Help Center/
GaussDB/
Developer Guide(Centralized_V2.0-8.x)/
SQL Reference/
SQL Syntax/
A/
ALTER DIRECTORY
Updated on 2025-09-22 GMT+08:00
ALTER DIRECTORY
Description
Modifies directory attributes.
Precautions
- Currently, only the directory owner can be changed.
- When enable_access_server_directory is set to off, only the initial user is allowed to change the directory owner. When enable_access_server_directory is set to on, users with the SYSADMIN permission and the directory object owner can change the directory object owner, and the user who changes the owner is required to be a member of the new owner.
- The DIRECTORY object cannot be used in a PDB.
Syntax
ALTER DIRECTORY directory_name
OWNER TO new_owner;
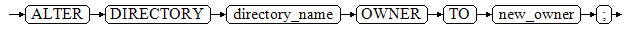
Parameters
- directory_name
Specifies the name of a directory to be modified. The value must be an existing directory name.
- new_owner
Specifies the new owner of the directory.
Examples
-- Create a directory. gaussdb=#CREATE OR REPLACE DIRECTORY dir as '/tmp/'; -- Create a user. gaussdb=#CREATE USER jim PASSWORD '********'; -- Change the owner of the directory. gaussdb=#ALTER DIRECTORY dir OWNER TO jim; -- Delete a directory. gaussdb=#DROP DIRECTORY dir; -- Delete the user. gaussdb=#DROP USER jim;
Helpful Links
Parent topic: A
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
The system is busy. Please try again later.
For any further questions, feel free to contact us through the chatbot.
Chatbot





