Configuring the Resource Recorder
Scenarios
You must enable the resource recorder for Config to track changes to your resource configurations.
You can modify or disable the resource recorder at any time.
You can enable or modify the resource recorder for up to 10 times per day. The number of times will be reset at 00:00 every day.
This section includes the following content:
Enabling the Resource Recorder with One Click (Recommended)
You can enable the Resource Recorder with only one click in Config. The default settings help you customize configurations with ease. For details about how to customize the Resource Recorder, see Enabling and Configuring the Resource Recorder.
- Log in to the Config console.
- Click
 in the upper left corner of the page. In the service list that is displayed, under Management & Governance, select Config.
in the upper left corner of the page. In the service list that is displayed, under Management & Governance, select Config. - In the navigation pane, choose Overview. On the displayed page, click Enable Resource Recorder.
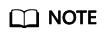
You can enable the Resource Recorder by one click only when the Resource Recorder is disabled. For details, see Disabling the Resource Recorder.
- On the Enable Resource Recorder page, click OK.
- Resource Monitoring Scope: All services and resource types supported by Config are monitored.
- Resource Dump: The OBS bucket config-bucket-DomainId is used, for example, config-bucket-123456789 to store resource snapshots. If you do not have an OBS bucket, the system will create one for you.
- Data Retention Period: The collected resource configuration information will be retained for seven years (2557 days) by default.
Figure 1 Enabling the resource recorder
Customizing and Configuring the Resource Recorder
If you have enabled the resource recorder and specified an OBS bucket and an SMN topic when you configure the resource recorder, Config will notify you of any changes (creation, modification, deletion, relationship change) to the resources within the monitoring scope and periodically store your notifications and resource snapshots.
- Log in to the Config console.
- In the navigation pane on the left, choose Resource Recorder.
- Toggle on Resource Recorder. In the displayed dialog box, click OK.
Figure 2 Enabling the resource recorder

- Select the monitoring scope.
By default, all resources supported by Config will be recorded by the resource recorder. You can also specify a resource scope for the resource recorder.
By default, the resource recorder records all resources of Config, and these resources cannot be deselected.
Figure 3 Specifying the monitoring scope
- Specify an OBS bucket.
Specify an OBS bucket to store notifications of resource changes and resource snapshots.
To enable the resource recorder, you must configure either an SMN topic or an OBS bucket.
- Select an OBS bucket from the current account:
Select Your bucket and then select a bucket from the drop-down list to store resource change notifications and resource snapshots. If you need to store the notifications and snapshots to a specific folder in the OBS bucket, enter the folder name after you select a bucket. If there are no OBS buckets in the current account, create one. For details, see Creating a Bucket.
- Select an OBS bucket from another account:
Select Other users' bucket and then configure Region ID and Bucket Name. If you need to store the notifications and snapshots to a specific folder in the OBS bucket, enter the folder name after you select a bucket. If you select a bucket from another account, you need required permissions granted by the account. For details, see Cross-Account Authorization.
After you specify an OBS bucket from the current or another account, Config will write an empty file named ConfigWritabilityCheckFile to the OBS bucket to verify whether resources can be written to the OBS bucket. If an error is reported, you can handle the error based on Why Is an Error Reported When Data Is Dumped to the OBS Bucket After the Resource Recorder Is Enabled?
Figure 4 Specifying an OBS bucket
- Select an OBS bucket from the current account:
- Specify a data retention period.
Select Seven years (2,557 days) or select A custom period and enter a retention period from 30 days to 2,557 days.
The data retention period only applies to resource configurations and snapshots reserved by Config. It will not affect your data storage with SMN or OBS.
After a retention period is configured, Config will delete data older than the retention period.
If you modify the data retention period, the change is only applied to newly recorded data. Existing data is not affected. For example, if you modify the data retention period from 100 days to 30 days, data recorded after the modification will only be retained for 30 days by Config, and data recorded before the modification will still be retained for 100 days.
Figure 5 Specifying a data retention period
- (Optional) Configure an SMN topic.
Toggle on Topic, then select a region and an SMN topic for receiving notifications of resource changes.
- Select a topic from the current account:
Select Your topic, then select a region and an SMN topic. If there are no SMN topics available, create one first. For details, see Creating a Topic.
- Select a topic from another account:
Select Topic under other account, and then enter a topic URN. For more details about topic URN, see Concepts. If you select a topic from another account, you need required permissions granted by the account. For details, see Cross-Account Authorization.
To send notifications with an SMN topic, you not only need to create the topic, but also add subscriptions and request subscription confirmations.
Figure 6 Selecting an SMN topic
- Select a topic from the current account:
- Grant permissions.
- Quick granting: This option will automatically create an agency named rms_tracker_agency to grant the required permissions for the resource recorder to work properly. The agency contains permissions, including the SMN Administrator for sending notifications and the OBS OperateAccess permission for writing data into an OBS bucket. The agency created by quick granting does not contain KMS permissions, so the resource recorder is unable to store resource snapshots and change notifications to an OBS bucket that is encrypted using KMS. If you need to use an encrypted bucket, you can add required KMS Administrator permissions to the agency or use custom authorization. For details, see Storing Resource Change Notifications and Resource Snapshots to an Encrypted OBS Bucket.
For details about how to add permissions in an agency, see Deleting or Modifying Agencies.
- Custom granting: You can create an agency using IAM to customize authorization for Config. The agency must include either the permissions for sending notifications using an SMN topic or the permissions for writing data into an OBS bucket. To store resource changes and snapshots to an OBS bucket that is encrypted using KMS, you need the required KMS Administrator permissions. For details, see Storing Resource Change Notifications and Resource Snapshots to an Encrypted OBS Bucket. For details about how to create an agency, see Cloud Service Agency.
Figure 7 Granting permissions

- Quick granting: This option will automatically create an agency named rms_tracker_agency to grant the required permissions for the resource recorder to work properly. The agency contains permissions, including the SMN Administrator for sending notifications and the OBS OperateAccess permission for writing data into an OBS bucket. The agency created by quick granting does not contain KMS permissions, so the resource recorder is unable to store resource snapshots and change notifications to an OBS bucket that is encrypted using KMS. If you need to use an encrypted bucket, you can add required KMS Administrator permissions to the agency or use custom authorization. For details, see Storing Resource Change Notifications and Resource Snapshots to an Encrypted OBS Bucket.
- Click Save.
- In the displayed dialog box, click OK.
Modifying the Resource Recorder
You can modify the resource recorder at any time.
- In the navigation pane on the left, choose Resource Recorder.
- Click Modify Resource Recorder.
Figure 8 Modifying the resource recorder

- Modify configurations.
- Click Save.
- In the displayed dialog box, click OK.
Disabling the Resource Recorder
You can disable the resource recorder at any time.
- In the navigation pane on the left, choose Resource Recorder.
- Toggle off the resource recorder.
- In the displayed dialog box, click OK.
Figure 9 Disabling the resource recorder

Cross-Account Authorization
- Granting SMN topic permissions to another account
- Log in to the SMN console using the authorized account.
- Attach related SMN permissions to target accounts based on Configuring Topic Policies in Basic Mode.
If an account is not attached with related SMN permissions, the account cannot receive resource change notifications.
- Granting OBS bucket permissions to another account
- Log in to the OBS console using the authorized account.
- Grant related OBS permissions to target accounts based on Creating a Custom Bucket Policy (JSON View).
The following is an example of a bucket policy. The policy allows the authorized account to store data into a specific object or folder in an OBS bucket. You need to configure the following parameters in a bucket policy:
- ${account_id}: ID of the authorized account
- ${agency_name}: Agency name. If you choose Quick granting, this parameter will be set to rms_tracker_agency.
- ${bucket_name}: The name of an OBS bucket.
- ${folder_name}: The name of a folder in an OBS bucket. If you do not need to specify a folder or object in an OBS bucket, you do not need to configure /${folder_name}.
{ "Statement": [ { "Sid": "org-bucket-policy", "Effect": "Allow", "Principal": { "ID": [ "domain/${account_id}:agency/${agency_name}" ] }, "Action": [ "PutObject" ], "Resource": [ "${bucket_name}/${folder_name}/RMSLogs/*/Snapshot/*", "${bucket_name}/${folder_name}/RMSLogs/*/Notification/*" ] } ] }
Storing Resource Change Notifications and Resource Snapshots to an Encrypted OBS Bucket
- Using an OBS bucket that is encrypted with SSE-OBS
If you need to store resource change notifications and snapshots to an OBS bucket encrypted using SSE-OBS, you only need to select the corresponding OBS bucket and no other operations are required.
- Using an OBS bucket that is encrypted with a default key of SSE-KMS
If you need to store resource change notifications and snapshots to an OBS bucket encrypted using a default key of SSE-KMS, you need to add the KMS Administrator permission to the agency assigned to the resource recorder.
- Using an OBS bucket that is encrypted with a custom key of SSE-KMS
If you need to store resource change notifications and snapshots to an OBS bucket that is encrypted using a custom key of SSE-KMS, you need to add the KMS Administrator permission to the agency assigned to the resource recorder.
If you need to store resource change notifications and snapshots to an OBS bucket that is from another account, and that is encrypted using a custom key of SSE-KMS, you need to add the KMS Administrator permission to the agency assigned to the resource recorder, and set the cross-account permission for the key at the same time. The procedure is as follows:
- Log in to the KMS consolemanagement console and access the DEW console to go to the Key Management Service page using the authorized account.
- In the Custom Keys tab, click the alias of a target key to go to its details page and create a grant on it.
- Grant the account the permissions for using custom keys based on Creating a Grant for a Custom Key.
- Select Account for User or Account and enter an account ID.
- Select Create Data Key, Describe Key, and Decrypt Data Key for Granted Operations.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





