LwM2M/CoAP Access
Introduction
Lightweight Machine to Machine (LwM2M), proposed by the Open Mobile Alliance (OMA), is a lightweight, standard, and universal IoT device management protocol that can be used to quickly deploy IoT services in client/server mode. LwM2M establishes a set of standards for IoT device management and application. It provides lightweight, compact, and secure communication interfaces and efficient data models for M2M device management and service support.
LwM2M/CoAP authentication supports both encrypted and non-encrypted access modes. Non-encrypted mode: Devices connect to IoTDA carrying the node ID through port 5683. Encrypted mode: Devices connect to IoTDA carrying node ID and secret through port 5684 by the DTLS/DTLS+ channel.
You are advised to use the encrypted access mode for security purposes.
For details about LwM2M syntax and APIs, see specifications.
IoTDA supports the plain text, opaque, Core Link, TLV, and JSON encoding formats specified in the protocol. In the multi-field operation (for example, writing multiple resources), the TLV format is used by default.
Constraints
|
Description |
Constraint |
|---|---|
|
Supported LwM2M version |
1.1 |
|
Supported DTLS version |
DTLS 1.2 |
|
Supported cryptographic algorithm suites |
TLS_PSK_WITH_AES_128_CCM_8 and TLS_PSK_WITH_AES_128_CBC_SHA256 |
|
Body length |
1 KB |
|
API specifications |
Endpoints
For details about the platform endpoint, see Platform Connection Information.
Use the endpoint corresponding to CoAP (5683) or CoAPS (5684) and port 5683 (non-encrypted) or 5684 (encrypted) for device access.
Authentication Process
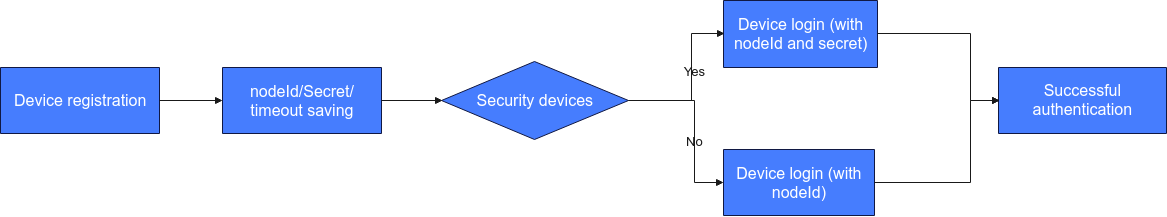
- An application calls the API for registering a device. Alternatively, a user uses the IoTDA console to register a device.
- The platform allocates a secret to the device and returns timeout.
- The secret can be defined during device registration. If no secret is defined, the platform allocates one.
- If the device is not connected to the platform within the duration specified by timeout, the platform deletes the device registration information.
- During login, the device sends a connection authentication request carrying the node ID (such as the IMEI) and secret if it is a security device, or carrying the node ID if it is a non-security device.
- If the authentication is successful, the platform returns a success message, and the device is connected to the platform.
Development Process
- Development on the platform: Create products, develop product models and codecs on the platform, and register devices. For details, see Creating a Product, Developing a Product Model, Developing a Codec, and Registering a Device.
- Development on the device: Use modules and Tiny SDKs on the device side for access. For details, see IoT Device SDK Tiny (C) User Guide.
Best Practices
FAQs
LwM2M/CoAP access FAQs:
- How Do I Know the Strength of the NB-IoT Network Signal?
- What Do I Do If an NB-IoT Module Failed to Be Bound to a Device?
- What Do I Do If an NB-IoT Module Failed to Be Bound to a Device?
- What Can I Do If an NB-IoT Module Cannot Report Data?
- Why Was a 513 Message Reported During the Connection of an NB-IoT Device?
- Why Does Data Reporting Fail When an NB-IoT Card Is Used in Another Device?
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





