Overview
ROMA Connect provides strict permissions management for user resources. In one instance, IAM users without the Tenant Administrator permission can view and manage only the integration applications and resources created by themselves. With integration application authorization, IAM users can share applications and resources with other IAM users under the same account.
Constraints
- This function allows permissions sharing among users under the same account. Operations permissions on application objects are still managed through IAM.
- Modifying or deleting the authorization of an integration application will affect other IAM users' check and use of resources of the integration application.
- An administrator (account with the Tenant Administrator permission) can authorize integration applications created by all its IAM users, but a common user without the permission can authorize only the integration applications they create.
Configuring Integration Application Authorization
- Log in to the ROMA Connect console. In the navigation pane on the left, choose Resource. On the displayed page, click the instance to access its console.
- In the navigation pane on the left, choose Integration Applications. On the page displayed, locate the target integration application and click Application Authorization Management.
- In the dialog box displayed, grant permissions to IAM users.
- In the Users area, select the IAM users to be authorized.
To filter users, select the username in the user filter area and enter a keyword to search for the users to be authorized.
- In the Selected area, configure management permissions of the integration application for selected IAM users.
You can grant permissions to each user separately or click  on the right of Permission to grant permissions to all selected users.
on the right of Permission to grant permissions to all selected users.
Figure 1 Configuring application permissions
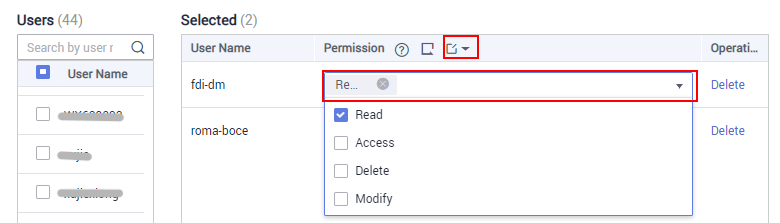
Table 1 Application permissions
|
Permission |
FDI |
APIC |
MQS |
LINK |
|
read |
View data sources of applications. |
View, debug, and export APIs of applications. |
View and export topics of applications. |
View and export devices, products, and rules of applications, as well as debug devices. |
|
modify |
Create and edit data sources of applications. |
Create, edit, release, take APIs offline, and import APIs of applications. |
Create and edit topics of applications. |
Create, edit, and import devices, products, and rules of applications, as well as reset device and product passwords. |
|
delete |
Delete data sources of applications. |
Delete APIs of applications. |
Delete topics of applications. |
Delete devices, products, and rules of applications, product properties, device topics, as well as rule data sources and destinations. |
|
access |
N/A |
Configure authorization, access control, request throttling, and signature key binding for APIs of applications. |
Configure permissions for topics of applications. |
Deliver commands to and forcibly take offline devices, as well as configure plug-ins for devices that use the OPC UA or Modbus protocol. |
|
admin |
Application administrator permissions. |
- Click OK.
In the integration application list, click  of an integration application to view its authorized IAM users and the permissions assigned.
of an integration application to view its authorized IAM users and the permissions assigned.
- Log in to a ROMA Connect console as the IAM user authorized in 3 and access the corresponding instance to check whether the authorization is successful.









