Viewing Server Protection Status
You are advised to periodically check the server protection status and handle security risks in a timely manner to prevent asset loss.
- Huawei Cloud servers purchased in the selected region
- Non-Huawei Cloud servers that have been added to the selected region
Viewing Server Protection Status
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose .
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- In the server list, view the protection status of servers. For details, see Server protection status.
You can check the server name, ID, IP address, OS, running status, and enterprise project. To set the items to be displayed in the server protection list, click
 in the upper right corner.Figure 1 Server protection status
in the upper right corner.Figure 1 Server protection status
- Searching for a server
To check the protection status of a server, enter a server name, server ID, or IP address in the search box above the server protection list.Figure 2 Searching for a protected server

- Viewing servers of a certain type
On the left of the server protection list, select a server protection edition or an asset importance category to view the protection status of each type of servers.
- Viewing server details
Hover your cursor over a server name to view details about the server OS, system version, and kernel version.
- Viewing server protection information
The Protection Status column indicates whether a server is protected. The protection status of a server is determined by Agent Status and Server Status. You can view the server risk detection status in the Risk Level column. For details about the preceding parameters, see Table 1.
Table 1 Protection description Parameter
Description
Server Status
HSS can only protect running servers. If the server is in the Stopped or other state, you cannot perform security checks or fix risks on the server.
Agent Status
- Not installed: The agent has not been installed or successfully started.
Click Install Agent and install the agent as prompted. For details, see Installing an Agent.
- Online: The agent has been installed and running properly.
- Offline: The agent has been installed, but the agent is disconnected from the HSS remote protection center. In this case, HSS cannot provide protection. For more information, see How Do I Fix an Abnormal Agent?
NOTE:
For an IDC server, its information will be automatically deleted from the server management page after its agent goes offline for 30 days.
- Installation failed: An error or problem occurred, leading to an installation failure. Click
 next to the installation failure status to view the cause. Rectify the fault by referring to What Should I Do If Agent Installation Failed?
next to the installation failure status to view the cause. Rectify the fault by referring to What Should I Do If Agent Installation Failed? - Installing: The agent is being installed.
Protection Status
- Enabled: The server is fully protected by HSS.
- Unprotected: HSS is disabled for the server. After the agent is installed, click Enable in the Operation column to enable protection.
- Protection interrupted: The server is shut down, the agent is offline, or the agent is uninstalled. You can hover the cursor on
 next to Protection interrupted to view the cause.
next to Protection interrupted to view the cause.
Risk Level
Risk status of a server. (Data is updated every 24 hours.)
- Risky: The server has risks. Hover your cursor over a risk icon to view risk distribution details. Click a risk quantity to go to the risk details page.
- Safe: No risks are found.
- Pending risk detection: HSS is not enabled for the server.
- Not installed: The agent has not been installed or successfully started.
- Searching for a server
Viewing the WTP Status
- Choose . The Servers tab page is displayed.
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- Check the server protection status.
Figure 3 Servers protected by WTP
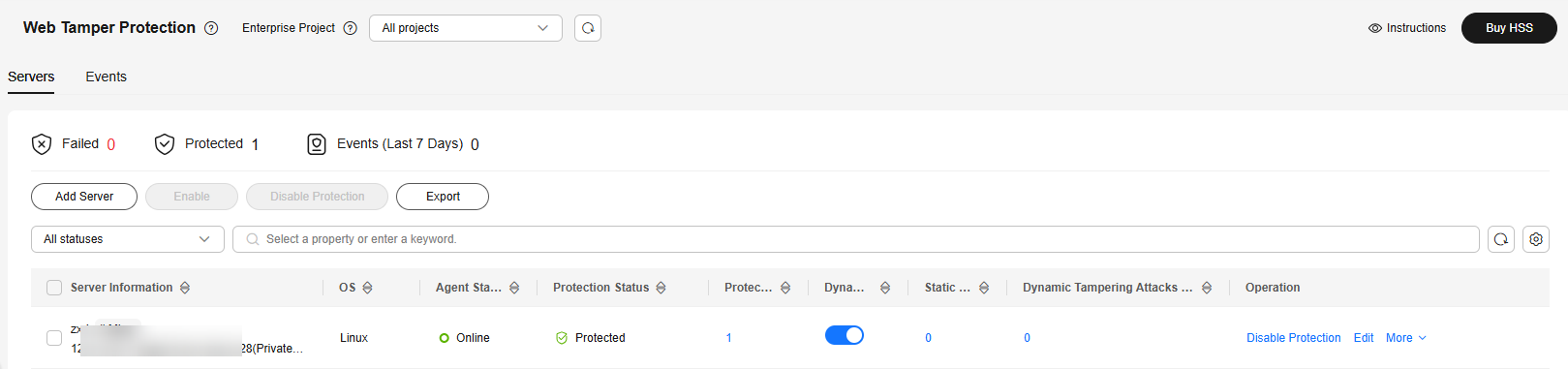
Table 2 Statuses Parameter
Description
Agent Status
- Not installed: The agent has not been installed or successfully started.
Click Install Agent and install the agent as prompted. For details, see Installing an Agent.
- Online: The agent has been installed and running properly.
- Offline: The agent has been installed, but the agent is disconnected from the HSS remote protection center. In this case, HSS cannot provide protection. For more information, see How Do I Fix an Abnormal Agent?
NOTE:
For an IDC server, its information will be automatically deleted from the server management page after its agent goes offline for 30 days.
- Installation failed: An error or problem occurred, leading to an installation failure. Click
 next to the installation failure status to view the cause. Rectify the fault by referring to What Should I Do If Agent Installation Failed?
next to the installation failure status to view the cause. Rectify the fault by referring to What Should I Do If Agent Installation Failed? - Installing: The agent is being installed.
Protection Status
WTP status.
- Enabling: Static WTP is being enabled.
- Protected: Static WTP protection is enabled for all protected directories.
- Partially protected: Static WTP protection is enabled for some protected directories and disabled for others.
- Protection failed: Static WTP protection fails to be enabled for at least one protected directory.
- Protection interrupted: The server is shut down, the agent is offline, or the agent is uninstalled. You can hover the cursor on
 next to Protection interrupted to view the cause.
next to Protection interrupted to view the cause. - Protection suspended: Static WTP protection is suspended for all protected directories.
- Unprotected: Static WTP protection is not enabled for a server.
Protected Directories
Number of directories added for static WTP protection. You can click the number to go to the protected directory details page.
Dynamic WTP
Status of dynamic WTP, which can be: : Dynamic WTP is enabled.
: Dynamic WTP is enabled. : Dynamic WTP is disabled. (After enabling dynamic WTP, restart Tomcat to make this setting take effect.)
: Dynamic WTP is disabled. (After enabling dynamic WTP, restart Tomcat to make this setting take effect.)
Static Tampering Attacks
Number of times that static web page files are attacked and tampered with.
Dynamic Tampering Attacks
Number of web application vulnerability exploits and injection attacks.
- Not installed: The agent has not been installed or successfully started.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





