Enforcing Bucket Encryption
Scenarios
In scenarios that have high compliance and security requirements, you can use a service control policy (SCP) provided by Organizations to enforce server-side encryption. This policy ensures that member accounts it applies to must enable server-side encryption when creating buckets, and encryption cannot be disabled for existing buckets.
Background
When using Huawei Cloud, you may have multiple HUAWEI IDs. For example, you may have created separate HUAWEI IDs for your company's headquarters and each of its subsidiaries. To efficiently manage these IDs, you can use Huawei Cloud Organizations to create an organization and add the IDs to the organization for unified management.
- Organization: An organization is an entity created to manage multiple accounts. Each organization is composed of one management account and multiple member accounts. For details, see Overview of Organizations.
- Management account: A management account is the account that you use to create an organization. You can also use the management account to manage permissions and resources for member accounts using policies (such as SCPs). For details, see Overview of an Account.
- Member account: Except for the management account, any other accounts in an organization are member accounts. For details, see Overview of an Account.
- Organizational unit (OU): An OU is a container or a grouping unit for member accounts in your organization. An OU can have multiple child OUs or member accounts. For details, see Organizational Units.
- Service control policies (SCPs): SCPs are a type of organization policy that you can use to manage permissions in your organization. The management account can use SCPs to limit which permissions can be assigned to member accounts. For details, see SCP Introduction.
Solution Architecture
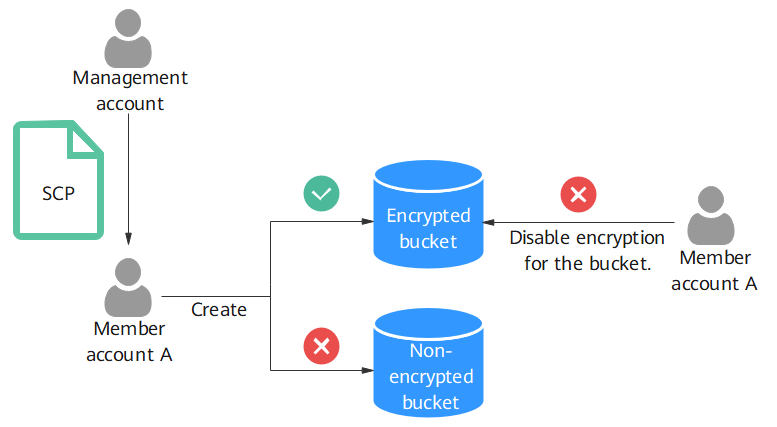
This section describes how to use an SCP to enforce bucket encryption. As shown in Figure 1, the management account creates an organization, and manages the member account A in the organization. The management account uses an SCP to enforce that member account A can only create encrypted buckets. The creation of non-encrypted buckets will be denied. Similarly, the SCP can prevent member account A from disabling encryption for existing buckets.
Constraints
An SCP is applied within 30 minutes after it is attached to a member account.
Operation Process
The process of enforcing bucket encryption is as follows:
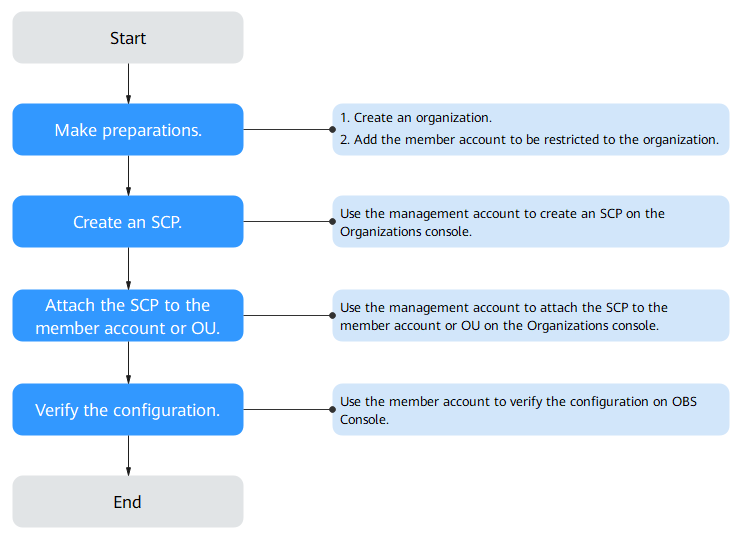
Step 1: Make Preparations on the Organizations Console
Before enforcing bucket encryption, make the following preparations:
- Create an organization. For details, see Creating an Organization. Then, the account you used to create the organization becomes the management account of the organization.
- Use the management account to add the member account to be restricted to the organization. For details, see Inviting an Account to Join Your Organization.
- (Optional) Move the account to be managed to an OU. To create an OU and move the account to the OU, see Creating an OU and Moving an Account. In this way, you can attach an SCP to the OU so that the policy is applied to all member accounts in that OU, which makes your management more efficient.
Step 2: Create an SCP on the Organizations Console
- Use the management account to log in to the Organizations console. In the navigation pane, choose Policies.
- Click Service control policies.
- Click Create Policy.
- Enter a policy name. Ensure that you are entering a unique policy name, different from any existing one.
- (Optional) Enter a description for the policy.
- Edit the policy content. The following are two example SCPs:
Example 1: This SCP enforces server-side encryption during bucket creation. It does not put limits on the encryption method or whether the encryption can be disabled for the bucket.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
{ "Version": "5.0", "Statement": [ { "Effect": "Deny", "Action": [ "obs:bucket:createBucket" ], "Condition": { "Bool": { "obs:BucketEncrypted": [ "false" ] } } } ] }
Example 2: This SCP enforces server-side encryption and the SSE-KMS method during bucket creation. It also prevents disabling encryption for existing buckets.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34
{ "Version": "5.0", "Statement": [ { "Effect": "Deny", "Action": [ "obs:bucket:createBucket" ], "Condition": { "StringNotEquals": { "obs:x-obs-server-side-encryption": [ "kms" ] } }, "Resource": [ "*" ] }, { "Effect": "Deny", "Action": [ "obs:bucket:putEncryptionConfiguration" ], "Condition": { "Bool": { "obs:BucketEncrypted": [ "false" ] } } } ] }
- Click Save in the lower right corner. The system then automatically verifies the syntax. If the policy list is displayed, the SCP is created successfully. If a message appears indicating incorrect policy content, modify the SCP syntax by referring to SCP Syntax.
Step 3: Attach the SCP to the Member Account or the OU on the Organizations Console
- Use the management account to log in to the Organizations console. In the navigation pane, choose Policies.
- Click Service control policies. The list of SCPs is displayed.
- Click Attach in the Operation column of the SCP created in Step 2. Then, select the member account or OU you want to attach the SCP to.
- In the displayed dialog box, enter "Confirm" and click OK.
Step 4: Verify the Configuration on OBS Console
Example 1:
- Use the member account to log in to OBS Console. In the navigation pane, choose Object Storage.
- Click Create Bucket in the upper right corner of the page.
- Configure bucket parameters by referring to Creating a Bucket. Do not enable server-side encryption.
- Click Create Now. If the bucket fails to be created, the configuration is in effect.
Example 2:
- Use the member account to log in to OBS Console. In the navigation pane, choose Object Storage.
- Click Create Bucket in the upper right corner of the page.
- Configure bucket parameters by referring to Creating a Bucket. Enable encryption for the bucket but do not select the SSE-KMS encryption method.
- Click Create Now. If the bucket fails to be created, the policy that enforces bucket encryption using SSE-KMS is in effect.
- Create another bucket with SSE-KMS used.
- Click the bucket in the bucket list to go to the Objects page.
- In the navigation pane, choose Overview.
- In the Basic Configurations area, click Server-Side Encryption.
- Disable server-side encryption and click OK. If server-side encryption fails to be disabled, the policy that prevents encryption from being disabled is in effect.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot