Adding and Editing an Alert
Scenarios
This section describes how to add or edit an alert.
Adding an Alert: SecMaster can manage cloud and off-cloud assets. For details about asset management, see Overview. Alerts for cloud assets can be automatically synchronized to SecMaster. For details, see Enabling Log Access. Alerts for off-cloud assets need to be connected to SecMaster manually. For details, see Adding an Alert or Importing Alerts.
Editing an Alert: If the alert status or basic information changes, you can edit alert parameters.
Adding an Alert
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 1 Workspace management page

- In the navigation pane on the left, choose .
Figure 2 Alerts
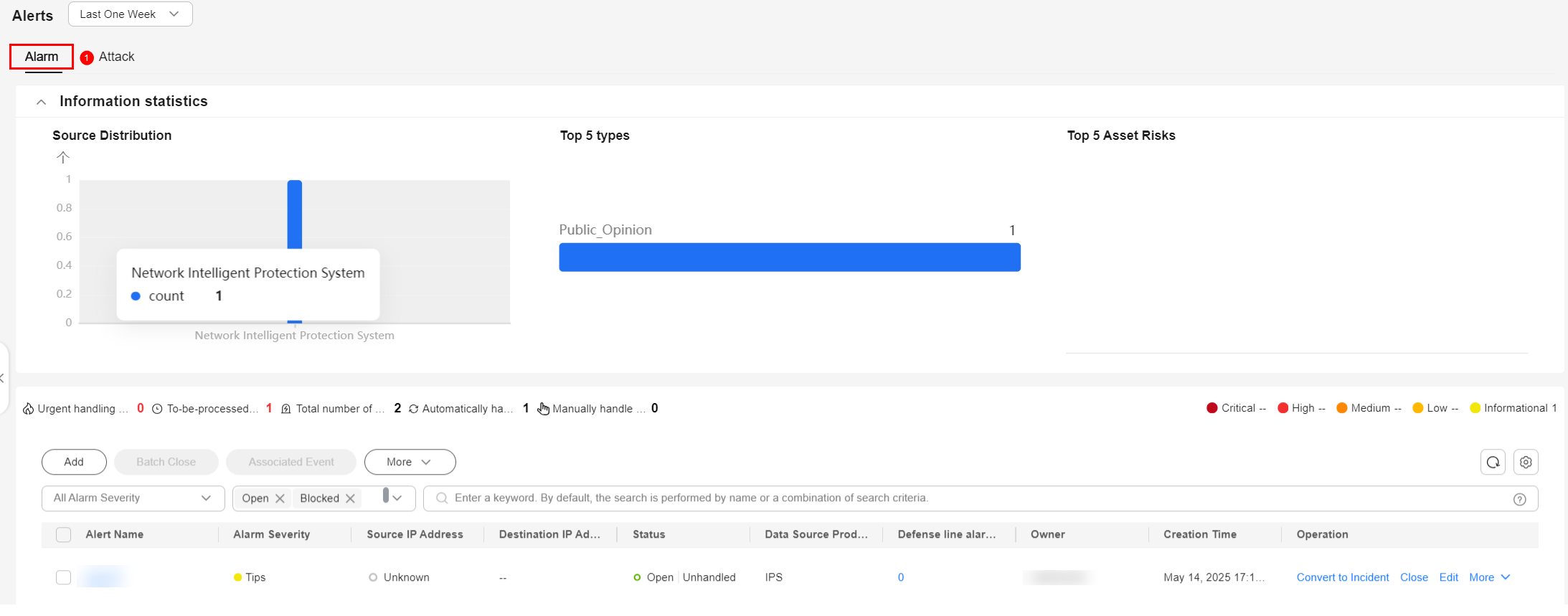
- On the Alerts page, click Add. On the Add page displayed on the right, set parameters as described in the following table.
Table 1 Alert parameters Parameter
Description
Basic Information
Alert Name
User-defined alert name. The value must contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 2,550 characters
Alert Type
Alert type
Alert Severity
Alert severity. The options are Informational, Low, Medium, High, and Critical. For details about alert severity levels, see Alert Severity Levels.
Status
Select an alert status. You can track the handling progress of an alert through its status. The options are Open, Blocked, and Closed.
- Open: For alerts that have not been handled and still require further attention, set their status to Open.
- Blocked: For alerts that cannot be handled temporarily but still need to be addressed later, set their status to Blocked.
- Closed: For alerts that have been handled and require no further action, set their status to Closed.
(Optional) Owner
Select the primary owner to track or handle the alert.
Data Source Product Name
Data source name
Data Source Type
Type of the data source. The options are Cloud Service, Third-party, and Private.
- Cloud Service: Aggregates alerts from cloud service logs that have been connected to SecMaster. For details, see Cloud Service Log Access Supported by SecMaster.
- Third-party: Aggregates alerts reported by third-party products.
- Private: Aggregates alerts reported by your private products.
Timeline
First Occurrence Time
Time when an alert is generated for the first time.
(Optional) Last Occurrence Time
Last time when an alert was generated
(Optional) Planned Closure Time
Time when the alert plan is disabled.
Other
(Optional) Verification Status
Select the alert verification status to indicate whether the alert is a real one and whether it has a negative impact. The options are as follows: Unknown, Positive, and False positive.
- Unknown: It is unclear whether the alert is associated with an attack.
- Positive: It has been confirmed that the alert was triggered by a successful attack.
- False positive: It has been confirmed that the alert was triggered by a failed attack.
- Suspicious: The alert is triggered by a suspicious attack, such as an attack attempt.
- Allow: The alert is triggered by an HSS alarm with no real attack behavior.
- Non-attack information: The alert is triggered by non-attack threats, such as system vulnerability alarms, risky accounts, and weak passwords.
(Optional) stage
Alert phase.
- Preparation: Prepare resources to process alert.
- Detection and analysis: Detect and analyze the cause of an alert.
- Containment, extradition, and recovery: Handle an alert.
- Post Incident Activity: Complete follow-up activities.
(Optional) Debugging data
Whether to enable simulated debugging.
(Optional) Labels
Alert labels.
Description
Alert description. The rules are as follows:
- Only uppercase letters, lowercase letters, digits, and the following special characters are allowed: -_ ()
- A maximum of 10,240 characters are allowed.
- Click OK. You can check details about the alert you add. Path: In the navigation pane on the left, choose .
Editing an Alert
- Log in to the SecMaster console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - Click
 in the upper left corner of the page and choose Security & Compliance > SecMaster.
in the upper left corner of the page and choose Security & Compliance > SecMaster. - In the navigation pane on the left, choose Workspaces > Management. In the workspace list, click the name of the target workspace.
Figure 3 Workspace management page

- In the navigation pane on the left, choose .
Figure 4 Alerts

- In the alert list, locate the row that contains the target alert, and click Edit in the Operation column.
- On the Edit slide-out that is displayed, modify alert parameters. For details about the parameters, see the following table.
Table 2 Alert parameters Parameter
Description
Basic Information
Alert Name
User-defined alert name. The value must contain:
- Only uppercase letters, lowercase letters, digits, and the special characters: -_ ()
- A maximum of 2,550 characters
Alert Type
Alert type
Alert Severity
Alert severity. The options are Informational, Low, Medium, High, and Critical.
For details about alert severity levels, see Alert Severity Levels.
Status
Select an alert status. You can track the handling progress of an alert through its status. The options are Open, Blocked, and Closed.
- Open: For alerts that have not been handled and still require further attention, set their status to Open.
- Blocked: For alerts that cannot be handled temporarily but still need to be addressed later, set their status to Blocked.
- Closed: For alerts that have been handled and require no further action, set their status to Closed.
(Optional) Owner
Select the primary owner to track or handle the alert.
Data Source Product Name
Name of the data source, which cannot be changed
Data Source Type
Type of the data source, which cannot be changed
Timeline
First Occurrence Time
Time when an alert is generated for the first time.
Last Occurrence Time
Last time when an alert was generated
Planned Closure Time
Time when the alert plan is disabled.
Suggestions
Recommended Solution
Description of the recommended alert handling method.
Other
Labels
Alert labels.
Debugging data
Whether to enable simulated debugging. This parameter cannot be modified once configured.
(Optional) Verification Status
Select the alert verification status to indicate whether the alert is a real one and whether it has a negative impact. The options are as follows: Unknown, Positive, and False positive.
- Unknown: It is unclear whether the alert is associated with an attack.
- Positive: It has been confirmed that the alert was triggered by a successful attack.
- False positive: It has been confirmed that the alert was triggered by a failed attack.
- Suspicious: The alert is triggered by a suspicious attack, such as an attack attempt.
- Allow: The alert is triggered by an HSS alarm with no real attack behavior.
- Non-attack information: The alert is triggered by non-attack threats, such as system vulnerability alarms, risky accounts, and weak passwords.
stage
Alert stage.
- Preparation: Prepare resources to process alert.
- Detection and analysis: Detect and analyze the cause of an alert.
- Containment, extradition, and recovery: Handle an alert.
- Post Incident Activity: Complete follow-up activities.
Description
Alert description. The rules are as follows:
- Only uppercase letters, lowercase letters, digits, and the following special characters are allowed: -_ ()
- A maximum of 10,240 characters are allowed.
- Click OK. You can check details about the alert. Path: In the navigation pane on the left, choose .
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.






