Configuring Access Control with Both VPC Endpoint Policies and OBS Bucket Policies
Scenarios
You can apply both VPC endpoint policies and OBS bucket policies to control access to OBS resources at the VPC level. This dual-policy approach ensures that data is transmitted within a secure network environment and minimizes the risk of unauthorized access. This approach is particularly useful in the following scenarios:
- Preventing Internet access to sensitive data: Healthcare organizations often store sensitive data such as medical images and electronic medical records in OBS. For compliance and security purposes, this data must not be transmitted over the Internet. Only authorized servers (ECSs, CCE, or BMSs) in a specific Huawei Cloud VPC can access the data over the intranet. Access from the other VPCs will be denied.
- Assigning VPC-specific access: Enterprises often need to share their data stored in OBS across departments with varying access levels. The development team in VPC1 requires read and write access to all data, the test team in VPC2 requires read access to all data, and other teams in VPC3 require read access to only a set of data.
Context
Virtual Private Cloud (VPC) allows you to provision logically isolated virtual private networks for cloud resources, such as cloud servers, containers, and databases. You can create and manage cloud resources in a VPC, which is secure and flexible. For more information, see What Is Virtual Private Cloud?
VPC Endpoint (VPCEP) provides secure, private channels that connect your VPCs to VPC endpoint services, for example, OBS. This allows resources within a VPC to access OBS without using EIPs. For more information, see What Is VPC Endpoint?
You can use VPCEP to share data stored in OBS with VPCs. You can also share data stored in OBS with on-premises data centers via Direct Connect or Virtual Private Network (VPN) to build a hybrid cloud network where you can flexibly integrate resources.
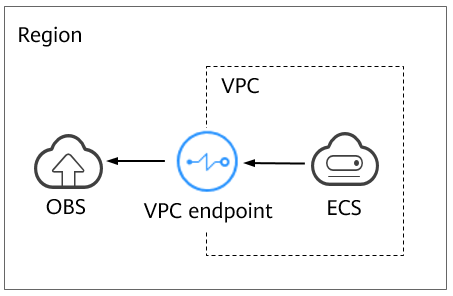
In the same region, if you want to use a VPC endpoint to access OBS over a private network, add OBS as a VPC endpoint service, and create a corresponding VPC endpoint in your VPC. You can then access OBS via the VPC endpoint.
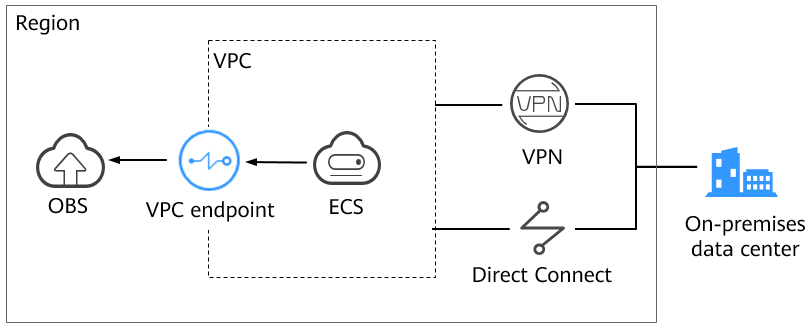
If you want to access OBS from an on-premises data center over a private network, use Direct Connect or a VPN gateway to set up a bridge between the on-premises data center and the VPC that is in the same region as OBS. Then, use a VPC endpoint to connect the VPC to OBS.
How the Dual-Policy Approach Works
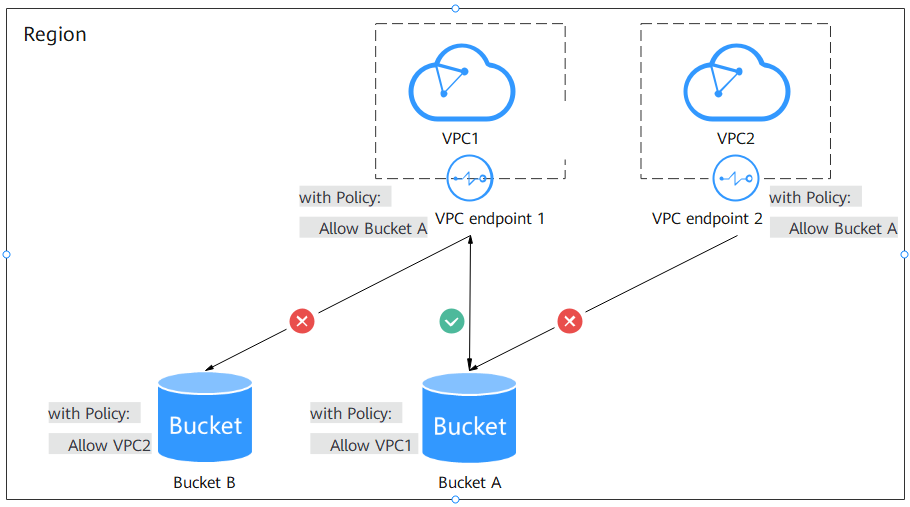
VPC endpoint policies and OBS bucket policies ensure data security by working on the request sources and the requested resources, respectively.
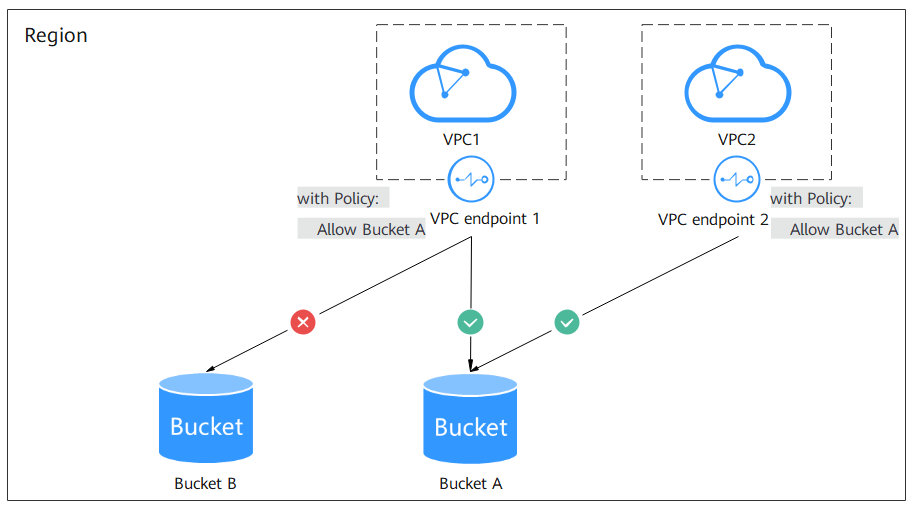
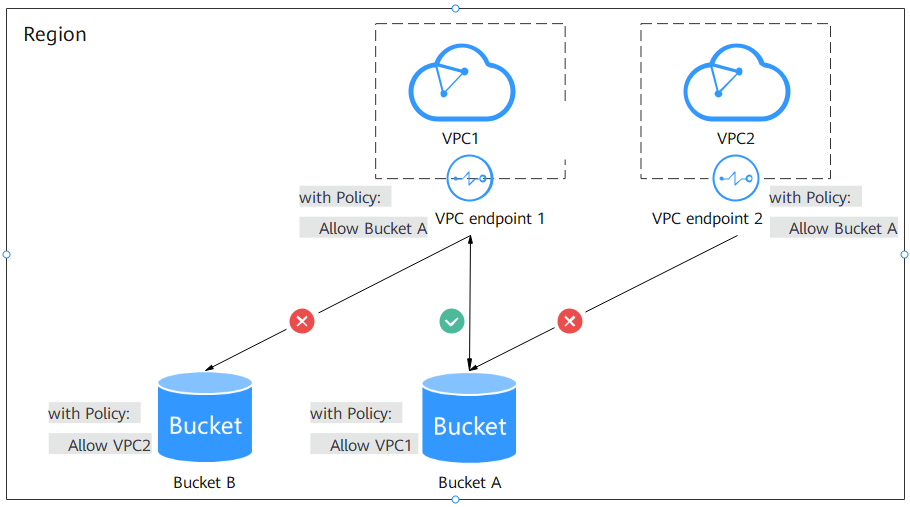
A VPC endpoint policy defines which resources in OBS can be accessed by servers (ECSs or CCE) in a given VPC. As shown in Figure 3, VPC endpoint 1 allows servers in VPC1 to access bucket A but not bucket B. Therefore, VPC1 can access bucket A but cannot access bucket B.
A bucket policy specifies servers in which VPC can access specific OBS buckets. As shown in Figure 3, bucket A's bucket policy allows requests from VPC1 but denies requests from VPC2. Therefore, VPC1 can access bucket A, but VPC2 cannot.
Typical Scenarios and Policy Configuration Examples
The following provides typical application scenarios and configuration examples of the dual-policy approach.
Securing Access with Both VPC Endpoint Policies and OBS Bucket Policies
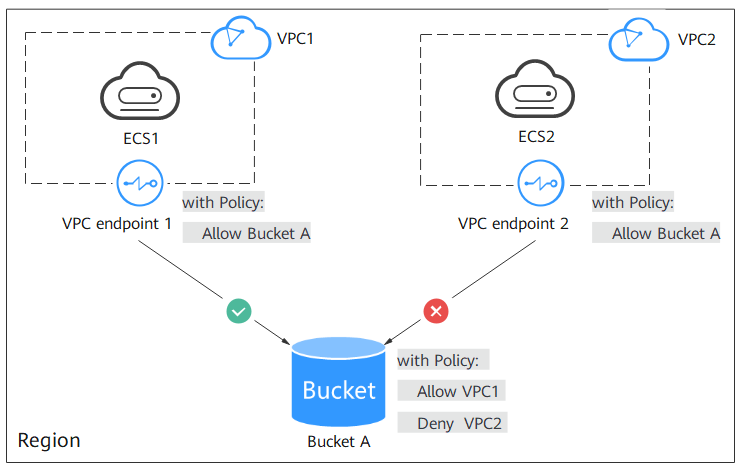
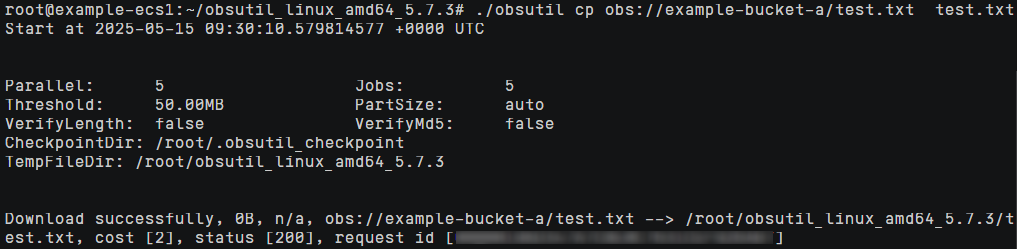
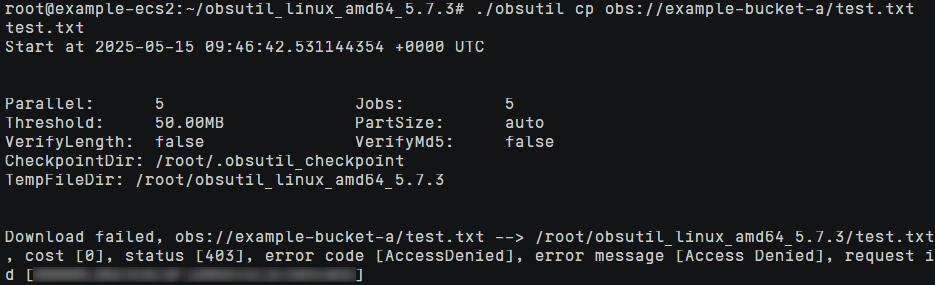
The following uses access from an ECS in a VPC to an OBS bucket as an example (as shown in Figure 6) to show how to secure access by configuring both VPC endpoint policies and OBS bucket policies.
|
Resource |
Region |
Quantity |
Resource Name |
Description |
|---|---|---|---|---|
|
VPC |
CN-Hong Kong |
2 |
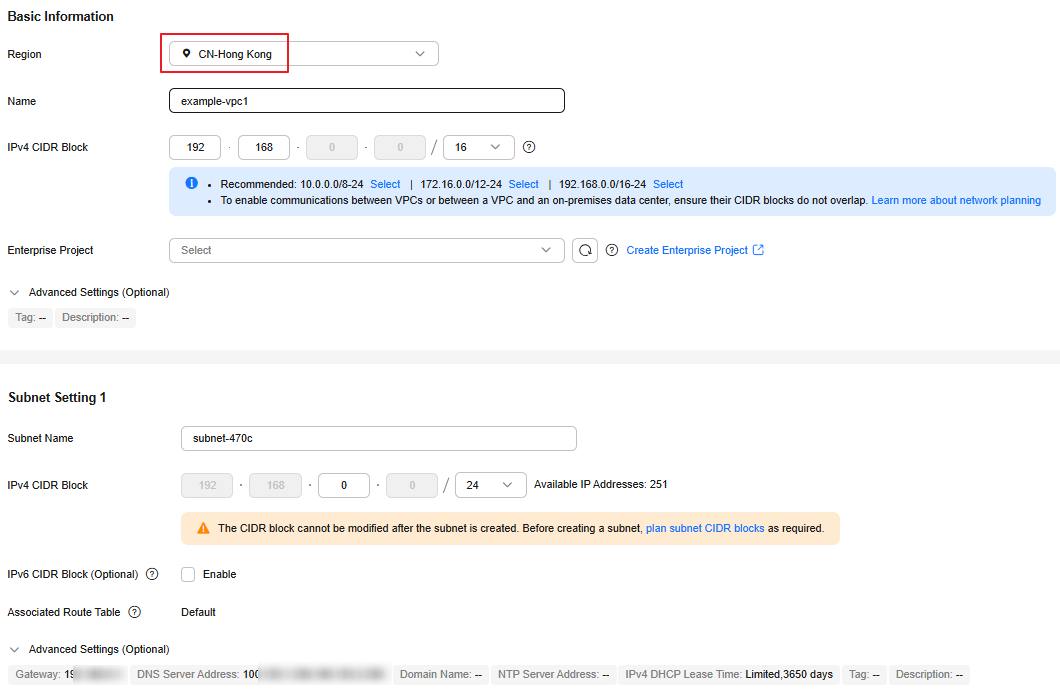
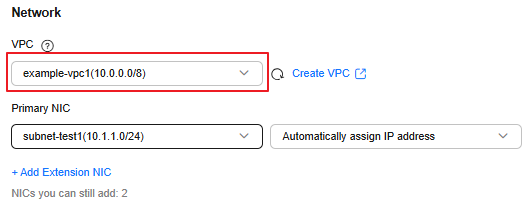
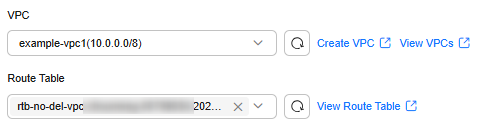
example-vpc1 |
It contains the example-ecs1 ECS and is associated with example-vpcep1. |
|
example-vpc2 |
It contains the example-ecs2 ECS and is associated with example-vpcep2. |
|||
|
VPC endpoint |
2 |
example-vpcep1 |
It is associated with example-vpc1 and controls the requests from example-vpc1. example-vpcep1 grants permission to upload objects to and download objects from example-bucket-a. |
|
|
example-vpcep2 |
It is associated with example-vpc2 and controls the requests from example-vpc2. example-vpcep2 grants permission to upload objects to and download objects from example-bucket-a. |
|||
|
ECS |
2 |
example-ecs1 |
Create this ECS in the example-vpc1 VPC and select a Linux OS, for example, Ubuntu 24.04 server 64bit(10GiB). |
|
|
example-ecs2 |
Create this ECS in the example-vpc2 VPC and select a Linux OS, for example, Ubuntu 24.04 server 64bit(10GiB). |
|||
|
OBS |
1 |
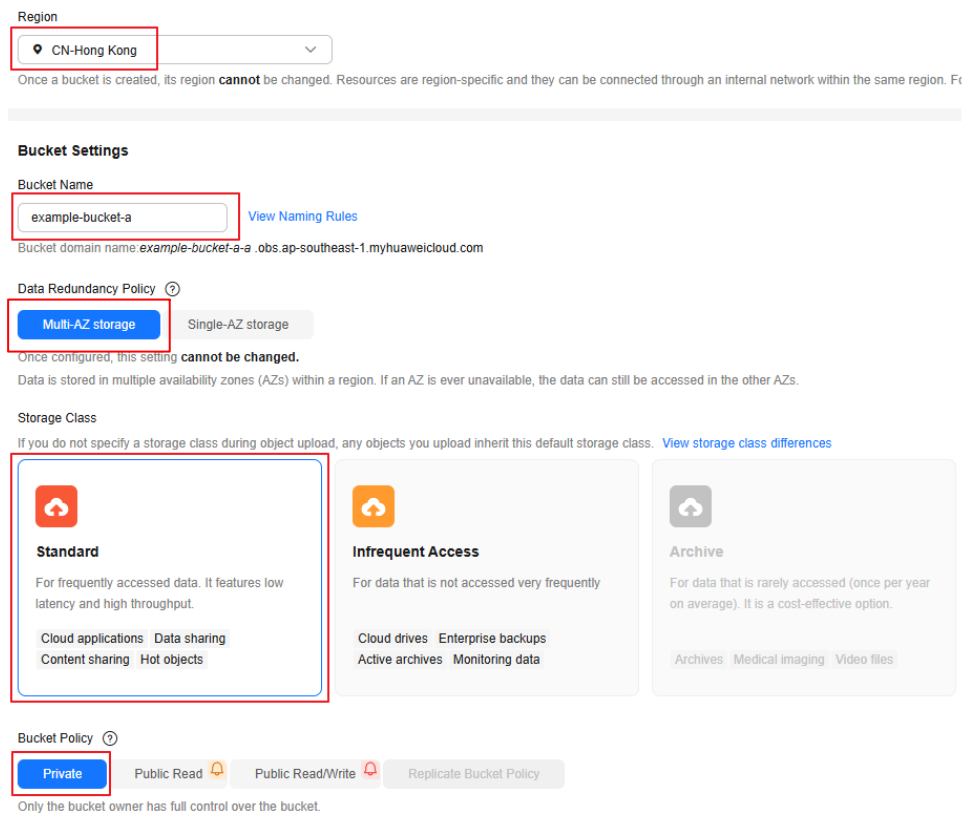
example-bucket-a |
The bucket policy allows access from example-vpc1 and denies access from example-vpc2. |
Related Operations
When securing access by configuring both VPC endpoint policies and OBS bucket policies, you may also need to perform the following operations:
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot