Installing ICAgent (Extra-Region Hosts)
An extra-region host refers to a host located outside the current Huawei Cloud region or a non-Huawei Cloud host. This category includes hosts in self-built Internet Data Centers (IDCs), those provided by third parties, and those in other Huawei Cloud regions. To collect logs from extra-region hosts to LTS, ensure that the hosts can communicate with LTS located in the current Huawei Cloud region, and then install ICAgent on the hosts. ICAgent is a log collection tool for LTS. It runs on hosts where logs need to be collected.
Extra-region hosts use two types of network channels to report logs to LTS:
- Public network: An extra-region host connected to the public network can communicate with and report logs to LTS in the current Huawei Cloud region through the public network. However, for security reasons, private lines are usually preferred in actual production environments.
If you select Public network when installing ICAgent on an extra-region host, ensure that the region supports log reporting via public networks.
- Private line: Extra-region hosts connect to LTS in the current Huawei Cloud region through a jump server or VPCEP, offering greater security and stability. In this scenario, extra-region hosts cannot communicate with LTS in the current region by default, and ICAgent installed on these hosts cannot directly access the network segment used by the Huawei Cloud management plane to report logs. Therefore, you need to configure a network connection solution to use a jump server or VPCEP to connect to the LTS backend and forward data to LTS.
- Jump server: functions as a data forwarder and forwards the data collected by ICAgent from extra-region hosts to LTS. This solution is suitable for tests or scenarios with low log traffic. VPCEP is recommended for scenarios with high log traffic.
- VPCEP: provides convenient and secure channels to connect to LTS in the current region, enabling resources in the VPC to access VPCEP without the need for EIPs. This solution reduces the risks of data transmission on public networks and improves the transmission security and efficiency.
Prerequisites
Before installing ICAgent, ensure that the time and time zone of your local browser are consistent with those of the host. If they are inconsistent, errors may occur during log reporting.
Installation Scenario Description
There are two methods to install ICAgent. Select one that best suits your needs.
|
Scenario |
Description |
|---|---|
|
Initial installation |
You can use this method to install ICAgent on a host that has no ICAgent installed. |
|
Inherited installation (supported only for Linux hosts) |
When ICAgent has already been installed on one host but needs to be installed on multiple hosts, you can use this method. |
Initial Installation
If ICAgent has not been installed on your host, follow these OS-specific steps.
- Log in to the LTS console.
- Choose Host Management > Hosts in the navigation pane.
- Click Install ICAgent.
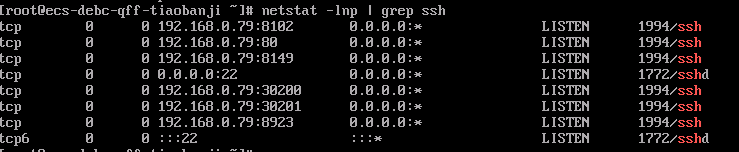
Figure 1 Installing ICAgent
- Set Host to Extra-region hosts.
- Set OS to Linux.
- Set Network Connectivity. For extra-region hosts to report logs to LTS in the current region, you are advised to select Private line for higher stability and reliability.
- Set LTS Backend Connection. If you select Private line in the previous step, the extra-region host cannot communicate with LTS in the current region by default, and ICAgent installed on the host cannot directly access the network segment used by the Huawei Cloud management plane to report logs. Therefore, you need to configure a network connection solution using either a jump server or VPCEP to connect to LTS.
- If you set LTS Backend Connection to VPCEP:
Configure a VPCEP domain name. With the assistance of Huawei Cloud network engineers, configure DNS domain name resolution rules in other regions to resolve VPCEP domain names to specified IP addresses. Then, copy the command as prompted on the Install ICAgent page.
ping {VPCEP domain name}Run this command on the host you want to collect logs from. If the ping command succeeds, the network configuration is correct. Proceed to 8.
- If you set LTS Backend Connection to Jump server:
- Create a Linux ECS as a jump server.
Log in to the ECS console and create a Linux ECS. For details, see Purchasing an ECS. If you have an ECS that meets the requirements for use as a jump server, skip this step.
- You are advised to use CentOS 6.5 64bit or later images. The minimum flavor for the ECS is 1 vCPU and 1 GB of memory, while the recommended flavor is 2 vCPUs and 4 GB of memory.
- If the jump server communicates with the extra-region host over the public network, an EIP must be enabled. Conversely, when it uses a VPC peering connection, an EIP is not required.
- The jump server must be in the same region as LTS.
- Add security group rules for the jump server and enable the corresponding inbound ports to ensure data connectivity between the extra-region hosts and the jump server.
- Log in to the ECS console, check the ECS list, and locate the ECS that you created as the jump server.
- Click its name to go to the ECS details page. Click the security group name to access the security group details page.
- Click the Inbound Rules tab and click Add Rule. Set the ports by referring to Table 2. Set other parameters based on your network requirements. For details, see Adding a Security Group Rule.
- Return to the ECS list, locate the ECS created in 7.a, and view its private IP address and EIP (available if an EIP has been enabled).
- Go back to the LTS console. On the Install ICAgent page, enter the obtained private IP address of the jump server to generate its SSH tunneling command. The private IP address of the jump server refers to the internal IP address of the VPC where the jump server is located.
- On the Install ICAgent page, click Copy Command to copy the SSH tunneling command.
ssh -f -N -L {Private IP address of the jump server}:8149:{LTS reporting IP address}:8149 -L {Private IP address of the jump server}:8102:{LTS reporting IP address}:8102 -L {Private IP address of the jump server}:8923:{LTS reporting IP address}:8923 -L {Private IP address of the jump server}:30200:{LTS reporting IP address}:30200 -L {Private IP address of the jump server}:30201:{LTS reporting IP address}:30201 -L {Private IP address of the jump server}:80:icagent-{Region}.{OBS domain name}:80 {Private IP address of the jump server} - Log in to the jump server as user root and run the copied SSH tunneling command.
- Run the following command to check whether the corresponding ports are being listened to. If the command output similar to Figure 2 is returned, the TCP ports are open.
netstat -lnp | grep ssh
If the jump server powers off and restarts, run the command again.
netstat -lnp | grep ssh
- On the Install ICAgent page, enter the DC and the connection IP address of the jump server.
- DC: Specify a name for the data center of the host so it is easier to find the host. Enter up to 64 characters. Use only digits, letters, hyphens (-), and underscores (_).
- Connection IP: If the jump server communicates with the extra-region host via EIP connection, enter the EIP of the jump server. Conversely, when using a VPC peering connection, enter the internal IP address (private IP address) of the VPC where the jump server locates. For the EIP and private IP address, see 7.c.
- Create a Linux ECS as a jump server.
- If you set LTS Backend Connection to VPCEP:
- Obtain an AK/SK. For details, see How Do I Obtain an Access Key (AK/SK)? On the Install ICAgent page, copy the ICAgent installation command and replace the AK/SK in the command with the obtained one.
- Log in to the extra-region host as user root (by using a remote login tool such as PuTTY) and run the copied command.
When message "ICAgent install success" is displayed, ICAgent has been installed in the /opt/oss/servicemgr/ directory of the host. You can then choose Host Management > Hosts in the navigation pane of the LTS console to check the ICAgent status.
If the installation fails, uninstall ICAgent and reinstall it. If the reinstallation fails, contact technical support.
The NIC information is obtained by ICAgent installed on the node using the ifconfig command. If inet information is not configured for the NIC, the IPv4 address is not reported, and -- is displayed in the Host IPv4 Address column on the Hosts page. If inet6 information is not configured, the IPv6 address is not reported, and -- is displayed in the Host IPv6 Address column on the Hosts page.
- Choose Host Management > Hosts in the navigation pane.
- Click Install ICAgent.
- Set Host to Extra-region hosts.
- Set OS to Windows.
Figure 3 Installing ICAgent (Windows)
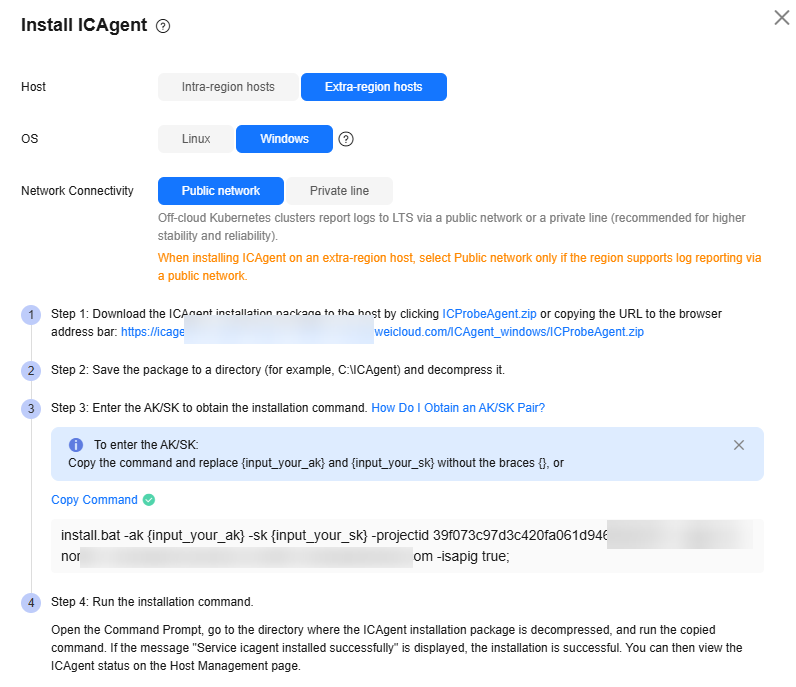
- Set Network Connectivity. Extra-region hosts report logs to LTS via a public network or a private line. The latter is recommended for higher stability and reliability.
- Set LTS Backend Connection. If you select Private line in the previous step, the extra-region host cannot communicate with LTS in the current region by default, and ICAgent installed on the host cannot directly access the network segment used by the Huawei Cloud management plane to report logs. Therefore, you need to configure a network connection solution using either a jump server or VPCEP to connect to LTS.
- If you set LTS Backend Connection to VPCEP:
Configure a VPCEP domain name. With the assistance of Huawei Cloud network engineers, configure DNS domain name resolution rules in other regions to resolve VPCEP domain names to specified IP addresses. Then, copy the command as prompted on the Install ICAgent page.
ping {VPCEP domain name}Run this command on the host you want to collect logs from. If the ping command succeeds, the network configuration is correct. Proceed to 7.
- If you set LTS Backend Connection to Jump server:
- Create a Linux ECS as a jump server.
Log in to the ECS console and create a Linux ECS. For details, see Purchasing an ECS. If you have an ECS that meets the requirements for use as a jump server, skip this step.
- You are advised to use CentOS 6.5 64bit or later images. The minimum flavor for the ECS is 1 vCPU and 1 GB of memory, while the recommended flavor is 2 vCPUs and 4 GB of memory.
- If the jump server communicates with the extra-region host over the public network, an EIP must be enabled. Conversely, when it uses a VPC peering connection, an EIP is not required.
- The jump server must be in the same region as LTS.
- Add security group rules for the jump server and enable the corresponding inbound ports to ensure data connectivity between the extra-region hosts and the jump server.
- Log in to the ECS console, check the ECS list, and locate the ECS that you created as the jump server.
- Click its name to go to the ECS details page. Click the security group name to access the security group details page.
- Click the Inbound Rules tab and click Add Rule. Set the ports by referring to Table 3. Set other parameters based on your network requirements. For details, see Adding a Security Group Rule.
- Return to the ECS list, locate the ECS created in 6.a, and view its private IP address and EIP (available if an EIP has been enabled).
- Go back to the LTS console. On the Install ICAgent page, enter the obtained private IP address of the jump server to generate its SSH tunneling command. The private IP address of the jump server refers to the internal IP address of the VPC where the jump server is located.
- On the Install ICAgent page, click Copy Command to copy the SSH tunneling command.
ssh -f -N -L {Private IP address of the jump server}:8149:{LTS reporting IP address}:8149 -L {Private IP address of the jump server}:8102:{LTS reporting IP address}:8102 -L {Private IP address of the jump server}:8923:{LTS reporting IP address}:8923 -L {Private IP address of the jump server}:30200:{LTS reporting IP address}:30200 -L {Private IP address of the jump server}:30201:{LTS reporting IP address}:30201 -L {Private IP address of the jump server}:80:icagent-{Region}.{OBS domain name}:80 {Private IP address of the jump server} - Log in to the jump server as user root and run the copied SSH tunneling command.
- Run the following command to check whether the corresponding ports are being listened to. If the command output similar to Figure 4 is returned, the TCP ports are open.
netstat -lnp | grep ssh
If the jump server powers off and restarts, run the command again.
netstat -lnp | grep ssh
- Create a Linux ECS as a jump server.
- If you set LTS Backend Connection to VPCEP:
- Click the link on the Install ICAgent page to download the ICAgent installation package.
- Save the ICAgent installation package to a directory on the Windows host, for example, C:\ICAgent, and decompress the package.
- Obtain an AK/SK and save it to replace the AK/SK in the installation command. For details, see How Do I Obtain an Access Key (AK/SK)?
If you set LTS Backend Connection to Jump Server, you also need to set Connection IP.
Connection IP: If the jump server communicates with the extra-region host via EIP connection, enter the EIP of the jump server. Conversely, when using a VPC peering connection, enter the internal IP address (private IP address) of the VPC where the jump server locates. For the EIP and private IP address, see 6.c.
- On the Install ICAgent page, click Copy Command to copy the ICAgent installation command.
- Log in to the Windows host, open the Command Prompt, go to the directory where the ICAgent installation package is decompressed, and run the ICAgent installation command.
If the message "Service icagent installed successfully" is displayed, the installation is successful. You can then choose Host Management > Hosts in the navigation pane of the LTS console to check the ICAgent status.
If the installation fails, uninstall ICAgent and reinstall it. If the reinstallation fails, contact technical support.
The NIC information is obtained by ICAgent installed on the node using the ifconfig command. If inet information is not configured for the NIC, the IPv4 address is not reported, and -- is displayed in the Host IPv4 Address column on the Hosts page. If inet6 information is not configured, the IPv6 address is not reported, and -- is displayed in the Host IPv6 Address column on the Hosts page.
Creating Multiple Jump Servers for Load Balancing Using ELB
A single jump server may encounter a single point of failure (SPOF), potentially leading to O&M instability. To mitigate this, you can create multiple jump servers and use ELB to distribute traffic among them, enhancing access reliability.
- Create a Linux ECS as a jump server.
Log in to the ECS console and create a Linux ECS. For details, see Purchasing an ECS. If you have an ECS that meets the requirements for use as a jump server, skip this step.
- You are advised to use CentOS 6.5 64bit or later images. The minimum flavor for the ECS is 1 vCPU and 1 GB of memory, while the recommended flavor is 2 vCPUs and 4 GB of memory.
- If the jump server communicates with the extra-region host over the public network, an EIP must be enabled. Conversely, when it uses a VPC peering connection, an EIP is not required.
- The jump server must be in the same region as LTS.
- Add security group rules for the jump server and enable the corresponding inbound ports to ensure data connectivity between the extra-region hosts and the jump server.
- Log in to the ECS console, check the ECS list, and locate the ECS that you created as the jump server.
- Click its name to go to the ECS details page. Click the security group name to access the security group details page.
- Click the Inbound Rules tab and click Add Rule. Set the ports by referring to Table 4. Set other parameters based on your network requirements. For details, see Adding a Security Group Rule.
- Return to the ECS list, locate the ECS created in 1, and view its private IP address and EIP (available if an EIP has been enabled).
- Return to the LTS console. In the navigation pane, choose Host Management > Hosts. Click Install ICAgent. On the displayed page, enter the private IP address of the jump server to generate the SSH tunneling command. The private IP address of the jump server refers to the internal IP address of the VPC where the jump server is located.
- On the Install ICAgent page, click Copy Command to copy the SSH tunneling command.
ssh -f -N -L {Private IP address of the jump server}:8149:{LTS reporting IP address}:8149 -L {Private IP address of the jump server}:8102:{LTS reporting IP address}:8102 -L {Private IP address of the jump server}:8923:{LTS reporting IP address}:8923 -L {Private IP address of the jump server}:30200:{LTS reporting IP address}:30200 -L {Private IP address of the jump server}:30201:{LTS reporting IP address}:30201 -L {Private IP address of the jump server}:80:icagent-{Region}.{OBS domain name}:80 {Private IP address of the jump server} - Log in to the jump server as user root and run the copied SSH tunneling command.
- Repeat the preceding steps to create multiple jump servers. Add them to the same VPC by selecting the same VPC for Network during their creation.
- Log in to the ELB console and create a load balancer. For details, see Creating a Dedicated Load Balancer. When creating the load balancer, you should:
- Select the same VPC as that of the jump servers during network configuration.
- Create an EIP for the load balancer. It is used for connection with the jump servers.
- Apply for the bandwidth based on the service requirements.
- Add listeners for TCP ports 30200, 30201, 8149, 8923, 8102, and 80. For details, see Adding a TCP Listener.
- Create a backend server group and add all jump servers in the group. For details, see Adding Backend Servers.
- Return to the LTS console. On the Install ICAgent page, enter the EIP of the load balancer in Connection IP, copy the installation command, and run it on the extra-region host.
Inherited Installation
When ICAgent has already been installed on one host but needs to be installed on multiple others, you can use the inherited installation or batch inherited installation method.
Assume that you need to install ICAgent on multiple hosts, and one of the hosts already has ICAgent installed. The ICAgent installation package, ICProbeAgent.tar.gz, is in the /opt/ICAgent/ directory. To install ICAgent on other hosts one by one:
In inherited installation, the hosts must all belong to the same VPC and be on the same subnet.
- Run the following command on the host where ICAgent has been installed, where x.x.x.x is the IP address of the host you want to install ICAgent on.
bash /opt/oss/servicemgr/ICAgent/bin/remoteInstall/remote_install.sh -ip x.x.x.x
- Enter the password for user root of the host when prompted.
- If the Expect tool is installed on the host that has ICAgent installed, the ICAgent installation should be able to complete without prompting you for a password. Otherwise, enter the password as prompted.
- Ensure that user root can run SSH or SCP commands on the host where ICAgent has been installed to remotely communicate with the remote host to install ICAgent.
- If the installation fails, uninstall ICAgent and reinstall it. If the reinstallation fails, contact technical support.
- When message "Install ICAgent success" is displayed, ICAgent has been installed in the /opt/oss/servicemgr/ directory of the host. You can then choose Host Management > Hosts in the navigation pane of the LTS console to check the ICAgent status.
Assume that you need to install ICAgent on multiple hosts, and one of the hosts already has ICAgent installed. The ICAgent installation package, ICProbeAgent.tar.gz, is in the /opt/ICAgent/ directory. In this case, you can follow the directions below to install ICAgent on other hosts in batches. The hosts must all belong to the same VPC and be on the same subnet.
Python 3.* is required for batch installation. If you are prompted that Python cannot be found during ICAgent installation, install Python of a proper version on the host and try again.
Prerequisites
The IP addresses and root's passwords of all hosts to install ICAgent have been collected, sorted in the iplist.cfg file, and uploaded to the /opt/ICAgent/ directory on the host that has ICAgent installed. An IP address and user root's password in the iplist.cfg file must be separated by a space. Examples:
192.168.0.109 Password (Replace the IP address and password with the actual ones)
192.168.0.39 Password (Replace the IP address and password with the actual ones)
- The iplist.cfg file contains sensitive information. You are advised to clear it after using it.
- If all servers share the same password, the iplist.cfg file only needs to include the IP addresses, not passwords. You need to enter the password during execution. If an IP address has a different password, enter the password after the IP address.
Procedure
- Run the following command on the host that has ICAgent installed:
bash /opt/oss/servicemgr/ICAgent/bin/remoteInstall/remote_install.sh -batchModeConfig /opt/ICAgent/iplist.cfg
Enter the default password for user root of the hosts to install ICAgent. If the passwords of all hosts have been configured in the iplist.cfg file, press Enter to skip this step.
Wait for a while. When message "Install ICAgent success" is displayed, ICAgent has been installed on all the hosts listed in the configuration file.
- Choose Host Management > Hosts in the navigation pane of the LTS console to check the hosts' ICAgent statuses. For details, see Checking the ICAgent Status.
Helpful Links
If you have any questions when installing ICAgent, see Host Management in the FAQ.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot