Injecting or Extracting Document Watermarks
The DSC console allows you to inject custom watermarks into PDF, PPT, Word, and Excel documents. This section explains how to inject these watermarks in local documents or cloud documents (those stored in OBS buckets).
Invisible watermarks are, as the name suggests, invisible and require specific tools for extraction. On the DSC console, you can extract watermarks from PDF, PPT, Word, and Excel files. For detailed instructions on extracting watermarks from either cloud documents (in an OBS bucket) or local documents, refer to the "Extracting Watermarks" section.
Prerequisites
- OBS asset access permissions are granted. For details, see Allowing or Disallowing Access to Cloud Assets.
- You have enabled and created assets on OBS. For details about how to enable OBS, see Enabling and Using OBS Buckets.
- The document format is PDF, PPTX, DOCX, or XLSX.
Constraints
- For details about how to dynamically embed watermarks into data and images, see the Data Security Center (DSC) API Reference.
- If you injected an invisible watermark, extract the watermark from the target file using tools. For details, see Extracting Watermarks from an OBS Bucket Document and Extracting Watermarks from Local Files.
- The file size cannot exceed 20 MB.
Video Tutorial
Injecting or Extracting Document Watermarks
To inject data watermarks to or extract them from a document, perform the following operations.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Data Asset Protection > Document Watermarking.
- Click Create Task in the upper left corner of the task list to create a task.
- Set the parameters shown in Table 1.
Table 1 Task parameters Parameter
Description
Task Name
Enter the watermark ingestion task name. The value can contain only letters, digits, underscores (_), and hyphens (-), and cannot exceed 255 characters.
Select File
Click Add File. In the right pane, select the name of the bucket to which you want to add a watermark. In the left pane, select a file. You can select multiple files.
Watermark Type
Both visible and invisible watermarks are supported. You can select multiple values.
- Visible watermark: Watermarks are visible on documents.
- Invisible watermark: The watermark text is invisible and needs to be extracted using tools. For details about how to extract an invisible watermark, see Extracting Watermarks from an OBS Bucket Document and Extracting Watermarks from Local Files.
Target Path
Click selecting a file path, and select the watermarked file.
Configure Visible Watermark
Set Watermark Type to Visible Watermark. Then, enter the watermark content, and set Sparseness, Text, Font Size, Font Angle, and Transparency.
Configure Invisible Watermark
This parameter is mandatory when Watermark Type is set to Invisible.
Set Text as required.
Figure 1 Inserting Watermarks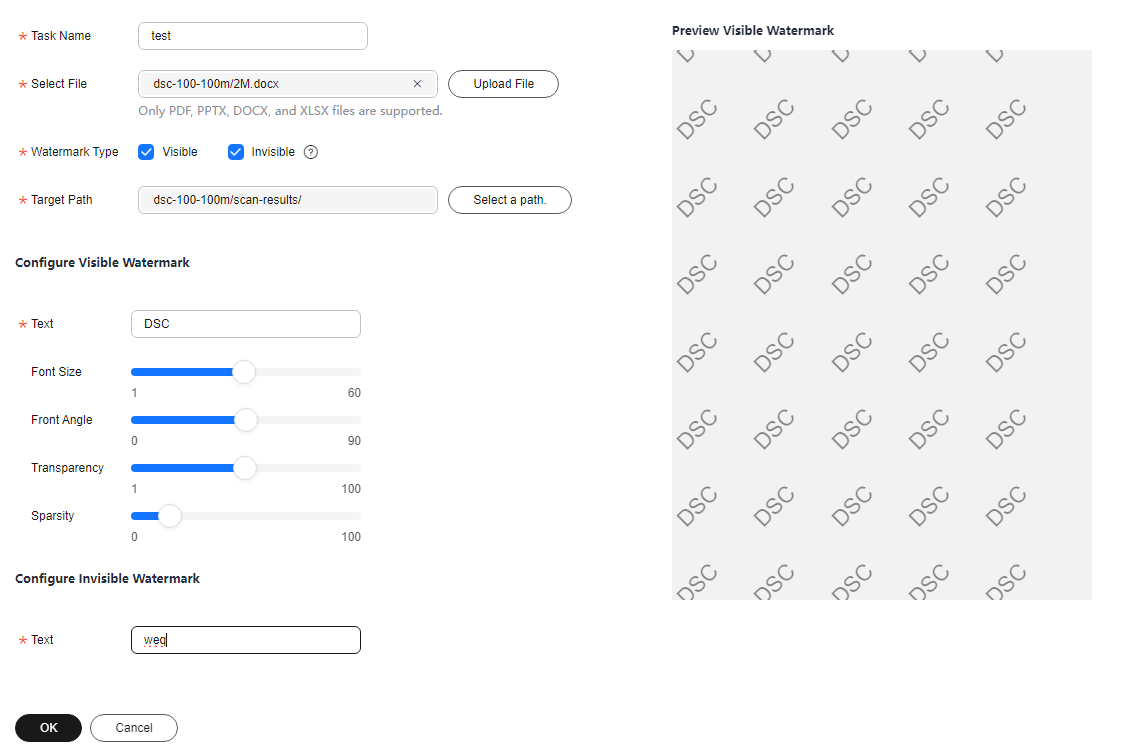
- Click OK. A message is displayed in the upper right corner, indicating that the watermark injection task is created successfully.
- In the watermark task list, click the task name to view the task running status.
- Running: You can view the progress of the watermark ingestion task.
- Finished: You can click Download in the Operation column to download the watermarked OBS bucket file.
- Failed: The watermark injection task fails to be executed. You can move the cursor to
 to view the failure cause.
to view the failure cause.
- If the injected watermark is a visible watermark, click Download to obtain the watermark file.
If you injected an invisible watermark, extract the watermark from the target document using tools. For details, see Extracting Watermarks from an OBS Bucket Document and Extracting Watermarks from Local Files.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Data Asset Protection > Document Watermarking.
- Click the Local File tab. The Watermark Injection page is displayed.
- Click Select File, and select the file to which the watermark is to be injected.
- After the file is uploaded, configure related parameters. Table 2 describes the related parameters.
Table 2 Watermarking parameters Parameter
Description
Watermark Type
Both visible and invisible watermarks are supported. You can select multiple values.
- Visible watermark: Watermarks are visible on documents.
- Invisible watermark: The watermark text is invisible and needs to be extracted using tools. For details about how to extract an invisible watermark, see Extracting Watermarks from an OBS Bucket Document and Extracting Watermarks from Local Files.
Configure Visible Watermark
Set Watermark Type to Visible Watermark. Then, enter the watermark content, and set Sparseness, Text, Font Size, Font Angle, and Transparency.
Configure Invisible Watermark
This parameter is mandatory when Watermark Type is set to Invisible.
Set Text as required.
Figure 2 Creating a Local File Data Injection Task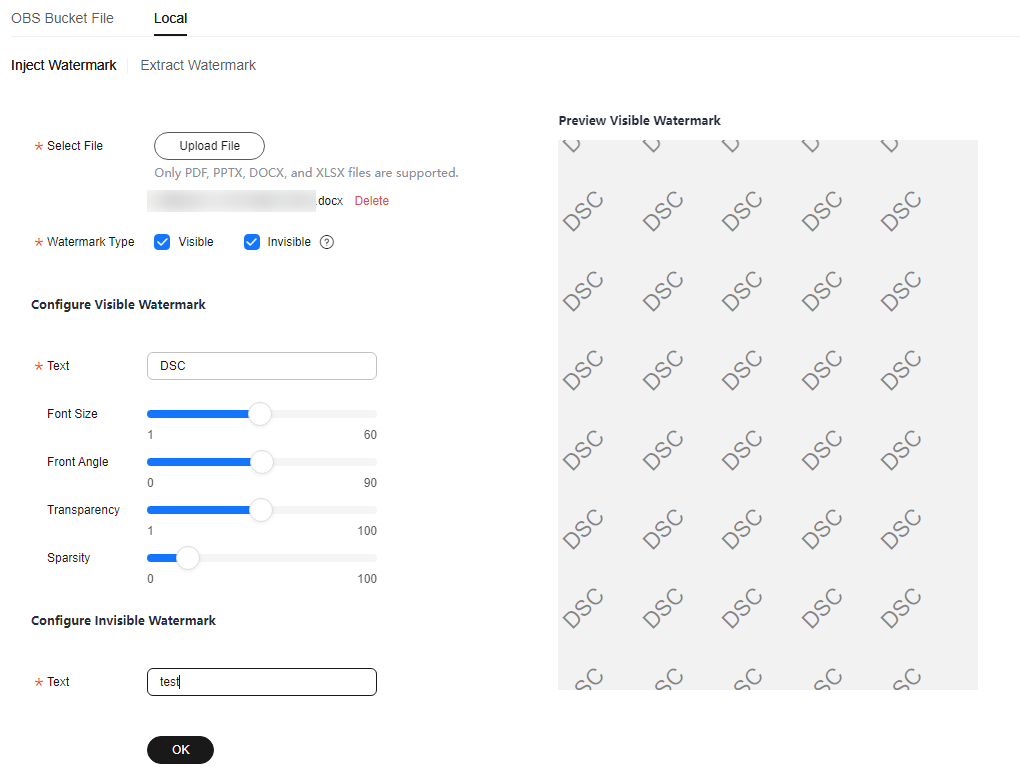
- After parameters are configured, click OK. The file with watermark injected is automatically downloaded to the specified path on the local PC.

- If you injected a visible watermark, open the target file to view the watermark.
- If you injected an invisible watermark, extract the watermark from the target file using tools. For details, see Extracting Watermarks from an OBS Bucket Document and Extracting Watermarks from Local Files.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose .
- Click the Watermark Extraction tab. The Watermark Extraction page is displayed.
- Click Create Task in the upper left corner. The Create Task page is displayed.
- Click Upload File to select the file from which you want to extract watermarks. You can select multiple OBS bucket files.
- Click OK. The watermark extraction task is created.
- Click the target task name. In the page displayed on the right, view the watermark extraction task status and the invisible watermark content of the OBS bucket file.
- Running: You can view the progress of the watermark extraction task.
- Completed: The watermark content is displayed in the Invisible Watermarks column. If there are no invisible watermarks, -- is displayed.
- Failed: The watermark extraction task fails to be executed. You can move the cursor to
 to view the failure cause.
to view the failure cause.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose .
- On the displayed page, choose . The Extract Watermark page is displayed.
- Upload the local document from which you want to extract the watermark text.
Only PDF, PPT, Word, and Excel documents are supported.
- After the file is uploaded, click OK. The invisible watermark content is displayed in the dialog box.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





