Managing Asset Catalogs
- The Service Domain classifies database assets using labels defined in Asset Group Management. To modify these classification labels, make adjustments directly within Asset Group Management by referring to Managing Asset Groups. You can click a classification label to view the following information:
Proportions of sensitive databases, tables, and columns of the data type and details about all instances contained in the asset.
- The Data Type tab further categorizes assets into Structured Data and Unstructured Data. Clicking a data type displays its sensitive database, table, and column proportions, along with details for all contained instances.
Architecture
Data Type
Structured data
- DWS
- PostgreSQL
- DMDBMS (Dameng)
- MySQL
- GaussDB
- Kingbase
- TDSQL
- SQLServer
- Hive
- MRS_HIVE
Unstructured data
OBS
Prerequisites
- Access to cloud assets has been authorized. For details, see Allowing or Disallowing Access to Cloud Assets.
- Specific assets have been added or authorized. For details, see Adding and Authorizing Data Assets in DSC.
- Metadata scanning has been completed. A metadata scanning task can be automatically triggered. For details, see Step 1: Scanning Metadata.
- Before exporting asset metadata, you need to enable the OBS service. For details about how to enable the OBS service, see Enabling and Using OBS.
Viewing the Asset Catalog
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Asset Management > Asset Catalog.
- In the Service Domain or Data Type tab, view the added data asset information. Table 2 describes related parameters.
- In the Service Domain tab, select a group from the navigation pane to view data assets.
Table 1 Data catalog parameters Parameter
Description
Statistics
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
The Statistics module provides the following information:
- Sensitive databases/Total databases: the percentage of sensitive databases in all databases.
- Sensitive tables/Total tables: the percentage of sensitive data tables in all data tables.
- Sensitive data columns/Total columns: the percentage of sensitive data columns in all data columns.
NOTE:WoW indicates the data changes compared with the previous week.
Percentage of Different Levels of Data
Pie chart showing the proportion of sensitive data columns of different sensitivity levels in the total data columns
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
Top 5 Categories
Top 5 data type with the highest proportion
Click View Details. On the Categorization Result Details page, view the statistics.
Data Volume
Line chart showing the change of data volume over time
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
Databases
Displays the number of databases, tables, and columns that contain sensitive data in a database instance. For details, see Viewing Instance Details or Bucket Details.
- Database Instance/ID: Database instance name or ID.
- Host port: host port number
- User: username
- Sensitive Databases: Number of databases in the instance that contain sensitive data.
- Sensitive Tables: Number of tables in the instance that contain sensitive data.
- Sensitive Columns: Number of columns in the instance that contain sensitive data.
- In the Data Type tab, select a data type from the navigation pane to view data assets.
- The following table lists the structured data asset information.
Table 2 Data catalog parameters Parameter
Description
Statistics
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
The Statistics module provides the following information:
- Sensitive databases/Total databases: the percentage of sensitive databases in all databases.
- Sensitive tables/Total tables: the percentage of sensitive data tables in all data tables.
- Sensitive data columns/Total columns: the percentage of sensitive data columns in all data columns.
NOTE:WoW indicates the data changes compared with the previous week.
Percentage of Different Levels of Data
Pie chart showing the proportion of sensitive data columns of different sensitivity levels in the total data columns
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
Top 5 Categories
Top 5 data type with the highest proportion
Click View Details. On the Categorization Result Details page, view the statistics.
Data Volume
Line chart showing the change of data volume over time
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and database.
Databases
Displays the number of databases, tables, and columns that contain sensitive data in a database instance. For details, see Viewing Instance Details or Bucket Details.
- Database Instance/ID: Database instance name or ID.
- Host port: host port number
- User: username
- Sensitive Databases: Number of databases in the instance that contain sensitive data.
- Sensitive Tables: Number of tables in the instance that contain sensitive data.
- Sensitive Columns: Number of columns in the instance that contain sensitive data.
- Unstructured data asset information table:
Table 3 Data catalog parameters Parameter
Description
Statistics
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and bucket.
The Statistics module provides the following information:
- Sensitive buckets/Total buckets: indicates the ratio of sensitive buckets to all buckets.
- Sensitive files/Scanned files: indicates the ratio of sensitive files to scanned files.
File Information Sensitivity Level Distribution
Displays a pie chart showing the distribution of sensitive files by sensitivity level as a percentage of all files.
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and bucket.
Top 5 Categories
Indicates the five most common data types.
Click View Details. On the Categorization Result Details page, view the statistics.
Data Volume
Line chart showing the change of data volume over time
Click View Details. On the Sensitive Data Statistics page, statistics are displayed in three dimensions: category, level, and bucket.
OBS Buckets
- Displays the OBS databases, sensitive files, and sensitivity levels. Locate an OBS bucket and click Details in the Operation column to view the files in the bucket and their labels, categories, sensitivity levels, and last scan time.
- Click
 to modify the Description, Label, Category, and Sensitivity Level. After sensitive data identification, Category and Sensitivity Level are automatically populated. Click
to modify the Description, Label, Category, and Sensitivity Level. After sensitive data identification, Category and Sensitivity Level are automatically populated. Click  to modify the information and then click
to modify the information and then click  to lock the information, preventing it from being modified again.
to lock the information, preventing it from being modified again.
- The following table lists the structured data asset information.
- In the Service Domain tab, select a group from the navigation pane to view data assets.
Viewing Instance Details or Bucket Details
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Asset Management > Asset Catalog.
- Click the Service Domain or Data Type tab. Under Databases, locate the target database and click
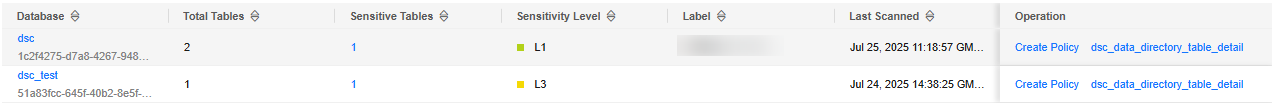
 to view its details, including the database name, total number of tables, number of sensitive tables, sensitivity level, label, and last scan time.
Click the database name. The Database Details page is displayed, including the Basic Information and Database Tables tabs.
to view its details, including the database name, total number of tables, number of sensitive tables, sensitivity level, label, and last scan time.
Click the database name. The Database Details page is displayed, including the Basic Information and Database Tables tabs.- The Basic Information tab displays the database type, version, and name, and allows you to modify the database description, label, category, and sensitivity level. Click Analyze to perform automatic sensitivity level analysis. The sensitivity levels of databases and tables are determined based on their column sensitivity levels generated in the sensitive data identification results.
- The Database Tables area displays the data table name, number of table columns and rows, associated schema, description, label, category, and sensitivity level. You can click the table name, number of columns, or schema name to view details.
Figure 1 Instance details
- Click the Data Type tab, choose OBS under UNSTRUCTURED DATA from the navigation pane. Under OBS Buckets, you can view the OBS databases, sensitive files, and sensitivity levels. Locate an OBS bucket and click Details in the Operation column to view the files in the bucket and their labels, categories, sensitivity levels, and last scan time.
Click
 to modify the Description, Label, Category, and Sensitivity Level. After sensitive data identification, Category and Sensitivity Level are automatically populated. Click
to modify the Description, Label, Category, and Sensitivity Level. After sensitive data identification, Category and Sensitivity Level are automatically populated. Click  to modify the information and then click
to modify the information and then click  to lock the information, preventing it from being modified again.
to lock the information, preventing it from being modified again.
Exporting Asset Metadata
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Asset Management > Asset Catalog.
- Click Export Asset Metadata in the upper right corner. The Export Asset Metadata dialog box is displayed.
- Asset Catalog
- If you click the Service Domain tab, select an asset catalog by service domain from the drop-down list.
- If you select the Data Type tab, select a data type from the drop-down list.
- If no asset catalog is selected, data is exported by data type.
- Target Bucket: Select a bucket from the drop-down list. If no bucket is available in the drop-down list, create an OBS bucket by referring to Creating an OBS Bucket. The catalog-results folder is created in the root directory of the bucket to store the exported file.
OBS storage occupies certain storage space, which may incur fees. For details, see OBS Billing Overview.
- Asset Catalog
- Click OK. The status of Export Asset Metadata changes to Queuing or Running.
- The status of the generated result file is as follows:
- Running: The file is being generated.
- Queuing: The generation task is queuing.
- The status of the generated result file is as follows:
- Click Download Exported File to download the exported file to the local PC.
Importing Classification and Grading Results
Batch import classification and grading results to existing metadata database table columns using the provided template.
- The metada must has been scanned and exist in the system.
- Additionally, the classification and grading template must be pre-configured in Configuring Sensitive Data Identification Policies.
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Asset Management > Asset Catalog.
- Click Import Classification Results in the upper right corner. The Import Classification Results dialog box is displayed.
- Click Download Template to download the template. The requirements for importing data are as follows:
- The uploaded file must be in XLSX format and not exceed 20 MB.
- A maximum of 100,000 data records can be imported.
- If metadata of an imported database, table, or column does not exist in the system, it will be skipped. The system returns details for the first 100 skipped or failed import records.
- If an imported classification and grading template is not found in the system, its associated information will be skipped. To ensure a successful import of all results, create or import the necessary classification and grading template on the Creating an Identification Template page.
- When an imported classification and grading result conflicts with existing metadata classifications, select one of the following processing modes:
- Add: The newly imported classification coexists with existing classification information.
- Overwrite: The newly imported classification replaces the original classification.
- Click Add File. Upon successful file upload, import progress reaches 100%.
- In the Databases area, click the database instance/ID entered in the uploaded template, click the database name in the uploaded template, click the Database Tables tab, click the table name in the uploaded template, click the Table Columns tab, and check whether Category and Security Level of Table Column Name are added.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





