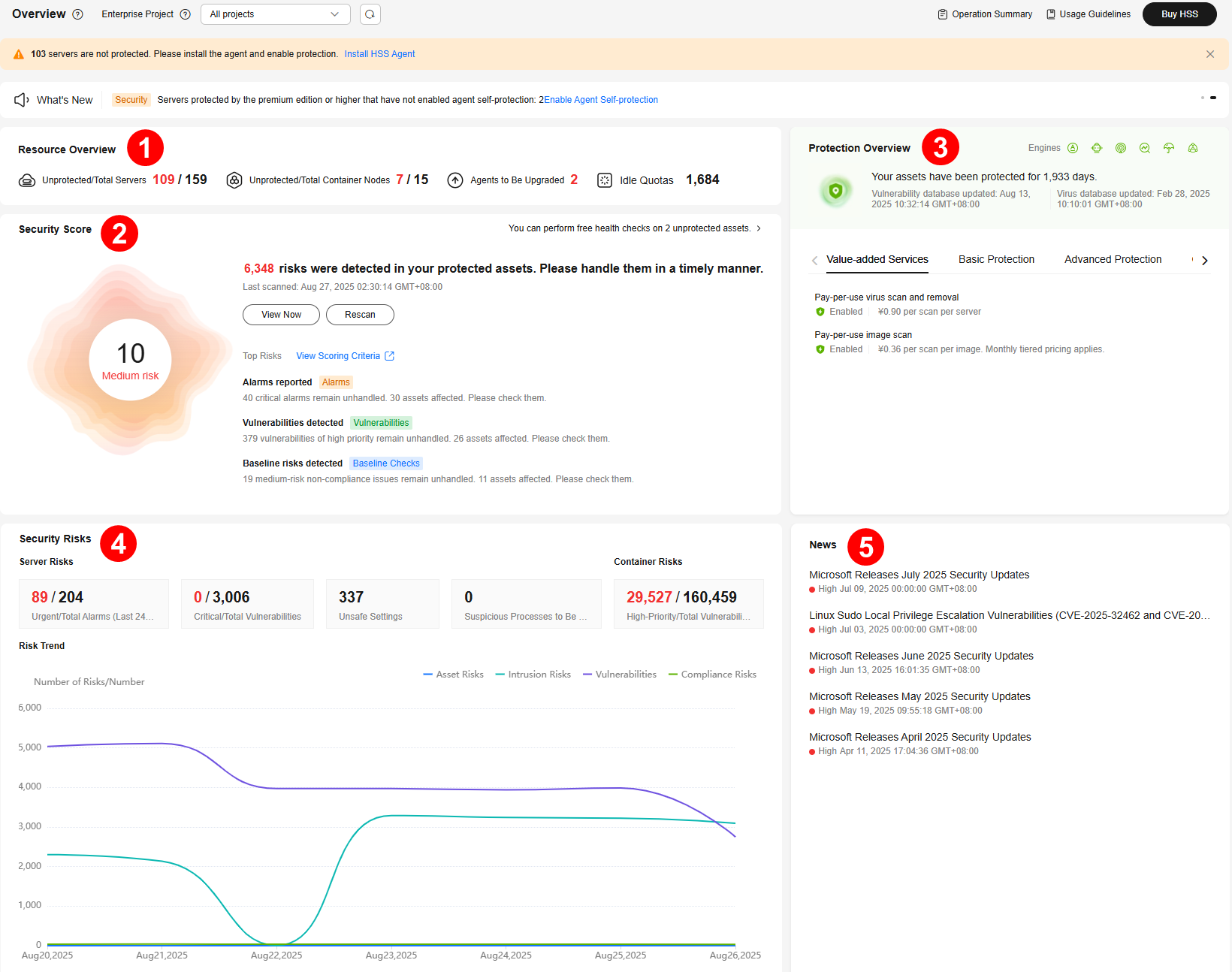
Checking the Dashboard
On the HSS dashboard, you can check the security score, risks, and protection overview of all your assets in real time, including servers and containers.
Checking the Dashboard
- Log in to the HSS console.Log in to the management console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane, choose Overview.
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- View asset security information. For details, see Table 1.
Table 1 Overview components Component
Description
Resource Overview
(Component 1 in Overview)
Check the percentage of unprotected servers or containers, idle quotas, and agents to be upgraded.
- Click the number of unprotected resources to go to the server or container management page and view the unprotected resource list.
- Click the number of agents to be upgraded to go to the agent list and upgrade agents.
- Click the number of idle quotas to go to the protection quota list.
NOTE:HSS will be continuously upgraded to provide new features and fix bugs. To enjoy better HSS features, upgrade the agent to the latest version in a timely manner. For details, see Upgrading the agent.
Secure score
(Component 2 in Overview)
The security score is in the range 0 to 100. The default score for risk-free assets is 100. Points are deducted based on baseline risks, vulnerability risks, intrusion risks, and asset risks. A low score indicates high security risks in assets. To ensure the security of your assets, you are advised to handle security risks in a timely manner and improve the security score.
- In the Security Score area, click View Now.
- In the Handle Now dialog box, view the deduction items and click
 to expand the details.
to expand the details. - Click Handle on the right of deduction items to go to the corresponding risk list. You can rectify the fault based on the risk details and handling suggestions.
For details about the score deduction items and how to increase the score, see Security Scores Criteria and Methods for Improving Scores.
- After the risk is fixed, click Rescan to update the score.
Protection Overview
(Component 3 in Overview)
Asset protection overview.
- Assets: Total number of assets in the current region.
You can click the total number of assets to go to the Assets page to view asset distribution and protection status.
- Unprotected/Total Servers: Number of unprotected servers and the total number of servers.
You can click the number of unprotected servers to go to the Servers & Quota page to view servers and enable protection. For details, see Enabling Protection.
- Unprotected/Total Containers: Number of unprotected containers and the total number of containers.
You can click the number of unprotected containers to go to the Containers & Quota page to view containers and enable protection. For details, see Enabling Protection.
- Vulnerability update time: The latest update time of the vulnerability.
- Security feature status: The number of servers protected by each feature and the number of items detected by each feature.
You can click View Details to go to corresponding feature page.
Security Risks
(Component 4 in Overview)
Security risks detected by HSS in your assets.
- Server Risks
- Urgent/Total Alarms (Last 24 Hours): Number of alarms that need to be handled immediately and the total number of alarms.
You can click the number of urgent alarms to go to the Alarms page and handle alarms. For details, see Handling Server Alarms.
- Critical/Total Vulnerabilities: Number of critical vulnerabilities and the total number of vulnerabilities.
You can click the number of critical vulnerabilities to go to the Vulnerabilities page and handle vulnerabilities. For details, see Handling Vulnerabilities.
- Unsafe Settings: Number of baseline risks to be handled.
You can click the number to go to the Baseline Checks page and fix baseline risks. For details, see Viewing and Processing Baseline Check Results.
- Suspicious Processes to Be Handled: Total number of suspicious processes to be handled.
You can click the number of suspicious processes to be handled to go to the Application Process Control page and handle suspicious processes. For details, see Checking and Handling Suspicious Processes.
- Urgent/Total Alarms (Last 24 Hours): Number of alarms that need to be handled immediately and the total number of alarms.
- Container Risks
High-Priority/Total Vulnerabilities: Number of high-risk vulnerabilities and the total number of vulnerabilities.
You can click the number of high-priority vulnerabilities to go to the Image Vulnerabilities tab and check vulnerability fixing suggestions.
- Risk Trend
Trends of asset risks, intrusion risks, vulnerability risks, and compliance risks in the last seven days.
News
(Component 5 in Overview)
Latest vulnerability information.
Best Practices
HSS best practices. Click a title to view details.
FAQ
HSS best FAQ. Click a title to view details.
Related Services
Security services related to HSS. Click a service name to go to its console.
Security Scores Criteria and Methods for Improving Scores
The security score for risk-free assets is 100. A low score indicates high security risks in assets. HSS calculates your security score based on detected security items (vulnerabilities, compliance, intrusions, assets, and images) and unprotected assets. Scores are deducted every time a risk is detected in a category until all scores in that category are deducted. The full score of each category is as follows:
- No vulnerabilities detected: 20. For details about the score deduction criteria and improvement methods, see Table 2.
- No compliance risks detected: 20. For details about the score deduction criteria and improvement methods, see Table 3.
- No intrusion risks detected: 30. For details about the score deduction criteria and improvement methods, see Table 4.
- No asset risks detected: 10. For details about the score deduction criteria and improvement methods, see Table 5.
- No image risks detected: 10. For details about the score deduction criteria and improvement methods, see Table 6.
- No unprotected assets detected: 10. For details about the score deduction criteria and improvement methods, see Table 7.
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Unhandled vulnerabilities |
Unhandled critical vulnerabilities |
All |
10 |
√ |
Fix vulnerabilities based on the suggestions provided, scan for vulnerabilities again, and update the score.
|
|
Unhandled high-risk vulnerabilities |
All |
3 |
√ |
||
|
Unhandled medium-risk vulnerabilities |
All |
1 |
√ |
||
|
Unhandled low-risk vulnerabilities |
All |
0.1 |
√ |
||
|
No vulnerability scan |
No vulnerability scans were performed in the past month. |
All |
15 |
× |
|
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Unhandled non-compliance items |
Unhandled high-risk non-compliance items |
All |
10 |
√ |
Rectify non-compliance items, perform a baseline check again, and update the score.
|
|
Unhandled medium-risk non-compliance items |
All |
3 |
√ |
||
|
Unhandled low-risk non-compliance items |
All |
1 |
√ |
||
|
Weak passwords |
Weak passwords |
All |
10 |
√ |
Use strong passwords. For details, see How Do I Set a Secure Password? |
|
Weak password check not enabled |
Weak password check policy not enabled |
All |
10 |
× |
Enable the Weak Password Detection policy to check for weak passwords on servers. For details, see Policy Management Overview. |
|
Baseline check not performed |
No baseline checks were performed in the past month. |
All |
10 |
× |
|
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Unhandled alarms |
Critical alarms not fixed |
All |
10 |
√ |
Handle alarms based on the suggestions provided. After alarms are handled, HSS will automatically update the score. For details, see Handling Server Alarms and Handling Container Alarms. |
|
Unhandled high-risk alarms |
All |
3 |
√ |
||
|
Unhandled medium-risk alarms |
All |
1 |
√ |
||
|
Unhandled low-risk alarms |
All |
0.1 |
√ |
||
|
Protection not enabled |
No security policies enabled |
All |
30 |
× |
In the HSS professional, enterprise, premium, WTP, and container editions, you need to enable protection policies. For details, see Policy Management Overview. The intrusion detection policies that need to be enabled for each edition are as follows:
|
|
Login security policy not enabled |
All |
10 |
× |
In HSS professional, enterprise, premium, WTP, and container editions, you need to enable the Login Security Check policy for servers. For details, see Policy Management Overview. |
|
|
Ransomware prevention policy not enabled |
Premium edition |
15 |
× |
The HSS premium, WTP, and container editions support ransomware prevention. In these editions, you need to enable the ransomware prevention policy and the backup policy. (10 points will be deducted if backup is not enabled.) For details, see Enabling Ransomware Prevention. |
|
|
WTP policy is not enabled |
WTP edition |
20 |
× |
In the HSS WTP edition, you need to enable WTP policy for servers. For details, see Enabling Protection. |
|
|
Container runtime detection policy not enabled |
Container edition |
20 |
× |
In the HSS container edition, you need to enable container escape, container process whitelist, container file monitoring, and container information collection policies and apply them to servers. For details, see Overview. |
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Open ports |
Open TCP/UDP high-risk ports |
All |
1 |
√ |
You are advised to disable unnecessary ports. To enable a port, choose , click Open Ports, and ignore the port. |
|
Asset discovery not enabled |
Asset discovery policy not enabled |
All |
5 |
× |
|
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Unsafe images |
High-risk images |
Container edition |
3 |
√ |
Re-create an image, scan the image, and update the score. |
|
Medium-risk images |
Container edition |
1 |
√ |
||
|
Medium-risk images |
Container edition |
0.1 |
√ |
||
|
Image security scan not performed |
No image security scans were performed in the past month. |
Container edition |
5 |
× |
In the HSS container edition, you are advised to perform image security scans. For details, see: |
|
Category |
Score Deduction Item |
Affected HSS Edition |
Points Deducted |
Multiply Deducted Score by Risk Quantity |
Methods for Improving Scores |
|---|---|---|---|---|---|
|
Server protection not enabled |
Unprotected servers |
All |
0.1–1 |
√ |
The points deducted for an unprotected server vary depending on its asset importance:
You are advised to enable protection for your server as soon as possible. For details, see Enabling Protection. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.