Using HSS to Scan for Trojans
Scenario
Trojans are an important issue in the current network security field. They intrude computer systems in different ways, which poses serious threats to user data security, privacy protection, and system stability.
To prevent Trojans, you need to update the OS and software in a timely manner, use secure network connections, and avoid downloading and running files from unknown sources. In addition, you can use HSS to view and handle reported Trojan alarms and fix system vulnerabilities to improve system security.
This section describes how to use HSS to scan for Trojans.
Prerequisites
HSS professional, enterprise, premium, WTP, or container edition has been enabled for the server. For details, see HSS Access Overview.
Step 1: Scan for and Remove Trojans
After HSS protection is enabled for a server, if a Trojan is implanted on the server, HSS will report a Trojan alarm. You need to determine whether the detected Trojan alarm file is normal. If it is an attack event, you are advised to isolate and kill malicious files.
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Detection & Response > Alarms. The Server Alarms page is displayed.
- In the Alarms to Be Handled area, choose to view the alarms reported within the specified time range.
Figure 1 Trojan alarm
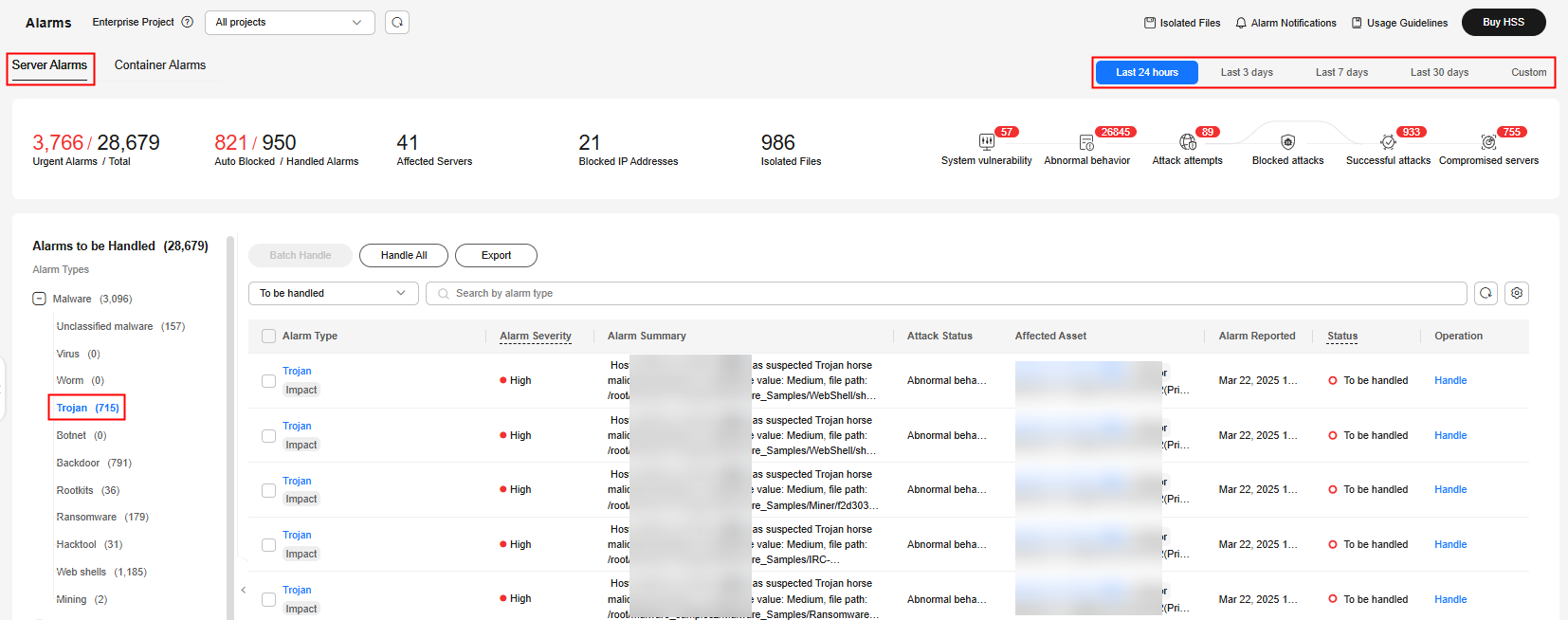
- In the alarm list on the right, click the alarm name to view details about the Trojan alarm.
- In the alarm list, click Handle in the Operation column.
- In the dialog box that is displayed, set Action to Isolate and kill.
If a program is isolated and killed, it will be terminated immediately and no longer able to perform read or write operations. Isolated source files of programs or processes are displayed on the Isolated Files slide-out panel and cannot harm your servers.
- In the upper right corner of the Alarms page, click Isolated Files to view the isolated files.
Step 2: Back Up and Restore Data, and Fix Vulnerabilities
- Data backup and restoration
If your data is lost due to Trojan malicious programs and you have subscribed to CBR, you can try to restore data using CBR. For details, see Restoring Data Using a Cloud Server Backup.
- Vulnerability fixing
To prevent the server from being intruded by Trojans again, you can use the vulnerability management function of HSS to view and fix the server vulnerabilities. For details, see Using HSS to Scan for and Fix Vulnerabilities.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





