Remediation Configuration Examples
This section provides examples of configuring remediation actions using RFS private templates and FunctionGraph functions. The remediation configuration process is as follows:
- Configuring Remediation Using RFS Private Templates
- Configuring Remediation Using a FunctionGraph Function
Configuring Remediation Using RFS Private Templates
- Add a rule based on the built-in policy "Cloud Trace Service (CTS)-Trackers (cts-tracker-exists)".
The compliance evaluation result based on this rule is non-compliant because the CTS tracker of the account is disabled.
Figure 1 CTS tracker disabled Figure 2 Evaluation result
Figure 2 Evaluation result
- Create a private RFS template and specify the template content.
The template enables the CTS tracker.
{ "resource": { "huaweicloud_cts_tracker": { "tracker": { "bucket_name": "${var.bucket_name}", "file_prefix": "${var.file_prefix}", "lts_enabled": "true" } } }, "variable": { "bucket_name": { "description": "Specifies the OBS bucket to which traces will be transferred.", "type": "string", "default": "" }, "file_prefix": { "description": "Specifies the file name prefix to mark trace files that need to be stored in an OBS bucket. The value contains 0 to 64 characters. Only letters, numbers, hyphens (-), underscores (_), and periods (.) are allowed.", "type": "string", "default": "" } }, "terraform": { "required_providers": { "huaweicloud": { "source": "huawei.com/provider/huaweicloud", "version": "1.58.0" } } } } - Configure remediation for the rule.
The following shows how to set required parameters:
- Select Automatic for Method.
- Select the created RFS private template. An IAM agency is required for the automatic remediation. In this example, the RFS private template will create a CTS tracker, the authorized cloud service of the agency is RFS, and the agency needs the permissions to create a CTS tracker (for example, CTS FullAccess). For details about how to create an agency, see Delegating Another Service for Resource Management.
- Resource ID Parameter: Config will assign the ID of the non-compliant resource to this parameter. In this example, file_prefix will be assigned the account ID, which will be passed to the RFS service for creating a resource stack and executing RF statements.
- Parameter: Config passes these static parameters to the RFS private template, and RFS will use them to create a resource stack and execute RF statements.
Figure 3 Configuring remediation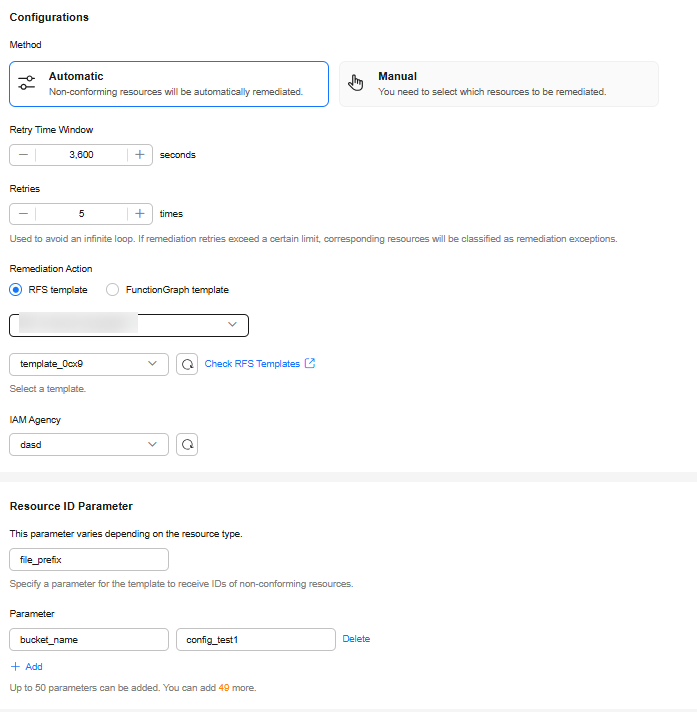
- Trigger the rule.
If the evaluation result remains non-compliant, Config automatically remediates the configuration by invoking the RFS private template to enable the CTS tracker for the current account.
The following figure shows that the CTS tracker of the current account is enabled. The non-compliant resource configuration issue. The non-compliant resource configuration is remediated.
Figure 4 CTS tracker enabled
Configuring Remediation Using a FunctionGraph Function
- Add a rule based on the built-in policy "Virtual Private Cloud (VPC)-VPCs (vpc-flow-logs-enabled)".
The compliance evaluation result of this rule is non-compliant because there are VPCs for which flow logs are disabled.
Figure 5 Evaluation result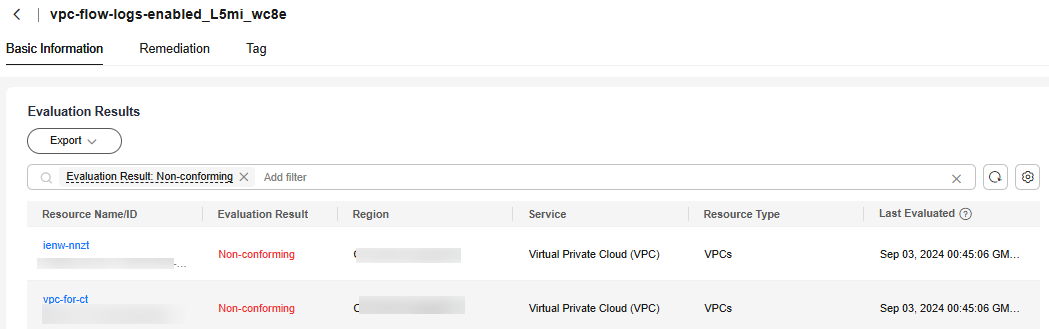
- Create a FunctionGraph function and enter the following function code.
This function enables flow logs for the specified VPC resources.
To use the following example function, add the dependency package huaweicloudsdkvpc. This dependency package is not available in all regions. If there is no such dependency package, import it. For details, see Configuring Dependency Packages.
# -*- coding:utf-8 -*- import time import requests import random, string import http.client from huaweicloudsdkcore.exceptions.exceptions import ConnectionException from huaweicloudsdkcore.exceptions.exceptions import RequestTimeoutException from huaweicloudsdkcore.exceptions.exceptions import ServiceResponseException from huaweicloudsdkvpc.v2.region.vpc_region import VpcRegion from huaweicloudsdkvpc.v2.vpc_client import VpcClient from huaweicloudsdkvpc.v2.model import CreateFlowLogReq from huaweicloudsdkvpc.v2.model import CreateFlowLogReqBody from huaweicloudsdkvpc.v2.model import CreateFlowLogRequest from huaweicloudsdkcore.auth.credentials import BasicCredentials requests.packages.urllib3.disable_warnings() def get_random_string(length=6): letters_and_digits = string.ascii_letters + string.digits return ''.join(random.choice(letters_and_digits) for _ in range(length)) def createFlowLog(context, project_id, request): auth = BasicCredentials(ak=context.getAccessKey(), sk=context.getSecretKey())\ .with_project_id(project_id) client = VpcClient.new_builder() \ .with_credentials(credentials=auth) \ .with_region(region=VpcRegion.value_of(region_id="cn-north-4")) \ .build() try: response = client.create_flow_log(request) return 200 except ConnectionException as e: print("A connect timeout exception occurs while the vpc performs some operations, exception: ", e.error_msg) return e.status_code except RequestTimeoutException as e: print("A request timeout exception occurs while the vpc performs some operations, exception: ", e.error_msg) return e.status_code except ServiceResponseException as e: print("There is service error, exception: ", e.status_code, e.error_msg) return e.status_code def handler(event, context): project_id = event.get("project_id") request_body = CreateFlowLogRequest(CreateFlowLogReqBody( CreateFlowLogReq( name="auto" + get_random_string(4), description="to remediate vpc", resource_type="vpc", resource_id=event.get("noncompliant_resource_id", {}), traffic_type="all", log_group_id=event.get("log_group_id", {}), log_topic_id=event.get("log_topic_id", {}), index_enabled=False ) )) for retry in range(5): status_code = createFlowLog(context, project_id, request_body) if status_code == http.client.TOO_MANY_REQUESTS: time.sleep(1) else: break - Configure remediation for the rule.
The following shows how to set required parameters:
- Select Automatic for Method.
- Select the created FunctionGraph function for the remediation action.
- Resource ID Parameter: Config will assign the ID of the non-compliant resource to this parameter. You need to use the noncompliant_resource_id variable to pass the ID of the non-compliant resource and use the resource_id=event.get("noncompliant_resource_id", {}) statement in the FunctionGraph function to obtain the ID. The ID of each non-compliant resource will be passed.
- Parameter: Config passes these static parameters to the FunctionGraph function for remediation. For example, to store the flow logs created for non-compliant VPC resources in a log group, you can add log_group_id to specify the log group ID and run log_group_id=event.get("log_group_id", {}) in the FunctionGraph function to obtain the log group ID.
For this example, the following example parameters can be added:
- project_id: project ID. For details about how to obtain the ID, see Obtaining Account, IAM User, and Project Information.
- log_group_id: log group ID. For details about how to obtain the ID, see Managing Log Groups.
- log_topic_id: log stream ID. For details about how to obtain the ID, see Managing Log Streams.
Figure 6 Configuring remediation
- Trigger the rule.
Config automatically corrects the configuration if the evaluation result is non-compliant. It calls the FunctionGraph function to create a flow log for each non-compliant VPC resource.
The following figure shows the remediation result. Flow logs have been created for all non-compliant VPC resources.
Figure 7 Flow logs created for the VPC resources
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





