Filtering Requests from Specific Regions
You can prevent users in certain geographical locations from accessing your content.
Scenarios
You can use geo-blocking when users in specific geographic areas need to be restricted from accessing your businesses due to local laws and regulations or business attributes. CDN identifies client IP addresses to determine the user access source. The working principle is as follows:
- Assume that your domain name www.example.com does not serve users in region W, and you have configured a blacklist for region W on the CDN console.
- CDN receives a request to access www.example.com from an IP address in region W. The DNS resolves the request to a CDN PoP in region W.
- The PoP detects that this IP address is not allowed to download resources under your domain name.
- CDN returns HTTP status code 403 (Forbidden) to the user.
Precautions
- You can configure up to 20 rules.
- If a blacklist and whitelist are configured for the same resource, when a user in both lists accesses the resource, the blacklist takes effect and status code 403 is returned.
- If a blacklist and whitelist are configured for the same resource, when a user outside both lists accesses the resource, status code 403 is returned.
- When a client request hits the blacklist and is blocked, PoP resources are consumed, generating a small amount of traffic or bandwidth fees. If the service type of the domain name is whole site acceleration, the client request is also charged for the request fees.
- Huawei Cloud periodically updates the IP address library. The locations of IP addresses that are not in the library cannot be identified. CDN allows requests from such IP addresses and returns resources to the users.
- If your domain name is connected to EdgeSec and a geo-blocking rule is configured in both services, the rule in CDN is executed first.
Procedure
-
Log in to the CDN console.
- In the navigation pane, choose .
- In the domain list, click the target domain name or click Configure in the Operation column.
- Click the Access Control tab.
- In the Geo-blocking area, click Add.
Figure 1 Adding a geo-blocking rule
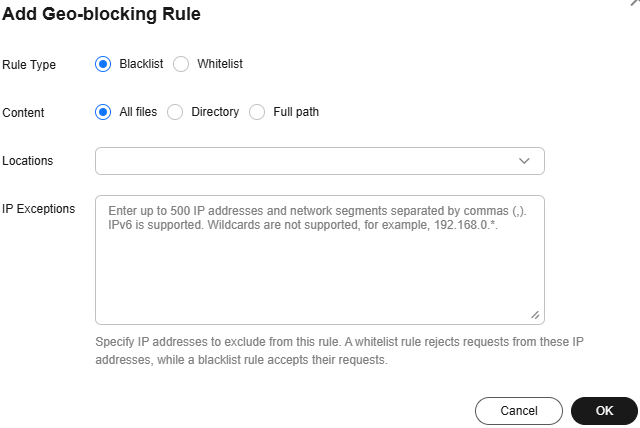
Table 1 Parameter details Parameter
Description
Example
Rule Type
Blacklist: Users in regions specified in the blacklist cannot access resources and status code 403 is returned.
Whitelist: Only users in regions specified in the whitelist can access resources. Status code 403 is returned for other users.
Blacklist
Content
All files: The rule takes effect for all files.
Directory: The rule takes effect for resources in the specified directory.
Full path: The rule takes effect for resources corresponding to the paths.
All files
Rule
Directory:- Start with a slash (/) and separate directories by commas (,).
- Enter up to 100 directories.
- Do not enter wildcard characters (*).
Full path:- Start with a slash (/) or wildcard (*). Wildcards (*) can be used for match.
- Do not enter two consecutive wildcard characters (*).
- Enter up to two wildcard characters (*).
- Enter up to 100 paths and separate them by comma (,).
NOTE:
- Each whitelist or blacklist rule must be unique.
- You can configure only one rule for all files.
/test/folder01,/test/folder02
Locations
User locations to which the rule applies. That is, users in the specified locations cannot access the resources (blacklist) or only they can access the resources (whitelist). For details about the supported regions, see Table 2.
Chinese mainland
IP Exceptions
IP addresses excluded from this rule. For example, if you have configured a blacklist whose Content is All files and added an exception IP address 0.0.0.0, this IP address is not restricted by this blacklist rule and requests from this IP address are accepted.
- IP addresses and CIDR blocks in the IP address/Subnet mask format are supported.
- Enter up to 500 IP addresses and CIDR blocks separated by commas (,).
- Wildcards are not supported, for example, 192.168.0.*.
- IPv6 is supported.
0.0.0.0
- Configure related information and click OK.
Supported Regions
|
Geographic Region |
User Location |
|---|---|
|
Asia |
Afghanistan, Armenia, Azerbaijan, Bahrain, Bangladesh, Bhutan, Cambodia, Chinese mainland, Georgia, Hong Kong (China), India, Indonesia, Iraq, Israel, Japan, Jordan, Kazakhstan, Kuwait, Kyrgyzstan, Lao People's Democratic Republic, Lebanon, Macao (China), Malaysia, Maldives, Mongolia, Myanmar, Nepal, Oman, Pakistan, Palestine, Philippines, Qatar, Republic of Korea, Saudi Arabia, Singapore, Sri Lanka, Taiwan (China), Tajikistan, Thailand, Timor-Leste, Türkiye, Turkmenistan, United Arab Emirates, Uzbekistan, Vietnam, and Yemen |
|
Europe |
Albania, Andorra, Austria, Belarus, Belgium, Bosnia and Herzegovina, Bulgaria, Croatia, Cyprus, Czech Republic, Denmark, Estonia, Faroe Islands, Finland, France, Greece, Hungary, Iceland, Ireland, Italy, Latvia, Lithuania, Luxembourg, Malta, Monaco, Montenegro, Netherlands, North Macedonia, Norway, Poland, Portugal, Republic of Moldova, Romania, San Marino, Serbia, Slovakia, Slovenia, Spain, Sweden, Switzerland, and United Kingdom of Great Britain and Northern Ireland |
|
South Africa |
Algeria, Angola, Benin, Botswana, Burkina Faso, Burundi, Cameroon, Central African Republic, Chad, Comoros, Côte d'Ivoire, Democratic Republic of the Congo, Djibouti, Egypt, Equatorial Guinea, Eritrea, Eswatini, Ethiopia, Gabon, Gambia, Ghana, Guinea, Guinea-Bissau, Kenya, Lesotho, Liberia, Libya, Madagascar, Malawi, Mali, Mauritania, Mauritius, Morocco, Mozambique, Namibia, Niger, Nigeria, Republic of the Congo, Rwanda, Sao Tome and Principe, Senegal, Seychelles, Sierra Leone, Somalia, South Africa, South Sudan, Togo, Tunisia, Uganda, United Republic of Tanzania, Zambia, and Zimbabwe |
|
North America |
Antigua and Barbuda, Bahamas, Barbados, Belize, Canada, Costa Rica, Dominica, Dominican Republic, El Salvador, Grenada, Haiti, Honduras, Jamaica, Mexico, Nicaragua, Panama, Saint Kitts and Nevis, Saint Lucia, Saint Vincent and the Grenadines, Trinidad and Tobago, and United States of America |
|
Oceania |
Australia, Cook Islands, Fiji, Micronesia, Kiribati, Marshall Islands, Nauru, Niue, New Zealand, Papua New Guinea, Solomon Islands, Tokelau, Tonga, Tuvalu, Vanuatu, and Samoa |
|
South America |
Argentina, Bolivia, Brazil, Chile, Colombia, Ecuador, Guyana, Paraguay, Peru, Suriname, and Venezuela |
Examples
Example 1: Assume that you have configured the following rules for the domain name www.example.com.

Result:
- The blacklist takes precedence over the whitelist. Therefore, the blacklist takes effect. When a user in the Chinese mainland accesses a resource in the /test folder (for example, www.example.com/test/abc.jpg), status code 403 is returned.
- When a user in Hong Kong (China) accesses the same resource, neither the blacklist nor the whitelist is hit. In this case, the access is denied and status code 403 is returned.
Example 2: Assume that you have configured the following rules for the domain name www.example.com.

Result:
- When a user in Hong Kong (China) accesses a resource in the /test folder (for example, www.example.com/test/abc.jpg), the blacklist is hit and status code 403 is returned.
- When a user in the Chinese mainland accesses the same resource, the whitelist is hit and the resource is returned to the user.
- When a user in Macao (China) accesses the same resource, neither the blacklist nor the whitelist is hit. In this case, the access is denied by default and status code 403 is returned.
Example 3: Assume that you have configured the following rules for the domain name www.example.com.

Result:
- When a user in Hong Kong (China) accesses a resource in the /test/abc folder (for example, www.example.com/test/abc/1.jpg), the blacklist is hit and status code 403 is returned.
- When a user in the Chinese mainland accesses a resource in the /test folder (for example, www.example.com/test/cat.jpg), the whitelist is hit and the corresponding resource is returned to the user.
- When a user in Hong Kong (China) accesses a resource in the /test folder (for example, www.example.com/test/cat.jpg), neither the blacklist nor the whitelist is hit. In this case, the access is denied by default and status code 403 is returned.
- When a user in Macao (China) accesses a resource in the /test folder (for example, www.example.com/test/cat.jpg), neither the blacklist nor the whitelist is hit. In this case, the access is denied by default and status code 403 is returned.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





