AK/SK Authentication
This section describes how to use AK and SK to sign requests.
- AK: access key ID, which is a unique identifier used in conjunction with a secret access key to sign requests cryptographically.
- SK: secret access key used in conjunction with an AK to sign requests cryptographically. It identifies a request sender and prevents the request from being modified.
Generating an AK and SK Pair
If an AK/SK pair has already been generated, skip this step. Find the downloaded AK/SK file, which is usually named credentials.csv.
As shown in the following figure, the file contains the username, access key ID, and secret access key.
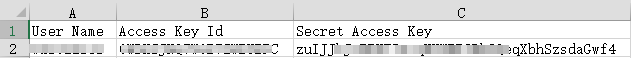
Note:
- You can create a maximum of two access keys with identical permissions and unlimited validity and cannot increase the quota. Each access key can be downloaded only once when created. Keep your access keys secure and change them periodically for security purposes. To change an access key, delete it and create a new one.
- Federated users cannot create access keys, but can create temporary access credentials (temporary AK/SK and security tokens). For details, see Temporary Access Key (for Federated Users).
- If you are an IAM user, move the pointer to the username in the upper right corner of the management console, choose Security Settings, click the Critical Operations tab, and check the enabling status of the Access Key Management feature.
- Disabled: All IAM users under the account can manage (create, enable, disable, and delete) their own access keys.
- Enabled: Only the administrator can manage users' access keys.
- If you cannot manage your access keys, request the administrator to perform either of the following operations:
- Manage access keys and send it to you.
- For details about how to assign permissions, see Assigning Permissions to an IAM User. For details about how to change access key status, see Access Key Management.
- If you are an administrator, you can view the AK of an IAM user on the user details page. The SK is kept by the user.
Perform the following procedure to generate an AK/SK pair:
- Go to the console homepage.
- Hover the cursor on the username and choose My Credentials from the drop-down list.
- Click the Access Keys tab.
- Click Create Access Key.
Each user can create a maximum of two access keys. The quota cannot be increased.
- To change an access key, delete it and create a new one.
- For newly created access keys, the last used time is the same as the creation time, but will change the next time you use them.
- Enter a description, and click OK.
- In the displayed dialog box, click Download to save the access key.
You can obtain the AK from the access key list and SK from the downloaded CSV file.
- For details about how to obtain a temporary AK/SK, see the IAM API Reference.
- Keep the CSV file properly. You can only download the file right after the access key is created. However, if you cannot find the file to obtain the key information, you can create a key.
- Open the CSV file in the lower left corner, or choose Downloads in the browser and open the CSV file.
- For security purposes, keep your access keys secure and change them periodically.
Generating a Signature
Generate a signature in the same way as in App authentication mode. Replace AppKey with AK and replace AppSecret with SK to complete the signing and request processing. You can sign requests to access APIs by using Java, Go, Python, C#, JavaScript, PHP, C++, C, and Android.
- The local time on the client must be synchronized with the clock server to avoid a large error in the value of the X-Sdk-Date request header.
- APIG (API Management) checks the time format and compares the time with the time when APIG (API Management) receives the request. If the time difference exceeds 15 minutes, APIG will reject the request.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





