Deleting a Pay-per-Use GaussDB Instance
Scenarios
On the Instances page, you can manually delete DB instances that fail to be created or unnecessary instances after service changes.
Billing
If a pay-per-use instance is deleted, its automated backups will also be deleted and you will no longer be billed for them. Manual backups, however, will be retained and continue to incur costs.
Precautions
- Instance deletion cannot be undone. Exercise caution when performing this operation. Back up your data first if you want to keep it after deleting an instance.
- Instances cannot be deleted while an operation is being performed on them. They can only be deleted once the operations are complete.
- You can restore a DB instance that was deleted up to 7 days ago from the recycle bin. For details, see Modifying the Recycle Bin Policy for a GaussDB Instance.
- If you delete a stopped instance, it cannot be rebuilt from the recycle bin. Exercise caution when performing this operation. If you might want to rebuild it later, start the instance first and make sure it is running properly before deleting it.
- Instances in the recycle bin will not incur charges.
- When pay-per-use instances are deleted, manual backups are retained. (To delete a yearly/monthly instance, you need to unsubscribe the order first. For details, see Unsubscribing a Yearly/Monthly GaussDB Instance.)
- After an instance is deleted, the system retains the most recent automated full backup of the instance from one day ago (or, if none exists, the latest automated full backup) and then creates a new full backup. You can restore the instance later by using any of the backups.
Procedure
- Log in to the management console.
- Click
 in the upper left corner and select a region and project.
in the upper left corner and select a region and project. - Click
 in the upper left corner of the page and choose .
in the upper left corner of the page and choose . - On the Instances page, locate the instance you want to delete and click More > Delete in the Operation column.
- In the displayed dialog box, click OK. Refresh the Instances page later to check that the deletion is successful.
Figure 1 Deleting an instance
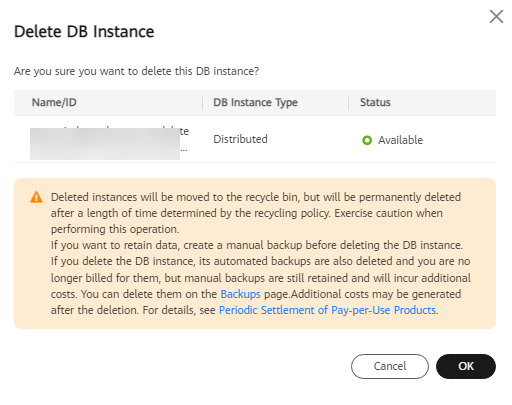
- If you have enabled the operation protection function, click Start Verification in the Delete DB Instance dialog box. On the displayed page, click Send Code, enter the obtained verification code, and click Verify to close the page.
Two-factor authentication improves the security of your account. For details about how to view and enable high-risk operation protection, see Identity and Access Management User Guide.
FAQ
Question:
Why is my instance still billed after I delete it?
Answer:
- Pay-per-use instances are postpaid resources. You are not billed immediately after a bill is generated. For example, if you delete a GaussDB instance (which is billed on an hourly basis) at 08:30, the expenditures for that hour from 08:00 to 09:00 are usually not billed until about 10:00.
- The instance has manual backups. After an instance is deleted, its manual backups are retained by default and will be billed based on the backup space pricing. If you no longer need the manual backups and want to stop being billed for them, simply delete them.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





