Using a Public NAT Gateway to Enable Servers to Be Accessed by the Internet
Scenarios
When one or more servers in a VPC need to provide services accessible from the Internet, you can add DNAT rules for a public NAT gateway, as introduced in this section.
Operation Process
|
Procedure |
Description |
|---|---|
|
Before using cloud services, sign up for a HUAWEI ID, enable Huawei Cloud services, complete real-name authentication, and top up your account. |
|
|
Assign an EIP. |
|
|
Create a public NAT gateway. |
|
|
Step 3: Add a Default Route Pointing to the Public NAT Gateway |
Add a route table. |
|
Add DNAT rules for the public NAT gateway so that servers in specific CIDR blocks share EIPs to access the Internet. |
|
|
Check whether the DNAT rule has been added. |
|
|
Step 6: Verify that Servers in a VPC Can Be Accessed from the Internet Through the NAT Gateway |
Verify that servers for which the DNAT rules are applied can be accessed by a client on the Internet. |
Preparations
Before using NAT gateways, sign up for a HUAWEI ID, enable Huawei Cloud services, complete real-name authentication, and top up your account.
Step 1: Assign an EIP
- Go to the Buy EIP page.
- On the Buy EIP page, set the EIP name to EIP-A.
You can configure other EIP parameters as required. For details, see Assigning an EIP.
- Click Next.
Return to the EIP list to view EIP-A you have assigned.
Step 2: Create a Public NAT Gateway
- Go to the Buy Public NAT Gateway page.
- On the Buy Public NAT Gateway page, configure required parameters.
Table 1 Descriptions of public NAT gateway parameters Parameter
Example
Description
Region
CN North-Beijing4
The region where the public NAT gateway is located.
Billing Mode
Pay-per-use
The billing mode of the public NAT gateway.
Specifications
Small
The specifications of the public NAT gateway.
The value can be Extra-large, Large, Medium, or Small. To view more details about specifications, click Learn more on the page.
Name
public-nat-01
The name of the public NAT gateway. Enter up to 64 characters. Only letters, digits, underscores (_), hyphens (-), and periods (.) are allowed.
VPC
vpc-A
The VPC that the public NAT gateway belongs to.
The selected VPC cannot be changed after you buy the public NAT gateway.
NOTE:To allow traffic to pass through the public NAT gateway, a route to the public NAT gateway in the VPC is required. When you buy a public NAT gateway, a default route 0.0.0.0/0 to the public NAT gateway is automatically added to the default route table of the VPC. If the default route 0.0.0.0/0 already exists in the default route table of the VPC before you buy the public NAT gateway, the default route that points to the public NAT gateway will fail to be added automatically. In this case, perform the following operations after the public NAT gateway is successfully created: Manually add a different route that points to the gateway or create a default route 0.0.0.0/0 pointing to the gateway in the new routing table.
Subnet
Subnet-A01
The subnet that the public NAT gateway belongs to.
The subnet must have at least one available IP address.
The selected subnet cannot be changed after you buy the public NAT gateway.
The NAT gateway will be deployed in the selected subnet. The NAT gateway works for the entire VPC where it is deployed. To enable communications over the Internet, add SNAT or DNAT rules.
Advanced Settings (Optional)
-
Click the drop-down arrow to configure advanced parameters of the public NAT gateway.
SNAT Connection TCP Timeout (s)
900
The timeout period of a TCP connection established using the SNAT rule. If no data is exchanged within this period, the TCP connection will be closed.
Value range: 40 to 7200
SNAT Connection UDP Timeout (s)
300
The timeout period of a UDP connection established using the SNAT rule. If no data is exchanged within this period, the UDP connection will be closed.
Value range: 40 to 7200
SNAT Connection ICMP Timeout (s)
10
The timeout period of an ICMP connection established using the SNAT rule. If no data is exchanged within this period, the ICMP connection will be closed.
Value range: 10 to 7200
TCP TIME_WAIT (s)
5
How long the side that actively closed the TCP connection is in the TIME_WAIT state.
Value range: 0 to 1800
Description
Not required
Supplementary information about the public NAT gateway. Enter up to 255 characters. Angle brackets (<>) are not allowed.
Tag
Not required
The identifier of the public NAT gateway. A tag is a key-value pair. You can add up to 20 tags to each public NAT gateway.
- Click Next. On the page displayed, confirm the public NAT gateway specifications.
- If you do not need to modify the information, click Submit.
On the Public NAT Gateways page, you can view the created public NAT gateway in the list.
Step 3: Add a Default Route Pointing to the Public NAT Gateway
- Go to the route table list page.
- On the Route Tables page, click Create Route Table in the upper right corner.
VPC: Select the VPC that the public NAT gateway belongs to.
- After the custom route table is created, click its name. The Summary page is displayed.
- Click Add Route and configure parameters as follows:
Destination: Set it to 0.0.0.0/0.
Next Hop Type: Select NAT gateway.
Next Hop: Select the created NAT gateway.
Figure 1 Add Route
- Click OK.
Step 4: Add a DNAT Rule
- Go to the public NAT gateway list page.
- On the displayed page, click the name of the public NAT gateway on which you need to add a DNAT rule.
- On the public NAT gateway details page, click the DNAT Rules tab.
- Click Add DNAT Rule.
- Configure required parameters. For details, see Table 2.
Figure 2 Add DNAT Rule
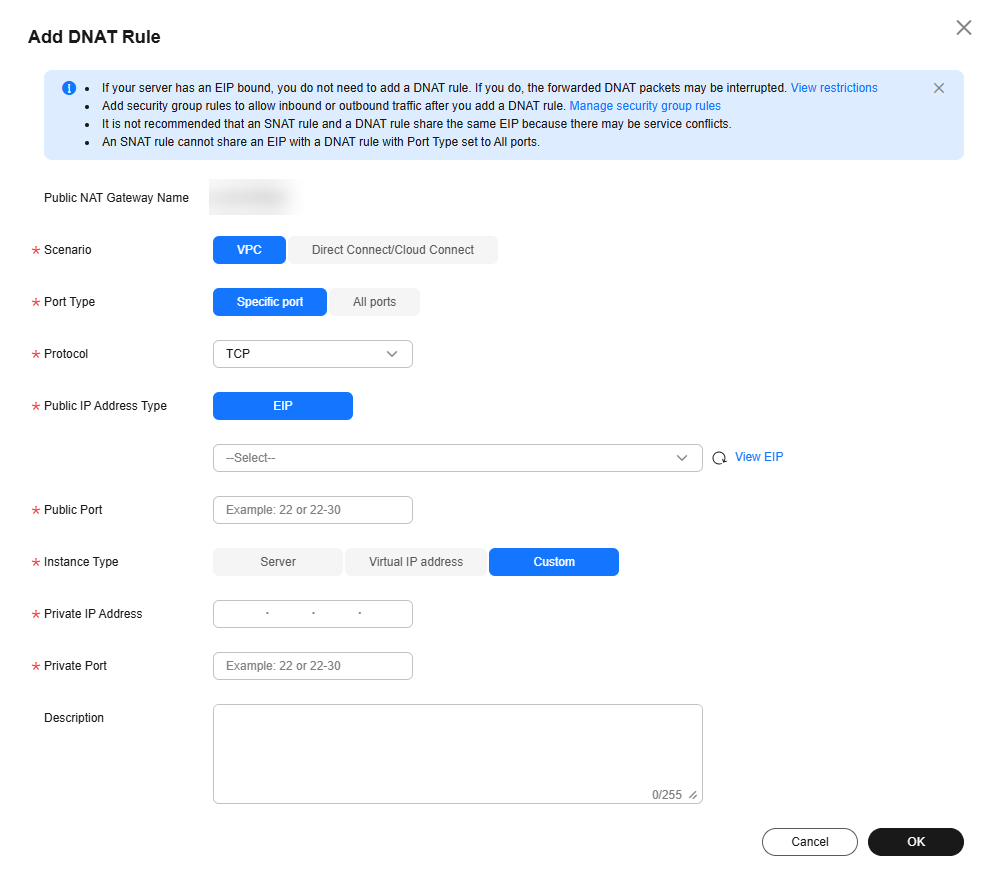
Table 2 Descriptions of DNAT rule parameters Parameter
Example
Description
Scenario
VPC
Select VPC if your servers in a VPC will use the DNAT rule to provide services accessible from the Internet.
Different servers in a VPC can share the same EIP to provide services accessible from the Internet.
Port Type
Specific port
The port type.
- All ports: All requests received by the gateway through all ports over any protocol will be forwarded to the private IP address of your server.
- Specific port: Only requests received from a specified port over a specified protocol will be forwarded to the specified port on the server.
Protocol
TCP
The protocol can be TCP or UDP. This parameter is available if you select Specific port for Port Type. If you select All ports, this parameter is All by default.
Public IP Address Type
EIP
The EIP of the public NAT gateway.
Public Port
80-100
The port of the EIP used by the NAT gateway. The port number ranges from 1 to 65535.
You can enter a specific port number or a port range, for example, 80 or 80-100.
Instance Type
Server
The instance type for which the DNAT rules are applied.
NIC
-
The network interface of the server.
Private Port
80-100
The port of the server that provides services accessible from the Internet through the DNAT rule. This parameter is available if you select Specific port for Port Type. The port number ranges from 1 to 65535.
You can enter a specific port number or a port range, for example, 80 or 80-100.
Description
Not required
Supplementary information about the DNAT rule. Enter up to 255 characters. Angle brackets (<>) are not allowed.
- Click OK.

After you add a DNAT rule, add rules to the security group associated with the servers to allow inbound or outbound traffic. Otherwise, the DNAT rule does not take effect. For details, see Adding a Security Group Rule.
Step 5: Verify that the DNAT Rule Has Been Added
- In the DNAT Rules tab, view details of the DNAT rule and check whether the DNAT rule has been created.
If Status of the SNAT rule is Running, the SNAT rule has been created.
Step 6: Verify that Servers in a VPC Can Be Accessed from the Internet Through the NAT Gateway
- Go to the ECS list page.
- Log in to ECS 02 with an EIP bound.
- On ECS 02, ping the EIP (120.46.131.153) to check whether ECS 01 on the private network can be accessed by ECS 02 on the public network through the NAT gateway.
Figure 3 Verification result

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





