Using a Cloud Connection and SNAT to Enable Private Networks to Access the Internet
Scenario
When customers require high-speed Internet access from their on-premises data centers to locations outside the Chinese mainland, they can use VPN, Cloud Connect, NAT Gateway (SNAT rules), and EIP.
For example, these services can enable fast access to services in Africa, Europe, or America.
Use Cases
- Using VPN to connect a customer's on-premises data center to a VPC in CN North-Beijing4
- Using a cloud connection to connect the VPC in CN North-Beijing4 to a VPC in CN-Hong Kong for network acceleration
- Purchasing NAT gateway in CN-Hong Kong, and adding an SNAT rule to enable on-premises servers to share the EIP to access the Internet outside the Chinese mainland
Figure 1 shows an example.
- In this solution, the network in CN East-Shanghai1 represents the on-premises data center.
- The CIDR block of the Internet outside the Chinese mainland is 8.8.8.0/24, and 8.8.8.8 is the only IP address used for testing.
Advantages
Cross-border connectivity and accelerated network access provide better user experience.
Constraints
The user account needs cross-border permissions. Otherwise, the user needs to authorize the current VPCs to an account with the cross-border permissions to create a cloud connection.
Resource Planning
|
Resource |
Resource Name |
Description |
Quantity |
|---|---|---|---|
|
VPC |
VPC-Test01 |
Region: CN East-Shanghai1 CIDR block: 172.18.0.0/24 172.18.0.0/24 represents the on-premises network. |
1 |
|
VPC-Test02 |
Region: CN North-Beijing4 CIDR block: 172.16.0.0/24 |
1 |
|
|
VPC-Test03 |
Region: CN-Hong Kong CIDR block: 172.17.0.0/24 |
1 |
|
|
EIP |
EIP-Test |
Region: CN-Hong Kong |
1 |
|
NAT gateway |
NAT-Test |
You need to purchase it in VPC-Test03 and use EIP EIP-Test. |
1 |
|
VPN gateway |
VPN-GW-Test01 |
Region: CN North-Beijing4 Local gateway: 49.49.49.49 |
1 |
|
VPN-GW-Test02 |
Region: CN East-Shanghai1 Local gateway: 223.223.223.223 |
1 |
|
|
VPN connection |
VPN-Test01 |
It is created to connect to VPN-GW-Test01. |
1 |
|
VPN-Test02 |
It is created to connect to VPN-GW-Test02. |
1 |
|
|
Cloud connection |
CC-Test |
It enables cross-region access between CN North-Beijing4 and CN-Hong Kong and accelerates network access. |
1 |
|
ECS |
ECS-Test01 |
Region: CN East-Shanghai1 Private IP address: 172.18.0.3 |
1 |
|
ECS-Test02 |
Region: CN East-Beijing4 Private IP address: 172.16.0.3 |
1 |
|
|
ECS-Test03 |
Region: CN-Hong Kong region Private IP address: 172.17.0.3 |
1 |
Process
Procedure
- Create VPCs.
For details, see Creating a VPC.
Ensure that the VPC CIDR blocks do not conflict with each other.
- VPC in CN East-Shanghai1 (VPC-Test01): 172.18.0.0/24
- VPC in CN North-Beijing4 (VPC-Test02): 172.16.0.0/24
- VPC in the CN-Hong Kong (VPC-Test03): 172.17.0.0/24
- Create two VPN connections.
Create VPN-GW-Test01 in CN North-Beijing4 and buy VPN-Test01.
Create VPN-GW-Test02 in CN East-Shanghai1 and buy VPN-Test02.
For details, see Buying a VPN Gateway and Buying a VPN Connection.
For details, see Creating a VPN Gateway and Creating a VPN Connection.
- In CN North-Beijing4:
- Local subnets: 172.16.0.0/24, 172.17.0.0/24, and 8.8.8.0/24
- Remote gateway: 223.223.223.223
- Remote subnet: 172.18.0.0/24
- In CN East-Shanghai1:
- Local subnet: 172.18.0.0/24
- Remote gateway: 49.49.49.49
- Remote subnets: 172.16.0.0/24, 172.17.0.0/24, and 8.8.8.0/24
When configuring the VPN connection between CN North-Beijing4 and CN East-Shanghai1, you need to ensure that local CIDR blocks in CN North-Beijing4 and remote subnets (8.8.8.0/24) in CN East-Shanghai1 are included so that these subnets can access the Internet outside of the Chinese mainland.
- In CN North-Beijing4:
- Create a cloud connection.
- Create a cloud connection (CC-Test).
For details, see Creating a Cloud Connection.
- Load the three VPCs to the created cloud connection.
For details, see Loading a Network Instance.
- Add custom CIDR blocks.
For details, see Adding Custom CIDR Blocks for a Cloud Connection.
- When you load the VPC in CN North-Beijing4, you need to add CIDR blocks 172.18.0.0/24 and 172.16.0.0/24.
- When you load the VPC in CN-Hong Kong, you need to add CIDR blocks 172.17.0.0/24 and 8.8.8.0/24.
To enable communication among all nodes, you need to add all local subnets.
- Buy a bandwidth package.
By default, a cloud connection provides 10 kbit/s of bandwidth for testing cross-region network connectivity. You need to buy a bandwidth package to ensure normal communication across regions.
For details, see Buying a Bandwidth Package.
- Assign inter-region bandwidths.
For details, see Assigning an Inter-Region Bandwidth.
- Create a cloud connection (CC-Test).
- Buy three ECSs.
Buy one ECS in each of the following regions: CN East-Shanghai1, CN North-Beijing4, and CN-Hong Kong.
For details, see Purchasing an ECS.
- Private IP address of the ECS (ECS-Test01) in CN East-Shanghai1: 172.18.0.3
- Private IP address of the ECS (ECS-Test02) in CN North-Beijing4: 172.16.0.3
- Private IP address of the ECS (ECS-Test03) in CN-Hong Kong: 172.17.0.3
- Buy an EIP and a NAT gateway.
Buy an EIP (EIP-Test) in the CN-Hong Kong region, buy a public NAT gateway (NAT-Test), and add an SNAT rule for each of the following CIDR blocks:
For details, see Assigning an EIP and Binding It to an ECS and Adding an SNAT Rule.
- VPC CIDR block: 172.17.0.0/24
- Direct Connect connection/Cloud connection CIDR blocks: 172.18.0.0/24 and 172.16.0.0/24
SNAT rules allow servers in private networks to access the Internet (8.8.8.0/24) outside the Chinese mainland.
Verification
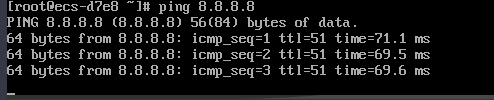
Test the network connectivity.
Ping the gateway (8.8.8.8) from the ECS in CN East-Shanghai1.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






