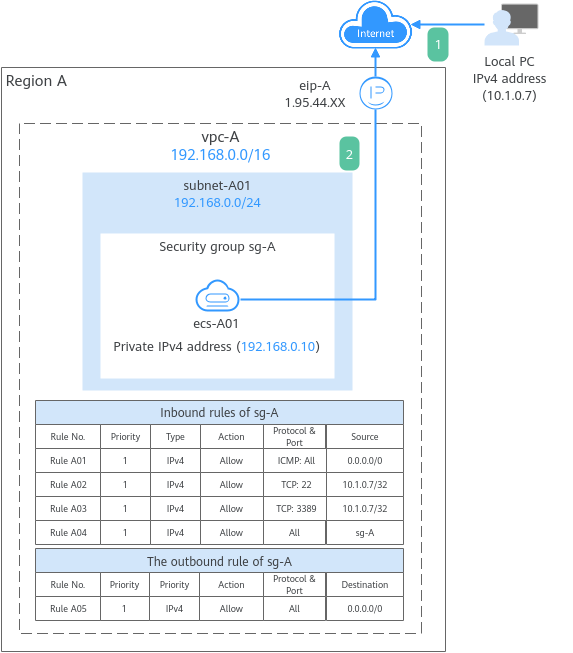
Setting Up an IPv4 Network in a VPC
This topic describes how to use a VPC to provide an ECS with an IPv4 private network on the cloud and bind an EIP to the ECS to allow the ECS to communicate with the Internet.
- To allow users to remotely log in to ECS-A01 from the local PC (IP address: 10.1.0.7) and perform operations on this ECS, you need to add the following inbound rules:
- Rule A01: allows ping to test ECS-A01 network connectivity.
- Rule A02: allows remote logins to ECS-A01 if the ECS runs Linux.
- Rule A03: allows remote logins to ECS-A01 if the ECS runs Windows.
- Rule A04: allows ECSs in the security group to communicate with each other.
- To allow ECS-A01 to access the Internet, you need to add an outbound rule.
Precautions
The network planning in this topic is only for your reference. Once a VPC and subnet are created, the CIDR blocks cannot be changed. Before creating VPCs, determine how many VPCs and subnets, and what CIDR blocks or connectivity options you will need.
For details, see VPC and Subnet Planning Suggestions.
Procedure
|
Procedure |
Description |
|---|---|
|
Before using cloud services, sign up for a HUAWEI ID, enable Huawei Cloud services, and complete real-name authentication. |
|
|
Create a VPC with an IPv4 CIDR block and a subnet.
|
|
|
Buy an ECS in the subnet you have created and configure security group rules for the ECS. |
|
|
Buy an EIP and bind it to the ECS so that the ECS can access the Internet. |
|
|
To test ECS connectivity, you can:
|
Preparations
Before creating resources such as VPCs and ECSs, you need to sign up for a HUAWEI ID and enable Huawei Cloud services.
If you already have a HUAWEI ID, skip this part.
Step 1: Create a VPC and Subnet
- Go to the page for creating a VPC.
- On the Create VPC page, set parameters as needed.
In this example, you need to create a VPC and a subnet.
Figure 2 Setting a subnet
Table 1 VPC parameters Parameter
Example Value
Description
Region
CN-Hong Kong
The region where the VPC is created. Select the region nearest to you to ensure the lowest possible latency. The VPC, ECS, and EIP used in this example must be in the same region.
The region cannot be changed after the VPC is created.
Name
VPC-A
The VPC name.
This parameter can be changed after the VPC is created.
IPv4 CIDR Block
192.168.0.0/16
The IPv4 CIDR block of the VPC. You are advised to select from the following CIDR blocks:- 10.0.0.0/8–24: The IP address ranges from 10.0.0.0 to 10.255.255.255, and the netmask ranges from 8 to 24.
- 172.16.0.0/12–24: The IP address ranges from 172.16.0.0 to 172.31.255.255, and the netmask ranges from 12 to 24.
- 192.168.0.0/16–24: The IP address ranges from 192.168.0.0 to 192.168.255.255, and the netmask ranges from 16 to 24.
The IPv4 CIDR block cannot be changed after the VPC is created.
Enterprise Project
default
The enterprise project by which resources are centrally managed. Select an existing enterprise project for the VPC.
The enterprise project cannot be changed after the VPC is created.
Monitor subnet IP address usage
No configuration is required.
Configure it as required. If this option is enabled, Cloud Eye will monitor the IPv4 address usage of all subnets in the current VPC.
This parameter can be changed after the VPC is created.
This parameter is available only in certain regions. You can check the regions on the console.
Block Access to Service Endpoints
No configuration is required.
Configure it as required. If this option is enabled, the VPC loses direct access to service endpoints over the private network.
This parameter can be changed after the VPC is created.
This parameter is available only in certain regions. You can check the regions on the console.
Advanced Settings (Optional) > Tag
No configuration is required.
The tag that is used to classify and identify resources. Add tags to the VPC as required.
After the VPC is created, you can edit tags added to the VPC.
Advanced Settings (Optional) > Description
No configuration is required.
Supplementary information about the VPC. Enter a description as required.
This parameter can be changed after the VPC is created.
Table 2 Subnet parameters Parameter
Example Value
Description
Subnet Name
Subnet-A01
The subnet name.
The name can be modified after the subnet is created.
IPv4 CIDR Block
192.168.0.0/24
The IPv4 CIDR block of the subnet, which is a unique CIDR block with a range of IP addresses in the VPC.
The CIDR block cannot be changed after the subnet is created.
IPv6 CIDR Block (Optional)
Disabled
Whether to automatically assign an IPv6 CIDR block to the subnet.
You can enable or disable this option after the subnet is created.
Associated Route Table
Default
The default route table that the subnet is associated with. Each VPC comes with a default route table. Subnets in the VPC are then automatically associated with the default route table.
The default route table has a preset system route that allows subnets in a VPC to communicate with each other.
After the subnet is created, you can create a custom route table and associate the subnet with it.
Advanced Settings (Optional) > Gateway
192.168.0.1
The gateway address of the subnet. You are advised to retain the default address.
The gateway address cannot be changed after the subnet is created.
Advanced Settings (Optional)- DNS Server Address
- Domain Name
- NTP Server Address
- IPv4 DHCP Lease Time
No configuration is required.
The parameters that are configured for the ECS in the VPC. In this example, retain the default values or leave them blank.
You can change the values after the subnet is created.
Advanced Settings (Optional) > Tag
No configuration is required.
The tag that is used to classify and identify resources. Add tags to the subnet as required.
After the subnet is created, you can edit the tags added to the subnet.
Advanced Settings (Optional) > Description
No configuration is required.
Supplementary information about the subnet. Enter a description as required.
This parameter can be changed after the subnet is created.
- Click Create Now.
You will be redirected to the VPC list, where you can find the VPC you have created.
Step 2: Buy an ECS
- Go to the page for buying an ECS.
- On the Buy ECS page, configure parameters as required.
In this example, set the ECS name to ECS-A01 and configure other parameters as follows:
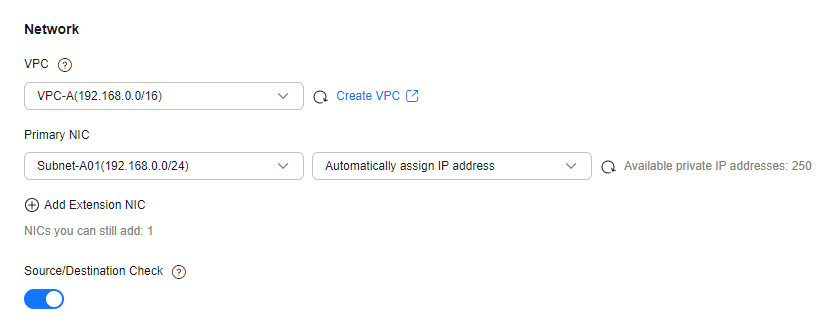
- Network: Select VPC-A and Subnet-A01 you have created.
Figure 3 Network settings
- Security Group: Create security group Sg-A and add inbound and outbound rules to it. Each security group comes with system rules. You need to check and modify the rules as required to ensure that all rules in Table 3 are added.
Figure 4 Inbound rules of Sg-A
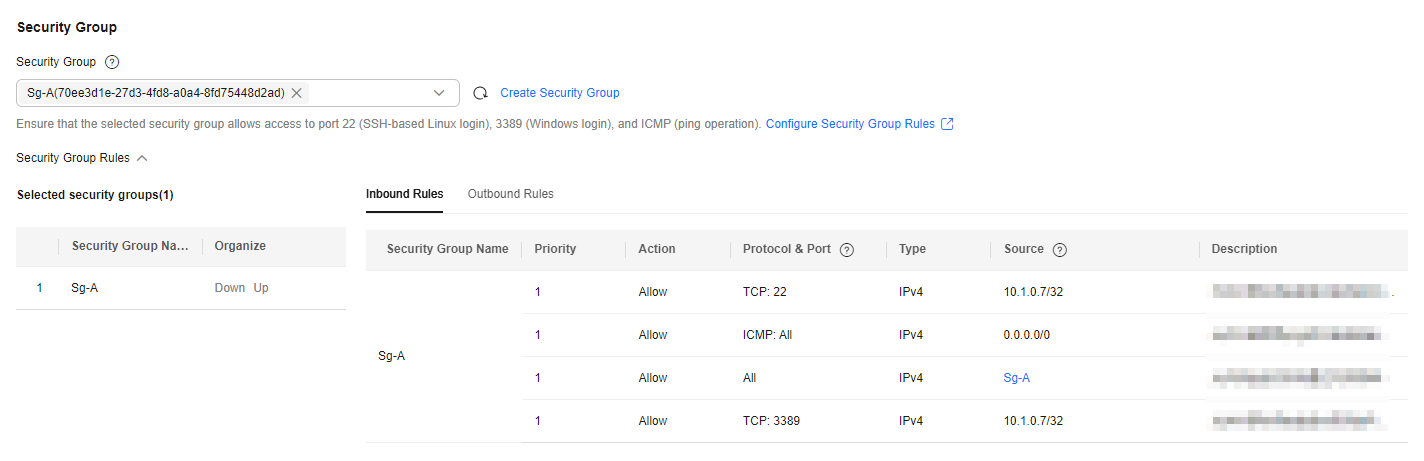 Figure 5 The outbound rule of Sg-A
Figure 5 The outbound rule of Sg-A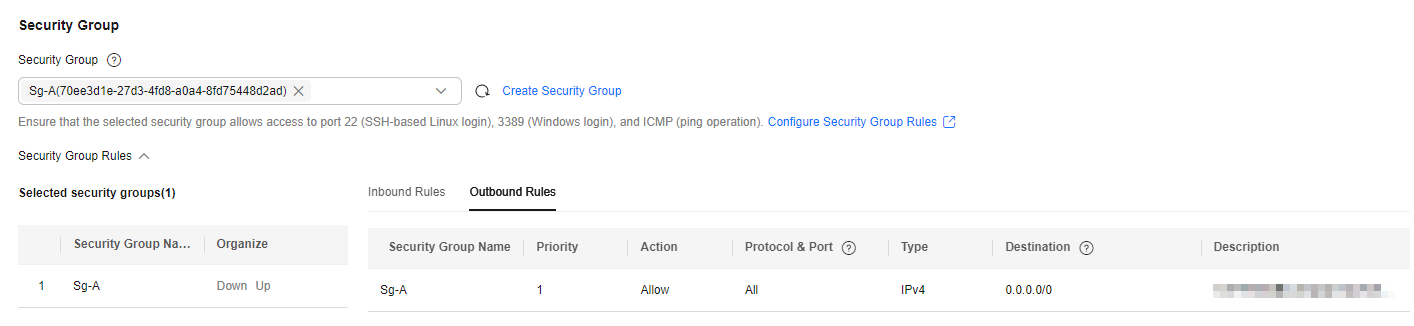
Table 3 Sg-A rules Direction
Action
Type
Protocol & Port
Source/Destination
Description
Inbound
Allow
IPv4
TCP: 22
Source: 10.1.0.7/32
Allows the local PC (10.1.0.7/32) to remotely log in to the Linux ECS over SSH port 22.
Inbound
Allow
IPv4
TCP: 3389
Source: 10.1.0.7/32
Allows the local PC (10.1.0.7/32) to remotely log in to the Windows ECS over RDP port 3389.
Inbound
Allow
IPv4
ICMP: All
Source: 0.0.0.0/0
Allows ping traffic to ECSs in the VPC over all ICMP ports to test network connectivity.
Inbound
Allow
IPv4
All
Source: current security group (Sg-A)
Allows the ECSs in the security group to communicate with each other.
Outbound
Allow
IPv4
All
Destination: 0.0.0.0/0
Allows the ECSs in the security group to access the external networks.
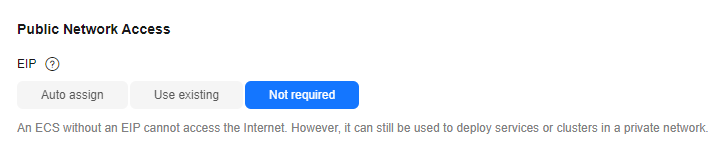
- EIP: Select Not required.
Figure 6 Selecting Not required
Configure other ECS parameters as required. For details, see Purchasing an ECS in Custom Config Mode.
- Network: Select VPC-A and Subnet-A01 you have created.
- Click Submit.
Return to the ECS list to view ECS-A01 you have bought.
Step 3: Buy an EIP and Bind It to the ECS
- Go to the Buy EIP page.
- On the Buy EIP page, configure the parameters as prompted.
You can configure other EIP parameters as required. For details, see Buying an EIP.
- Click Next.
Return to the EIP list to view EIP-A you have assigned.
- In the EIP list, locate EIP-A and click Bind in the Operation column.
The Bind EIP dialog box is displayed.
- In the displayed dialog box, select ECS-A01 and click OK.
Return to the EIP list. You can see that ECS-A01 is displayed in the Associated Instance column.
Step 4: Test Network Connectivity
- Use the local PC to remotely log in to ECS-A01.
Multiple methods are available for logging in to an ECS. For details, see Logging In to an ECS.
- Test the network connectivity between ECS-A01 and Internet:
ping <IPv4-EIP or Domain-name>
Example command:
ping support.huaweicloud.com
If information similar to the following is displayed, ECS-A01 can communicate with the Internet.[root@ecs-a01 ~]# ping support.huaweicloud.com PING hcdnw.cbg-notzj.c.cdnhwc2.com (203.193.226.103) 56(84) bytes of data. 64 bytes from 203.193.226.103 (203.193.226.103): icmp_seq=1 ttl=51 time=2.17 ms 64 bytes from 203.193.226.103 (203.193.226.103): icmp_seq=2 ttl=51 time=2.13 ms 64 bytes from 203.193.226.103 (203.193.226.103): icmp_seq=3 ttl=51 time=2.10 ms 64 bytes from 203.193.226.103 (203.193.226.103): icmp_seq=4 ttl=51 time=2.09 ms ... --- hcdnw.cbg-notzj.c.cdnhwc2.com ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3004ms rtt min/avg/max/mdev = 2.092/2.119/2.165/0.063 ms
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot