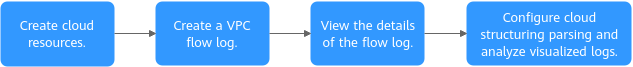
Viewing the Traffic of ECSs from the Same VPC
Solution Architecture

Constraints
For details about the restrictions on flow logs, see Constraints.
Resource Planning
The following resource details are only for your reference. You can modify them if needed.
|
Resource |
Quantity |
Description |
|---|---|---|
|
VPC and subnet |
VPC: 1 Subnet: 2 |
|
|
ECS |
2 |
Configure the two ECSs as follows:
|
|
VPC flow log |
1 |
|
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|---|---|---|---|---|---|
|
Inbound |
Allow |
IPv4 |
TCP: 22 |
Source: 0.0.0.0/0 |
Allows remote logins to Linux ECSs over SSH port 22. |
|
Inbound |
Allow |
IPv4 |
TCP: 3389 |
Source: 0.0.0.0/0 |
Allows remote logins to Windows ECSs over RDP port 3389. |
|
Inbound |
Allow |
IPv4 |
All |
Source: current security group (Sg-X) |
Allows the ECSs in Sg-X to communicate with each other using IPv4 addresses. |
|
Inbound |
Allow |
IPv6 |
All |
Source: current security group (Sg-X) |
Allows the ECSs in Sg-X to communicate with each other using IPv6 addresses. |
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows ECSs in Sg-X to access the external networks using IPv4 addresses. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows ECSs in Sg-X to access the external networks using IPv6 addresses. |

If the source of an inbound rule is set to 0.0.0.0/0, all external IP addresses are allowed to remotely log in to your instances. Exposing port 22 or 3389 to the public network will leave your instances vulnerable to network risks. To address this issue, set the source to a trusted IP address, for example, the IP address of your local PC.
|
Security Group |
Direction |
Action |
Type |
Protocol & Port |
Source |
Description |
|---|---|---|---|---|---|---|
|
Sg-X |
Inbound |
Allow |
IPv4 |
All |
Security group Sg-A |
Allows IPv4 traffic from ECSs in Sg-A to reach ECSs in Sg-X. |
|
Sg-A |
Inbound |
Allow |
IPv4 |
All |
Security group Sg-X |
Allows IPv4 traffic from ECSs in Sg-X to reach ECSs in Sg-A. |
Procedure
Figure 2 shows the process for viewing the traffic of ECSs in a VPC.
Step 1: Create Cloud Resources
- Create a VPC with two subnets.
For details, see Creating a VPC and Subnet.
- Create two ECSs.
For details, see Purchasing an ECS in Custom Config Mode.
Step 2: Create a VPC Flow Log
- Create a log group and log stream on the LTS console.
For details about how to create a log group, see Creating a Log Group.
For details about how to create a log stream, see Creating a Log Stream.
- Create a VPC flow log.
For details, see Creating a VPC Flow Log.
Step 3: View the VPC Flow Log
The flow log collects the information about the traffic flowing through the network interface attached to ECS-01.
- Remotely log in to ECS-01.
For details, see How Do I Log In to My ECS?
- Ping ECS-02 from ECS-01 and collect logs:
ping <private-IP-address-of-ECS-02>
Example command:
ping 192.168.1.31
Information similar to the following is displayed. You can view the flow log records in about 10 minutes. Do not stop the ping command during flow log collection.[root@ecs-01 ~]# ping 192.168.1.31 PING 192.168.1.31 (192.168.1.31) 56(84) bytes of data. 64 bytes from 192.168.1.31: icmp_seq=1 ttl=64 time=0.292 ms 64 bytes from 192.168.1.31: icmp_seq=2 ttl=64 time=0.186 ms 64 bytes from 192.168.1.31: icmp_seq=3 ttl=64 time=0.162 ms ...
- Wait for about 10 minutes and view the VPC flow log information by referring to Viewing a VPC Flow Log.
You can enter the IP address (192.168.1.31) of ECS-02 in the search box to quickly filter the logs of the communication between ECS-01 and ECS-02.
Figure 3 Viewing logs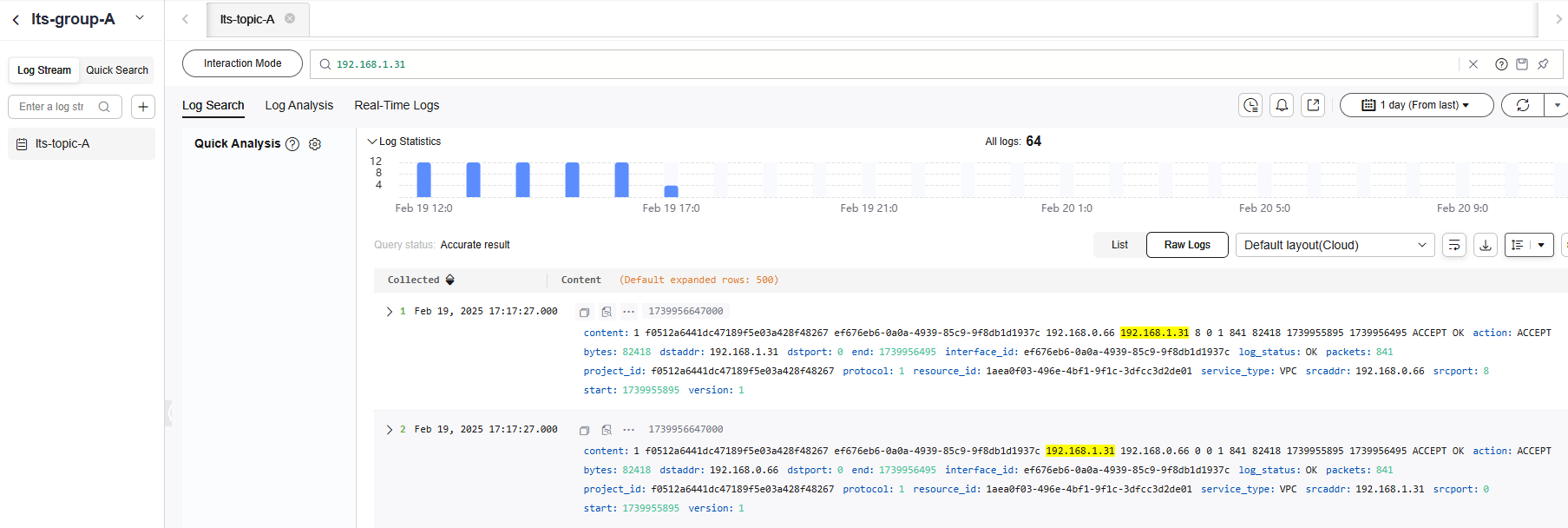 The flow log record is in the following format:
The flow log record is in the following format:<version> <project-id> <interface-id> <srcaddr> <dstaddr> <srcport> <dstport> <protocol> <packets> <bytes> <start> <end> <action> <log-status>
- Example log: 1 f0512a6441dc47189f5e03a428f48267 ef676eb6-0a0a-4939-85c9-9f8db1d1937c 192.168.0.66 192.168.1.31 8 0 1 585 57330 1739877133 1739877733 ACCEPT OK
- Log description: The VPC flow log version is 1. The log shows that 585 echo request packets (type=8,code=0) were sent from the source (192.168.0.66) to the destination (192.168.1.31) via the network interface ef676eb6-0a0a-4939-85c9-9f8db1d1937c using ICMP (protocol=1) during 19:12:13 to 19:22:13 (10 minutes), on February 18, 2025. The size of all packets is 57,330 bytes.
For details about flow log data, see VPC Flow Log Data.
Step 4: Configure Cloud Structuring Parsing and Analyze Visualized Logs for the VPC Flow Log
- Configure cloud structuring parsing.
Table 4 shows the parameter settings in this example. For details, see Cloud Structuring Parsing.
Figure 4 Configuring cloud structuring parsing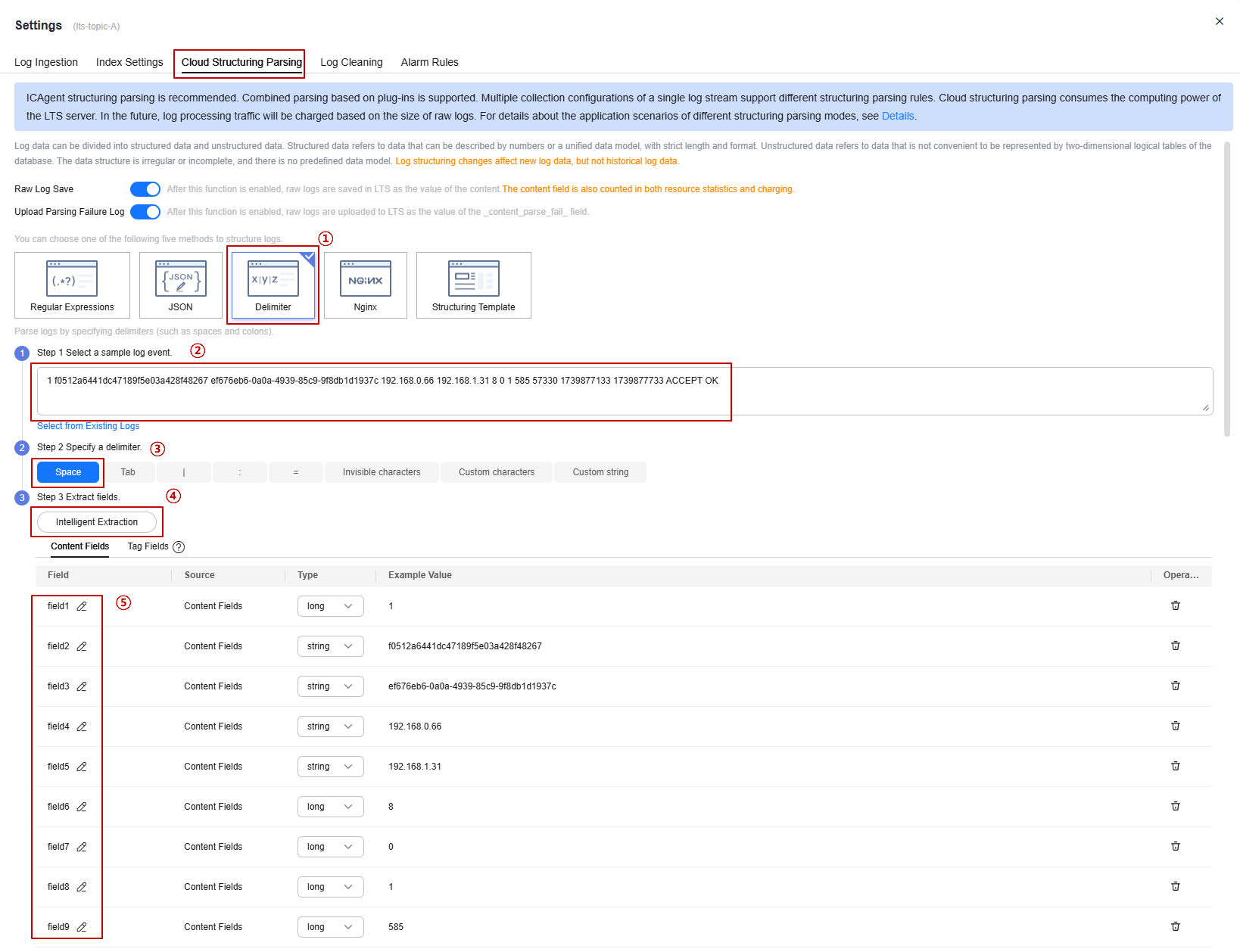
Table 4 Parameters for configuring cloud structuring parsing Step
Operation
1
Set the structuring mode to Delimiter.
2
Enter the VPC flow log:
1 f0512a6441dc47189f5e03a428f48267 ef676eb6-0a0a-4939-85c9-9f8db1d1937c 192.168.0.66 192.168.1.31 8 0 1 585 57330 1739877133 1739877733 ACCEPT OK
3
Select Space as the delimiter.
4
Click Intelligent Extraction.
5
In the intelligent extraction field list, change the field name to the flow log parameters:
version, project-id, interface-id, srcaddr, dstaddr, srcport, dstport, protocol, packets, bytes, start, end, action, and log-status
- Analyze the logs based on the cloud structuring parsing.
The following shows two visualized log analysis methods:
- Visualize logs in statistical charts. Statistical charts, such as tables, bar charts, and line charts, are rendered by LTS based on SQL query syntax.
- On the Log Analysis tab, enter the required statement in the search box by referring to Using SQL Analysis Syntax to obtain the required logs.
The following takes the traffic of ECS-01 every hour as an example.
SELECT TIME_FORMAT(TIME_CEIL(__time, 'PT1H'), 'yyyy-MM-dd HH:mm:ss') as "time", count(1) as pv group by "time"
- On the right of the page, configure the time and other information.
In this example, you can view the hourly traffic data within a day. For more information about the statistical charts, see Statistical Charts.
Figure 5 Traffic line chart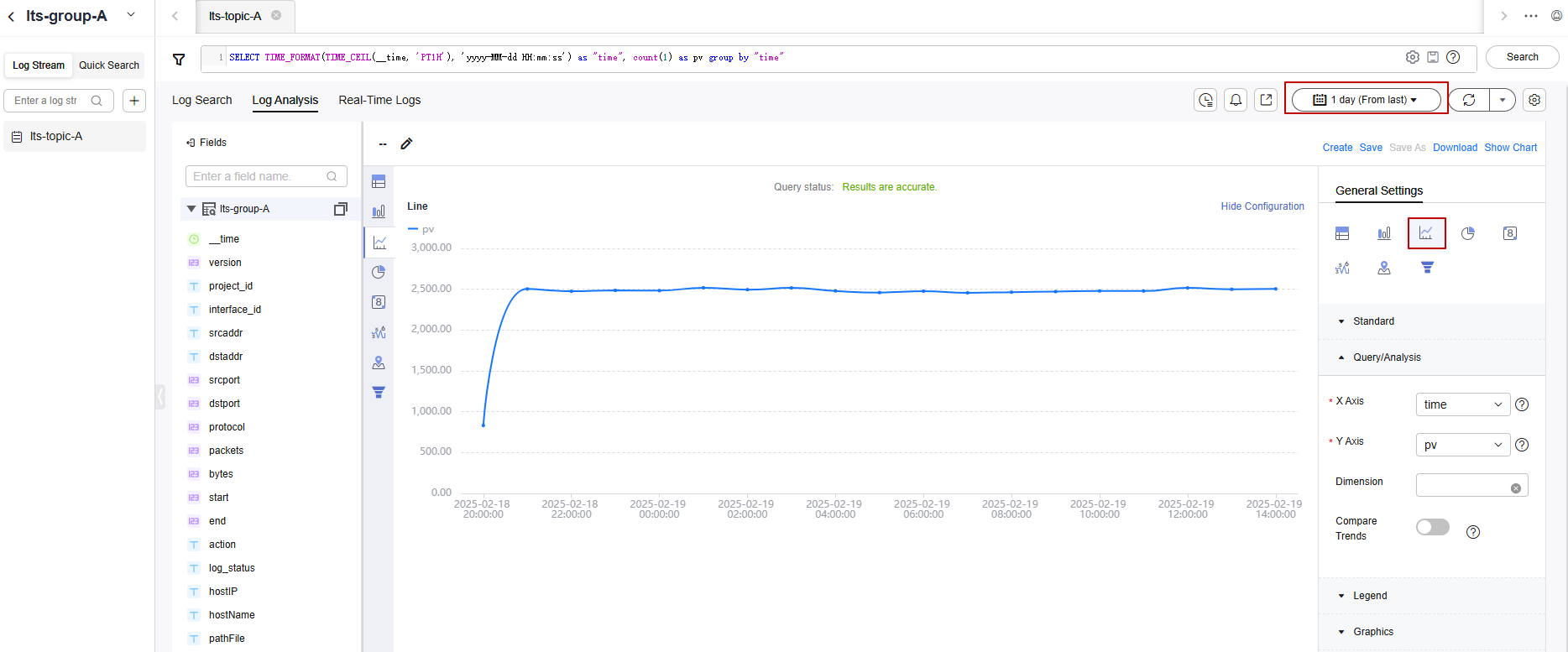
- On the Log Analysis tab, enter the required statement in the search box by referring to Using SQL Analysis Syntax to obtain the required logs.
- Visualize logs in dashboards. The dashboard is a real-time data visualization tool provided by LTS.
- Ingest VPC logs to LTS by referring to Ingesting VPC Logs to LTS.
- After VPC logs are ingested, choose Dashboards > VPC dashboard templates > VPC Flow Logs on the LTS console.
Wait for a few minutes and view the log data. For more information about the dashboard, see VPC Dashboard Template.
Figure 6 VPC flow log dashboard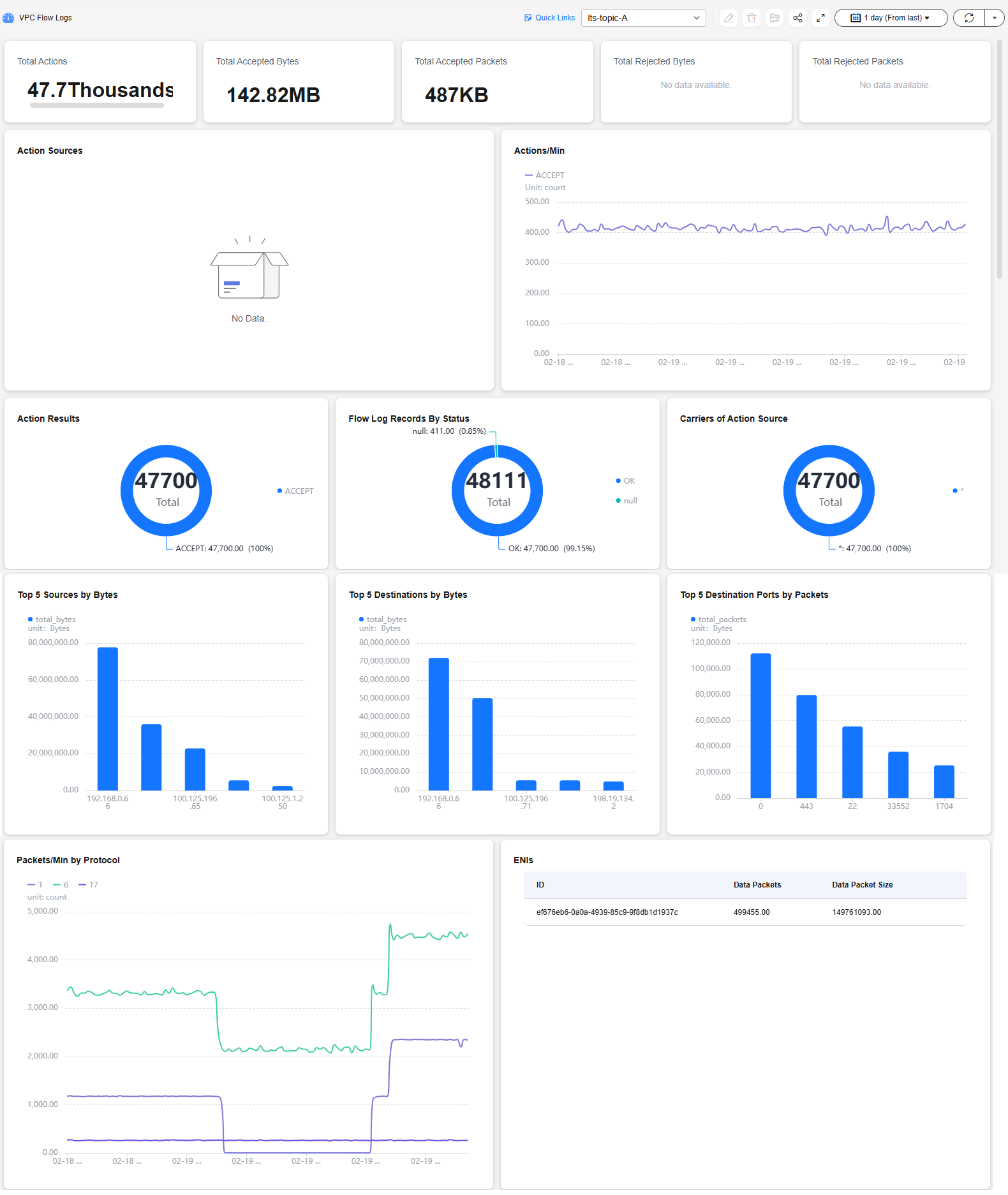
- Visualize logs in statistical charts. Statistical charts, such as tables, bar charts, and line charts, are rendered by LTS based on SQL query syntax.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot