DWS Security Best Practices
Security is a shared responsibility between Huawei Cloud and you. Huawei Cloud is responsible for the security of cloud services to provide a secure cloud. As a tenant, you should properly use the security capabilities provided by cloud services to protect data, and securely use the cloud. For details, see Shared Responsibilities.
This practice provides actionable guidance for enhancing the overall security of your service data when using DWS.
Configure security settings in the following phases of using DWS to meet your service needs.
- DWS cluster creation and database connection:
- Database object design:
- SQL service development:
- Enabling Row-level Access Control to Make Row-level Data Partially Visible
- Masking Column Data
- Using DWS Built-in Functions to Encrypt Data
- Viewing Audit Logs to Check the Users Who Have Modified Service Data
- Employing Intelligent O&M (Automatic Vacuum) to Address Service Performance Bottlenecks as They Arise
- O&M:
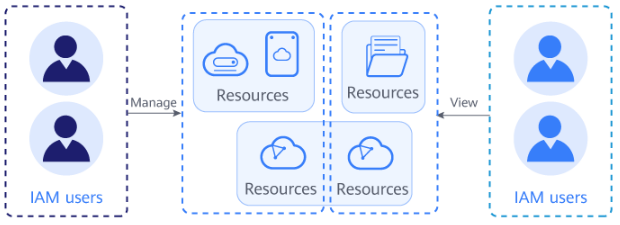
Controlling Resource Access
If you want to give varying levels of access to your company's DWS resources on Huawei Cloud, using IAM is an effective way to manage permissions in detail. IAM provides identity authentication, permissions management, and access control, helping you securely manage access to your Huawei Cloud resources. With IAM, you can use your Huawei Cloud account to create IAM users and assign permissions to them to control their access to specific resources.
- Scenario 1: To allow software developers in your company to use DWS resources while restricting high-risk operations and resource deletion, you can create IAM users tailored for these developers and grant them only the essential permissions for DWS usage.
- Scenario 2: Allow employees to use only DWS resources, but not the resources of other services. To this end, grant them only the permissions for DWS.
You can use IAM to control cloud resource access and prevents misoperations on cloud resources.
Enabling Critical Operation Protection for the Console
DWS protects mission-critical operations. If you want to perform a mission-critical operation on the console, you must enter a credential for identity verification. You can perform the operation only after your identity is verified. For account security, you are advised to enable the operation protection function. This function takes effect for the account and its sub-users.
Currently, the following operations are supported: binding an EIP, scaling out a cluster, changing specifications, deleting a cluster, restarting a cluster, starting a cluster, stopping a cluster, adding or deleting a CN, upgrading a cluster, modifying parameters, deleting idle nodes, and enabling or disabling auto scaling.
For details, see Enabling Critical Operation Protection for the DWS Console.
Enabling Cluster-Level Transparent Encryption
In a traditional database cluster, user data is stored in plaintext in column-store or row-store files. Malicious cluster maintenance personnel or attackers can bypass the database permission control mechanism in the OS or steal disks to access user data. DWS interconnects with Huawei Cloud KMS to implement transparent data encryption and enhance user data security.
In DWS database-level TDE, each DWS cluster has a CEK and is configured with a DEK. DEKs are encrypted using the CEKs and their ciphertext is stored in DWS. Keys are applied for, encrypted, and decrypted through the KMS service. The cryptographic algorithm is configured using configuration items. Currently, AES and SM4 algorithms are supported.
For details, see Using KMS to Encrypt DWS Clusters .
Connecting to a Database Through SSL-encrypted Data Transmission
DWS supports the standard SSL. As a highly secure protocol, SSL authenticates bidirectional identification between the server and client using digital signatures and digital certificates to ensure secure data transmission. To support SSL connection, DWS has obtained the formal certificates and keys for the server and client from the CA certification center. It is assumed that the key and certificate for the server are server.key and server.crt respectively; the key and certificate for the client are client.key and client.crt respectively, and the name of the CA root certificate is cacert.pem.
The SSL mode delivers higher security than the common mode. By default, the SSL function is enabled in a cluster to allow SSL or non-SSL connections from the client. For security purposes, you are advised to enable SSL connection. The server certificate, private key, and root certificate have been configured in DWS by default.
For details, see Establishing Secure TCP/IP Connections in SSL Mode.
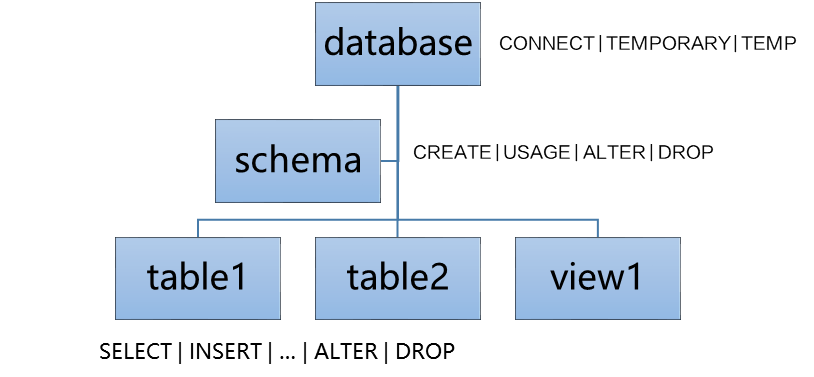
Isolating Workloads Through Database and Schema Configurations
In DWS, you can isolate workloads through database and schema configurations. The differences are:
- Databases cannot communicate with each other and share very few resources. Their connections and permissions can be isolated.
- Schemas share more resources than databases do. User permissions on schemas and subordinate objects can be flexibly configured using the GRANT and REVOKE syntax.
You are advised to use schemas to isolate services for convenience and resource sharing purposes. It is recommended that system administrators create schemas and databases and then assign required permissions to users.
- Each database has one or more schemas. Each schema contains various types of objects, such as tables, views, and functions.
- To access an object at the bottom layer, a user must be granted the permission on the object at the upper layer.
- To create or delete a schema, you must have the CREATE permission for its database.
- To access table1 in a schema, a user must be granted the CONNECT permission for its database, the USAGE permission of the schema, and the SELECT permission of table1.
For details, see How Does DWS Implement Workload Isolation?
DWS uses the GRANT syntax to grant permissions to roles and users. A common user cannot access a table without the permissions granted by the system administrator dbadmin or the table owner. This default mechanism controls user access to data and can prevent data leakage.
GRANT is used in the following scenarios:
- Granting system permissions to roles or users
System permissions are also called user attributes, including SYSADMIN, CREATEDB, CREATEROLE, AUDITADMIN, and LOGIN.
They can be specified only by the CREATE ROLE or ALTER ROLE syntax. The SYSADMIN permission can be granted and revoked using GRANT ALL PRIVILEGE and REVOKE ALL PRIVILEGE, respectively. System permissions cannot be inherited by a user from a role, and cannot be granted using PUBLIC.
- Granting database object permissions to roles or users
Grant permissions for a database object (table, view, column, database, function, or schema) to a role or user.
GRANT grants specified database object permissions to one or more roles. These permissions are appended to those already granted, if any.
DWS grants the permissions on certain types of objects to PUBLIC. By default, permissions on tables, columns, sequences, foreign data sources, foreign servers, schemas, and tablespaces are not granted to PUBLIC, but the following permissions are granted to PUBLIC: CONNECT and CREATE TEMP TABLE permissions on databases, EXECUTE permission on functions, and USAGE permission on languages and data types (including domains). An object owner can revoke the default permissions granted to public and grant permissions to other users. For security purposes, create an object and set its permissions in the same transaction, so that the object will not be accessible to any other users until you configure its permissions and end the transaction. In addition, you can run the ALTER DEFAULT PRIVILEGES statement to modify the default permissions.
- Granting a role's or user's permissions to other roles or users
Grant a role's or user's permissions to one or more roles or users. In this case, every role or user can be regarded as a set of one or more database permissions.
If WITH ADMIN OPTION is specified, the member can in turn grant permissions in the role to others, and revoke permissions in the role as well. If a role or user granted with certain permissions is changed or revoked, the permissions inherited from the role or user also change.
A database administrator can grant permissions to and revoke them from any role or user. Roles having CREATEROLE permission can grant or revoke membership in any role that is not an administrator.
For more information, see GRANT.
Revoking Permissions
After a user is granted with a database object permission, you can use the REVOKE syntax to revoke a permission from a user if the user no longer needs it, or if you need to control the user's permissions.
For more information, see REVOKE.
Enabling Row-level Access Control to Make Row-level Data Partially Visible
Multiple users may need to access and perform operations on the same table at the same time. In this case, you need to grant users the permissions for specific rows in the table. DWS can implement row-level access control. For example, a table administrator can see an entire table, but user A is allowed to view only specific rows in the table when they run SELECT * FROM table_name. This feature enables database access control to be accurate to each row of data tables. In this way, the same SQL query may return different results for different users.
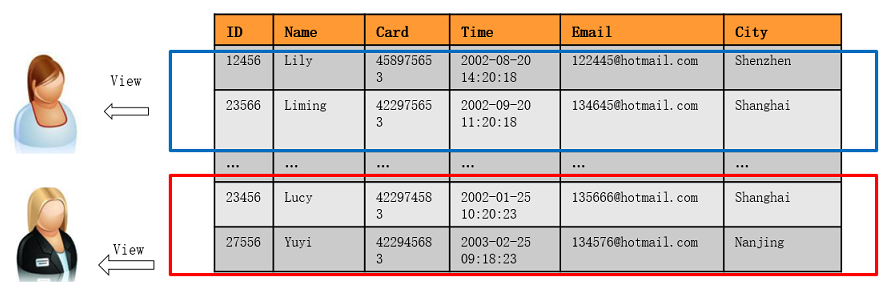
You can create a row-level access control policy for a data table. The policy defines an expression that takes effect only for specific database users and SQL operations. When a database user accesses the data table, if a SQL statement meets the specified row-level access control policies of the data table, the expressions that meet the specified condition will be combined by using AND or OR based on the attribute type (PERMISSIVE | RESTRICTIVE) and applied to the execution plan in the query optimization phase.
Row-level access control is used to control the visibility of row-level data in tables. By predefining filters for data tables, the expressions that meet the specified condition can be applied to execution plans in the query optimization phase, which will affect the final execution result. Currently, the SQL statements that can be affected include SELECT, UPDATE, and DELETE.
For details, see Row-Level Access Control.
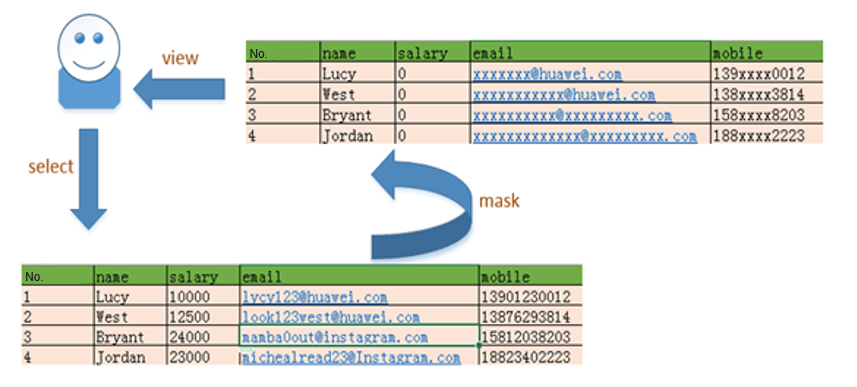
Masking Column Data
DWS provides the column-level dynamic data masking function. For sensitive data, such as the ID card number, mobile number, and bank card number, the dynamic data masking function is used to redact the original data to protect data security and user privacy.
For details, see Data Redaction.
Using DWS Built-in Functions to Encrypt Data
Data encryption is widely used in information systems to prevent unauthorized access and data leakage. As the core of an information system, the DWS data warehouse also provides transparent encryption and encryption using SQL functions.
DWS provides hash functions and symmetric cryptographic algorithms to encrypt and decrypt columns. Hash functions include sha256, sha384, sha512, and SM3. Symmetric cryptographic algorithms include AES128, AES192, AES256, and SM4.
- Hash functions
- Symmetric encryption algorithms
- gs_encrypt(encryptstr, keystr, cryptotype, cryptomode, hashmethod)
Encrypts an encryptstr string using the keystr key based on the cryptographic algorithm specified by cryptotype and cryptomode and the HMAC algorithm specified by hashmethod, and returns the encrypted string.
- gs_decrypt(decryptstr, keystr, cryptotype, cryptomode, hashmethod)
Decrypts a decryptstr string using the keystr key based on the cryptographic algorithm specified by cryptotype and cryptomode and the HMAC algorithm specified by hashmethod, and returns the decrypted string. The keystr used for decryption must be the same as that used for encryption.
- gs_encrypt_aes128(encryptstr,keystr)
Encrypts encryptstr strings using keystr as the key and returns encrypted strings. The length of keystr ranges from 1 to 16 bytes.
- gs_decrypt_aes128(decryptstr,keystr)
Decrypts decryptstr strings using keystr as the key and returns decrypted strings. The keystr used for decryption must be the same as that used for encryption. keystr cannot be empty.
- gs_encrypt(encryptstr, keystr, cryptotype, cryptomode, hashmethod)
For details, see Encrypting and Decrypting Data Columns.
Viewing Audit Logs to Check the Users Who Have Modified Service Data
Database audit logs record users' daily activities, including accessing and modifying service data. By reviewing these logs, database administrators can stay informed about the current state of service data access and modification, and proactively identify any potential risks related to data leakage or malicious tampering. For users who maliciously tamper with data, promptly disable their permissions to ensure service security. For details, see Viewing Database Audit Logs.
Employing Intelligent O&M (Automatic Vacuum) to Address Service Performance Bottlenecks as They Arise
Intelligent O&M helps DWS users with O&M tasks. With this feature, you can specify the proper time window and number of tasks to execute based on the cluster workload. Besides, Intelligent O&M can adjust task execution policies according to service changes in a timely manner to reduce the impact on services. Periodic tasks and one-off tasks are supported, and you can configure the time window as required.
The database administrator can configure the following tasks on the console to implement auto clean. For details, see Intelligent O&M Overview.
- Frequent table creation and deletion can lead to table bloating. To free up space, you can run the VACUUM command on system catalogs.
- Frequently update and delete operations can lead to table bloating. To free up space, you can run the VACUUM or VACUUM FULL command on system catalogs.
Monitoring the Database Health on the Monitoring Panel
DMS is provided by DWS to ensure the fast and stable running of databases. It collects, monitors, and analyzes disk, network, OS, and cluster performance metrics. It also diagnoses database hosts, instances, and service SQL statements based on the collected metrics to expose key faults and performance problems in a database in a timely manner, and guides customers to optimize and resolve the problems. For details, see Cluster O&M.
Periodically Backing Up Service Data
DWS supports cluster-level data backup to prevent data loss. Service data can be backed up to OBS. For details, see Snapshot Overview.
Enabling Cross-AZ Dual-Cluster DR
When a cluster is deployed within a single AZ, a fault in the AZ impacts all nodes in the cluster. Under these circumstances, cluster-level backup and recovery are inadequate for ensuring data security. Therefore, you can create two cross-AZ clusters to implement DR management.
A homogeneous DWS DR cluster is deployed in another AZ (within the region). If the production cluster fails to provide read and write services due to natural disasters in the specified region or cluster internal faults, the DR cluster becomes the production cluster to ensure service continuity.
For details, see DWS Cluster DR Scenarios.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





