Networks
Cluster Network Structure
- Node Networks
A node network assigns IP addresses to nodes in a cluster. You need to select a VPC subnet as the node network of the CCE cluster. The number of available IP addresses in a subnet determines how many nodes (including control plane nodes and worker nodes) can be created at most in a cluster. The number of nodes that can be created in a cluster is also determined by the container networks. For details, see Maximum Number of Pods That Can Be Created on a Node.
- Container Networks
A container network assigns IP addresses to pods in a cluster. CCE inherits the IP-Per-Pod-Per-Network network model of Kubernetes. That means each pod has an independent IP address on a network plane and all containers in a pod share the same network namespace. All pods in a cluster run in a directly connected flat network. They can access each other through their IP addresses without using NAT. Kubernetes only provides a network mechanism for pods. It does not directly configure pod networks. You can use specific container network add-ons to configure networks for pods and manage container IP addresses.
CCE supports the following types of container networks:
- Container tunnel networks: A container tunnel network is built on a node network using tunnel encapsulation, ensuring independence from the node network plane. In a CCE cluster, the container tunnel network uses VXLAN encapsulation, with Open vSwitch serving as the backend virtual switch. VXLAN encapsulates Ethernet packets into UDP packets, enabling tunnel-based transmission.
- VPC networks: A VPC network seamlessly combines VPC routing with the underlying network, making it ideal for high-performance scenarios. However, the maximum number of nodes allowed in a cluster is determined by the VPC route quota. Each node in a cluster that uses a VPC network is assigned a CIDR block with a fixed number of IP addresses. VPC network performance is superior to container tunnel networks because there is no tunnel encapsulation overhead. In addition, as routes destined for nodes and containers are added to a VPC route table, containers can be directly accessed from outside the cluster.
- Cloud Native 2.0: Developed by CCE, a Cloud Native 2.0 network integrates the elastic network interfaces and supplementary network interfaces of VPC. Container IP addresses are allocated from the VPC CIDR block. Cloud Native 2.0 networks support features like ELB passthrough networking and association of security groups and EIPs with pods. Additionally, because container tunnel encapsulation and NAT are not required, Cloud Native 2.0 networks enable higher network performance than the container tunnel and VPC networks.
Different container network models vary in terms of performance, networks, and application scenarios. Container Networks describes the functions and features of these models.
- Service Networks
Services are a kind of Kubernetes resource object. Each Service has a static IP address. When creating a cluster on CCE, you can specify the Service CIDR block. The Service CIDR block cannot overlap with the node or container CIDR block. The Service CIDR block can be used only within a cluster.
Network Access
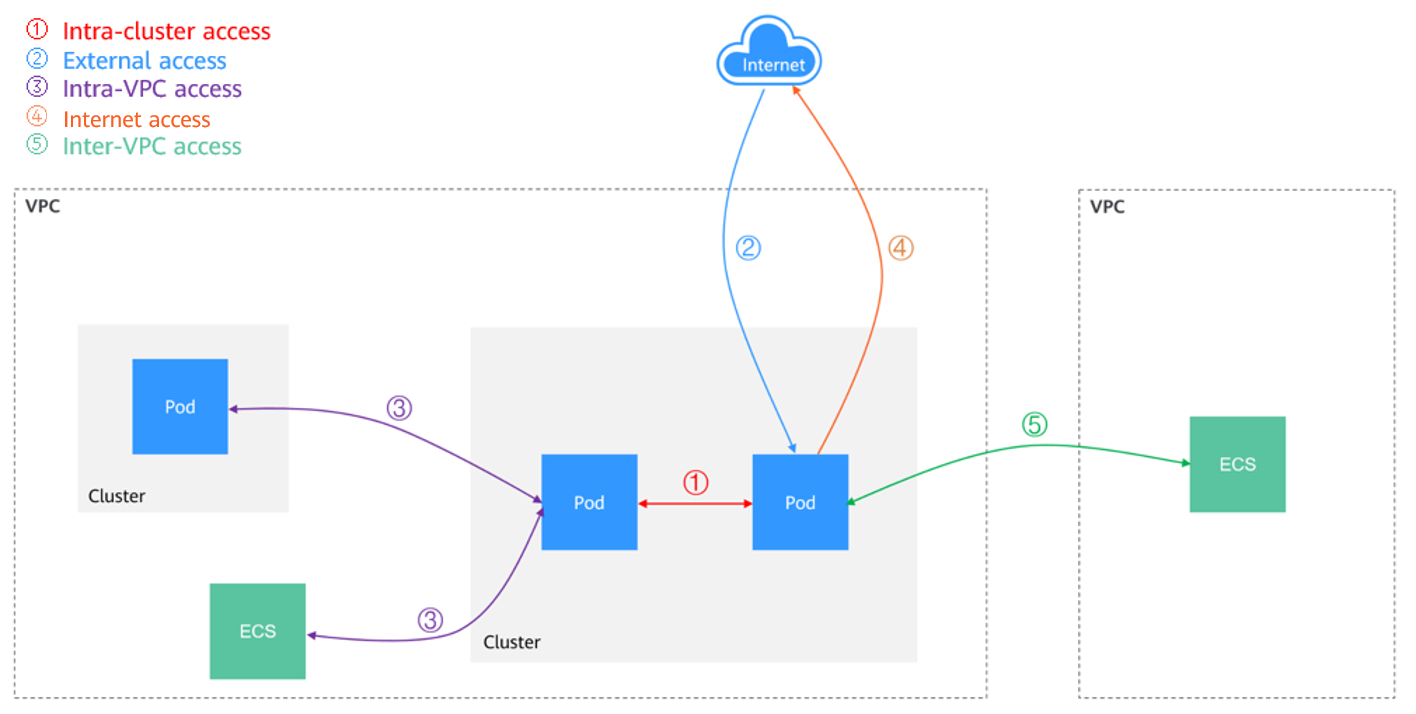
In a CCE cluster, there are the following network access scenarios:
- Accessing a workload from within the cluster: Create a ClusterIP Service and access the workload through the Service.
- Accessing a workload from outside the cluster: Create a LoadBalancer Service or an ingress.
- Accessing a workload through the Internet: Bind an EIP to the LoadBalancer Service.
- Accessing a workload through an intranet: Use the internal IP address of the LoadBalancer Service. To access multiple workloads that are located in different VPCs, you need a peering connection.
- Accessing an external network from a workload:
- Accessing an intranet: Allow the traffic from the container CIDR block in the security group of the peer end.
- Accessing the Internet: Bind an EIP to the node where the container is located (in a VPC or tunnel network) or directly bind an EIP to the pod IP address. For details, see Configuring an EIP for a Pod. Additionally, configure SNAT rules using a NAT gateway. For details, see Accessing the Internet from a Container.
Best Practices
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





