Restricting Access Time Using IAM
To ensure service and data security, you can use IAM policies to restrict users to access cloud services only within specified time ranges.
Application Scenarios
Company A has purchased many Huawei Cloud resources, such as ECS, BMS, and IMS instances. To ensure service and data security, the company expects that users can access Huawei Cloud only during working hours.
The following steps describe how to use custom policies to allow IAM users to access Huawei Cloud only during working hours.
Step 1: Create a Custom Policy
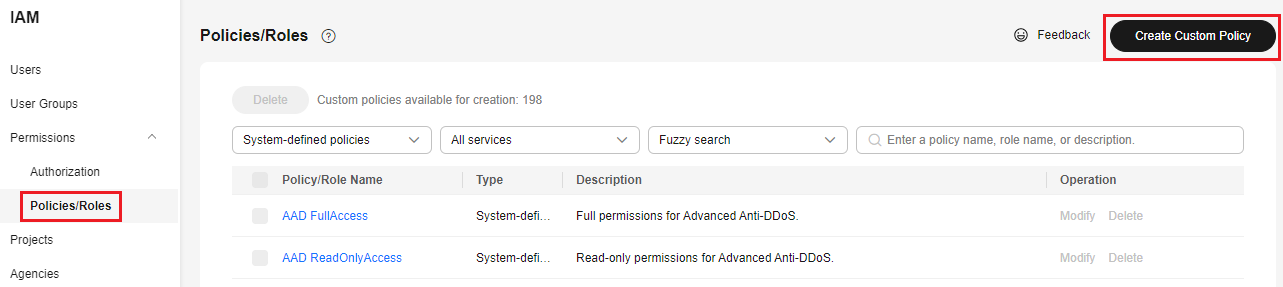
- Log in to the IAM console as the administrator.
- In the navigation pane, choose Permissions > Policies/Roles, and then click Create Custom Policy in the upper right corner.
Figure 1 Creating custom policies
- Enter a policy name, for example, example-policy.
- Select JSON for Policy View.
- Enter the policy content.
Figure 2 Entering policy content

{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "iam:users:createUser" ], "Condition": { "DateGreaterThan": { "g:CurrentTime": [ "2025-03-08T08:05:22Z" ] }, "DateLessThan": { "g:CurrentTime": [ "2025-03-09T08:05:42Z" ] } } }, { "Effect": "Allow", "Action": [ "iam:*:list*", "iam:*:get*" ] } ] } - (Optional) Enter a brief description for the policy.
- Click Confirm.
Step 2: Create an IAM User Group
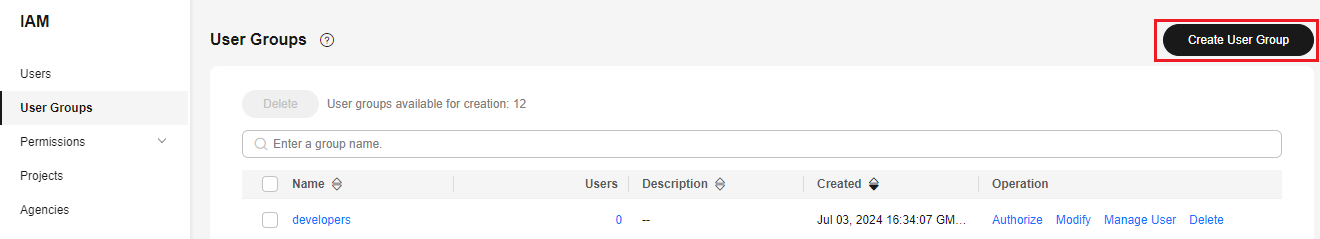
- Log in to the IAM console as the administrator.
- In the navigation pane, choose User Groups and then click Create User Group.
Figure 3 Creating a user group
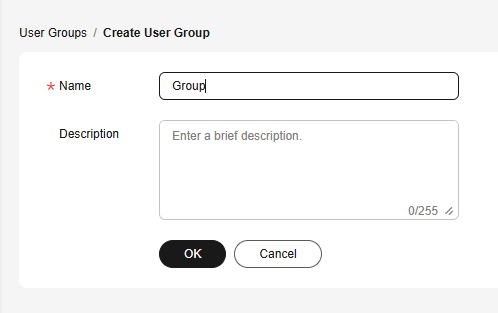
- In the Create User Group dialog box, enter a name.
Only letters, digits, spaces, hyphens (-), and underscores (_) are allowed.Figure 4 Setting user group information
- Click OK.
You will be redirected to the user group list and the created user group is displayed in the list.
Step 3: Authorize the IAM User Group
- In the user group list, click Authorize in the row containing the user group Group.
Figure 5 Authorizing a user group
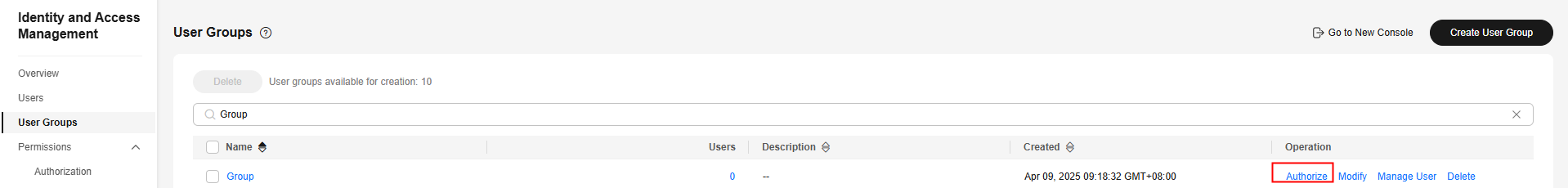
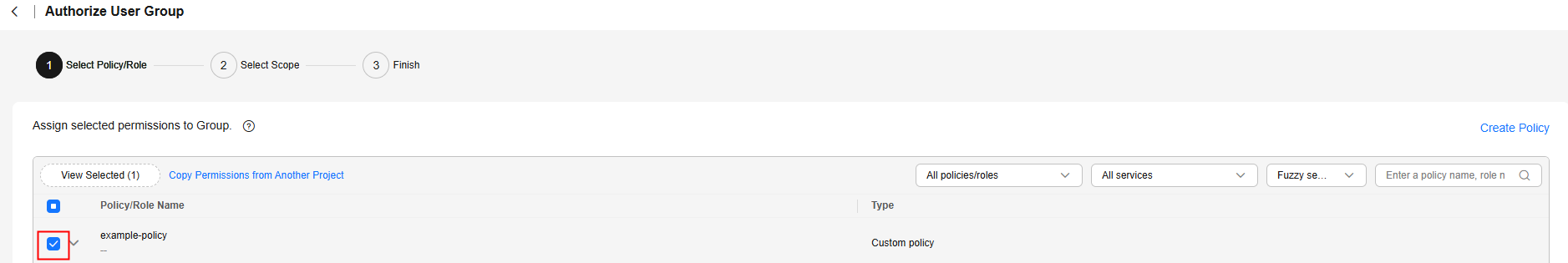
- In the Select Policy/Role tab, select example-policy. Click Next.
Figure 6 Selecting permissions
- Specify the scope. The system automatically recommends an authorization scope for the permissions you selected. Table 1 describes all the authorization scopes provided by IAM.
Table 1 Authorization scopes Scope
Description
All resources
IAM users will be able to use all resources, including those in enterprise projects, region-specific projects, and global services under your account based on assigned permissions.
Enterprise projects
IAM users can use the resources in the enterprise projects you select based on the assigned permissions. This option is available only when the enterprise project function has been enabled.
For details about Enterprise Project, see What Is Enterprise Project Management Service? To enable the enterprise project function, see Enabling the Enterprise Project Function.
Region-specific projects
IAM users can use the resources in the region-specific projects you select based on the assigned permissions.
If you select global service permissions, the permissions will be applied to all resources by default. If you select project-level service permissions, the permissions will be applied to the region-specific projects you select.
NOTE:The region-specific projects for Dedicated Cloud cannot be selected.
Global services
IAM users can use global services based on the assigned permissions. Global services are deployed for all physical regions. IAM users do not need to specify a region when accessing these services, such as Object Storage Service (OBS) and Content Delivery Network (CDN).
If you select project-level service permissions, the permissions will be applied to all resources by default. If you select global service permissions, the permissions will be applied to the global services.
- Click OK.
Step 4: Create an IAM User
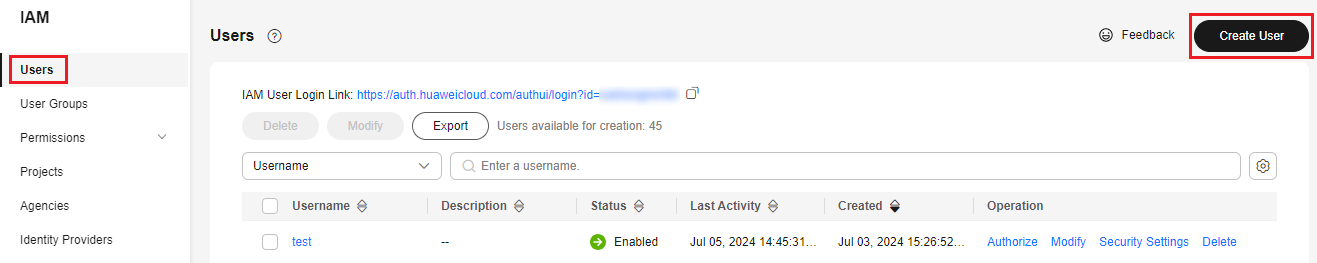
- Log in to the IAM console as the administrator.
- Choose Users in the navigation pane and click Create User in the upper right corner.
Figure 7 Creating a user
- Specify the user details on the Create User page.
Figure 8 Specifying user details
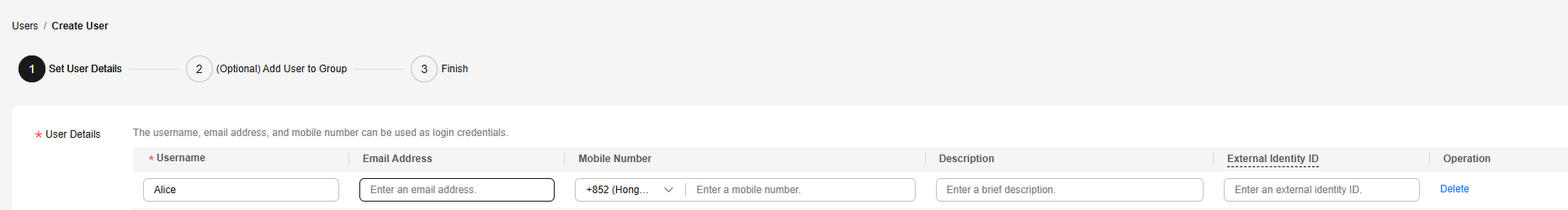
Table 2 User information Parameter
Example Value
Description
Username
Alice
The name is user-defined and must be different from that of any other account or any IAM user in the account.
Email Address
Skip
The name is user-defined and must be different from that of any other account or any IAM user in the account. It can be used to authenticate the IAM user and reset the password.
Mobile Number
Skip
The name is user-defined and must be different from that of any other account or any IAM user in the account. It can be used to authenticate the IAM user and reset the password.

- Users can log in to Huawei Cloud using the username, email address, or mobile number.
- If users forget their passwords, they can reset them, through email address or mobile number verification. If no email addresses or mobile numbers have been bound to users, they need to contact the administrator to reset their passwords.
- Specify Access Type.
Figure 9 Selecting access types
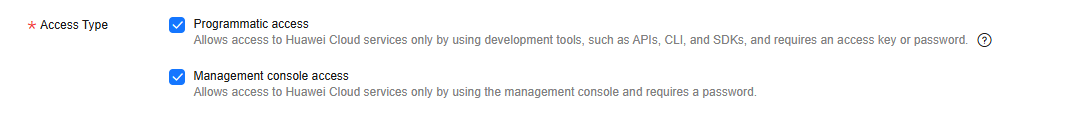
Table 3 Access types Access Type
Description
Programmatic access
An access key or password is generated for the IAM user. This type allows access to cloud services using development tools, such as APIs, CLI, and SDKs.
Management console access
A password is generated for the IAM user. This type allows access to cloud services using the management console. If you select this option, Password must be selected for Credential Type.
- Configure the credential type.
Figure 10 Configuring the credential type
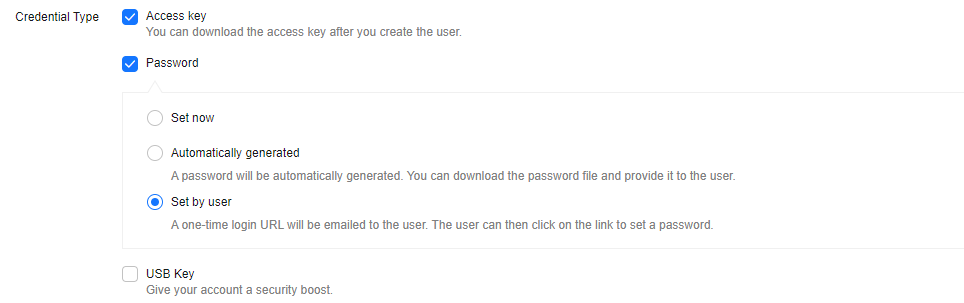
Table 4 Credential types Credential Type
Example
Description
Access key
Select it.
An access key comprises an AK and SK, and is used as a long-term identity credential to sign your requests for Huawei Cloud APIs.
After users are created, you can download the access keys (AK/SK) generated for these users.
Password
Set now
-
Set a password for the user and determine whether to require the user to reset the password at the first login.
If you will use the IAM user by yourself, you are advised to select this option, set a password, and deselect Require password reset at first login.
Automatically generated
-
The system automatically generates a login password for the user. After the user is created, download the EXCEL password file and provide the password for the user. The user can then use this password for login.
The password file must be downloaded upon the user creation. If you cancel the download, the password file cannot be obtained again. You can change the password of an IAM user by referring to Changing the Password of an IAM User.
This option is available only when you create a single user.
Set by user
Select it.
A one-time login URL will be emailed to the user. The user can click the link to log in to the console and set a password.
If you do not use the IAM user, select this option and enter the email address and mobile number of the IAM user. The user can then set a password by clicking the one-time login URL sent over email. The login URL is valid for two days.
USB Key
Deselect it.
A USB key is a device that stores user credentials. You can use a USB key, rather than a password to verify your identity. This option is more secure, as there is no password to be leaked.
Once selected, the USB key is the only way for the IAM user to log in. The password will be invalidated and can no longer be used.
- Enable or disable login protection. This function is available only when Access Type is Management console access. In this example, select Enable.
- Login protection enabled: IAM users need to enter verification codes in addition to their usernames and passwords during console login. For the best possible security, this two-factor identity authentication is recommended.
- Login protection disabled: You can enable login protection after user creation by referring to Modifying IAM User Information.
Figure 12 Login protection disabled
- Enable or disable API login protection. This function is available when only login protection is enabled and the verification mode is set to virtual MFA.
- API login protection enabled: Both a password and a virtual MFA device are required to obtain an IAM user token. To obtain an IAM user token using both a password and a virtual MFA device, see Obtaining a User Token Through Password and Virtual MFA Authentication.
- API login protection disabled: You can enable API login protection after user creation. Locate the target user, and click Security Settings in the Operation column. In the displayed tab, click
 next to Verification Method of the Login Protection function, enable this function, and select Virtual MFA device.
next to Verification Method of the Login Protection function, enable this function, and select Virtual MFA device.
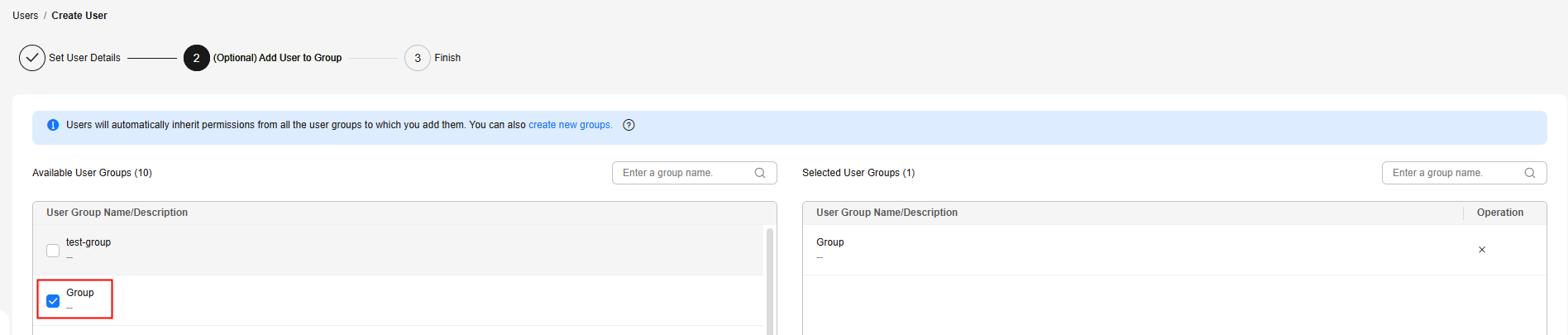
- Click Next to add Alice to the user group you created.
Figure 13 Adding the user to the user group
- Click Create.
Figure 14 User created

Step 5: Log in to the Console as an IAM User
- Use the IAM user Alice to log in to the system from 08:05:22 on March 8, 2025 to 08:05:22 on March 9, 2025. On the login page, click IAM User. On the IAM User Login page, enter the tenant name or Huawei Cloud account name, IAM username or email address, and IAM user password.
Figure 15 Logging in as an IAM user
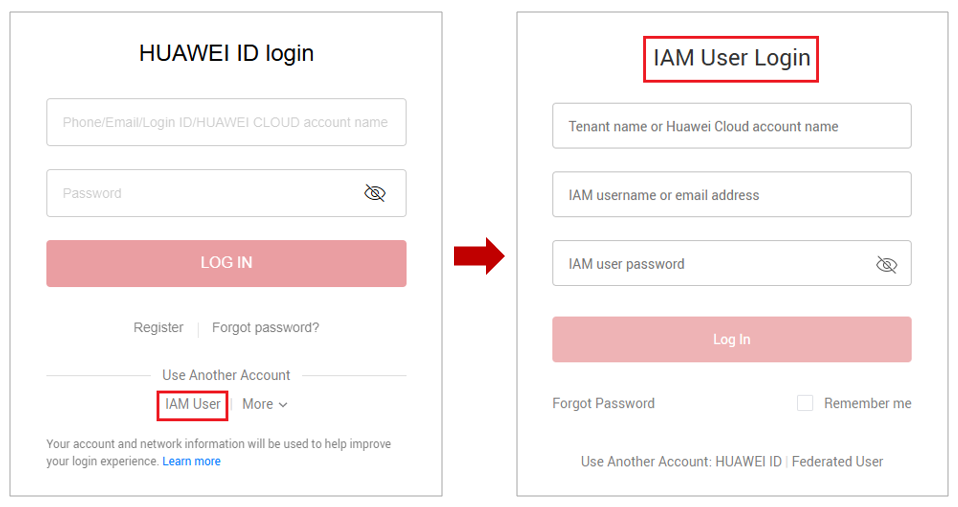
Table 5 Login parameters Parameter
Example
Description
Tenant name or Huawei Cloud account name
Company-A
Account used to create the IAM user, for example, Company-A.
IAM username or email address
Alice
IAM username or email address entered during the user creation. You can obtain the IAM username and IAM user's initial password from the administrator.
IAM user password
********
Password of the IAM user, rather than the account. Enter the downloaded password.
- Click Log In.

If you log in to IAM outside the allowed time range, you cannot create IAM users.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot