Device Certificates
Overview
For a device using MQTTS X.509 certificates, when it connects to the platform for the first time, IoTDA utilizes the uploaded and verified device CA certificate to authenticate the device certificate. After the authentication is successful, the platform automatically saves the device certificate and generates expiration warnings. You can check and disable device certificates.
Constraints
- IoTDA generates alarms for device certificates that are about to expire within 30 days. Update the certificates in a timely manner to prevent access failures.
- The device certificate quota provided by IoTDA is 1.5 times of the device quantity quota. To ensure smooth storage of new certificates, delete expired certificates in a timely manner. Failure to do so may result in the inability to check certificates on the console. However, this does not affect device access to the platform.
- A device is associated with a device certificate through the certificate fingerprint. After a device certificate is disabled, all devices associated with it cannot access the platform.
Procedure
- Upload and verify the device CA certificate. For details about how to create and verify a device CA certificate, see Registering a Device Authenticated by an X.509 Certificate.
- Register a device that uses the X.509 certificate for authentication. Log in to the IoTDA console. In the navigation pane, choose Devices > All Devices. On the displayed page, click Register Device. Set Authentication Type to X.509 certificate and Fingerprint to the SHA-256 fingerprint of the device certificate. If you do not specify the fingerprint, the device certificate fingerprint carried when the device successfully accesses the platform for the first time is recorded by default.
- Use the device certificate to access the device to the platform.
Figure 1 Device connection parameters
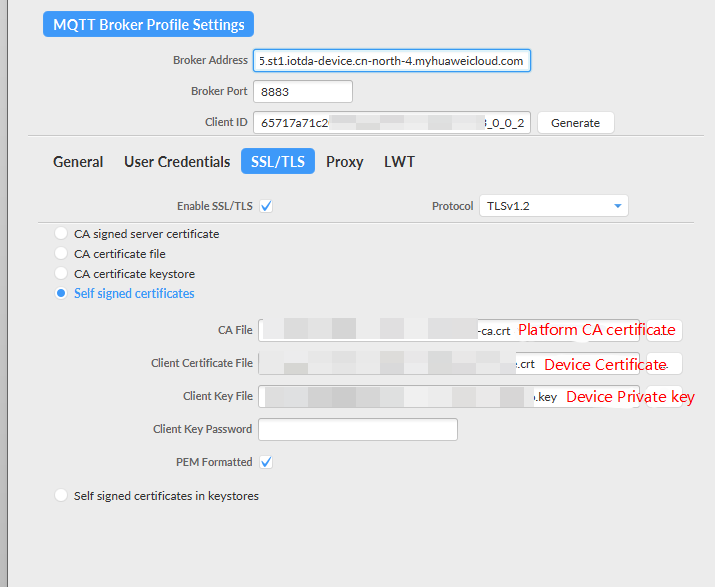
- Log in to the IoTDA console. In the navigation pane, choose Devices > Device Certificates. Click the Device Certificates tab to check the device certificate list and details.
Figure 2 Device certificate - Certificate list
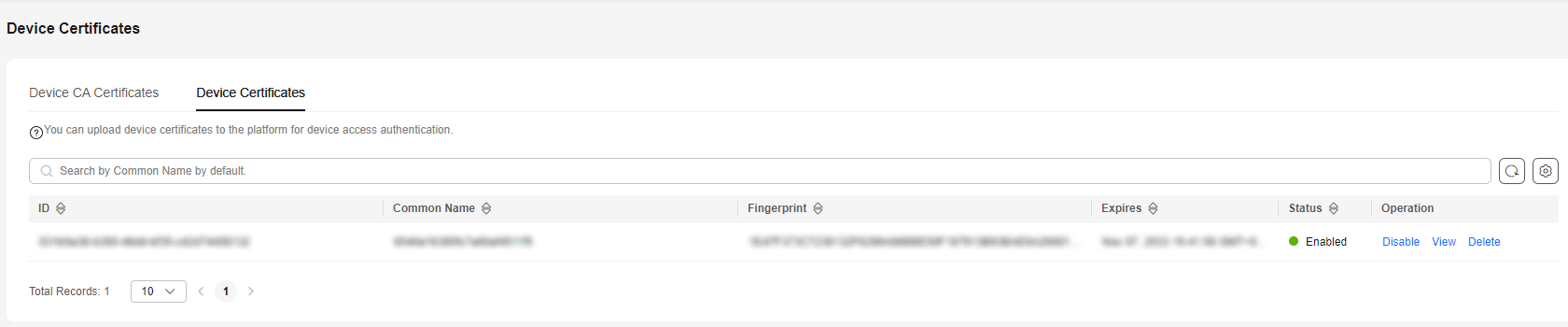 Figure 3 Device certificate - Certificate details
Figure 3 Device certificate - Certificate details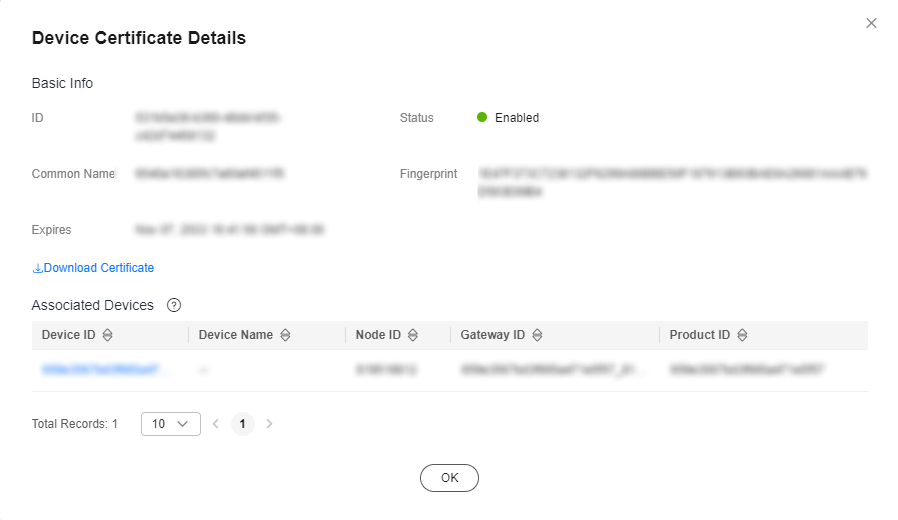
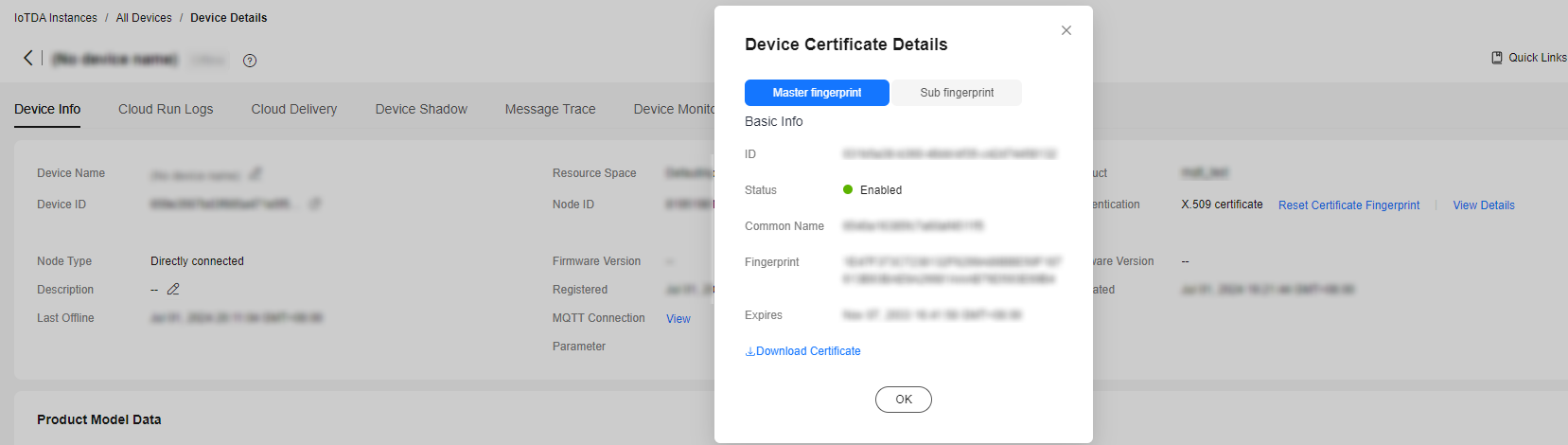
- In the navigation pane, choose Devices > All Devices. Locate the target device, click View in the Operation column. On the displayed page, click the button for checking the certificate details.
Figure 4 Device - Device details - Certificate details
Alarms
- IoTDA generates an expiration warning for device certificates. You can check the certificates that are about to expire in the recent month in the Application Operations Management (AOM) alarm list.
Figure 5 Device certificate expiration alarm -AOM

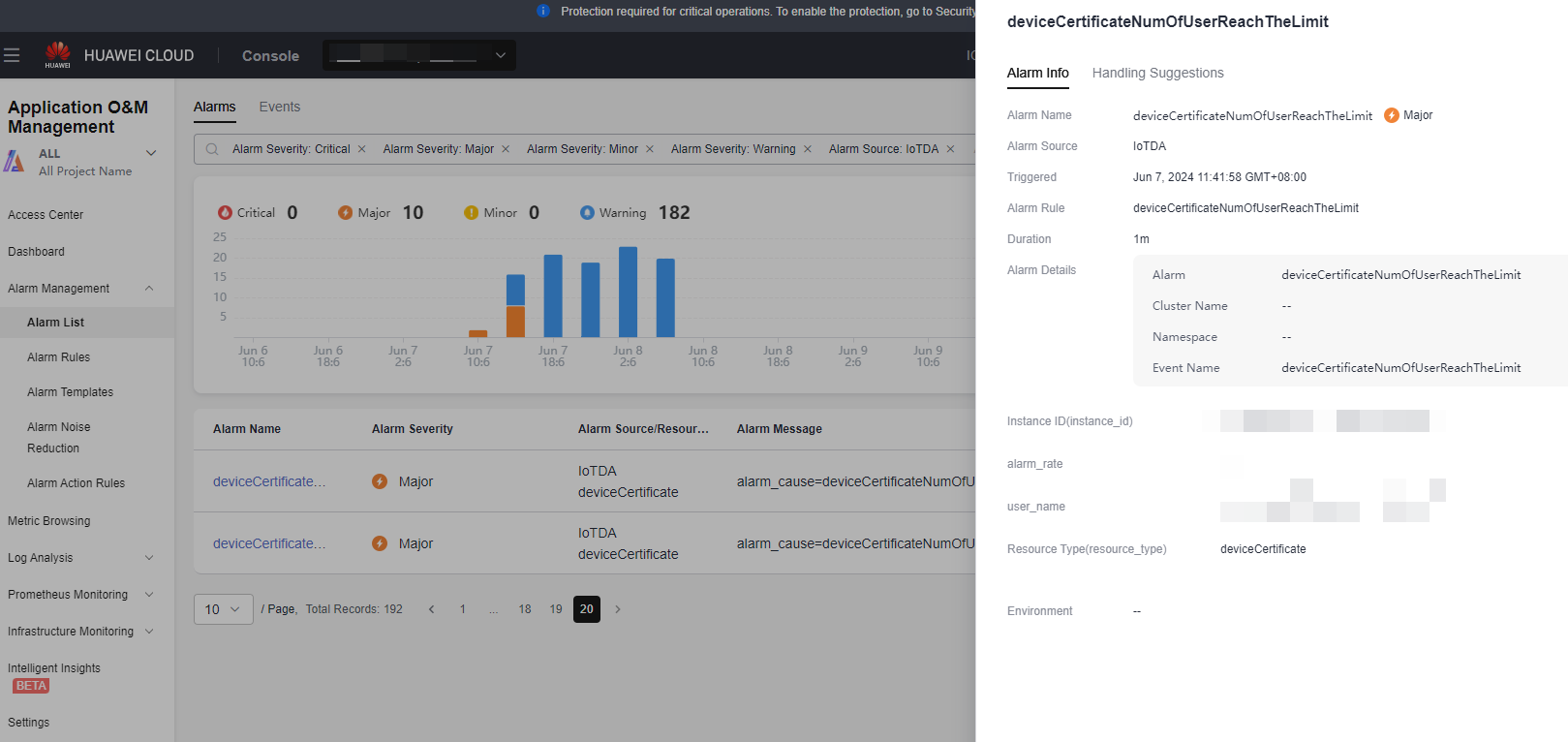
- IoTDA generates a warning when the number of device certificates exceeds the threshold. Delete expired certificates in a timely manner.
Figure 6 Insufficient device certificate quota -AOM
AOM allows you to create an alarm action rule to send alarm notifications through SMSs, emails, and WeCom messages. For details, see Creating an Alarm Action Rule.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





