Using DNS Resolver and Linux Bind to Resolve Domain Names Across Accounts
Scenarios
Huawei Cloud DNS Resolver mainly applies to the hybrid cloud DNS solution. It seamlessly connects the customer's local network to the Huawei Cloud VPC infrastructure network. The solution aims to simplify DNS management and enable efficient domain name resolution in Huawei Cloud.
You can use DNS Resolver to resolve DNS queries between the local DNS and Huawei Cloud without setting up another DNS server in Huawei Cloud. This enables seamless communication between local networks and Huawei Cloud resources, facilitates hybrid deployment, and reduces management costs.
In this practice, we will:
- Deploy a Linux Bind server on the local network for cross-account DNS resolution.
- Configure DNS Resolver in Huawei Cloud for domain name resolution.
- Use domain names for communication between servers under different accounts.
Solution
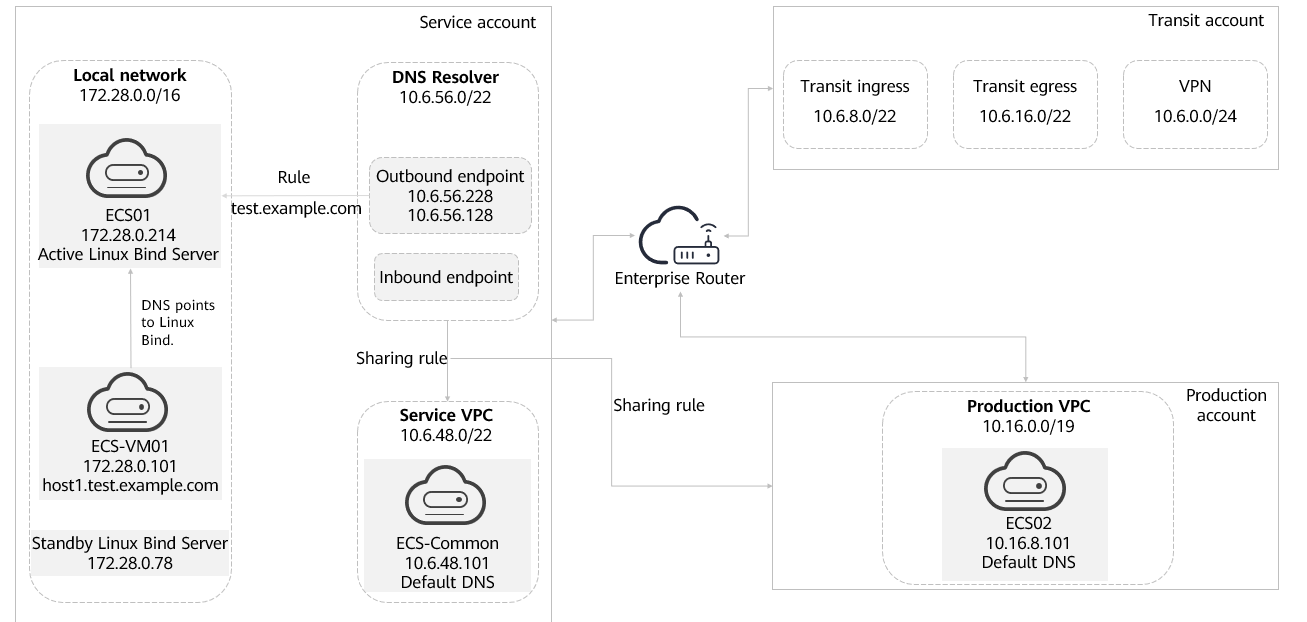
As shown in Figure 1, to demonstrate DNS resolution between the local network and Huawei Cloud, we will create three VPCs under the service account. The isolated VPC is used to deploy a Linux Bind server. The IP address range of the local network is 172.28.0.0/16. The other two VPCs are used for deploying DNS Resolver and connectivity tests. Create a VPC under the production account for carrying workloads in the production environment. All VPCs are connected through an enterprise router to enable communication between resources of different accounts.
- VM01: a server on the local network.
- ECS01: a test server under the service account.
- ECS02: a test server under the production account.
DNS Resolver is associated with the service VPC. All DNS rules are shared among different VPCs of different accounts.
DNS queries from an ECS are first sent to the Huawei Cloud DNS server. If the queries are for a private domain name (domain name specified in the endpoint rule) of the on-premises DNS server in an IDC, the queries are forwarded to the on-premises DNS server over the outbound endpoint for resolution.
In this practice, the IP addresses in the local network and Huawei Cloud are for reference only. In actual applications, deploy the solution based on the actual network plan.
Preparations
- You need to be familiar with the following basic concepts:
- Multi-account strategy in Huawei Foundation Architecture (HFA)
- An enterprise router or VPC peering connection used for VPC network connectivity
- DNS resolution in Huawei Cloud
- Linux environment and the BIND software package
- Service deployment regions: DNS Resolver has been rolled out in some regions. You need to plan services in these regions. For details, see DNS Resolver Overview.
- Resource Access Manager (RAM): In a multi-account environment, you need to use RAM to share DNS rules between different accounts without the need to creating duplicate rules in each account. DNS Resolver and its rules should be configured only in service accounts.
- Account permissions: You must have root permissions in at least three Huawei Cloud accounts. The following table describes the account types and their usage.
Account Type
Usage
Transit account
Used to connect different VPCs through an enterprise router.
Service account
Used to host shared resources (such as DNS Resolver).
Production account
Used to host workloads in the production environment.
Step 1: Establish VPC Connections Between Different Accounts
- In the service account, create three VPCs for the following purposes:
- Associate with the Linux Bind server as the local network.
- Associate with DNS Resolver.
- Associate with the test server in the service account.
- In the production account, create a VPC and associate it with the test server in the production account.
- In the transit account, create an enterprise router and configure VPC connections and route tables.
- Share the enterprise router with the service and production accounts.
- In the production account, create a VPC connection to add the production VPC to the enterprise router.
- In the service account, create a VPC connection and add all VPCs in the account to the enterprise router.
- In the transit account, configure the route tables of the enterprise router as follows:
- Associate all VPCs in the service account with the default route table.
- In the default route table of the enterprise router, create propagations for all VPCs in the service and production accounts.
- Associate the production VPC with the custom route table.
- In the custom route table of the enterprise router, create propagations for all VPCs in the service and production accounts.
Step 2: Deploy Servers
- Deploy Linux Bind servers in the service account and deploy test servers in the service and production accounts.
- In the service account, purchase ECSs. The detailed information is as follows:
- ECS-VM01: functions as the test server on the internal network. The private IP address is 172.28.0.101.
- ECS01: functions as the active Linux Bind server on the local network. The private IP address is 172.28.0.214.
- ECS-Common: functions as the test server in the service account. The private IP address is 10.6.48.101.
- On ECS-VM01, set the DNS server IP address to 172.28.0.214, the IP address of the active Linux Bind server.
- In the production account, purchase an ECS.
ECS02: functions as the test server in the production account. The private IP address is 10.16.8.101.
- In the service account, purchase ECSs. The detailed information is as follows:
- Configure the Linux Bind server in the service account.
- Log in to the Linux Bind server ECS-VM01 and run the following commands to install bind-utils and open the /etc/named.conf file:
$ sudo yum update $ sudo yum install bind-utils $ vim /etc/named.conf
- Modify the /etc/named.conf file.
- Configure the trusted ACL list to allow DNS queries only from the IP addresses of ECS01, ECS-VM01, standby Linux Bind server, ECS-Common, and ECS02.
IP addresses: 172.28.0.101, 172.28.0.214, 172.28.0.78, 10.6.48.101, and 10.16.8.101
- Bind the server to listen on port 53 and ensure that port 53 is allowed in the security group bound to the test server.
- Allow queries from the trusted IP address list.
- If there is a standby DNS server, transmit queries to the standby DNS server.
- Configure the trusted ACL list to allow DNS queries only from the IP addresses of ECS01, ECS-VM01, standby Linux Bind server, ECS-Common, and ECS02.
- On the Linux Bind server, run the following commands to configure the local file:
$ vim /etc/named/named.conf.local zone "test.example.com" { type master; file "/etc/named/zones/db.test.example.com"; # Path of the zone file }; zone "28.172.in-addr.arpa" { type master; file "/etc/named/zones/db.172.28"; # Subnet 172.28.0.0/24 }; - Create a forward zone file and edit it:
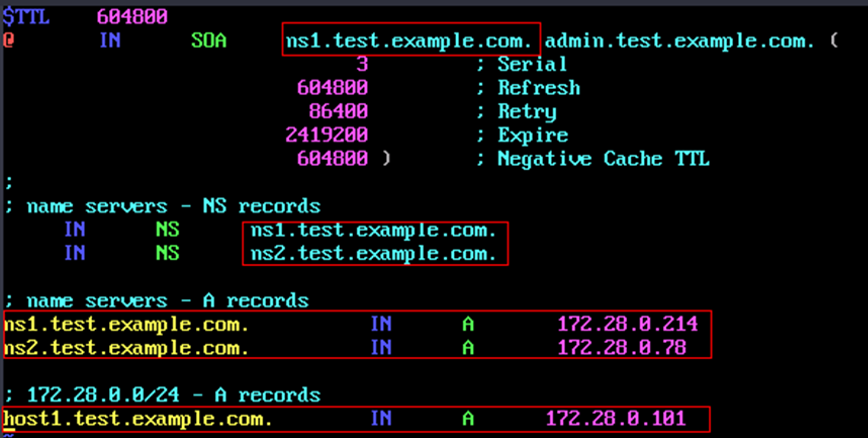
$ sudo chmod 755 /etc/named $ sudo mkdir /etc/named/zones $ sudo vim /etc/named/zones/db.test.example.com
Modify the file and insert the highlighted information according to the following figure.
- Create a reverse zone file and edit it:
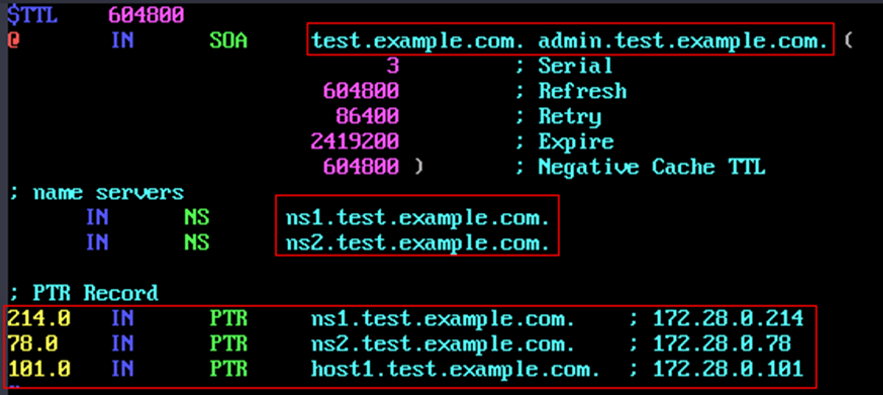
$ sudo vim /etc/named/zones/db.172.28
Modify the file and insert the highlighted information according to the following figure.
- Check the BIND configuration syntax.
$ sudo named-checkconf $ sudo named-checkzone test.example.com /etc/named/zones/db.test.example.com $ sudo named-checkzone 128.10.in-addr.arpa /etc/named/zones/db.172.28
- Start the BIND service.
$ sudo systemctl enable named $ sudo systemctl start named
- Log in to the Linux Bind server ECS-VM01 and run the following commands to install bind-utils and open the /etc/named.conf file:
Configuring DNS Resolver
- Create inbound and outbound endpoints in the service account.
For details, see Creating an Inbound Endpoint and Creating an Outbound Endpoint.
- Configure an outbound rule for forwarding DNS queries to the Linux Bind server.
For details, see Adding an Endpoint Rule.
- Share the outbound rule with the production account.
For details, see Creating a Share.
- In the production account, access the DNS console, and associate the production VPC with the shared outbound rule of DNS Resolver.
Verification
Test DNS resolution using the same account.
- On ECS-VM01, resolve the private domain name associated with ECS-VM01.
nslookup host1.test.example.com
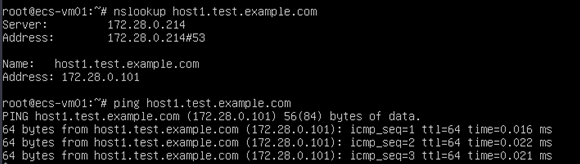
- On ECS-Common, resolve the private domain name associated with ECS-VM01.
nslookup host1.test.example.com
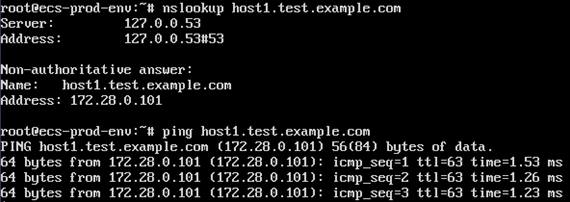
Summary
In this practice, we have learned how to deploy a Linux Bind DNS server in Huawei Cloud and use DNS Resolver to resolve domain names in a multi-account environment.
DNS Resolver helps you avoid repeatedly setting up domain controllers in the local environment and Huawei Cloud. This reduces management costs.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot