Injecting or Extracting Database Watermarks
Prerequisites
- Access to cloud assets has been authorized. For details, see Allowing or Disallowing Access to Cloud Assets.
- An RDS or DWS database has been authorized. For details, see Adding and Authorizing Database Assets.
- An MRS database has been authorized. For details, see Adding and Authorizing Big Data Assets.
- You have configured the DWS and MRS_Hive permissions. For details, see (Optional) Configuring GaussDB(DWS) and MRS Hive.
Constraints
|
Type |
Restriction |
|---|---|
|
Injecting a Watermark |
|
|
Extracting a Watermark |
|
Injecting or Extracting Database Watermarks
You can add or extract data watermarks to or from database table data by performing the following operations:
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Data Asset Protection > Database Watermark.
- Click Create Task. The Configure basic information page is displayed.
Figure 1 Configuring basic information

Table 1 Parameters for configuring basic information Parameter
Description
Task Name
Enter a task name.
The value can contain only letters, digits, underscores (_), and hyphens (-), and cannot exceed 255 characters.
Watermark ID
Enter the watermark identifier to be injected.
Embedding Scheme
Click the drop-down list box to select a watermark embedding scheme. The options are as follows:
- Lossless - pseudo column watermark: A pseudocolumn related to other attributes of the relationship table is generated. The pseudo column is deceptive to attackers. Watermarks are embedded into the pseudo column to reduce damage to the original data.
- Lossless - pseudo row watermark: Pseudo rows are generated based on the data type, data format, and value range. Watermarks are embedded into these pseudo rows to reduce damage to the original data.
- Lossy - column watermark: If you directly add watermarks to column data, the data will be modified or damaged.
NOTE:A higher error correction level indicates more watermark bits and a lower bit error rate (BER) during source tracing. Note that a higher error correction level requires more data as the embedding target to ensure embedding integrity. The default value is 1.
- Click Next. On the Configure source and target information page, set related parameters by referring to Table 2.
- Lossless - pseudo column watermark: Embed watermarks to created columns to avoid data loss.
Figure 2 Pseudo column watermarks
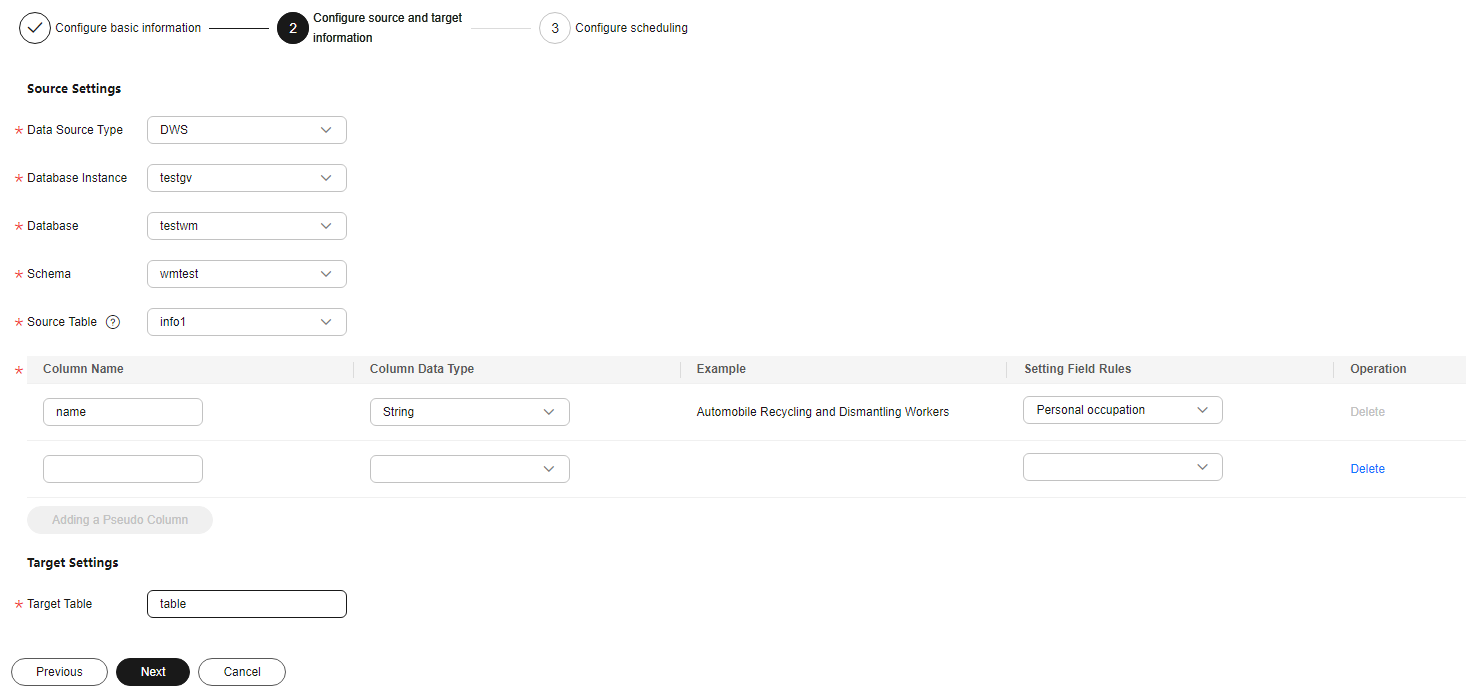
Table 2 Source and destination parameters of pseudo column watermarks Parameter
Description
Data Source Type
Select a data source type from the drop-down list box.
- When Embedding Scheme is set to Lossy - Column Watermark, the following data source types are supported:
- DWS
- MRS_HIVE
- When Embedding Scheme is set to Lossless pseudo-column watermarking or Lossless pseudo-line watermarking, the following data types are supported:
- DWS
- PostgreSQL
- MySQL
Database Instance
Select a Database Instance from the drop-down list. If no database instance is available, add databases by following the instructions provided in sections Adding and Authorizing Database Assets and Adding and Authorizing Big Data Assets.
Database
Select a Database from the drop-down list.
Schema
This parameter is displayed when Database is DWS or PostgreSQL. Click a Mode as required.
Source Table
Select the corresponding Source Table name.
Column Name
Only letters, numbers, underscores (_), and hyphens (-) are allowed (255 characters max).
Column Data Type
Click to select the data type of the embedded pseudocolumn.
- Numeric
- String
- Date
Example Value
Choose Setting Field Rules. The embedded pseudocolumn data example is displayed.
Setting Field Rules
- If Column Data Type is set to Numeric, this parameter is a random number. You can specify the range and precision of the random number. If the range and precision are not specified, pseudo data will be randomly generated.
- When Column Data Type is set to String, you can select pseudo data such as the person name, ID card number, and mobile number from the drop-down list box.
- When the Column Data Type is set to Date, you can specify a date range. If no date range is specified, pseudo data is randomly generated.
Add a Pseudo Column
You can click Add a Pseudo Column to add two pseudo-columns.
Target Table
Enter the target table name. The name can contain only letters, digits, underscores (_), and hyphens (-) and cannot exceed 255 characters.
- When Embedding Scheme is set to Lossy - Column Watermark, the following data source types are supported:
- Lossless - pseudo-line watermark: Watermarks are embedded into line copies to avoid data loss.
Figure 3 Pseudo-line watermark
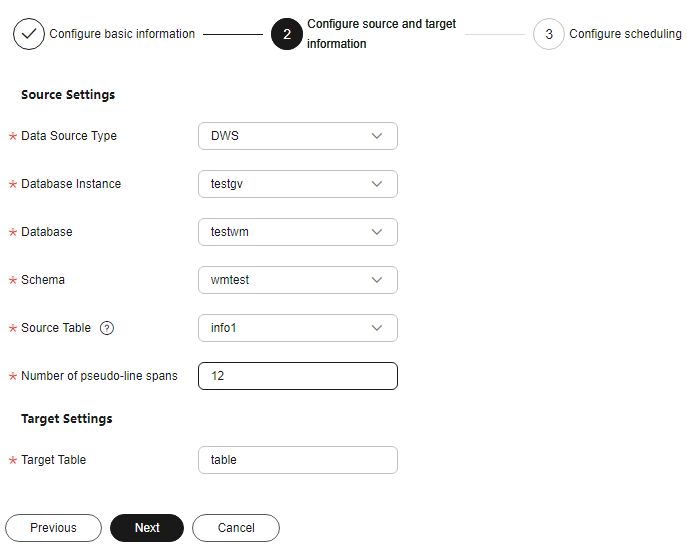
Table 3 Source and destination parameters of pseudo-line watermarks Parameter
Description
Data Source Type
Select a Data Source Type from the drop-down list. The following data source types are supported:
- DWS
- PostgreSQL
- MySQL
Database Instance
Select a Database Instance from the drop-down list. If no database instance is available, add databases by following the instructions provided in sections Adding and Authorizing Database Assets and Adding and Authorizing Big Data Assets.
Database
Select a Database from the drop-down list.
Mode
This parameter is displayed when Database is DWS or PostgreSQL. Click a Mode as required.
Source Table
Click and select the corresponding source data table name.
Number of Pseudo-Line Spans
Enter a valid integer greater than 1 to specify the number of pseudo-rows inserted into the original data.
Target Table
Enter the name of the data storage table with watermarks embedded. The name can contain only letters, digits, underscores (_), and hyphens (-), and cannot exceed 255 characters.
- Lossy - column watermark: Embed watermarks directly to the column data.
Figure 4 Lossy column watermarks
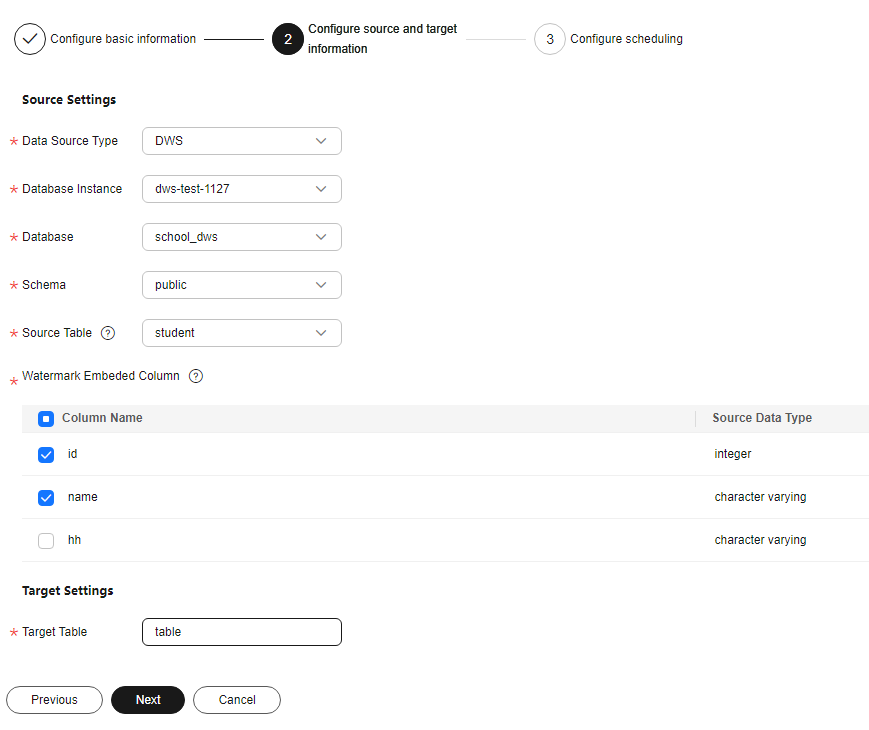
Table 4 Source and destination parameters of lossy column watermarks Parameter
Description
Data Source Type
Select a Data Source Type from the drop-down list. The following data source types are supported:
- DWS
- MRS-HIVE
Database Instance
Select a Database Instance from the drop-down list. If no database instance is available, add databases by following the instructions provided in sections Adding and Authorizing Database Assets and Adding and Authorizing Big Data Assets.
Database
Select a Database from the drop-down list.
Mode
This parameter is displayed when the Database is DWS. Click a Mode as required.
Source Table
Select the corresponding Source Table name.
Watermark Embedding Bar
Click to select the column data to which watermarks are embedded. You can select multiple columns.
NOTE:- The source database character set must be UTF-8.
- A single column in the embedding target cannot have more than 30% redundant data.
Target Table
Enter the name of the data storage table with watermarks embedded. The name can contain only letters, digits, underscores (_), and hyphens (-), and cannot exceed 255 characters.
- Lossless - pseudo column watermark: Embed watermarks to created columns to avoid data loss.
- Click Next. The Configuring scheduling page is displayed.
Figure 5 Configuring scheduling
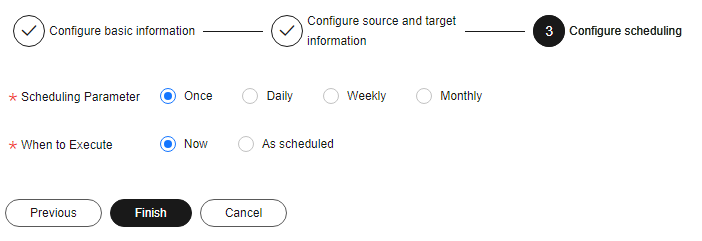
- If the Scheduling Parameter is set to Once, you can select Now or As scheduled to start the watermark embedding task.
- If the Scheduling Parameter is set to Daily, Weekly, or Monthly, start the watermark embedding task at a specified time daily, weekly, or monthly.
- Click Finish.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Data Asset Protection > Database Watermark.
- Click the Extract Watermark tab.
- Click Create Task. In the displayed dialog box, set parameters based on Table 5.
Figure 6 Creating an extraction task
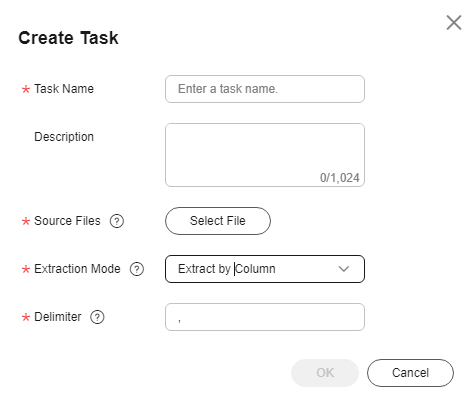
Table 5 Creating a watermark extraction task Parameter
Description
Task Name
Enter a task name.
Source Files
The source file must be in CSV format and cannot be larger than 20 MB. The table may contain more than 1,500 rows of data. The CSV file content is encoded in UTF-8 mode. Ensure that the data is complete and correct.
Extraction Mode
Select a watermark extraction mode from the drop-down list box. For lossy column embedding and lossless column embedding, extract watermarks by column. For lossless line embedding, extract watermarks by row.
Delimiter
Delimiters in a file. For example: comma (,)
- Click OK. The watermark extraction task is created.
Related Operations
- A running watermark embedding task cannot be edited or deleted.
- In the Inject Watermark tab, locate the target task and click Edit in the Operation column to modify the configurations of the watermark injection task.
- In the Inject Watermark tab, locate the target task and click Delete in the Operation column to delete the watermark injection task. You can also select multiple tasks and click Batch Delete to delete them.
The deletion operation cannot be undone.
- In the Inject Watermark tab, locate the target task and choose in the Operation column to start the task.
- In the Inject Watermark tab, locate the target task and choose in the Operation column to stop the task.
- In the Inject Watermark tab, locate the target task and choose in the Operation column to execute the task.
- In the Extract Watermark tab, locate the target task and click Delete in the Operation column to delete the watermark extraction task. You can also select multiple tasks and click Batch Delete to delete them.
The deletion operation cannot be undone.
- In the Extract Watermark tab, locate the target task and click View Result in the Operation column to view the extracted invisible watermark content.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





