Creating a User Desktop Image
Scenarios
This section describes how to create a user desktop image.
Prerequisites
- You have obtained the username and password for logging in to the console.
- You have obtained the password of the OS administrator Administrator.
Creating an Image
- Log in to the ECS console.
- In the service list, choose Elastic Cloud Server.
- Locate the row that contains the desired ECS, and choose More > Manage Image > Create Image.
- On the page for creating a private image, configure parameters as prompted.
- Type: Select Create Image.
- Image Type: Select System disk image.
- Source: Select ECS. Select an ECS that has been stopped in Configuring an ECS.
- Name: Configure this parameter based on the actual OS, for example, Workspace_Image_01.
- Enterprise Project: Select the enterprise project to which the resource belongs, for example, default.
- Check the box I have read and agree to the Statement of Commitment to Image Creation and Image Disclaimer and click Next.
- Click Submit.
It takes about 10 to 15 minutes to create an image. The created image is displayed in the list under Cloud Server Console > Image Management Service > Private Image.
Configuring a Certificate and Secure Boot for the Image
After the image is created, call the API to configure the certificate of version 2011 and VTPM secure boot.
- Obtain the public key certificate as follows before enabling secure boot:
- Platform key: Click here to obtain the WindowsOEMDevicesPK.der certificate.
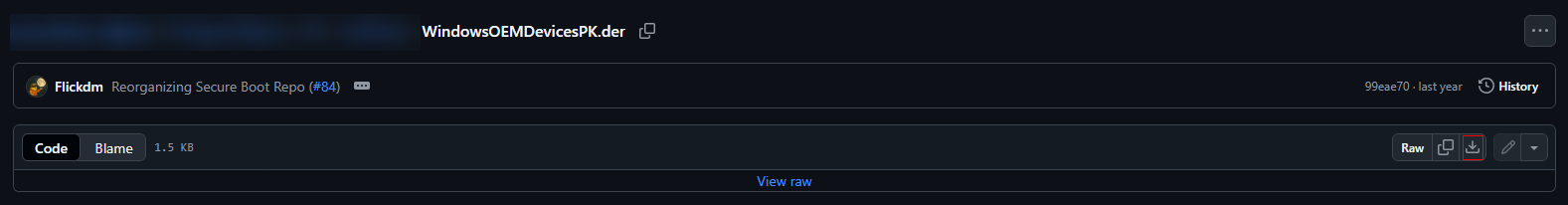
- Key exchange key: Click here to obtain the MicCorKEKCA2011_2011-06-24.der certificate.
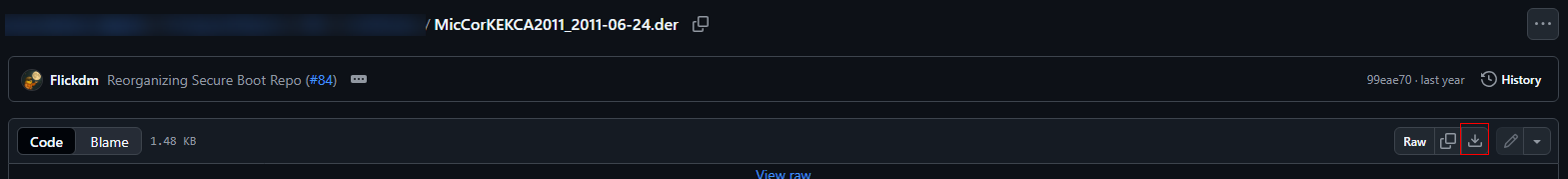
- Signature database: Click here to obtain the MicWinProPCA2011_2011-10-19.der certificate.
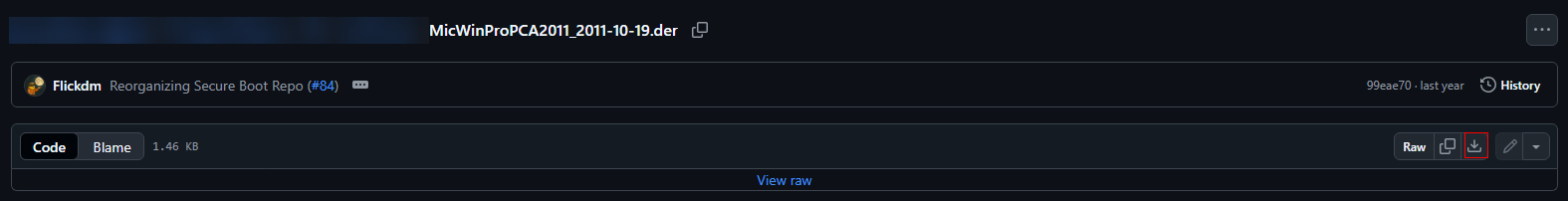
- Platform key: Click here to obtain the WindowsOEMDevicesPK.der certificate.
- Search for Windows PowerShell in the Start menu of the local Windows PC, and click Run as administrator to open the Windows PowerShell window.
- Run the following commands in sequence to convert the certificate obtained in 1 to the Base64 format:
- Convert the WindowsOEMDevicesPK.der certificate to the Base64 format:
[System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes("WindowsOEMDevicesPK.der certificate storage path")) | Out-File -FilePath "WindowsOEMDevicesPK.base64 certificate generation path" -NoNewline
- Convert the MicCorKEKCA2011_2011-06-24.der certificate to the Base64 format:
[System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes("MicCorKEKCA2011_2011-06-24.der certificate storage path")) | Out-File -FilePath "MicCorKEKCA2011_2011-06-24.base64 certificate generation path" -NoNewline
- Convert the MicWinProPCA2011_2011-10-19.der certificate to the Base64 format:
[System.Convert]::ToBase64String([System.IO.File]::ReadAllBytes("MicWinProPCA2011_2011-10-19.der certificate storage path")) | Out-File -FilePath "MicWinProPCA2011_2011-10-19.base64 certificate generation path" -NoNewline

Replace the three certificate storage paths and three certificate generation paths in the preceding commands with the actual ones.
Example of the WindowsOEMDevicesPK.der certificate:
- Example of the certificate storage path: C:\WindowsOEMDevicesPK.der
- Example of the certificate generation path: C:\WindowsOEMDevicesPK.base64
- Convert the WindowsOEMDevicesPK.der certificate to the Base64 format:
- Call the APIs to enable secure boot and VTPM.
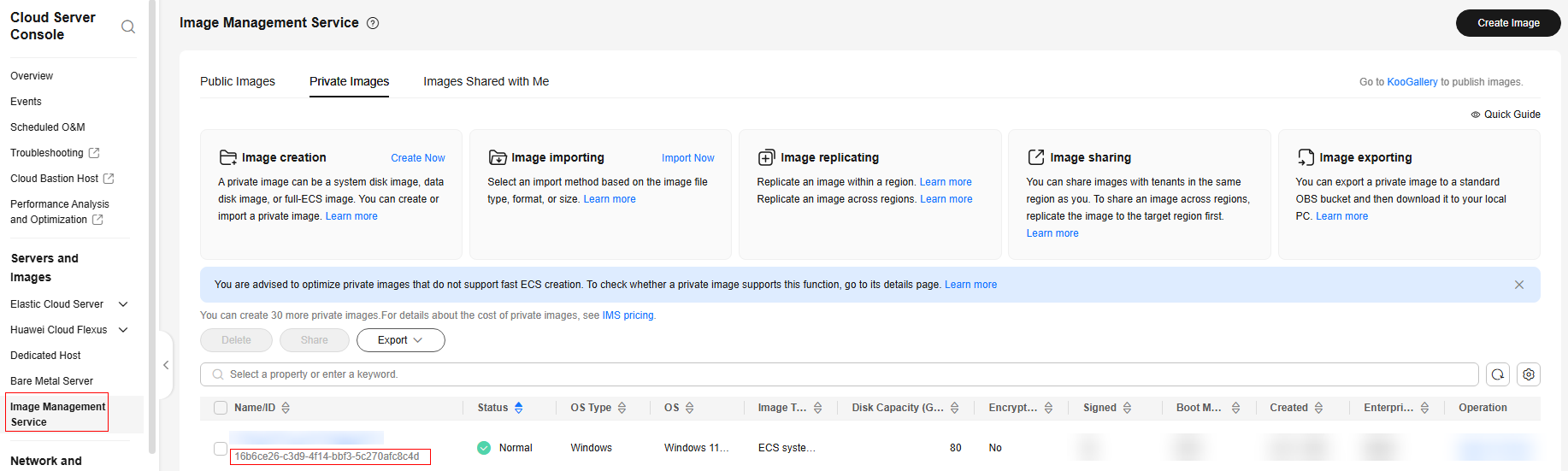
- Obtain the image_id. In the navigation pane of the ECS console, choose Image Management Service.
- On the Image Management Service page, obtain the image ID, as shown in Figure 1.
- Edit the following content:
Replace the values of the following parameters:
- Replace $__platform_key with the content of the WindowsOEMDevicesPK.base64 certificate generated in 3.
- Replace $__key_exchange_key with the content of the MicCorKEKCA2011_2011-06-24.base64 certificate generated in 3.
- Replace $__signature_database with the content of the MicWinProPCA2011_2011-10-19.base64 certificate generated in 3.
Do not copy -----BEGIN CERTIFICATE----- in the first line and -----END CERTIFICATE----- at the end when copying the key content in 3.
[ { "op": "add", "path": "/__support_tpm", "value": "true" },{ "op": "add", "path": "/__support_secure_boot", "value": "true" }, { "op": "add", "path": "/__platform_key", "value": "$__platform_key" }, { "op": "add", "path": "/__key_exchange_key", "value": "$__key_exchange_key" }, { "op": "add", "path": "/__signature_database", "value": "$__signature_database" } ]
- Call the API through API Explorer.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot