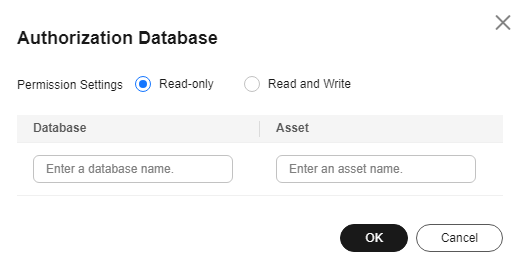
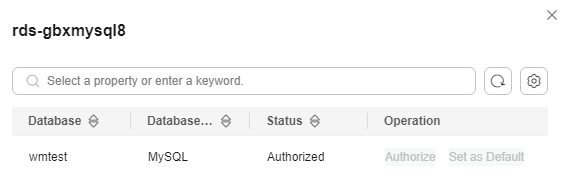
Adding and Authorizing Database Assets
To identify sensitive data, mask static data, or add/extract data watermarks for database assets, you must authorize DSC to access your databases.
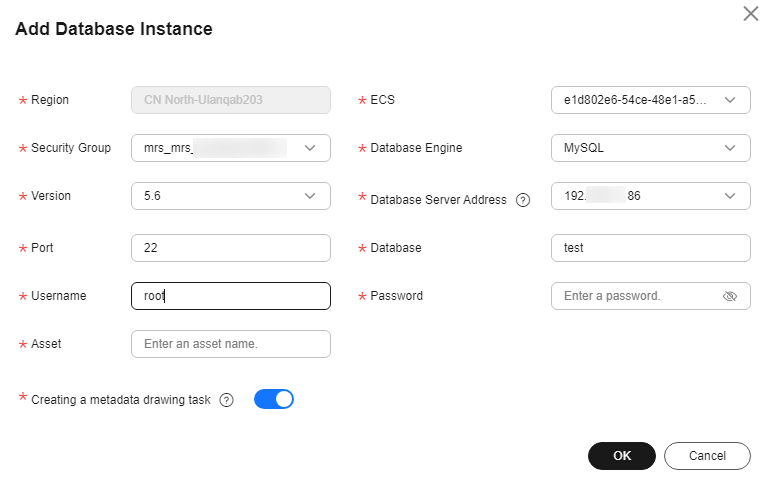
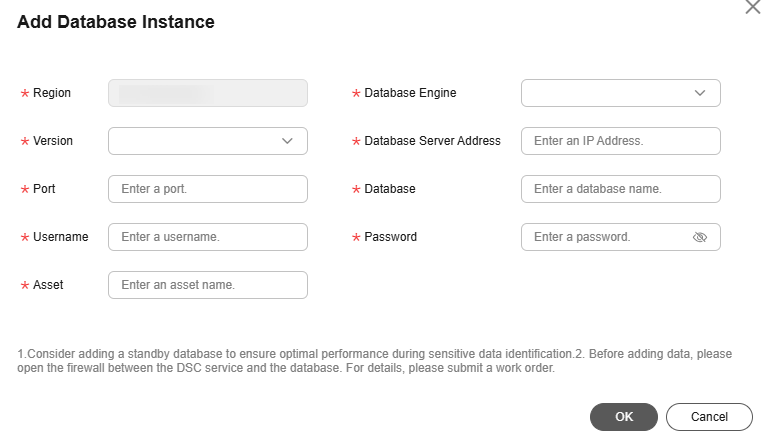
- For self-built databases: Add the instance to DSC according to "Adding a Database Instance", then authorize access by referring to Authorizing Access to a Database Asset.
- For cloud databases: Instance addition is not required. Instead, authorize DSC's access by referring to Authorizing Access to a Database Asset.
Prerequisites
|
Type |
Prerequisites |
|---|---|
|
Self-built database |
|
|
DWS cross-account or cross-VPC instance |
|
Constraints
- The following DWS instance versions are supported: 9.1.0, 9.0, 8.3.0, 8.2.1, 8.2.0, 8.1.3, 8.1.1, 8.0.1, and 8.0.0.
- For user-built databases, only data sources and versions supported by DSC can be added. For details, see Table 2.
Table 2 Data sources and versions supported by DSC Data Source
Version
MySQL
5.6, 5.7, 5.8, and 8.0
SQL Server
2017_SE, 2017_EE, and 2017_WEB
2016_SE, 2016_EE, and 2016_WEB
2014_SE and 2014_EE
2012_SE, 2012_EE, and 2012_WEB
2008_R2_EE and 2008_R2_WEB
PostgreSQL
15, 14, 13, 12, 11, 10, 9.6, 9.5, 9.4, 9.1, and 1.0
TDSQL
10.3.X
Oracle
11 and 12
KingBase
V8
GaussDB
1.3, 1.4, and 2.7
DMDBMS
7 and 8
DWS
8.1.X
Adding and Authorizing Database Assets
This section describes how to add your database assets to DSC for data security management.
Related Operations
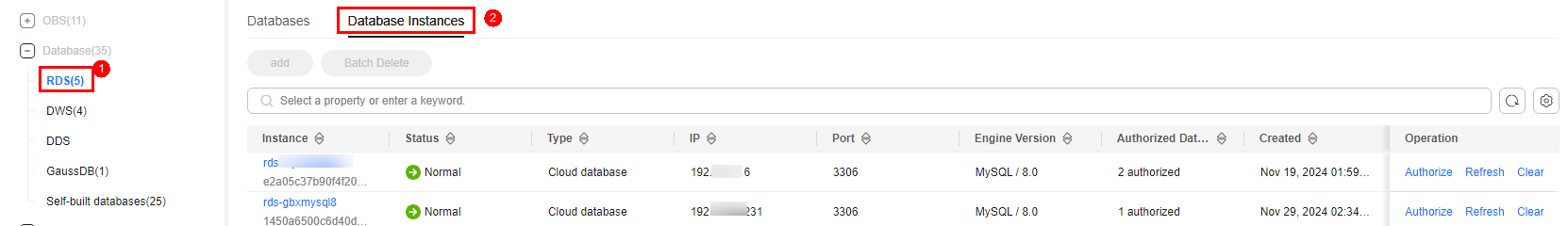
- Deleting a DB instance
Only self-built DB instances can be deleted. You can delete an instance only when there are no authorized databases and metadata under it.
Select multiple self-built database instances and click Batch Delete in the upper left corner of the instance list to delete the instances. You can also click Delete in the Operation column of the instance list to delete a single DB instance.
- Drawing metadata of an instance
- If the number of authorized databases of a cloud database instance is greater than 0, click Refresh in the Operation column of the instance list to obtain the database, table, and column information of the instance.
Cloud databases that do not support metadata collection are excluded. For details, see Step 1: Scanning Metadata.
- If you enable the function of automatically creating a metadata task when adding a self-built database instance, the system automatically creates a metadata task to obtain all metadata of the instance after the instance is created.
User-built databases that do not support metadata collection, such as SQL Server, are excluded. For details, see Step 1: Scanning Metadata.
- You can manually create a metadata task by referring to section Step 1: Scanning Metadata.
- If the number of authorized databases of a cloud database instance is greater than 0, click Refresh in the Operation column of the instance list to obtain the database, table, and column information of the instance.
- Creating an identification task
In the Databases tab, locate the target asset and click Create Identification Task in the Operation column. For details, see Creating an Identification Task.
- Testing connectivity in batches
You can select multiple database instances and data instances to perform connectivity tests in batches.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot