Creating a Workspace Agency
Workspace Agency Overview
A workspace agency can help improve security operations efficiency without requiring additional personnel. With a workspace agency, you can:
- Manage multiple workspaces centrally.
- View asset risks, alerts, and incidents in one place.
- Enable cross-account security operations.
For details about workspace agencies, see Table 1.
|
Function |
Feature |
Description |
|---|---|---|
|
Centralized security operations |
Situation Overview |
This area shows the security evaluation results from multiple workspaces managed by the workspace agency view. For more details, see Checking the Situation Overview. |
|
Large Screen |
Security data from multiple workspaces can be displayed and managed on one large screen. For details, see Overall Situation Screen and Monitoring Statistics Screen. |
|
|
Security Reports |
This area displays all security reports of workspaces managed by the agency view. You can view the security reports by workspace. The name of the workspace a security report belongs to is displayed next to the security report name. For more details, see Checking a Security Report. |
|
|
Unified asset management |
Resource Manager |
This area displays all assets of workspaces managed by the agency view. Assets are managed centrally. You can identify the workspace an asset belongs to based on the Workspace Name column in the asset list. For more details, see Overview. |
|
Unified risk prevention |
Baseline Inspection |
You can aggregate the baseline check results from multiple workspaces into an agency view for centralized management. For more details, see Viewing Baseline Check Results, Starting an Immediate Baseline Check, and Check Result Feedback. You can identify the workspace a check item belongs to based on the Workspace Name column in the check result list. |
|
Vulnerabilities |
You can aggregate vulnerability information from workspaces managed by the agency view and view them centrally. For more details, see Overview. You can identify the workspace to which a vulnerability belongs based on the Workspace Name column of the vulnerability. |
|
|
Security Policies |
You can aggregate security policies from multiple workspaces into an agency view for centralized management. For more details, see Adding an Emergency Policy and Managing Emergency Policies. On the page of the workspace agency view, you can identify the workspace a security policy belongs to based on the Workspace Name column in the security policy list. |
|
|
Unified threat operations |
Incidents |
You can aggregate incidents from multiple workspaces into an agency view for centralized management. For more details, see Viewing Incidents, Adding and Editing an Incident, and Closing and Deleting an Incident. On the page in the workspace agency view, you can identify the workspace an incident belongs to based on the Workspace Name column in the incident list. |
|
Alerts |
You can aggregate alerts from multiple workspaces into an agency view for centralized management. For more details, see Viewing Alert Details, Converting an Alert into an Incident or Associating an Alert with an Incident, Closing and Deleting an Alert, Adding and Editing an Alert, and one-click blocking or unblocking. On the page in the workspace agency view, you can identify the workspace an alert belongs to based on the Workspace Name column in the alert list. |
|
|
Indicators |
You can aggregate indicators from multiple workspaces into an agency view for centralized management. For more details, see Viewing Indicators and Adding and Editing an Indicator. On the page in the workspace agency view, you can identify the workspace an indicator belongs to based on the Workspace Name column in the indicator list. |
|
|
Log Audit |
Overview |
You can learn about the overall log audit status in a statistical period by workspace. |
|
Security Data |
You can view and manage data spaces by workspace. For more details, see Overview. |
|
|
Cloud Service Access |
You can view and manage log data by workspace. For more details, see Cloud Service Log Access Supported by SecMaster and Enabling Log Access. |
|
|
Modeling Analysis |
Intelligent Modeling |
You can view and manage resources by workspace. Viewing Model Templates, Creating and Editing a Model, Viewing a Model, and Managing Models are supported. |
|
Security Orchestration |
Playbooks |
You can view and manage playbooks by workspace. For details, see Overview. |
|
Layouts |
You can view and manage layouts by workspace. For more details, see Viewing Layouts and Viewing a Layout Template. |
|
|
Plugins |
You can view and manage plugins by workspace. For details, see Viewing Plugin Details. |
Workspace Hosting Process
The process of hosting a workspace is as follows.
|
Procedure |
Description |
|---|---|
|
You need to create an agency view to manage the delegation that other users give you for workspace hosting. |
|
|
You can create agencies to authorize other users to manage your workspaces in a project. In this way, asset risks, alerts, and incidents across workspaces can be centrally managed for security operations. |
|
|
You need to grant permission to other users to manage your workspaces and they need to accept your delegation to attach your workspaces to their workspaces.
The accepted workspaces will be attached to your workspaces. |
Limitations and Constraints
- The specifications of the workspace agency views and the number of workspaces are as follows:
- Constraints on workspace agency views: Only one workspace agency view can be created in a region for an account.
- Constraints on managed workspaces:
- Single-region scenario: A maximum of 100 workspaces can be managed by a workspace agency view.
- Cross-region scenario: A maximum of 10 workspaces can be managed by a workspace agency view.
- If you want to use one agency view to manage workspaces in excessive of the limit, submit a service ticket to apply for capacity expansion.
- Restrictions: A maximum of 10 agencies can be created by an account.
- If you select Organization for Initiated By while creating an agency, there are some limitations you need to know:
- If you select all accounts under all organizations for the agency, the agency will work for workspaces of new accounts of an organization.
- If you select all accounts of a specific organization for the agency, it takes a while for workspaces of new accounts of the organization to be synchronized to the agency.
Video Tutorial
This video shows how to create and manage a workspace agency.
Step 1: Create an Agency View
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose .
Figure 1 Agencies

- On the Agency Views tab, click Create Agency View. The Create Agency View slide-out panel is displayed.
Figure 2 Creating an agency view

- Configure parameters required for creating the agency view.
Table 3 Parameters for creating an agency view Parameter
Description
Agency View Name
Name of the agency view. Configuration constraints:
- Only letters (A to Z and a to z), numbers (0 to 9), and the following special characters are allowed: -_()
- A maximum of 64 characters are allowed.
Workspace Name
The workspace you want to associate with the agency view. The workspace you associate is the main workspace.
(Optional) Description
Description of the agency view. Enter a maximum of 512 characters.
- Click OK.
The created agency view will be displayed on the Agency Views tab.
Step 2: Create an Agency
- In the navigation pane on the left, choose .
Figure 3 Agencies

- On the Agencies page, click Create Agency in the upper right corner of the page.
- On the Create Agency slide-out is displayed, configure agency parameters.
Table 4 Parameters for creating an agency Parameter
Description
Initiated By
Agency creator.
- Current Tenant
- Organization: If you use an administrator account of an organization or an agency account to log in to SecMaster, you can select a workspace under the organization for workspace hosting.
The Organizations service is an account management service that enables you to consolidate multiple accounts into an organization so that you can centrally manage these accounts. For details, see Overview of Organizations.
Agency Created By
Workspace
If you select Current account for Initiated By, you need to select a workspace you want to authorize others to manage.
Account
If you select Organization for initiated By, you need to select an account for the agency.
Agency Accepted By
Account
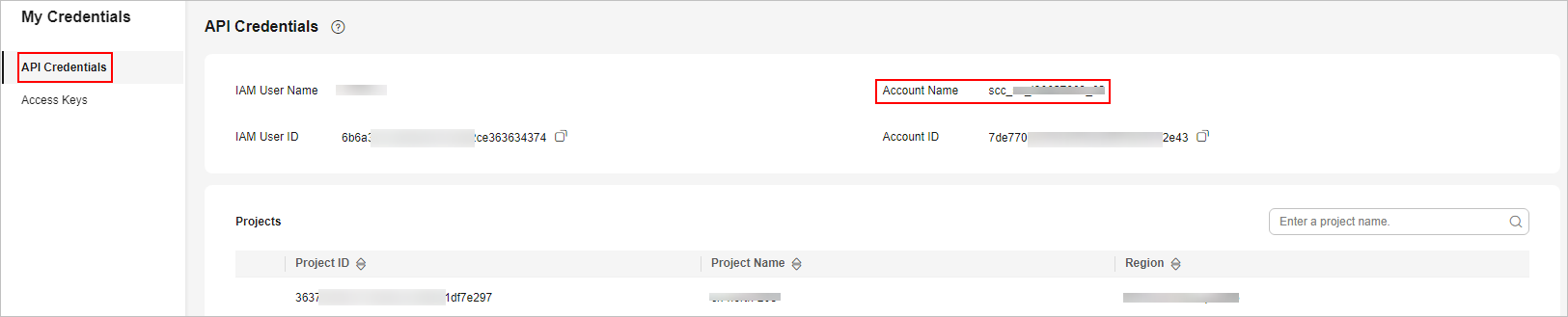
Account name of the user who delegates the management permission to this agency. You can also enter the current account as the agency account, or obtain the account name as follows:
- You have logged in to the SecMaster console. Move the cursor to the username in the upper right corner and select My Credentials from the drop-down list. The API Credentials page is displayed by default.
- On the API Credentials page, obtain the Account Name.
Figure 4 Account Name
Agency View
An existing agency view. If there are no agency views, click Create Agency View and create one. For details, see Step 1: Create an Agency View.
Agency Details
Agency Name
Name of the agency. Configuration constraints:
- Only letters (A to Z and a to z), numbers (0 to 9), and the following special characters are allowed: -_()
- A maximum of 64 characters are allowed.
Agency Duration
Select an agency duration. Only Permanent is supported.
Agency Policy
Select an agency policy. An agency policy defines the operation permissions a user has for managed workspaces. You can select multiple agency policies at a time.
You can query the meaning of a policy in IAM. To view the meaning, perform the following steps:
- You have logged in to the SecMaster console. Move the cursor to the username in the upper right corner and select Identity and Access Management from the drop-down list. The IAM console is displayed.
- In the navigation pane on the left, choose . On the Policies page, enter the policy name in the search box.
View the meaning and scope of the policy.
Description
Description of the agency. Enter a maximum of 512 characters.
- Click OK.
Step 3: Authorize an Agency
- In the navigation pane on the left, choose .
Figure 5 Agencies

- On the Agencies page, click the Workspaces Managed by Me tab. In the row containing the workspace you want to manage, click Accept in the Operation column.
If the system displays a message indicating that you are not authorized when you try to accept an agency, get authorization by referring to Authorizing SecMaster first.
- In the displayed dialog box, click OK.
Follow-up Operations
Choose Workspaces > Management, click the name of the created agency view. You can view details about workspaces managed in the agency view.
Related Operations
- Editing an agency view
- Locate the row that contains the agency view, and click Edit in the Operation column.
- On the Edit Agency View slide-out panel, modify the parameters and click OK.
- Deleting an agency view
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





