Ransomware Prevention Overview
What Is Ransomware Prevention?
Ransomware emerged with the Bitcoin economy. It is a Trojan that is disguised as a legitimate email attachment or bundled software and tricks you into opening or installing it. It can also arrive on your servers through website or server intrusion. Once a system is attacked by ransomware, most of its important files will be encrypted. You can obtain file restoration keys only after paying high ransom to the attacker. This not only causes service interruption, data leakage, or data loss, but also lead to economic loss.
HSS provides ransomware prevention to detect and defend against ransomware. It can automatically back up data either at a scheduled time, or immediately if ransomware is detected. This can help you defend against ransomware and reduce loss.
Ransomware Prevention Principles
- Defending against known ransomware in real time
HSS has a virus sample library of billions of samples, covering all the known ransomware families. HSS coordinates local and cloud antivirus. On local servers, it uses the proprietary third-generation antivirus engine to detect ransomware attacks. In the cloud antivirus center, it uses behavior analysis, intelligence, AI models, and multi-engine detection to identify and block ransomware.
- Using honeypots to detect and block unknown ransomware
- Linux
You can deploy static and dynamic honeypot files on servers to make directory traps, capturing possible ransomware encryption behaviors in real time. If the action of a ransomware prevention policy is set to Report alarm and isolate, once an abnormal behavior is identified, an alarm will be reported and the file encryption process will be blocked immediately.
- Windows
You can deploy static honeypot files on servers to make directory traps, capturing possible ransomware encryption behaviors in real time. AI ransomware detection algorithms are used to identify the feature segments, fingerprints, and suspicious behaviors of virus-infected files and to block them.
- Linux
- Protecting data integrity through backup
HSS works with CBR to back up data to defend against ransomware. After this function is enabled, you can configure a policy to periodically back up server data. If a ransomware attack is detected, HSS will immediately trigger backup to ensure server data integrity and reduce service loss.
Figure 1 Backup to defend against ransomware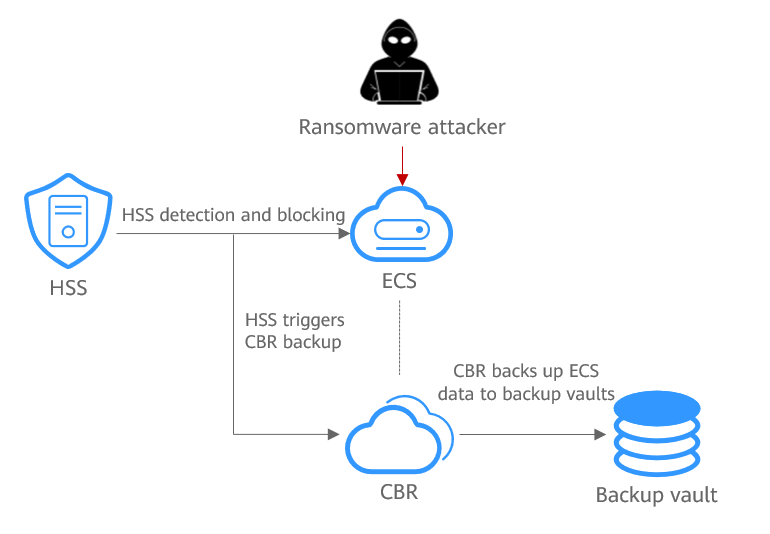
Constraints
- Only the HSS premium, WTP, and container editions support ransomware prevention. For details about how to purchase and upgrade HSS, see Purchasing an HSS Quota and Upgrading a Protection Quota.
- If the agent of version 3.2.10 or later is installed on a Linux server, or the agent of version 4.0.22 or later is installed on a Windows server, and the HSS premium, WTP, or container edition is enabled for the server, HSS will automatically enable ransomware prevention for the server, but will not automatically enable ransomware backup. You can enable it as needed. If the agent version installed on the server is not in the preceding range, you need to manually enable ransomware prevention and backup.
- Ransomware prevention is a systematic project that involves multiple aspects, including security management and technical defense. As an important part of ransomware prevention, HSS helps to identify and block ransomware, but it cannot defend against all ransomware. To minimize the loss caused by ransomware, you are advised to build a systematic protection solution, including but not limited to reducing exposure to the the Internet, strengthening network access control, strictly managing account permissions, and building a highly reliable service architecture. In addition, you are advised to periodically back up important service data, so that services can be quickly restored through backup if a ransomware attack occurs, thus reducing interruptions.
Process of Using Ransomware Prevention

|
Operation |
Description |
|---|---|
|
Enable ransomware prevention for a server, deploy static and dynamic honeypots, and detect ransomware attacks in real time.
CAUTION:
If you find suspicious files on a server after enabling ransomware prevention, submit a service ticket to contact technical support and check whether the files are the honeypots deployed by HSS. Honeypot files are used to detect ransomware attacks. They do not affect your services, do not contain any malicious content, and cannot be manually deleted.
|
|
|
So far, no tools can defend against all ransomware. Servers need to be periodically backed up, so that data can be restored using the backup in a timely manner to reduce loss if a ransomware event occurs. |
|
|
Once a ransomware attack is detected during ransomware protection, analyze and isolate the ransomware in a timely manner, and fix the security weaknesses of the system. |
|
|
If ransomware intrusion succeeds and your service data is lost, you can use the backup to restore data and reduce loss. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






