Synchronizing OneAccess Organization Users to Huawei Cloud Astro Zero
OneAccess is an identity management service that enables you to centrally manage, authenticate, and authorize identities. With OneAccess, you can control access of your users to cloud and on-premises applications, and defend against access risks. OneAccess is integrated into Huawei Cloud Astro Zero so that you can directly use OneAccess to manage portal users.
Prerequisites
Before integrating OneAccess into Huawei Cloud Astro Zero, complete the following configurations.
- Purchase OneAccess instances.
Before using OneAccess, you need to purchase OneAccess instances. For details, see Buying an Instance.
- Add an organization (equivalent to Huawei Cloud Astro Zero's role) and a user (equivalent to Huawei Cloud Astro Zero's portal user) to OneAccess.
The organization is used to manage enterprise employees. Each company or department corresponds to one organization. You can add users to an organization to manage and authorize them in batches. The top organization, as the root node, can have multiple sub-organizations and users. Additionally, multiple levels of organizations and users can be added under these sub-organizations. For details about how to add an organization and a user, see Adding an Organization and Creating a User.
- You can add an app to the OneAccess instance management portal. By configuring OneAccess integration authentication information, you can establish a trust relationship between OneAccess and Huawei Cloud Astro Zero.
For details about how to add an application and grant permissions, see Adding an Application and Authorization Management. The authorized account is the user added in 2.
- Configure the application in OneAccess so that users can log in to it through OneAccess.
- Configure authentication information by referring to Authentication Integration.
Currently, Huawei Cloud Astro Zero can be integrated with OneAccess in OAuth2, SAML2, or CAS authentication mode.
- OAuth2: OAuth is an open standard that allows users to authorize third-party applications to access their information stored on a specific resource server without sharing usernames and passwords with the third-party applications.
- SAML2: SAML 2.0 is an XML-based protocol that uses security tokens containing assertions to pass information about an end user between an IdP and an SP. SAML 2.0 is a standard proposed by the Organization for Standardization (OASIS) for secure operations. It is an open standard used by many identity providers (IdPs). For details about SAML 2.0, see SAML 2.0 Technical Overview.
- CAS: CAS is an HTTP2- and HTTP3-based protocol, requiring access to each component through a specific URL. You can configure OneAccess as a service provider using the CAS protocol to enable user accounts of third-party applications to access OneAccess.
- Obtain the authentication information.
Choose General > API Authentication Credential, click Enable, and record the values of ClientId and ClientSecret, which will be used in 1.
- ClientSecret is an important credential used to verify the identity of a developer. Do not provide the ClientSecret to other developers or store it in code.
- OneAccess does not store ClientSecret. Keep it properly after obtaining it.
- You can reset ClientSecret. If you reset ClientSecret, the new ClientSecret takes effect immediately, and all interfaces that use the old ClientSecret become invalid. Exercise caution when performing this operation.
- Grant API permissions to the application. For details, see Authorizing Access to Built-in APIs.
- Authorize users by referring to Authorization Management > Managing Application Accounts > Configuring Authorization Policies for Application Accounts.
- Enable the application organization model and synchronize organization data to the enterprise application by referring to Object Models > Application Organizations.
- Configure authentication information by referring to Authentication Integration.
Configuring OneAccess Integration Authentication Information
- Configure the OneAccess integration authentication information in Huawei Cloud Astro Zero.
- Log in to the Huawei Cloud Astro Zero console and click Access Homepage. The application development page is displayed.
- In the upper left corner of the page, click
 and choose Environments > Environment Configuration.
and choose Environments > Environment Configuration. - In the navigation pane, choose Integrated Connection > Identity Authentication.
- Click the OneAccess icon.
- Configure the label, name, and logo, and click the next button.
Table 1 Basic parameters Parameter
Description
Label
Create a label for OneAccess integration authentication for display.
Name
Name of the OneAccess integration authentication, which must be globally unique. The address determines the account to be authenticated based on the name. The naming requirements are as follows:
- Enter up to 64 characters.
- Start with a letter and can contain only letters, digits, and underscores (_). Do not end with an underscore (_).
Logo
Create a logo for OneAccess integration authentication.
- In the authentication protocol area, select OAuth2, SAML2, or CAS based on the authentication mode set for OneAccess in 4, set the authentication provider, and click the next button.
Table 2 Parameters for configuring OAuth2 authentication Parameter
Description
Authentication Protocol
Authentication protocol between Huawei Cloud Astro Zero and OneAccess.
Domain of OneAccess
Log in to the OneAccess instance console to obtain the user access domain name. For details, see Logging In to the OneAccess Administrator Portal.
Authentication Address
Set the authentication login address. The authentication address in OAuth mode is https://{host} /api/v1/oauth2/authorize, where {host} is the domain name of the OneAccess instance.
For obtaining an access token
Request address for obtaining the access token. Set it to https://{host} /api/v1/oauth2/token, where {host} indicates the domain name of the OneAccess instance and access_token indicates the token for accessing the API.
For obtaining user information
URL for obtaining user information. Set it to https://{host} /api/v1/oauth2/userinfo, where {host} indicates the domain name of the OneAccess instance.
Logout Address
After a user logs out of Huawei Cloud Astro Zero, the user is redirected to the logout address of the server. You are advised to configure the logout address. The variable {redirect} can be added to the logout address. During logout, the variable is replaced with the currently configured page address.
Example: https://{host}/api/v1/logout?redirect_url={redirect}
Auto-Create User on Login
Indicates whether to automatically create a user when the user logs in to the system for the first time and the user does not exist in the system.
Profile
When you log in to the system as the OneAccess user, if the user does not exist and automatic user creation is enabled, this permission is used as the default permission for the created user.
Verify state
Indicates whether to verify the state parameter.
After responding to a request, Astro Zero redirects the request to OneAccess. OneAccess determines whether to verify the consistency of the state parameter (that is, the state in the cookie or session) based on the configuration. If the state is inconsistent after the verification is enabled, Huawei Cloud Astro Zero rejects the request and does not send a request for obtaining the access_token. If they are the same, the process runs properly.
You are advised to enable state verification to prevent CSRF attacks.
Table 3 Parameters for configuring CAS authentication Parameter
Description
Authentication Protocol
Authentication protocol between Huawei Cloud Astro Zero and OneAccess.
Domain of OneAccess
Log in to the OneAccess instance console to obtain the user access domain name. For details, see Logging In to the OneAccess Administrator Portal.
Authentication Address
Set the authentication login address. The CAS authentication address is https://{host} /api/v1/cas/login, where {host} is the domain name of the OneAccess instance.
URL used to validate tickets
Address for verifying tickets and obtaining user attribute information. Currently, only CAS 2.0 and CAS 3.0 are supported.
Set the CAS ticket verification address to https://{host} /api/v1/cas/p3/serviceValidate, where {host} indicates the domain name of the OneAccess instance.
Logout Address
After a user logs out of Huawei Cloud Astro Zero, the user is redirected to the logout address of the server. You are advised to configure the logout address. The variable {redirect} can be added to the logout address. During logout, the variable is replaced with the currently configured page address.
Example: https://{host}/api/v1/logout?redirect_url={redirect}
Auto-Create User on Login
Indicates whether to automatically create a user when the user logs in to the system for the first time and the user does not exist in the system.
Profile
When you log in to the system as the OneAccess user, if the user does not exist and automatic user creation is enabled, this permission is used as the default permission for the created user.
Table 4 Parameters for configuring SAML2 authentication Parameter
Description
Authentication Protocol
Authentication protocol between Huawei Cloud Astro Zero and OneAccess.
Domain of OneAccess
Log in to the OneAccess instance console to obtain the user access domain name. For details, see Logging In to the OneAccess Administrator Portal.
Logout Address
After a user logs out of Huawei Cloud Astro Zero, the user is redirected to the logout address of the server. You are advised to configure the logout address. The variable {redirect} can be added to the logout address. During logout, the variable is replaced with the currently configured page address.
Example: https://{host}/api/v1/logout?redirect_url={redirect}
Auto-Create User on Login
Indicates whether to automatically create a user when the user logs in to the system for the first time and the user does not exist in the system.
Profile
When you log in to the system as the OneAccess user, if the user does not exist and automatic user creation is enabled, this permission is used as the default permission for the created user.
Verify state
Indicates whether to verify the state parameter.
After responding to a request, Astro Zero redirects the request to OneAccess. OneAccess determines whether to verify the consistency of the state parameter (that is, the state in the cookie or session) based on the configuration. If the state is inconsistent after the verification is enabled, Huawei Cloud Astro Zero rejects the request and does not send a request for obtaining the access_token. If they are the same, the process runs properly.
You are advised to enable state verification to prevent CSRF attacks.
Client Certificate
Public key of the SAML client signature certificate.
To obtain the public key of a self-signed certificate, for example, saml.crt, perform the following steps. The certificate created using this method applies only to test scenarios.
- Run the following command on the Linux host to generate the key file saml.key:
openssl genrsa -out saml.key 2048
After the command is executed, a private key file saml.key is generated in the current directory.
The generated key must be in the following format:
-----BEGIN PRIVATE KEY----- …………………………………………….. -----END PRIVATE KEY-----
- Use the key file obtained in the previous step to generate the saml.csr file.
openssl req -new -key saml.key -out saml.csr
- Enter the country, region, organization, email address, and common name as prompted, and press Enter. Set the common name to the username or domain name. If HTTPS is used, the common name must be set to the domain name. Otherwise, an alarm will be generated on the browser.
- Issue the certificate file saml.crt using the generated file.
openssl x509 -req -days 365 -in saml.csr -signkey saml.key -out saml.crt
The generated certificate must be in the following format:
-----BEGIN CERTIFICATE----- ..................................................................... -----END CERTIFICATE-----
Client Certificate Private Key
Private key of the SAML signature certificate.
The self-signed certificate private key is the saml.key file generated during the creation of the client certificate. Certificates created this way apply only for testing scenarios.
Idp Metadata File
Metadata file of the SAML server, which is obtained from the SAML identity provider. For details about how to obtain the file, see Obtaining IdP Metadata.
- Run the following command on the Linux host to generate the key file saml.key:
- In the Identity Source Configuration step, configure the peer authentication ID and peer authentication key, and click the save button.
Peer authentication ID and peer authentication key are the values of ClientId and ClientSecret of the OneAccess application obtained in 4.b.
- Click the synchronization button to synchronize organization and user information. You can synchronize organization and user information immediately or set a scheduled synchronization task.
When users are synchronized to Huawei Cloud Astro Zero, some OneAccess users may already exist in Huawei Cloud Astro Zero. In this case, use the account unification function to control the user synchronization mode.
- When the account unification function is enabled, existing portal users in Huawei Cloud Astro Zero will be synchronized and unified with OneAccess accounts during the synchronization process.
- If this parameter is set to And, the system will require that the mobile number, email address, and username all match in order to normalize the portal user account.
- If this parameter is set to Or and the mobile number, email address, and username are all selected, the system will normalize the portal user account if any one of these matches. It checks in the order of mobile number, email address, then username, and stops once a match is found.
- If you do not enable the unified account configuration function, a portal user will be created for the account in OneAccess.
Figure 1 Synchronous identity authentication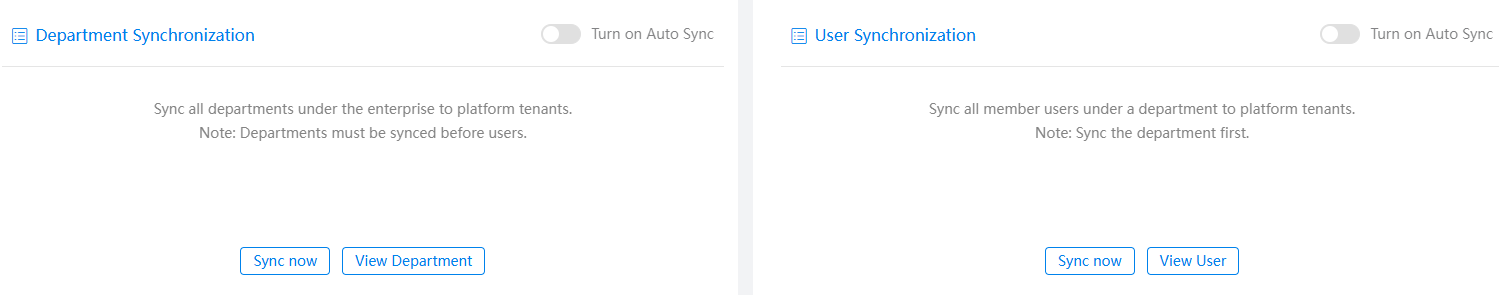
- Synchronizing departments or users immediately
- Click Sync now under Department Synchronization. In the dialog box that is displayed, select Also clear departments that are not included to clear the deleted OneAccess departments from Huawei Cloud Astro Zero. Click the confirm button.
- Click Sync now under User Synchronization. In the dialog box that is displayed, select Also clear users that are not included to clear the deleted OneAccess users from Huawei Cloud Astro Zero. Click the confirm button.
- Setting a scheduled task to implement automatic synchronization
- In the Department Synchronization area, enable Turn on Auto Sync, click Automatic Synchronization Settings under Department Synchronization, set the first synchronization time and execution period, and select Also clear departments that are not included to clear the departments deleted from OneAccess in Huawei Cloud Astro Zero, click the confirm button.
- In the User Synchronization area, enable Turn on Auto Sync, click Automatic Synchronization Settings under User Synchronization, set the first synchronization time and execution period, and select Also clear users that are not included to clear the deleted users in OneAccess from Huawei Cloud Astro Zero, click the confirm button.
The system synchronizes the OneAccess organization information to the Organizations & Users > Organizations page of the Huawei Cloud Astro Zero service configuration center, and synchronizes the OneAccess user information to the Organizations & Users > Users page of the Huawei Cloud Astro Zero service configuration center.
The organization-level user information synchronized here is the OneAccess global organization user information. This information is not in a one-to-one relationship with the organizations and accounts added in the OneAccess application associated with Huawei Cloud Astro Zero. A global user can only be authenticated and logged in after being authorized by the OneAccess application. Therefore, only authorized users in the OneAccess application can log in to the system.
- When the account unification function is enabled, existing portal users in Huawei Cloud Astro Zero will be synchronized and unified with OneAccess accounts during the synchronization process.
- (Optional) In the authentication configuration area, click the download button to download the SP metadata file. You need to configure the file in the identity provider.
Perform this step only when the authentication protocol in 1.f is set to SAML2.
- Configure authentication information in OneAccess.
- Log in to the OneAccess instance management portal. In the navigation pane, choose Resources > Applications.
- Click the added application and click the application icon on the application information page.
- Click Authentication Integration in the left pane, and configure the authentication parameters.
- If the authentication protocol is set to Oauth2 or CAS, refer to Table 5.
Table 5 Description Parameter
Description
Standard Authentication
The standard authorization mode is the most common and secure authentication method. It is designed for web applications with backends. In this mode, authorization codes are sent via the frontend, while tokens are stored securely in the backend to prevent leakage. All interactions with the resource server also occur in the backend.
Simplified Authentication
For web applications without a backend, tokens are stored in the frontend. This mode is suitable for scenarios with lower security requirements and omits the step of obtaining an authorization code, unlike the standard authorization mode.
Resource Owner Password
This mode is suitable for scenarios where users have high trust in clients. Users provide their usernames and passwords to the clients to apply for tokens.
Client Password
This mode is suitable for applications that do not have frontends. In this mode, clients initiate token requests.
Callback URL
Callback URL after successful authorization. Set this parameter to https://{host}/baas/auth/v1.0/idp/authorize/{Authentication configuration name}.
host indicates the environment domain name of Huawei Cloud Astro Zero. The authentication setting name is the name set in 1.e and must contain the namespace.
Mandatory. During authentication, OneAccess verifies the address of Huawei Cloud Astro Zero.
Logout URL
Logout URL to be visited after a user logs out of their session.
Access Token Validity
Validity period of the access token in seconds. The default value is 7200 seconds, that is, 2 hours.
Refresh Token Validity
Validity period of the refresh token. The default value is 0, indicating that the refresh token is not supported. When the access token of a user expires, the user can use their refresh token to obtain a new one.
The prerequisite for automatic token update is that the validity period of the refresh token is longer than that of the access token.
- If the authentication protocol is set to SAML, click Upload File to upload the SP metadata file downloaded in 1.i.
- If the authentication protocol is set to Oauth2 or CAS, refer to Table 5.
- Log in to the system as an authorized user to access the service application.
For example, to access the default application portal page, enter https://{host}/baas/auth/v1.0/idp?client-name={Authentication configuration name}&redirect=https://{host}/app/portal.html.
host indicates the environment domain name of Huawei Cloud Astro Zero. The authentication setting name is the name set in 1.e and must contain the namespace. The value of redirect can be set to the URL of the page to visit after login, and it needs to be URL-encoded.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





