Methods for Improving ECS Security
Scenarios
If ECSs are not protected, they may be attacked by viruses, resulting in data leakage or data loss.
You can use the methods introduced below to protect your ECSs from viruses or attacks.
Protection Types
ECS can be protected externally and internally.
|
Type |
Description |
Protection Method |
|---|---|---|
|
External security |
DDoS attacks and Trojan horses or other viruses are common external security issues. To address these issues, you can choose services such as Host Security Service (HSS) based on your service requirements: |
|
|
Internal security |
Incorrect ports opening and weak passwords may cause internal security issues. Improving the internal security is the key to improving the ECS security. If the internal security is not improved, external security solutions cannot effectively intercept and block various external attacks. |
Enabling HSS
Host Security Service (HSS) is designed to protect server workloads in hybrid clouds and multi-cloud data centers. It integrates server security, container security, and web tamper protection capabilities. HSS protects your system integrity, enhances application security, monitors user operations, and detects intrusions.
HSS is designed to enhance server security through diverse functions, including server management, risk prevention, intrusion detection, security operations, and web tamper protection (WTP). HSS can comprehensively identify and manage information assets on servers, detect server risks in real time, and prevent intrusions. This helps companies build a server security system and reduce threats. For more information about how HSS works, see What Is HSS?
After installing the HSS agent on your ECSs, you will be able to check the ECS security status and risks in a region on the HSS console.
We provide different methods for you to install the HSS agent depending on whether your ECSs are to be created or already exist.
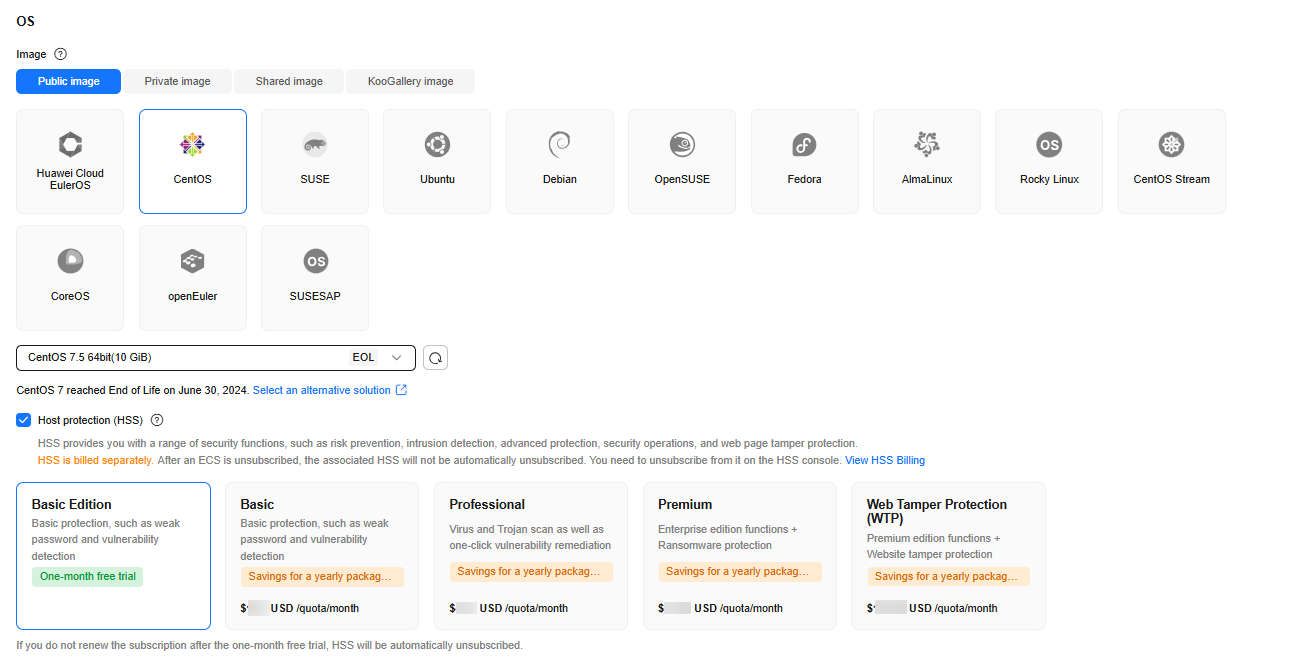
When you use certain public images to create ECSs, you are advised to use HSS to protect your ECSs.
- Basic edition (one-month free trial): After this function is enabled, the HSS basic edition can be used free of charge for 30 days. The HSS basic edition supports detection of OS vulnerabilities, weak passwords, and brute force cracking to improve the overall security for your ECSs.

After the free trial period expires, the HSS basic edition quotas will be automatically released, and HSS will not protect your servers.
If you want to retain or upgrade HSS security capabilities, you are advised to enable the advanced HSS edition. For details, see What Should I Do When the Free Trial of HSS Basic Edition Expires?
This option is selected by default.
- Advanced HSS edition (paid): You can choose from HSS basic, professional, enterprise, premium, and Web Tamper Protection (WTP) editions and you need to pay for it.
After ECSs are purchased, you can switch between different editions on the HSS console after Advanced HSS edition (paid) is enabled. For details about the differences among different editions, see Specifications of Different Editions.
- None: HSS is disabled and servers are not protected.
After you select an HSS edition, the system automatically installs the HSS agent, enables account cracking prevention, and offers host security functions.
If the basic or enterprise edition does not meet your service requirements, you can purchase an HSS quota of your desired edition and change the protection quota edition on the HSS console to obtain advanced protection without reinstalling the agent.
For existing ECSs without host protection enabled, you can enable HSS as needed. The process is as follows.
|
No. |
Step |
Description |
|---|---|---|
|
1 |
HSS provides the basic, professional, enterprise, premium, web tamper protection, and container editions. Each edition supports different functions and features. You need to purchase the corresponding edition based on your protection requirements for servers. For details about the differences between HSS editions, see Features. |
|
|
2 |
The agent is a piece of software provided by HSS. It is installed on cloud servers to interact with the HSS cloud protection center, performing security checks and protection for servers. You can enable HSS only after the HSS agent is installed on your servers. |
|
|
3 |
You need to enable protection for your ECSs. |
|
|
4 |
(Optional) Enabling Alarm Notifications |
By default, security risks detected by HSS are displayed on the management console. You need to log in to the console and view the risks. If you want to know the security risks of servers or containers in a timely manner, you can enable the alarm notification function. After the function is enabled, HSS will send security risks to you by SMS or email. |
|
5 |
(Optional) Common Security Configuration |
To improve ECS security, you can configure the following ECS security protection items based on your service requirements:
|
Configuring Cloud Bastion Host
CBH can monitor the usage of the CBH system, monitor O&M activities of each managed resource, and identify suspicious O&M actions in real time. This protects resources and data from being accessed or damaged by external or internal users. CBH reports alarms to customers, who can then more easily handle or audit O&M issues in a timely, centralized manner.
After logging in to the CBH instance, you need to create users, resources, and access policies successively, and then you can manage assets and perform O&M operations.
- You can log in to your CBH system through a web browser, MSTSC client, or SSH client.
Using a Web Browser to Log In to a CBH System supports system management and resource O&M. This method is recommended for system user admin or administrators to manage the CBH system and assign O&M permissions.
Using an SSH Client to Log In to a CBH System enables you to count on your experiences in using SSH clients to manage O&M on authorized resources. You can use an SSH client to directly log in to the CBH system for resource O&M.
Using the MSTSC Client to Log In to a CBH System enables you to count on your experience in using MSTSC to manage O&M on authorized resources. You can use an MSTSC client to directly log in to the CBH system for resource O&M.
- Before using CBH for system management and O&M, administrators need to create a system user and assign system roles to them.
System users then can access the modules within the permissions.

Only the admin user has the permissions to manage system roles.
- A CBH system allows you to centrally manage cloud resources as well as their accounts and permissions. To manage resources centrally, you need to add resources to your CBH system first.
A host or application resource may have multiple accounts for logins.
CBH allows you to log in to managed resources through managed accounts without having to repeatedly enter the usernames and passwords.
The default account for each managed resource is Empty. If you use the Empty account, enter the account username and password for accessing the host resource.
- To use CBH to maintain resources, configure access control policies, associate system users with resources, and assign resource permissions to system users.
- After obtaining the resource access control permission, you can log in to resources and perform O&M through the system. The entire O&M process is monitored and recorded.
You can select different login methods based on resource types.
- You can log in to many types of managed resources, including databases, within the granted permissions for further O&M in the CBH system.
Administrators can audit logins and operations of other system users, and audit their O&M sessions on the system web page.
Monitoring ECSs
Monitoring is key for ensuring ECS performance, reliability, and availability. Using monitored data, you can determine ECS resource utilization. The cloud platform provides Cloud Eye to help you obtain the running statuses of your ECSs. You can use Cloud Eye to automatically monitor ECSs in real time and manage alarms and notifications to keep track of ECS performance metrics.
- Basic monitoring
Basic monitoring does not require the agent to be installed and automatically reports ECS metrics to Cloud Eye. Basic monitoring for KVM ECSs is performed every 5 minutes.
- OS monitoring
By installing the Agent on an ECS, OS monitoring provides system-wide, active, and fine-grained monitoring. OS monitoring for KVM ECSs is performed every minute.
To enable OS monitoring when purchasing an ECS:
Select Enable Detailed Monitoring when purchasing an ECS. After this option is selected, the cloud platform automatically installs the agent required for OS monitoring.

Currently, detailed monitoring is only available for specific OSs in specific regions. Log in to the console and check if it is available in your target region.
Figure 2 Enabling OS monitoring when purchasing an ECS
To enable OS monitoring for a created ECS:
You need to manually install the agent if Enable Detailed Monitoring is not selected during the creation.
For instructions about how to install and configure the Agent, see Agent Installation and Configuration.
- Process monitoring
Process monitoring provides monitoring of active processes on ECSs and it requires the Agent to be installed on the ECSs to be monitored. Processes are monitored at an interval of 1 minute (for KVM ECSs).
After server monitoring is enabled, you can set ECS alarm rules to customize the monitored objects and notification policies and learn about the ECS running status at any time.
On the ECS console, click  to view monitoring metrics.
to view monitoring metrics.

Enabling Anti-DDoS
To defend against DDoS attacks, Huawei Cloud provides multiple security solutions. You can select an appropriate one based on your service requirements. Anti-DDoS Service on Huawei Cloud provides three sub-services: Cloud Native Anti-DDoS (CNAD) Basic (also known as Anti-DDoS), CNAD Pro, and Advanced Anti-DDoS (AAD).
Anti-DDoS is free while CNAD Pro and AAD are paid services.
For details about CNAD Pro and AAD, see What Is CNAD Basic?
If you choose to purchase an EIP when purchasing an ECS, the console will display a message indicating that you have enabled free-of-charge Anti-DDoS protection.

Anti-DDoS defends ECSs against DDoS attacks and sends alarms immediately when detecting an attack. In addition, Anti-DDoS improves the bandwidth utilization to further safeguard user services.
Anti-DDoS monitors the service traffic from the Internet to public IP addresses and detects attack traffic in real time. It then scrubs attack traffic based on user-configured defense policies without service interruptions. It also generates monitoring reports that provide visibility into the security of network traffic.
Backing Up Data Periodically
Data backup is a process of storing all or part of data in different ways to prevent data loss. The following uses Cloud Backup and Recovery (CBR) as an example. For more backup methods, see Overview.
CBR enables you to back up ECSs and disks with ease. In case of a virus attack, accidental deletion, or software or hardware fault, you can restore data to any point in the past when the data was backed up. CBR protects your services by ensuring the security and consistency of your data.
To enable CBR when purchasing an ECS:
Set CBR when purchasing an ECS. The system will associate the ECS with a cloud backup vault and the selected backup policy to periodically back up the ECS.
- Create new
- Enter the name of the cloud backup vault. The name consists of 1 to 64 characters. Only letters, digits, underscores (_), and hyphens (-) are allowed. For example, vault-f61e. The default naming rule is vault_xxxx.
- Enter the vault capacity, which is required for backing up the ECS. The vault capacity cannot be smaller than that of the ECS to be backed up. The value range is from the ECS's total capacity to 10,485,760, in GiB.
- Select a backup policy from the drop-down list, or log in to the CBR console and configure a desired one.
- Use existing
- Select an existing cloud backup vault from the drop-down list.
- Select a backup policy from the drop-down list, or log in to the CBR console and configure a desired one.
- Not required
Skip this configuration if CBR is not required. If you need to enable CBR after purchasing an ECS, log in to the CBR console, locate the target vault, and associate it with the ECS.

To back up data for a created ECS:
You can use the cloud server backup and cloud disk backup to back up your ECS data.
- Cloud server backup (recommended): Use this backup method if you want to back up the data of all EVS disks (system and data disks) attached to an ECS. This prevents data inconsistency caused by the time difference in creating a backup.
- Cloud disk backup: Use this backup method if you want to back up the data of one or more EVS disks (system or data disk) attached to an ECS. This minimizes backup costs on the basis of data security.
Enhancing the Login Password Strength
Key pair authentication is recommended because it is more secure than password-based authentication.
If you select Password, ensure that the password meets complexity requirements to prevent malicious attacks. For details, see Overview of Password Reset.
The system does not periodically change the ECS password. It is recommended that you change your password regularly for security.
The password must conform to the following rules:
- The password must consist of at least 10 characters.
- Do not use easily guessed passwords (for example, passwords in common rainbow tables or passwords with adjacent keyboard characters). The password must contain at least three of the following character types: uppercase letters, lowercase letters, digits, and special characters.
- Do not include accounts in passwords, such as administrator, test, root, oracle, and mysql.
- Change the password at least every 90 days.
- Do not reuse the latest five passwords.
- Set different passwords for different applications. Do not use the same password for multiple applications.
Improving the Port Security
You can use security groups to protect the network security of your ECSs. A security group controls inbound and outbound traffic for your ECSs. Inbound traffic originates from the outside to the ECS, while outbound traffic originates from the ECS to the outside.
You can configure security group rules to grant access to or from specific ports. You are advised to disable high-risk ports and only enable necessary ports.
For details about common high-risk ports, see Best Practices in Enabling High-Risk Ports. You are advised to change these ports to non-high-risk ports.
Periodically Upgrading the Operating System
After ECSs are created, you need to maintain and periodically upgrade the operating system. The officially released vulnerabilities will be released in Security Notices.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





