更新时间:2025-09-15 GMT+08:00
基于Cookie字段的配置
攻击案例
竞争对手控制数台主机,与大多普通访客一样,共用同一IP,或通过代理频繁更换源IP,持续向网站“www.example.com”发起HTTP Post请求,网站并无较大的负载能力,网站连接数、带宽等资源均被该攻击者大量占用,正常用户无法访问网站,最终竞争力急剧下降。
防护措施
- 根据服务访问请求统计,判断网站是否有大量同一IP请求发生,如果有则说明网站很有可能遭受了CC攻击。
- 登录EdgeSec服务控制台。
- 在左侧导航栏选择,进入“安全防护”的“域名接入”页面。
- 在目标域名所在行的“防护策略”栏中,单击“已开启N项防护”,进入“防护策略”页面,确认“CC攻击防护”的“状态”为“开启”
 ,单击“自定义CC攻击防护规则”,进入CC防护规则配置页面。
,单击“自定义CC攻击防护规则”,进入CC防护规则配置页面。 - 在“CC攻击防护”规则配置页面左上角,单击“添加规则”,选择“限速模式”为“Cookie”,并输入字段名。

“防护动作”选择“阻断”,设置“阻断时长”,能够在攻击被拦截后,攻击者需额外等待一段时间, 该设置能进一步对攻击者行为进行限制,建议对安全要求非常高的用户设置。
图1 用户限速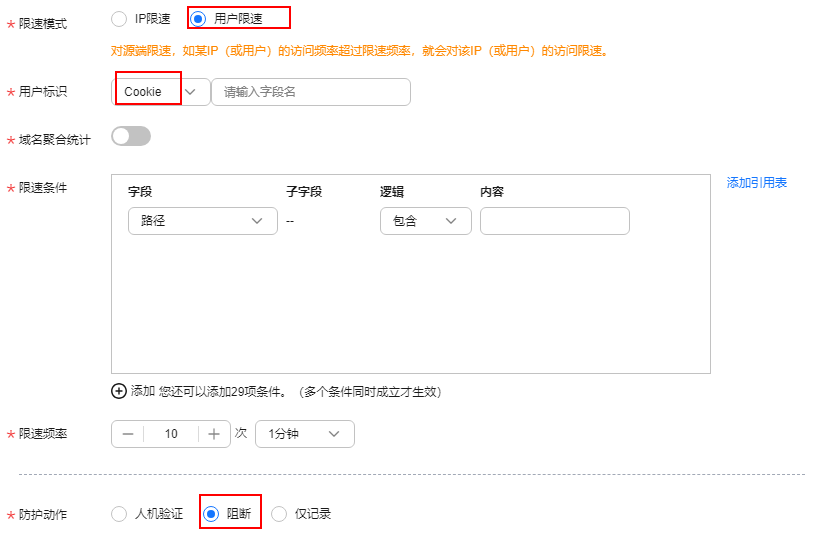
- 限速模式:选择“Cookie”,根据Cookie键值区分单个Web访问者。
- 限速频率:单个Web访问者在限速周期内可以正常访问的次数,如果超过该访问次数,边缘安全将暂停该Web访问者的访问。
- 防护动作:选择“阻断”模式。在攻击被拦截后,攻击者需额外等待一段时间才能访问正常的网页, 该设置能进一步对攻击者行为进行限制,建议对安全要求非常高的用户设置。
- 人机验证:表示超过“限速频率”后弹出验证码,进行人机验证,完成验证后,请求将不受访问限制。人机验证目前支持英文。
- 阻断:表示超过“限速频率”将直接阻断。
- 仅记录:表示超过“限速频率”将只记录不阻断。
- 限流:表示超过“限速频率”将限制流量速率。
- 阻断页面:可选择“默认设置”或者“自定义”。
父主题: CC攻击防御






