Assigning Permissions to an IAM User
IAM users created without being added to any groups do not have any permissions. The administrator can assign permissions to these IAM users on the IAM console. IAM users can also assign permissions to themselves. After authorization, the users can use cloud resources in your account as specified by their permissions.
Constraints
A maximum of 500 permissions (including system-defined permissions and custom policies) can be assigned to each IAM user for enterprise projects.
Procedure
- Log in to the IAM console as the administrator.
- In the user list, click Authorize in the row that contains the target user.
Figure 1 Authorizing an IAM user
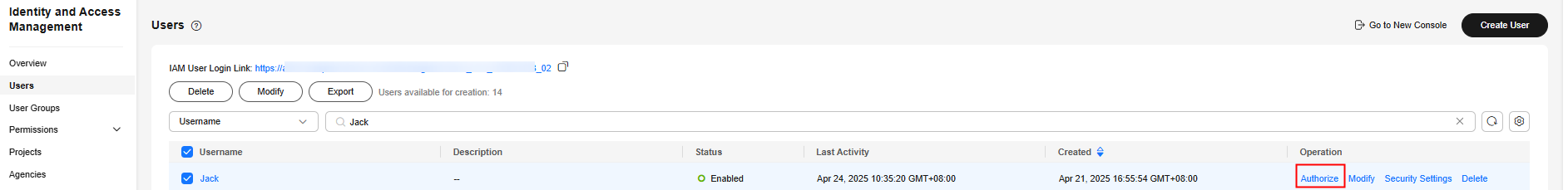
- On the Authorize User page, select an authorization mode and permissions.
- Inherit permissions from user groups: Add the IAM user to certain groups to inherit their permissions.
If you select this option, select the user groups which the user will belong to.
Figure 2 Enterprise Project function not enabled
- Select permissions: Directly assign specific permissions to the IAM user. You can assign permissions directly to IAM users only when Enterprise Project is enabled. To enable Enterprise Project, see Enabling the Enterprise Project Function.
If you select this option, select permissions, click Next in the lower right, and then go to step 4.
Figure 3 Enterprise project function enabled
- If you add an IAM user to the default group admin, the user becomes an administrator and can perform all operations on all cloud services.
- If a user is added to multiple user groups, the user inherits the permissions assigned to all these groups.
- For details on the system-defined permissions of all cloud services supported by IAM, see System-defined Permissions.
- If you have enabled enterprise management, you cannot create subprojects in IAM.
- Inherit permissions from user groups: Add the IAM user to certain groups to inherit their permissions.
- On the Select Scope page, select enterprise projects that the IAM user can access. You do not need to perform this step if you have selected Inherit permissions from user groups.
- Click OK.
You can go to the Permissions > Authorization page and view or modify the permissions of the IAM user.
In the enterprise project authorization, if OBS permissions are assigned, they will be applied about 15 to 30 minutes after the authorization is complete.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





