Implementing Asset Classification and Grading Through Data Exploration
Create a metadata task. The data task creates a connection based on the database and pulls the database, data table, and data view of the instance. After the metadata task is executed, you can view data details on the data exploration page and add descriptions, labels, security levels, and classifications to the data, implementing hierarchical and classified management of data assets.
Prerequisites
DSC has been allowed to access the database assets. For details, see Allowing or Disallowing Access to Cloud Assets.
Constraints
Metadata tasks can be created for the following data sources: MySQL, TDSQL, PostgreSQL, Dameng, Kingbase, GaussDB, DWS, Hive, and MRS_HIVE.
Step 1: Scanning Metadata
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Asset Management > Metadata Task.
- On the Metadata Collection Task page, click Create. On the Create Collection Task page, configure the data source. Table 1 describes the data source parameters.
- Click Next. The Configure subtasks page is displayed.
- Choose
 or
or  to enable or disable Scan user tables.
to enable or disable Scan user tables. - Choose
 or
or  to enable or disable Scan systems tables, including information_schema.
to enable or disable Scan systems tables, including information_schema. - Choose
 or
or  to enable or disable Scan column constraints to check whether the constraints contain primary keys or whether there are unique constraints.
to enable or disable Scan column constraints to check whether the constraints contain primary keys or whether there are unique constraints. - Choose
 or
or  to enable or disable Scan views to check whether metadata contains views.
to enable or disable Scan views to check whether metadata contains views. - Choose
 or
or  to enable or disable Scan column comments.
to enable or disable Scan column comments. - Click
 or
or  to enable or disable Scan permissions.
to enable or disable Scan permissions.
- Choose
- Click Next. On the Configure Task Information page, configure task information. For details about the parameters, see Table 2.
Table 2 Parameters description Parameter
Description
Task Details
- Task: You can customize the name of a collection task. This parameter is mandatory. The value can contain only letters, digits, underscores (_), and hyphens (-), and cannot exceed 255 characters.
- Task Description: Task description. This parameter is optional.
Task Settings
Click
 or
or  to enable or disable Delete disconnected metadata.
to enable or disable Delete disconnected metadata.When to Execute
- Identification Period: You can select Once, Daily, Weekly, or Monthly.
- When to Execute: You can select Now or As scheduled.
- Start time: If you select As scheduled, click
 to set the start time.
to set the start time.
- Click Next. On the configuration confirmation page that is displayed, confirm the parameters.
- Click Finish. A new metadata collection task is created.
Step 2: Exploring Data
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Asset Management > Data Exploration.
- Select a display mode from the drop-down list box in the upper left corner.
- Database
- Schema
- Table
- Data Column
- Click a database name.
You can add descriptions, labels, sensitivity levels, and categories to databases, data tables, and data views.
Click Analyze to perform automatic sensitivity level analysis. The sensitivity levels of databases and tables are determined based on their column sensitivity levels generated in the sensitive data identification results.
Figure 1 Database details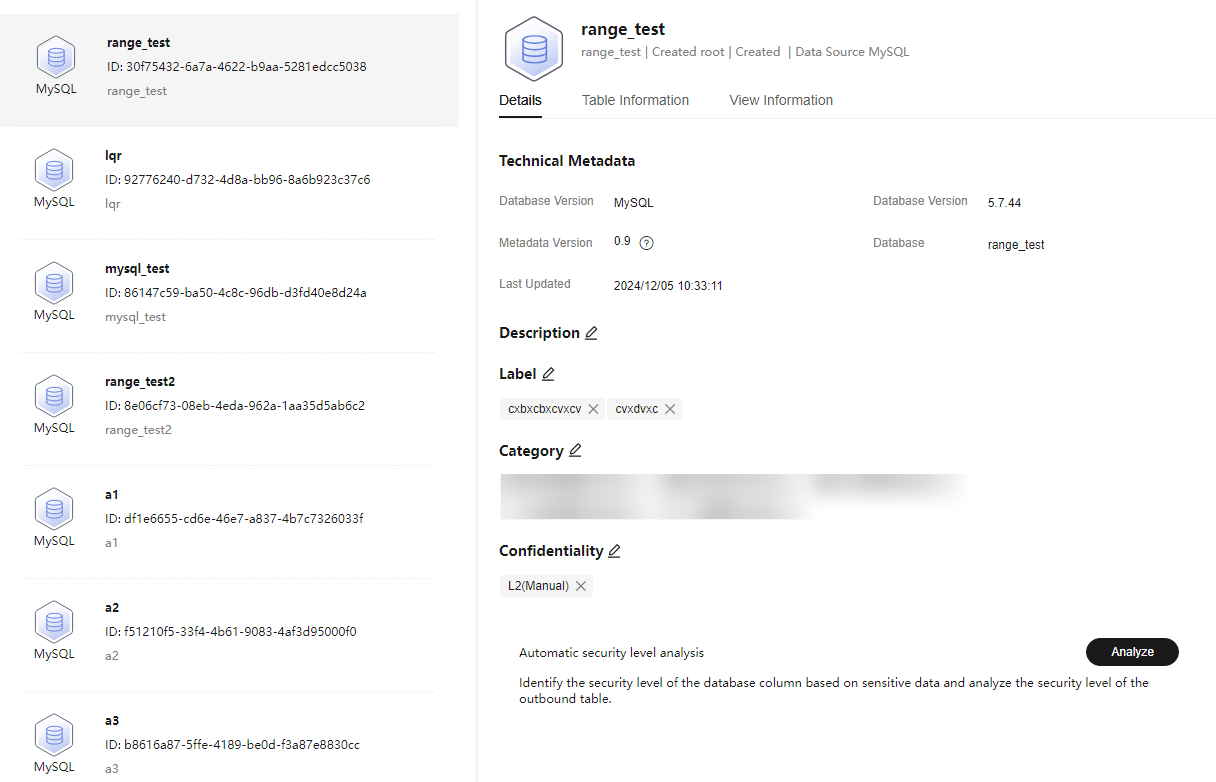
- View detailed information about the database.
- On the data details page, click the Table Information tab.
- Click a table name to view its details.
- Select a table and click Identifier in the upper left corner to add a table identifier. You can select a label or sensitivity level.
- Label: Click the Select Label text box to select an added label or enter text and press Enter to add a label temporarily, and click OK.
- Sensitivity Level: Select a sensitivity level from the drop-down list. The sensitivity levels include built-in levels and custom levels. To create a sensitivity level, see Adding a Sensitivity Level. Select a sensitivity level and click OK.
- You can also click the edit button to add information such as the category, sensitivity level, label, and description for a single table.
- On the data details page, click the View Information tab.
- Click the view name to view the view details.
- Click the View Information tab, select a view, and click Identifier in the upper left corner to add a view identifier. The identifier may be a label or a sensitivity level.
- Label: Click the Select Label text box to select an added label or enter text and press Enter to add a label temporarily, and click OK.
- Sensitivity Level: Select a sensitivity level from the drop-down list. The sensitivity levels include built-in levels and custom levels. To create a sensitivity level, see Adding a Sensitivity Level. Select a sensitivity level and click OK.
- You can also click the edit button to add information such as the category, sensitivity level, label, and description to the view.
- Click the Schema Information tab (this tab is displayed only when the database has schemas).
- Select a schema and click Identifier in the upper left corner to add a column identifier. The identifier may be a label or a sensitivity level.
- Label: Click the Select Label text box to select an added label or enter text and press Enter to add a label temporarily, and click OK.
- Sensitivity Level: Select a sensitivity level from the Select Sensitivity Level drop-down list. The sensitivity levels include built-in levels and custom levels. To create a sensitivity level, see Adding a Sensitivity Level. Select a sensitivity level and click OK.
- You can also click the edit button to add information such as the category, sensitivity level, label, and description to the schema.
- Select a schema and click Identifier in the upper left corner to add a column identifier. The identifier may be a label or a sensitivity level.
- On the data details page, click the Table Information tab.
Related Operations
Enter a database name, database table name, data table column name, or template name in the search box to search for the database information you want to view.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





