Enabling and Configuring the Resource Recorder
Scenarios
The resource recorder automatically detects and records changes made to your resources that are supported by Config.
If you have enabled the resource recorder and specified an OBS bucket and an SMN topic when you configure the resource recorder, Config will notify you of any changes (creation, modification, deletion, relationship change) to the resources within the monitoring scope and periodically store your notifications and resource snapshots.
To get full functionality of Config, you need to enable the resource recorder. If the resource recorder is disabled, other functions may be affected. For example, you may fail to update your resource data, create and use rules, or to aggregate resource data.
This section describes how to enable and configure the resource recorder.
Preparations
- If you already have a Huawei account, skip this step. If you do not have one, follow the following steps to create one:
- Go to Huawei Cloud and click Sign Up.
- Sign up for a Huawei account and enable Huawei Cloud services.
After your account is created, you will be directed to your personal information page.
- Complete real-name authentication by following the instructions in Individual Real-Name Authentication or Enterprise Real-Name Authentication.
- Top up your account.
Config is free of charge, but the SMN topic and the OBS bucket that you configured for the resource recorder will be charged. For details, see SMN billing and OBS billing.
Ensure your account has sufficient balance to avoid unavailability of the resource recorder and other functions of Config. For more details, see Topping up an Account.
Procedure
The following steps describe only the mandatory parameters for the resource recorder. Retain the default values for other parameters. For more information about how to configure the resource recorder, see Configuring the Resource Recorder.
- Log in to the Config console.
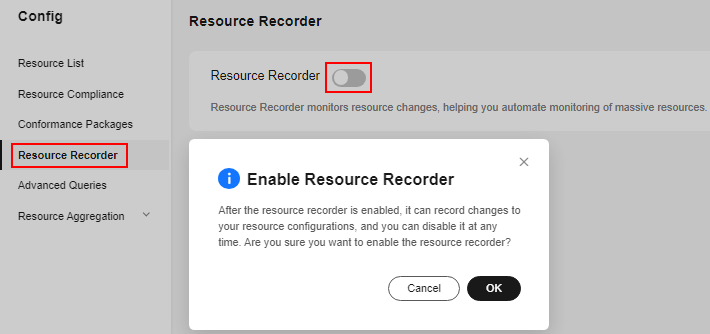
- In the navigation pane on the left, choose Resource Recorder.
- Toggle on the resource recorder and in the displayed dialog box, click OK.
- Specify an OBS bucket.
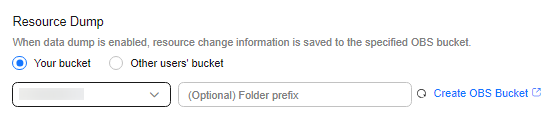
Select an OBS bucket from the current account or another account to store resource change messages and snapshots.
If there are no OBS buckets in the current account, create one first. For details, see Creating a Bucket.
- Configure an SMN topic.
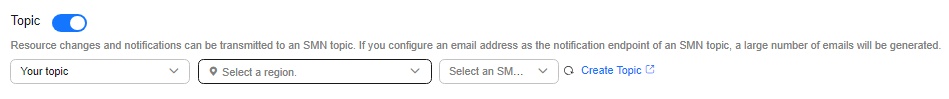
Toggle on the SMN topic, select Your topic, and select a region and an SMN topic.
If there are no SMN topics available in the current account, create one first. For details, see Creating a Topic.
To send notifications with an SMN topic, you not only need to create the topic, but also add subscriptions and request subscription confirmations.
- Specify a data retention period.
You can select Seven years (2,557 days) or customize a period.
- Grant permissions.
Quick granting will automatically create an agency named rms_tracker_agency to grant the required permissions for the resource recorder to work properly. The agency contains permissions, including the SMN Administrator for sending notifications and the OBS OperateAccess permission for writing data into an OBS bucket.
- Click Save.
- In the displayed dialog box, click OK.
Related Information
You can modify or disable the resource recorder at any time. You can enable or modify the resource recorder for up to 10 times per day. The number of times will be reset at 00:00 every day.
- When configuring the resource recorder, you can select OBS buckets or SMN topics of other accounts. However, you must first use the other accounts to authorize the current account. For details, see Cross-Account Authorization.
- If you select Custom granting to customize authorization for the resource recorder, you need to create an agency with IAM, and the agency must include either the permissions for sending notifications using an SMN topic or the permissions for writing data into an OBS bucket based on related configurations. If you want to store resource change messages and resource snapshots in an OBS bucket encrypted using KMS, you will also need the KMS Administrator permission. For details, see Storing Resource Change Notifications and Resource Snapshots to an Encrypted OBS Bucket in the Config User Guide. For details about how to create an agency, see Cloud Service Agency.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





