Enabling COC
Enabling COC
When you log in to Cloud Operations Center (COC) for the first time, you need to obtain the agency permissions for accessing other cloud services and enable COC. The procedure is as follows:
- Log in to COC.
- The service authorization page is displayed, prompting you to create the ServiceAgencyForCOC agency. This agency is used to grant COC the permissions to access other cloud services. For details about the permissions included in the agency, see Table 1.
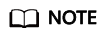
The COCServiceAgencyDefaultPolicy policy is added to the ServiceAgencyForCOC agency to support new service scenarios. If you enabled COC and authorized it during the open beta test of COC in the first half of 2024, manually add the COCServiceAgencyDefaultPolicy policy. This policy is compatible with the permissions required for future scale-out scenarios and does not affect the COC service features in use. For details, see ServiceAgencyForCOC Agency Supplement Policy.
Figure 1 Enabling COC and obtaining required permissions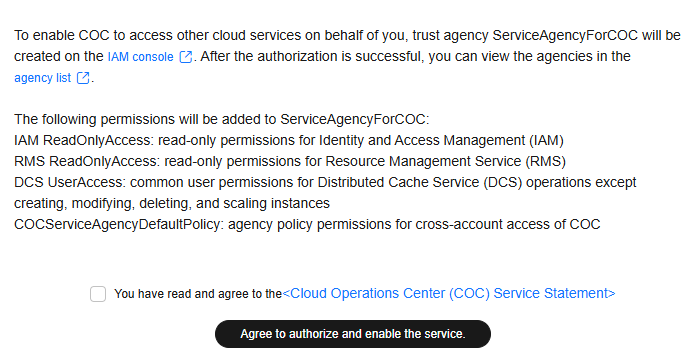
Table 1 Permissions in ServiceAgencyForCOC Permission
Description
Project [Region]
Scenario
IAM ReadOnlyAccess
Read-only permissions for IAM
Global service [Global]
Used to read personnel information under an IAM account in the Personnel Management module.
RMS ReadOnlyAccess
Read-only permissions for RMS
Global service [Global]
Used to synchronize managed cloud service resources in the Resource Management module.
DCS UserAccess
Common user permissions for DCS operations (excluding creating, modifying, deleting, and scaling instances).
Permissions on all resources (including new projects in the future)
Used to inject faults into DCS resources in the Chaos Drills module.
COCServiceAgencyDefaultPolicy
Service agency policy for cross-account access to COC
Permissions on all resources (including new projects in the future)
- Used to subscribe to notification channels in the personnel management module.
- Used to batch restart ECSs and RDS DB instances and change OSs in the Batch Resource Operations module.
- Used to query organization information in the cross-account scenario.
- Select "I have read and agree to the Cloud Operations Center (COC) Service Statement and click Agree to authorize and enable the service.
- After the authorization, you can enable COC and access the COC console to use its automatic O&M and fault management functions.
ServiceAgencyForCOC Agency Supplement Policy
You can authorize a missing policy for an agency on the COC console or on the IAM console.
The following are two methods for adding missing policies. You can select one as needed.
- Log in to COC.
- The alerting information about the missing policy is displayed on the top of the page. Click Obtain Permission.
Figure 2 Authorizing a user
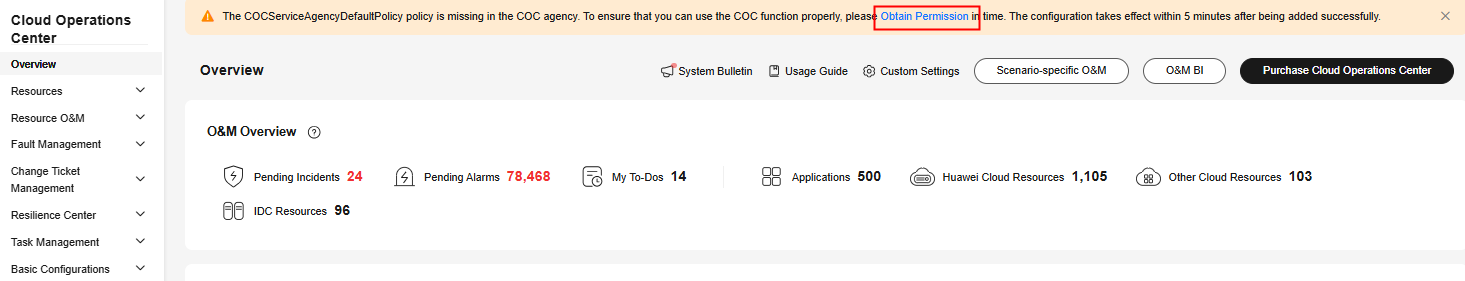
- In the Obtain Permission dialog box, click OK.
Figure 3 Confirming an authorization
- If the system prompts that the authorization succeeded, the policy has been added to the ServiceAgencyForCOC agency. The alerting information on the top of the COC page disappears.
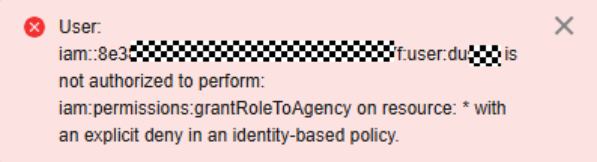
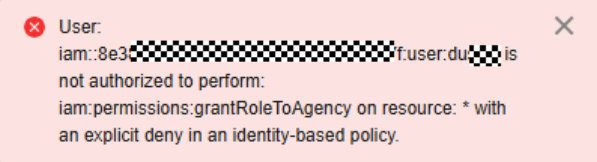
- If the following error message is displayed, the current user does not have the permissions in iam:permissions:grantRoleToAgency, contact the master account or an account with administrator permissions to add the missing policy displayed in the error information to the ServiceAgencyForCOC agency.
Figure 4 Error message
- Log in to the IAM console.
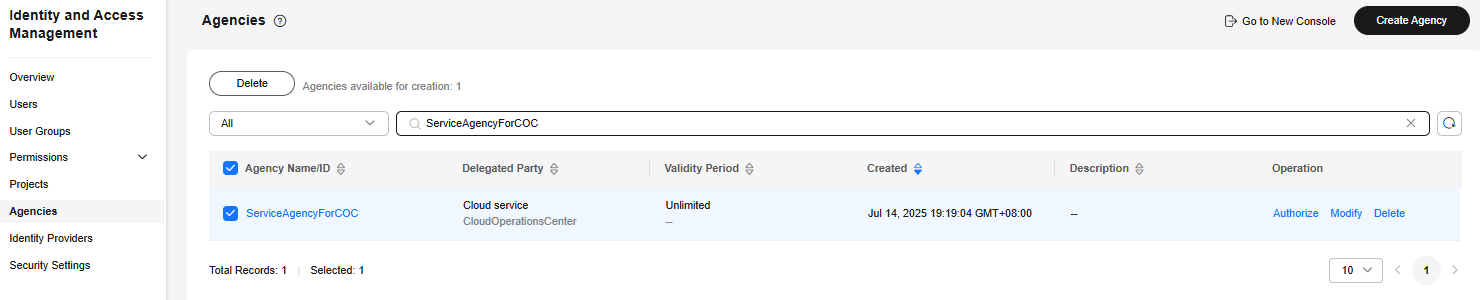
- In the navigation pane, choose Agencies.
- Search for ServiceAgencyForCOC.
Figure 5 Searching for ServiceAgencyForCOC
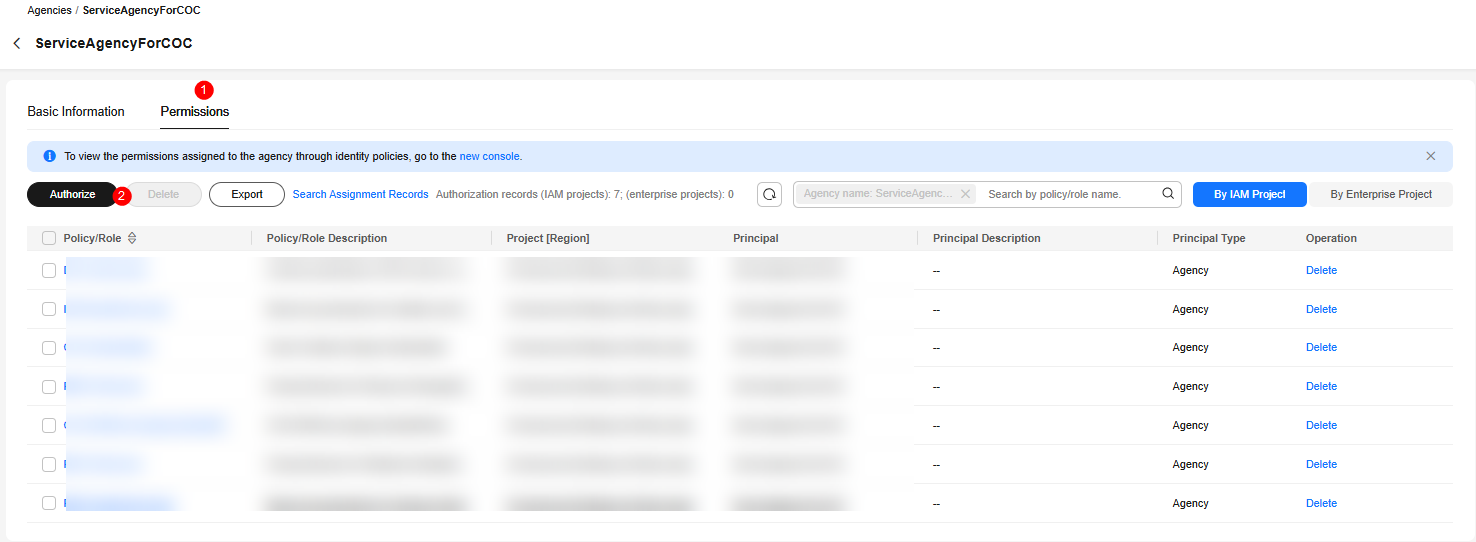
- In the list below, click ServiceAgencyForCOC.
- Click Permissions.
- Click Authorize.
Figure 6 Granted permissions
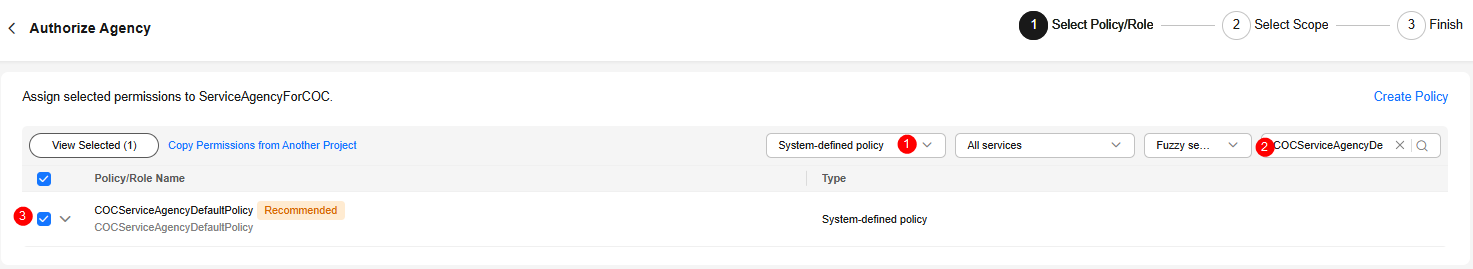
- Set Type to System-defined policy, enter the missing policy name (for example, COCServiceAgencyDefaultPolicy) in the text box on the right, and select the policy.
Figure 7 Selecting a policy
- Click Next, confirm the authorization scope, and click OK.
- If the system prompts that the authorization succeeded, the policy has been added to the ServiceAgencyForCOC agency. The alerting information on the top of the COC page disappears.
- If the following error message is displayed, the current user does not have the permissions in iam:permissions:grantRoleToAgency, contact the master account or an account with administrator permissions to add the missing policy displayed in the alerting information to the ServiceAgencyForCOC agency.
Figure 8 Error message
Modifying or Deleting Agency Permissions
After COC is enabled, if an agency has excessive or insufficient permissions, you can modify the agency policy on IAM.
- You can change the cloud service, validity period, description, and permissions for cloud service agencies, but not the agency name and type.
- Modifying the permissions of cloud service agencies may affect the usage of certain functions of cloud services. Exercise caution when performing this operation.
- For more information about agencies, visit IAM.
- To modify the permissions, validity period, and description of an agency, locate the agency you want to modify and click Modify.
Figure 9 Agencies
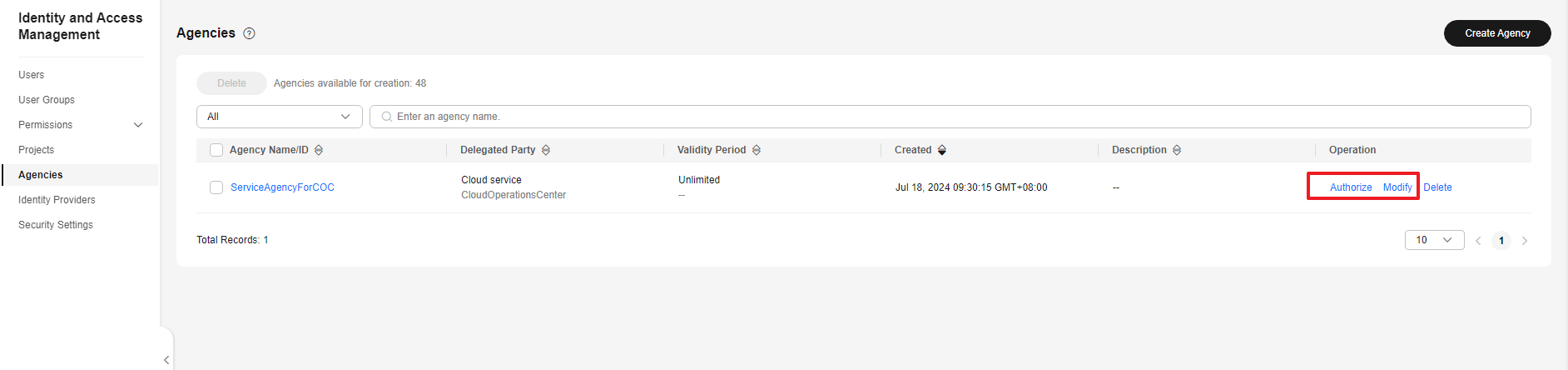
- If you need to authorize the agency or delete the authorized permissions, perform operations on the permission granting page.
Figure 10 Granted permissions
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





