Authentication Credentials
Introduction
When connecting to IoTDA, a device must carry a credential for authentication. Currently, two types of authentication credentials are available.
- Secret: the device secret you preset on IoTDA during device registration for future authentication. After successful authentication, the device is activated and communicates with the platform. There are two types of secrets:
- Master secret: primary secret used for device access authentication.
- Sub secret: secondary secret used when the master secret fails to pass the authentication. Unavailable for devices accessed using CoAP.
- X.509 certificate: a digital certificate used for communication entity authentication. IoTDA allows devices to use their own X.509 certificates. For details, see Connecting a Device That Uses the X.509 Certificate Based on MQTT.fx. In this mode, the platform verifies the device certificate fingerprints that you preset on the platform for authentication during connection establishment. There are two types of fingerprints:
- Master fingerprint: primary fingerprint used for device access certificate authentication.
- Sub fingerprint: secondary fingerprint used when the master fingerprint fails to pass the authentication.
Updating
You need to update a device access credential in some scenarios, for example, when an X.509 certificate is about to expire. You can reset device credentials by calling the APIs for resetting a device fingerprint or resetting a device secret. IoTDA provides master/sub fingerprints and secrets to prevent device authentication failure and service interruption during credential update and resetting. For example, when you add a new certificate fingerprint, the platform sets the fingerprint as a backup (sub fingerprint). In this way, the corresponding device can use both the old certificate (if not updated on the device side timely) and the new certificate to connect to the platform smoothly.
Scenarios
1. In high availability (HA) scenarios, a device has two secrets to connect to the platform.
2. During the credential update and resetting, a device does not disconnect from the platform and causes no service losses.
Procedure
- Access the IoTDA service page and click Access Console. Click the target instance card.
- In the navigation pane, choose . By default, all devices in the current instance are displayed in the device list.
- Click View in the Operation column of the target device. On the displayed page, click Reset Secret or Reset Fingerprint. In the displayed dialog box, select Sub secret or Sub fingerprint.
Figure 1 Device details - Resetting sub secret
 Figure 2 Device details - Resetting sub fingerprint
Figure 2 Device details - Resetting sub fingerprint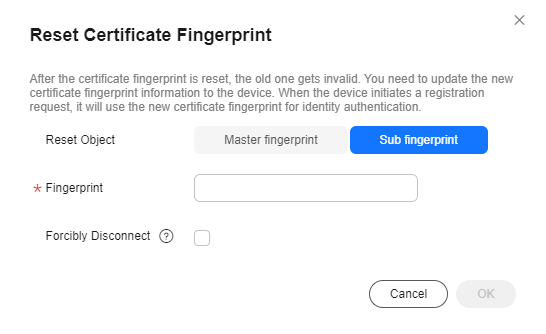
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





