognition Threshold |
The threshold for recognizing image complexity. Decreasing this value increases image quality but consumes more network bandwidth resources. The value ranges from 0 to 255. |
60 |
|
|
Lossless compression |
Specifies the image compression algorithm. You can select Basic compression or Deep compression. When you compress the same picture, the compression ratio and CPU usage of basic compression are lower than those of deep compression. |
Basic compression |
|
|
Deep Compression Level |
This parameter takes effect after Deep compression is selected. A higher compression level means a higher compression ratio and CPU usage but lower bandwidth usage. Level 0 indicates a copy operation and no compression is involved. This level consumes the fewest CPU resources but the most bandwidth resources. |
Level 0 |
|
|
Lossy Compression Quality |
This parameter is used to set the image quality after lossy compression. Increasing this value improves image quality. The value ranges from 20 to 100. |
85 |
|
|
Color Enhancement for Office Work |
This parameter is used for color enhancement in office scenarios.
|
|
|
|
Video Compression Parameters |
Quality/Bandwidth First |
|
Quality |
|
Average Video Bitrate (Kbit/s) |
Video compression algorithm parameter. In the Bandwidth First mode, increasing this value improves video quality. The value ranges from 256 to 100,000. |
18,000 |
|
|
Peak Video Bitrate (Kbit/s) |
Video compression algorithm parameter. Increasing this value improves display quality. The value ranges from 256 to 100,000. |
18,000 |
|
|
Average Video Quality |
Average quality coefficient of video. In the Quality First mode, increasing this value compromises video quality. The value ranges from 5 to 59. |
15 |
|
|
Lowest Video Quality |
Lower limit of video quality. In the Quality First mode, increasing this value compromises video quality. The value ranges from 5 to 69. |
25 |
|
|
Highest Video Quality |
Upper limit of video quality. In the Quality First mode, increasing this value compromises video quality. The value ranges from 1 to 59. |
7 |
|
|
GOP Size |
Video compression algorithm parameter. Decreasing this value improves video quality but consumes more bandwidth resources. It is recommended that this value be 1 to 2 times the video frame rate. The value ranges from 0 to 65,535. |
100 |
|
|
Encoding Preset |
Video compression algorithm parameter. Decreasing this value means faster encoding and better smoothness but lower image quality and higher bandwidth usage. |
Preset 1 |
|
|
Rendering Acceleration |
Rendering Acceleration |
|
|
|
Video Acceleration Enhancement |
|
|
|
|
Video Optimization |
|
Disabled |
|
|
GPU Color Optimization |
NOTE:
This parameter applies only to GPU desktops. |
|
|
|
Video Recognition Threshold |
Number of frames required when you open or exit a video. It is easier to open or exit a video as the value increases. The value ranges from 0 to 500. |
10 |
|
|
Frame Rate Statistical Length |
Number of statistical frames during video detection. It is easier to open a video as the value decreases. The value ranges from 2 to 100. |
4 |
|
|
Image Quality Threshold |
It is easier to open a video as the value decreases. The value ranges from 0 to 100. |
0 |
|
|
Refresh Frequency Threshold |
It is easier to open a video as the value decreases. The value ranges from 1 to 100. |
3 |
|
|
Threshold of Exiting Video Area |
It is easier to exit a video as the value decreases. The value ranges from 0 to 100. |
8 |
|
|
Min Video Width |
It is easier to open a video as the value decreases. The value ranges from 0 to 1,280. |
191 |
|
|
Min Video Height |
It is easier to open a video as the value decreases. The value ranges from 0 to 1,280. |
191 |
|
|
Proportion Threshold of Single-Frame Natural Image Block |
It is easier to open a video as the value decreases. The value ranges from 0.000001 to 1. |
0.3 |
|
|
Number of Cyclical Natural Images |
It is easier to open a video as the value decreases. The value ranges from 0 to 100. |
2 |
|
|
Threshold of the Non-Natural Image Area Percentage |
It is harder to exit a video as the value increases. The value ranges from 0.000001 to 1. |
0.85 |
|
|
Number of Non-Natural Images |
It is harder to exit a video as the value increases. The value ranges from 0 to 100. |
25 |
|
|
Other Parameters |
Graphics Card Memory (MB) |
Device memory capacity. The value ranges from 0 to 64. This parameter affects the bandwidth in some scenarios. Increasing this value reduces the bandwidth usage. |
64 |
|
Driver Delegation Mode |
|
|
|
|
Driver Delegation Latency (*30ms) |
The value ranges from 1 to 100. |
80 |
|
|
Video Latency (*30ms) |
The value ranges from 1 to 100. |
80 |
|
|
Change Resolution in Computer |
|
|
|
|
Application Recognition |
Configure display policies for specific applications. (Provided by Huawei engineers)
NOTE:
A Windows 10 computer supports up to 4 applications. |
- |
Files and Clipboards
|
Type |
Parameter |
Description |
Example Value |
|---|---|---|---|
|
File Redirection |
File redirection switch |
Users can use drivers in file redirection mode on cloud desktops. |
Read-only |
|
Fixed driver |
NOTE:
When file redirection is disabled, this function is disabled. |
|
|
|
Removable driver |
NOTE:
When file redirection is disabled, this function is disabled. |
|
|
|
CD/DVD-ROM driver |
|
|
|
|
Network driver |
|
|
|
|
Traffic Control |
|
|
|
|
Good Network Latency Threshold (ms) |
Latency threshold of good network. The value ranges from 1 to 1000. |
30 |
|
|
Normal Network Latency Threshold (ms) |
Latency threshold of normal network. The value ranges from 1 to 1000. |
70 |
|
|
Poor Network Latency Threshold (ms) |
Latency threshold of poor network. The value ranges from 1 to 1000. |
100 |
|
|
Reducing Step (KB) |
Step of reducing the transmission speed. The value ranges from 1 to 100. |
20 |
|
|
Slow Increasing Step (KB) |
Slow step of increasing the transmission speed. The value ranges from 1 to 100. |
10 |
|
|
Quick Increasing Step (KB) |
Quick step of increasing the transmission speed. The value ranges from 1 to 100. |
20 |
|
|
Start Speed (KB/s) |
Initial transmission speed. The value ranges from 1 to 10,240. |
1024 |
|
|
Test Block Size (KB) |
Block size of speed testing. The value ranges from 64 to 1024. |
64 |
|
|
Test Time Gap (ms) |
Gap of testing. The value ranges from 1,000 to 100,000. |
10,000 |
|
|
Compression |
|
|
|
|
Compression Threshold (Byte) |
The value ranges from 0 to 10,240. |
512 |
|
|
Min Compression Rate |
The value ranges from 0 to 1,000. |
900 |
|
|
File Size Supported by Linux |
|
|
|
|
File Size Threshold for Linux (MB) |
The value ranges from 0 to 4,096. |
100 |
|
|
Mobile Client Redirection |
|
|
|
|
Linux Root Directory Mounting |
|
|
|
|
Linux Root Directory Mounting Path |
If root directory mounting is enabled on Linux, you need to configure the mounting path. The value contains a maximum of 256 characters in UTF-8 format. |
\var\log |
|
|
Linux File System Mounting Path |
The value contains a maximum of 256 characters in UTF-8 format. |
\media|\Volumes|\swdb\mnt|\home|\storage|\tmp|\run\media |
|
|
Linux Fixed Driver File System Format |
The value contains a maximum of 256 characters in UTF-8 format. |
- |
|
|
Linux Removable Driver File System Format |
The value contains a maximum of 256 characters in UTF-8 format. |
vfat|ntfs|msdos|fuseblk|sdcardfs|exfat|fuse.fdredir |
|
|
Linux CD-ROM Driver File System Format |
The value contains a maximum of 256 characters in UTF-8 format. |
cd9660|iso9660|udf |
|
|
Linux Network Driver File System Format |
The value contains a maximum of 256 characters in UTF-8 format. |
smbfs|afpfs|cifs |
|
|
Path Separator |
A single ASCII character |
| |
|
|
Read/Write Speed (Kbit/s) |
This option is disabled when File Redirection and Send File From VM to Client are disabled. The value 0 indicates that the read/write speed is not limited. Other values indicate the configured read/write speed. The default minimum speed is 32 kbit/s. If the minimum speed is lower than 32 kbit/s, 32 kbit/s is used by default. |
0 |
|
|
Send File |
Send File from VM to Client |
|
|
|
Clipboard Redirection |
Clipboard Redirection |
NOTE:
|
Bidirectional |
|
Clipboard Rich Text Redirection |
|
|
|
|
Clipboard File Redirection |
|
|
Sessions
|
Parameter |
Description |
Recommended Value |
|---|---|---|
|
Auto Screen Locking |
|
Disabled |
|
Validity Period |
Specifies the time when the policy takes effect. The time is the local time of the cloud desktop. |
- |
|
Screen Locking In (Minute) |
Specifies the waiting time before the desktop screen is automatically locked. The value ranges from 3 to 86,400. |
10 |
|
Auto Disconnect/Log Out/Restart/Stop/Hibernate After Auto Screen Locking |
After the desktop is hibernated, the applications on the desktop are paused. After the desktop is woken up, the applications can be restored to the status when they were paused.
|
Disabled |
|
Automatic Disconnection/Logout/Restart/Shutdown/Hibernation After Screen Lock In (Minute) |
Specifies the waiting time before a desktop is automatically disconnected, logged out of, restarted, shut down, or hibernated. The value ranges from 1 to 86,400. |
1440 |
|
Automatic Logout/Restart/Shutdown/Hibernation After Disconnection |
|
Disabled |
|
Automatic Logout/Restart/Shutdown/Hibernation After Disconnection In (Minute) |
Specifies the waiting time before a desktop is automatically logged out of, restarted, shut down, or hibernated after disconnection. The value ranges from 10 to 86,400. |
10 |
|
Self-help console login preemption |
This configuration item is used to determine whether preemption login through the self-help console is allowed when a user desktop has been logged in to. |
|
|
Disconnection After Screen Locking |
This parameter determines whether to disconnect from a desktop immediately when the desktop is locked. Screen locking may happen when the automatic session locking policy is triggered or the user locks the desktop screen.
NOTE:
|
|
Watermarking
Configure watermark policies, as shown in Table 8.
|
Parameter |
Description |
Example Value |
|---|---|---|
|
Watermarking |
|
|
|
Security First |
After this function is enabled, if the client version is earlier than the server version, access is rejected. |
|
|
Custom Content |
The content contains only digits, uppercase letters, lowercase letters, and some special characters, and cannot exceed 45 characters. After you customize the content, the desktop screen displays the watermark in the format of Custom content Login username Time displayed on the desktop. For example, if the custom content is set to CopyRight, the watermark is CopyRight user 2022-01-08 01:01:01. |
- |
|
User Information |
Terminal user information. If the user does not enter the mobile number or email address, the user information is not displayed.
|
Username |
|
Date-Time Sequence |
Sequence in which the date and time are displayed:
Example: 2020-01-01 16:40 for DT; 16:40 2020-01-01 for TD |
DT (date-time format) |
|
Display Mode |
|
Random motion |
|
Alignment |
Watermark alignment. Options: Left alignment, Right alignment, and Center alignment |
Left alignment |
|
Quantity |
Number of watermarks. This parameter is available when Display Mode is set to Fixed position. The value ranges from 1 to 17. |
1 |
|
Repeated Watermarks |
Number of repeated watermarks. This parameter is available when Display Mode is set to Fixed position. The value ranges from 1 to 17. |
1 |
|
Repetition Interval |
Interval of repeated watermarks. This parameter is available when Display Mode is set to Fixed position. The value ranges from 1 to 17. |
10 |
|
Tilt |
Specifies the tilt of the watermark displayed on the desktop. The value ranges from –90 to 90. |
–45 |
|
Font Size |
Watermark font size. The value ranges from 8 to 100. |
30 |
|
Color |
Watermark color |
|
|
Opacity (%) |
The value ranges from 0 to 100. 0% indicates completely transparent, and 100% indicates completely opaque. |
87.5 |
|
Preview |
You can click to preview the watermark in 16:9 or 4:3. |
- |
General Audio/Video Bypass
After installing applications and the Huawei Cloud Workspace client on a local terminal running Windows 10, you can configure the audio/video bypass policy to access a cloud desktop from the Huawei Cloud Workspace client and use the applications on the local terminal without installing the applications on the cloud desktop. Table 9 describes the general audio/video bypass policy.
The audio/video bypass function has the following restrictions:
- This parameter is available only when the local terminal runs Windows 10 and the cloud desktop runs Windows.
- Non-cloud desktop applications can be mapped to cloud desktops using the general audio/video bypass policy only when these applications work properly on local terminals.
- Before logging in to a cloud desktop and using an application mapped to the cloud desktop through the audio/video bypass policy, you need to stop the applications that have been started on the local terminal. Otherwise, the application cannot be used on the cloud desktop.
- Before using applications that are mapped to the cloud desktop through the audio/video bypass policy, ensure that the cloud desktop is in full screen mode.
- When an application that is mapped to the cloud desktop through the audio/video bypass policy is used on the cloud desktop, other applications on the cloud desktop cannot be used to interact with the application. For example, you cannot use the screenshot software on the cloud desktop to capture the application GUI.
- The input method used by the application is the terminal-side input method. If you want to switch the input method when using an application that is mapped to the cloud desktop through the audio/video bypass policy on the cloud desktop, you need to switch the input method of the local terminal. For example, an input method is switched by using a keyboard shortcut, or an input method is switched on a local desktop by minimizing a cloud desktop.
- When an application that is mapped to the cloud desktop through the audio/video bypass policy is used on the cloud desktop, if you press Alt+Tab to switch between windows, the local terminal GUI is displayed.
- If the Video devices (such as cameras) policy in USB Port Redirection is enabled on the current cloud desktop, the camera on the local terminal cannot be used when you perform video-related operations on the cloud desktop using applications mapped to the cloud desktop through the audio/video bypass policy.
- If you want to copy text between a cloud desktop and an application mapped to the cloud desktop through the audio/video bypass policy, you need to enable the clipboard redirection policy on the cloud desktop. For details about policy configuration, see How Do I Copy Files Between a Desktop and a Local Storage Device?
- After a local application is mapped to the cloud desktop through the audio/video bypass policy, you are not advised to use the software package to install the application on the cloud desktop. Otherwise, when you start the application on a web page, the application installed using the software package on the cloud desktop will be started.
|
Parameter |
Description |
Example Value |
|---|---|---|
|
General Audio/Video Bypass |
|
|
|
Software Path |
Used to configure the software path and start parameters for the general audio/video bypass policy. Separate multiple paths with semicolons (;). If an installation path contains spaces, use double quotation marks ("") to quote the path. Example: "C:\Users\userName\AppData\Roaming\HuaweiMeeting\HuaweiMeeting\HuaweiMeeting.exe" --bypass; HuaweiMeeting.exe --bypass; Currently, only Huawei Cloud Meeting is supported.
NOTE:
|
C:\Users\Username\AppData\Roaming\HuaweiMeeting\HuaweiMeeting\HuaweiMeeting.exe |
Virtual Channels
The administrator can configure a virtual channel policy so that users can access the cloud desktop through the Huawei Cloud Workspace client and download plug-ins. Table 10 describes virtual channel policies.
|
Parameter |
Description |
Example Value |
|---|---|---|
|
Virtual Channel Control |
|
|
|
Custom Virtual Channel Registered Name |
Contact Huawei technical support to obtain it. |
- |
|
Configuration Information |
Contact Huawei technical support to obtain it. |
- |
|
Third-Party Plug-in Name |
Used by clients (Windows clients only) to load third-party plug-ins, for example, LyncVdiPluginLib. Multiple plug-in names can be entered and must be separated by spaces or commas (,). |
LyncVdiPluginLib |
Keyboards and Mouse Devices
|
Parameter |
Description |
Recommended Value |
|---|---|---|
|
Computer Mouse Device Feedback |
|
Adaptive |
|
Computer Mouse Device Simulation Mode |
If you select Relative positioning, the value of Change the size of text, apps, and the other items on the display settings cannot be higher than 100% on the user VM.
|
Absolute positioning |
|
Self-help Console Login Preemption |
This configuration item is used to determine whether preemption login through the self-help console is allowed when a user desktop has been logged in to. |
|
|
Computer External Cursor Feedback |
|
|
Screen Recording Audit

If you use screen recording audit for the first time, the OBS resources are required. You need to add access authorization. After the authorization is granted, an agency named workspace_trust_for_obs will be created for you in IAM. Do not delete or modify workspace_trust_for_obs.
|
Parameter |
Description |
Recommended Value |
|---|---|---|
|
Screen Recording Audit |
|
|
|
Screen Recording Type |
|
Continuous |
|
Audio Recording |
After the recording starts, determine whether to record the audio of the cloud desktop. |
No |
|
Frame Rate |
2/5/10/15 FPS |
5 FPS |
|
Resolution |
720p, 1080p, or original resolution |
1080p |
|
Recording File Segment |
10/20/30/60 minutes |
10 minutes |
|
Save To |
|
Auto create |
|
Key event audit |
You can enable this function to collect key events of desktops. For details, see Event Audit. |
- |
|
Application monitoring: including application startup, termination, abnormal exit, installation, and uninstallation, and no application response
NOTE:
|
||
|
App Startup/Termination Monitoring
|
||
|
File monitoring: file creation, deletion, and renaming Monitored file extension: including .doc, .ppt, .xlsx, and .txt. A maximum of 1,000 characters are allowed. You can customize the file format. For details about more file name extensions, see Common File Name Extensions. |
||
|
Protocol behavior monitoring: file redirection, USB insertion and removal, clipboard operations, idle (no operations), and file printing |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot