Using a Dedicated Load Balancer to Forward Traffic by Port Ranges
Scenarios
If your service has dynamic ports or you need to listen to multiple ports, instead of configuring a fixed port for each listener, you can use a dedicated load balancer and enable Forward by Port Ranges to route traffic across backend servers over multiple ports or port ranges. This simplifies listener configurations and makes O&M easier.
Prerequisites
- There is a dedicated network load balancer with an EIP bound to it. If there is no such resource, you can buy one and bind an IPv4 EIP to the load balancer.
- There are two ECSs (ECS01 and ECS02), each hosting an application. The security group rules of ECS01 and ECS02 allow access over ports 30000 to 30005.
Step 1: Create a Backend Server Group and Enable Forward to Same Port
In this practice, a backend server group that supports Forward to Same Port is used. If this option is enabled, you do not need to specify a backend port when you add a backend server. The listener routes requests to the backend server over the same port as the frontend port.
- Go to the backend server group list page.
- Click Create Backend Server Group in the upper right corner.
- Configure the parameters based on Table 1 and retain the default values for other parameters.
Table 1 Parameters required for configuring a routing policy Parameter
Example Value
Description
Backend Server Group Name
server_group
Specifies the name of the backend server group.
Type
Dedicated
Specifies the type of load balancer that can use the backend server group.
Load Balancer
Associate existing
Specifies whether to associate a load balancer.
Click Associate existing and select a load balancer you have created.
Backend Protocol
TCP
Specifies the protocol that backend servers in the backend server group use to receive requests from the listeners.
Select TCP.
Forward to Same Port
Enable it.
Specifies whether to enable the forward to same port option. After you enable it, you do not need to specify a backend port when you add a backend server. The listener routes requests to the backend server over the same port as the frontend port.
This option cannot be disabled after being enabled.
Load Balancing Algorithm
Weighted round robin
Specifies the load balancing algorithm used by the load balancer to distribute traffic.
Weighted round robin: Requests are routed to different servers based on their weights. Backend servers with higher weights receive proportionately more requests, whereas equal-weighted servers receive the same number of requests.
For more information, see Load Balancing Algorithms.
- Click Next to add backend servers and configure health check.
- Click Add Cloud Server, select ECS01 and ECS02, and retain the default values for other parameters.
- Enable Health Check. The ECSs do not have default backend ports because Forward to Same Port is enabled for the backend server group. You only need to configure a health check port.
In this practice, set the health check port to 80 and retain the default values for other health check parameters.
- Click Next.
- Confirm the configuration and click Create Now.
Step 2: Add a TCP Listener and Enable Forwarding by Port Ranges
This practice uses a TCP listener as an example to distribute traffic by port ranges.
- Go to the load balancer list page.
- Locate the target load balancer and click Add Listener in the Operation column.
- On the displayed page, set Frontend Protocol to TCP, enable Forwarding by Port Ranges, and set the port range to 30000-30005.
Figure 1 Adding a TCP listener and selecting port ranges
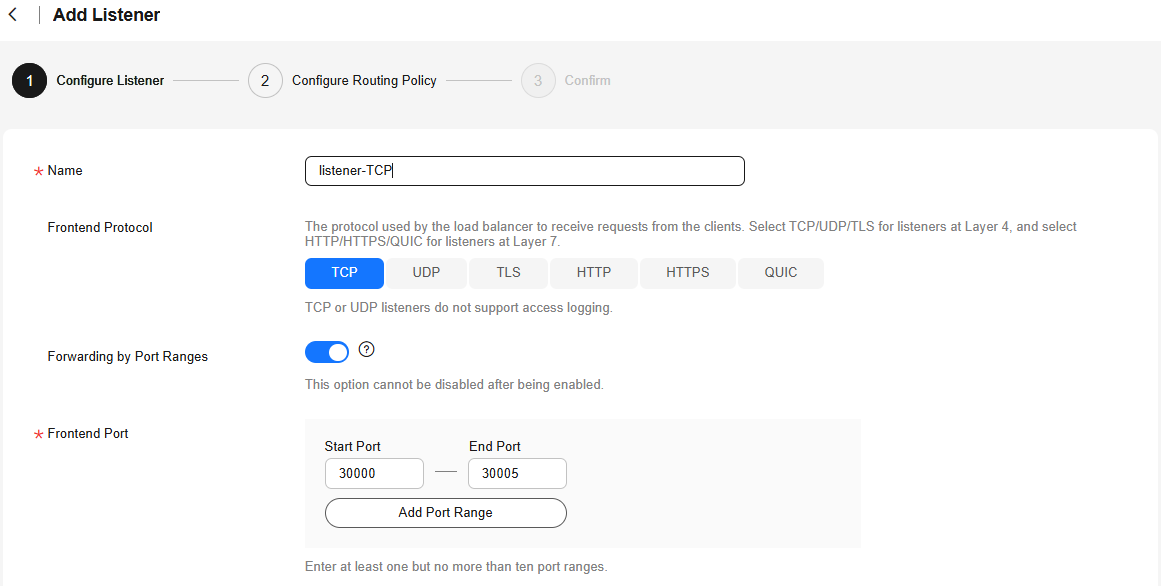
- Click Next: Configure Request Routing Policy and configure the backend server group.
Click Use Existing and select the backend server group created in Step 1: Create a Backend Server Group and Enable Forward to Same Port.
- Click Next: Confirm, confirm the configurations, and submit your request.
Step 3: Configure Domain Name Resolution
You can add an A record set to resolve the domain name to the public IP address of the load balancer so that clients can access the load balancer using the public domain name.
For details about how to configure A record sets, see Routing Internet Traffic to a Website.
- Go to the DNS console.
- In the navigation pane on the left, choose Public Zones.
The zone list is displayed.
- Locate the zone and click Manage Record Sets in the Operation column.
- Click Add Record Set.
- Configure the parameters based on Table 2.
Table 2 Parameters for adding an A record set Parameter
Example Value
Description
Type
A – Map domains to IPv4 addresses
Type of the record set. In this example, set it to A - Map domains to IPv4 addresses.
Name
www
Prefix of the domain name to be resolved.
Line
Default
Resolution line. The DNS server will return the IP address of the specified line, depending on where visitors come from.
The default value is Default.
Default: returns the default resolution result irrespective of where the visitors come from.
TTL (s)
300
Cache duration of the record set on a local DNS server, in seconds.
In this example, the default value 300 is used.
Value
192.168.12.2
IPv4 addresses mapped to the domain name. In this example, set this parameter to the EIPs bound to the load balancer.
Advanced Settings (Optional)
-
Click
 to expand the advanced settings, set the alias and weight of the record set, and add a description and tags. In this example, the default settings are used.
to expand the advanced settings, set the alias and weight of the record set, and add a description and tags. In this example, the default settings are used. - Click OK.
- Switch back to the Record Sets tab.
Check the record you just added in the record set list. If its status is Normal, the record set is added.
Step 4: Verifying Forwarding Traffic by Port Ranges
- Testing Load Balancer Availability
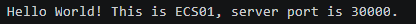
- Use any Linux client that can access the public network as an example. Run curl <domain-name> <any-port-between-30000-and-30005> multiple times. If information similar to "Hello World! This is ECS01, server port is specific-port-number" is displayed, the load balancer can forward requests to the backend server.
Figure 2 Linux client requests distributed to ECS01
- Access the domain name and any port number between 30000 and 30005 using a browser, for example, http://domain-name:30000. If information similar to the following figure is displayed, the client can access the application.
Figure 3 Browser requests distributed to ECS01

- Use any Linux client that can access the public network as an example. Run curl <domain-name> <any-port-between-30000-and-30005> multiple times. If information similar to "Hello World! This is ECS01, server port is specific-port-number" is displayed, the load balancer can forward requests to the backend server.
- Simulating a Service Fault
- Run systemctl stop nginx.service to disable the application running on ECS01.
Wait for several minutes and run curl <domain-name> <any-port-between-30000-and-30005> on the client again. The information similar to the following figure is still displayed.
Figure 4 Client requests distributed to ECS02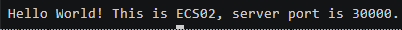
- Access the domain name and any port number between 30000 and 30005 using a browser, for example, http://domain-name:30000. If information similar to the following figure is displayed, the client can access the application.
Figure 5 Browser requests distributed to ECS02
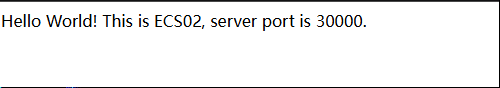
- Run systemctl start nginx.service to enable the application on ECS01 and systemctl stop nginx.service to disable the application on ECS02.
Wait for several minutes and run telnet <domain-name> <any-port-between-30000-and-30005> on the client again. The information similar to the following figure is still displayed.
Figure 6 Linux client requests distributed to ECS01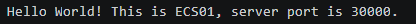
- Access the domain name and any port number between 30000 and 30005 using a browser, for example, http://domain-name:30000. If information similar to the following figure is displayed, the client can access the application.
Figure 7 Browser requests distributed to ECS01
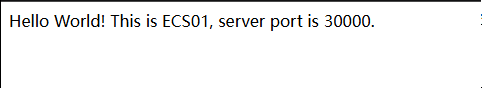
- The preceding test result shows that ELB can route requests to the healthy backend server over any port between 30000 and 30005, if a single backend server fails.
- Run systemctl stop nginx.service to disable the application running on ECS01.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





